Infographic Protecting Patient Data
•
3 likes•6,681 views
Learn the security risks of digital healthcare technology and how healthcare organizations can protect their patients’ data with Fortinet’s Security Fabric.
Report
Share
Report
Share
Download to read offline
Recommended
An Ounce of Prevention: How Healthcare Organizations Can Stop Cybercrime in I...

Healthcare regularly tops the list of most cyberattacked industries thanks to the extremely valuable patient information it retains. And as healthcare becomes more digitally connected than ever before, it’s imperative that these organizations invest in top-notch IT security.
More: http://ms.spr.ly/6001pYtz3
Why shaWHY SHARE CYBER THREAT INFORMATIONre cyber threat information

Cyber threat information sharing is essential to thwarting successful hacks and minimizing consequences should a breach occur. For many years large organizations have had opportunities to work with the Department of Homeland Security (DHS) to share indicators of compromise to ensure the protection of critical infrastructure and major business entities.
https://mikeechols.com/why-share-cyber-threat-information
Mha690 wk1 dis2

The document discusses the Health Insurance Portability and Accountability Act (HIPAA) and its requirements for protecting private health information. It notes that HIPAA was established in 1996 and outlines its privacy and security rules. It also provides recommendations for HIPAA compliance, including training employees, implementing access controls, conducting security audits, and logging system activity. Finally, it discusses the civil and criminal penalties for violating HIPAA regulations.
Data integrity, security and privacy

Data integrity refers to data accuracy and is a vital concern for organizations. Data security protects data from destruction and misuse, both intentional and accidental, and is a growing challenge as organizations grant database access. A database activity monitoring program continually monitors databases to detect and report possible intrusions and other threats in real time.
Defending Your Institution Against Ransomware Attacks

This article was published in Education Technology Insights in June 2019. Because the publisher didn’t include my references, this document is shared to provide the article’s references cited.
https://education-security.educationtechnologyinsights.com/cxoinsights/defending-your-institution-against-ransomware-attacks-nid-646.html
Handling information Standard by Skills for Care

This document discusses handling information in health and social care. It states that information about an individual's care is private and must be kept confidential, only sharing with those who need to know. It provides examples of who would need to know, such as care workers involved in an individual's care but not neighbors or unrelated care workers. The document also discusses risks of sharing on social media and legal requirements regarding data protection and freedom of information. Policies around secure storage, passwords, and filing are outlined. Concerns about improper information handling should be reported to managers.
The CIA Triad - Assurance on Information Security

Confidentiality, Integrity and Availability of Data are the basis for providing assurance on IS Security. This document gives a small overview of the impact of confidentiality, integrity and availability on the data and the need of securing the CIA.
Q4 Threat Report 2016

The FortiGuard Labs threat research team analyzed real-world threat data from around the globe to create this insightful report. It not only shares findings on the most prevalent exploits, malware, and botnets, but offers observations on threat variance by region and industry for an accurate picture of worldwide threat activity.
Recommended
An Ounce of Prevention: How Healthcare Organizations Can Stop Cybercrime in I...

Healthcare regularly tops the list of most cyberattacked industries thanks to the extremely valuable patient information it retains. And as healthcare becomes more digitally connected than ever before, it’s imperative that these organizations invest in top-notch IT security.
More: http://ms.spr.ly/6001pYtz3
Why shaWHY SHARE CYBER THREAT INFORMATIONre cyber threat information

Cyber threat information sharing is essential to thwarting successful hacks and minimizing consequences should a breach occur. For many years large organizations have had opportunities to work with the Department of Homeland Security (DHS) to share indicators of compromise to ensure the protection of critical infrastructure and major business entities.
https://mikeechols.com/why-share-cyber-threat-information
Mha690 wk1 dis2

The document discusses the Health Insurance Portability and Accountability Act (HIPAA) and its requirements for protecting private health information. It notes that HIPAA was established in 1996 and outlines its privacy and security rules. It also provides recommendations for HIPAA compliance, including training employees, implementing access controls, conducting security audits, and logging system activity. Finally, it discusses the civil and criminal penalties for violating HIPAA regulations.
Data integrity, security and privacy

Data integrity refers to data accuracy and is a vital concern for organizations. Data security protects data from destruction and misuse, both intentional and accidental, and is a growing challenge as organizations grant database access. A database activity monitoring program continually monitors databases to detect and report possible intrusions and other threats in real time.
Defending Your Institution Against Ransomware Attacks

This article was published in Education Technology Insights in June 2019. Because the publisher didn’t include my references, this document is shared to provide the article’s references cited.
https://education-security.educationtechnologyinsights.com/cxoinsights/defending-your-institution-against-ransomware-attacks-nid-646.html
Handling information Standard by Skills for Care

This document discusses handling information in health and social care. It states that information about an individual's care is private and must be kept confidential, only sharing with those who need to know. It provides examples of who would need to know, such as care workers involved in an individual's care but not neighbors or unrelated care workers. The document also discusses risks of sharing on social media and legal requirements regarding data protection and freedom of information. Policies around secure storage, passwords, and filing are outlined. Concerns about improper information handling should be reported to managers.
The CIA Triad - Assurance on Information Security

Confidentiality, Integrity and Availability of Data are the basis for providing assurance on IS Security. This document gives a small overview of the impact of confidentiality, integrity and availability on the data and the need of securing the CIA.
Q4 Threat Report 2016

The FortiGuard Labs threat research team analyzed real-world threat data from around the globe to create this insightful report. It not only shares findings on the most prevalent exploits, malware, and botnets, but offers observations on threat variance by region and industry for an accurate picture of worldwide threat activity.
OIF 112G Panel at DesignCon 2017

This document discusses the development of 112Gbps electrical interfaces. It begins with an overview of the OIF's CEI specifications for various data rates ranging from 1.6Gbps to 112Gbps. It then examines potential modulation schemes for 112Gbps, including PAM-4, PAM-8, duo-binary and DMT. The document evaluates the feasibility of a 112Gbps very short reach channel based on existing 56Gbps channel models. It finds that channel improvements would be needed to support 112Gbps. Finally, it considers approaches to developing improved 112Gbps channels, such as reducing channel length, using lower loss materials, and integrating cable connectors.
Zaptech Solutions - Software Development Company

A custom software development company offering development services for web, mobile and desktop applications besides various games development.
Cloud Expo May 09 Richard Britton, Cloud Computing for SMEs

Richard Britton - IT Director at Easynet Connect, ISP for SMEs in the UK - presentation at Cloud Expo london May 2009
Arise EMEA - My Story Video Contest

Arise invites its CSPs to participate in a video contest - send us a video clip, not more than 3 mins, sharing your experience as a homeworker and telling us what you love most about the work you do.
Agile - Scrum

The document discusses key concepts in Agile development including Scrum framework. It compares traditional waterfall model with Agile approach. Some key Scrum concepts covered are roles, events, artifacts, empirical process control, transparency, self-organizing teams. It provides details on events like daily scrum, sprint planning and retrospective. Artifacts discussed are product backlog, sprint backlog and definition of done. Traditional vs Agile success rates are also shared.
Data on demand flexible archiving in a big content world

The Xenos Repository provides document storage and multi-channel delivery for high-volume customer statements, electronic documents and scanned images. It has advanced storage capabilities that leverage different storage tiers and can compress content to reduce storage costs. The Xenos Repository also offers indexing, business intelligence, and content analytics capabilities by integrating with Actuate BIRT. It addresses shortcomings of other archival systems and allows users to analyze, enhance, and interact with stored content across channels.
ECC Cloud and Security

The cloud has been around for a while and is really starting to take off! Here are some thoughts on security that may be useful and help you get your head around your security exposure.
High Performance Medical Reconstruction Using Stream Programming Paradigms

High Performance Medical Reconstruction Using Stream Programming ParadigmsQuEST Global (erstwhile NeST Software)
The complexity of Medical image reconstruction requires tens to hundreds of billions of computations per second. Until few years ago, special purpose processors designed especially for such applications were used. Such processors require significant design effort and are thus difficult to change as new algorithms in reconstructions evolve and have limited parallelism. Hence the demand for flexibility in medical applications motivated the use of stream processors with massively parallel architecture. Stream processing architectures offers data parallel kind of parallelism.Msp deck v1.0

This document discusses how managed service providers (MSPs) can evolve their business models to offer more competitive managed security services. It notes that MSPs must move from being mere implementers and maintainers to true managed service providers that focus on retention through value articulation. The document recommends that MSPs support all infrastructure types, enable faster identification and prevention of threats through integrated monitoring and analytics, and leverage a single tool to capitalize on new opportunities in the information security market, which is growing at 24.9% annually for IT security outsourcing.
2014 Ecommerce Holiday Prep

Tenzings guide to preparing your Ecommerce infrastructure, applicatoin and marketing for the holiday season - The Updated 2015 Guide is available at http://info.tenzing.com/holidayprep
Insperity Business Confidence Survey Q2 2015 [Infographic]![Insperity Business Confidence Survey Q2 2015 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Insperity Business Confidence Survey Q2 2015 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Insperity asked executives from 5,300 businesses about their second quarter 2015 results and what those meant for the remainder of 2015. Here’s what they shared.
iBOS Solution - Incessant Business Operations Suite 

iBOS Solution: iBOS is a business operations suite that automates & optimizes internal operations by connecting people, departments, resources and support divisions, to serve the enterprise core business in a timely & competitive manner. Presented as part of Guest speaker slot in Application Innovation Track- Industry Solutions Showcase at Appian World 2015 from Apr 27-29 at WA, DC.
Get Your Head in the Cloud

The document discusses cloud computing and its advantages for businesses. Specifically, it notes that cloud computing involves delivering hosted services over the Internet. It advocates that businesses should focus on their core competencies and outsource non-essential tasks like IT that can be provided more cheaply and efficiently in the cloud. Some key benefits of cloud computing mentioned include low upfront costs, flexibility to quickly access more resources as needed, and having the provider manage the infrastructure.
Call Management Services Should be Part of Every Business Telephone System

Today’s sophisticated call management systems integrate various other devices including mobiles and tabs so that an all inclusive call management can be achieved by the business.
Innovation management -by Sudhakar Ram

Mastek is a high-end provider of enterprise technology solutions that enables business transformation, particularly in the insurance industry. It has over 19 years of insurance experience working with over 90 customers globally. It provides various insurance software products and has over 1200 insurance technology professionals and a 180 person research and development lab. Mastek has received several awards and recognition for its work in the insurance industry. It focuses on helping insurers overcome technology barriers and unlock innovation.
Product Engineering

Geometric provides product engineering services from initial concept development to final production ready design.
How marketers can leverage Ektron DXH's Exact Target for better client engage...

How marketers can leverage Ektron DXH's Exact Target for better client engage...Suyati Technologies Pvt Ltd
In this webinar -- How marketers can leverage Ektron DXH's Exact Target for better client engagement -- we will discuss:
1. How to increase customer engagement and target personalized content.
2. How the Ektron DXH - ExactTarget Connector can solve the problems of marketers, and fill the gaps in existing tools.
3. Demo of Ektron - ExactTarget connector.
Webinar Video: https://www.youtube.com/watch?v=5h47CbfMXZw
Website: http://suyati.com/services/cms/ektron/Christmas 2015

Santa uses technology like unified desktop software, big data algorithms, and mobile apps to efficiently manage present production and delivery logistics in his workshop. This allows him to track naughty/nice statuses, present wishes, production workflows, and optimize Santa's delivery route, helping fulfill every child's wish on Christmas despite the massive scale of operations. While technology helps, the true Christmas miracle remains how Santa accomplishes this enormous task in just one night.
Cybersecurity

ybersecurity is an increasing
concern for many in the
medical cybersecurity and
information technology
professions. As computerized
devices in medical facilities
become increasingly networked
within their own walls and
with external facilities, the risk
of cyberattacks also increases,
threatening confidentiality,
safety, and well-being. This
article describes what health
care organizations and
imaging professionals should
do to minimize the risks.
Systems Thinking on a National Level, Part 2Drew David.docx

This document discusses various cybersecurity threats faced by the healthcare industry, including phishing emails, SQL injection attacks, eavesdropping, and viruses. Phishing emails are a major issue, accounting for 93% of breached healthcare data. Hackers use phishing emails that appear legitimate to trick staff into revealing sensitive information. The document also examines ways to better protect against these threats, such as password protection, data loss prevention, access controls, and staff training. Overall, the document analyzes the cybersecurity risks healthcare organizations face and ways to decrease breaches through education and prevention methods.
Privacy and Security by Design

Privacy and Security by Design Spotlight Presentation at HIMMS Privacy and Security Forum, December 5th 2016. Presented by Jeff R. Livingstone, PhD, Vice President and Global Lead, Life Sciences & Healthcare, Unisys Corporation.
Why healthcare is the biggest target for cyberattacks-converted.pdf

Sparity provides the Top Custom healthcare Software and Application development services for healthcare industries in USA and Across the Globe. We can help you build a leading-edge tech platform with the right UI/UX framework and functionalities. We Make a positive impact with modern healthcare services
More Related Content
Viewers also liked
OIF 112G Panel at DesignCon 2017

This document discusses the development of 112Gbps electrical interfaces. It begins with an overview of the OIF's CEI specifications for various data rates ranging from 1.6Gbps to 112Gbps. It then examines potential modulation schemes for 112Gbps, including PAM-4, PAM-8, duo-binary and DMT. The document evaluates the feasibility of a 112Gbps very short reach channel based on existing 56Gbps channel models. It finds that channel improvements would be needed to support 112Gbps. Finally, it considers approaches to developing improved 112Gbps channels, such as reducing channel length, using lower loss materials, and integrating cable connectors.
Zaptech Solutions - Software Development Company

A custom software development company offering development services for web, mobile and desktop applications besides various games development.
Cloud Expo May 09 Richard Britton, Cloud Computing for SMEs

Richard Britton - IT Director at Easynet Connect, ISP for SMEs in the UK - presentation at Cloud Expo london May 2009
Arise EMEA - My Story Video Contest

Arise invites its CSPs to participate in a video contest - send us a video clip, not more than 3 mins, sharing your experience as a homeworker and telling us what you love most about the work you do.
Agile - Scrum

The document discusses key concepts in Agile development including Scrum framework. It compares traditional waterfall model with Agile approach. Some key Scrum concepts covered are roles, events, artifacts, empirical process control, transparency, self-organizing teams. It provides details on events like daily scrum, sprint planning and retrospective. Artifacts discussed are product backlog, sprint backlog and definition of done. Traditional vs Agile success rates are also shared.
Data on demand flexible archiving in a big content world

The Xenos Repository provides document storage and multi-channel delivery for high-volume customer statements, electronic documents and scanned images. It has advanced storage capabilities that leverage different storage tiers and can compress content to reduce storage costs. The Xenos Repository also offers indexing, business intelligence, and content analytics capabilities by integrating with Actuate BIRT. It addresses shortcomings of other archival systems and allows users to analyze, enhance, and interact with stored content across channels.
ECC Cloud and Security

The cloud has been around for a while and is really starting to take off! Here are some thoughts on security that may be useful and help you get your head around your security exposure.
High Performance Medical Reconstruction Using Stream Programming Paradigms

High Performance Medical Reconstruction Using Stream Programming ParadigmsQuEST Global (erstwhile NeST Software)
The complexity of Medical image reconstruction requires tens to hundreds of billions of computations per second. Until few years ago, special purpose processors designed especially for such applications were used. Such processors require significant design effort and are thus difficult to change as new algorithms in reconstructions evolve and have limited parallelism. Hence the demand for flexibility in medical applications motivated the use of stream processors with massively parallel architecture. Stream processing architectures offers data parallel kind of parallelism.Msp deck v1.0

This document discusses how managed service providers (MSPs) can evolve their business models to offer more competitive managed security services. It notes that MSPs must move from being mere implementers and maintainers to true managed service providers that focus on retention through value articulation. The document recommends that MSPs support all infrastructure types, enable faster identification and prevention of threats through integrated monitoring and analytics, and leverage a single tool to capitalize on new opportunities in the information security market, which is growing at 24.9% annually for IT security outsourcing.
2014 Ecommerce Holiday Prep

Tenzings guide to preparing your Ecommerce infrastructure, applicatoin and marketing for the holiday season - The Updated 2015 Guide is available at http://info.tenzing.com/holidayprep
Insperity Business Confidence Survey Q2 2015 [Infographic]![Insperity Business Confidence Survey Q2 2015 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Insperity Business Confidence Survey Q2 2015 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Insperity asked executives from 5,300 businesses about their second quarter 2015 results and what those meant for the remainder of 2015. Here’s what they shared.
iBOS Solution - Incessant Business Operations Suite 

iBOS Solution: iBOS is a business operations suite that automates & optimizes internal operations by connecting people, departments, resources and support divisions, to serve the enterprise core business in a timely & competitive manner. Presented as part of Guest speaker slot in Application Innovation Track- Industry Solutions Showcase at Appian World 2015 from Apr 27-29 at WA, DC.
Get Your Head in the Cloud

The document discusses cloud computing and its advantages for businesses. Specifically, it notes that cloud computing involves delivering hosted services over the Internet. It advocates that businesses should focus on their core competencies and outsource non-essential tasks like IT that can be provided more cheaply and efficiently in the cloud. Some key benefits of cloud computing mentioned include low upfront costs, flexibility to quickly access more resources as needed, and having the provider manage the infrastructure.
Call Management Services Should be Part of Every Business Telephone System

Today’s sophisticated call management systems integrate various other devices including mobiles and tabs so that an all inclusive call management can be achieved by the business.
Innovation management -by Sudhakar Ram

Mastek is a high-end provider of enterprise technology solutions that enables business transformation, particularly in the insurance industry. It has over 19 years of insurance experience working with over 90 customers globally. It provides various insurance software products and has over 1200 insurance technology professionals and a 180 person research and development lab. Mastek has received several awards and recognition for its work in the insurance industry. It focuses on helping insurers overcome technology barriers and unlock innovation.
Product Engineering

Geometric provides product engineering services from initial concept development to final production ready design.
How marketers can leverage Ektron DXH's Exact Target for better client engage...

How marketers can leverage Ektron DXH's Exact Target for better client engage...Suyati Technologies Pvt Ltd
In this webinar -- How marketers can leverage Ektron DXH's Exact Target for better client engagement -- we will discuss:
1. How to increase customer engagement and target personalized content.
2. How the Ektron DXH - ExactTarget Connector can solve the problems of marketers, and fill the gaps in existing tools.
3. Demo of Ektron - ExactTarget connector.
Webinar Video: https://www.youtube.com/watch?v=5h47CbfMXZw
Website: http://suyati.com/services/cms/ektron/Christmas 2015

Santa uses technology like unified desktop software, big data algorithms, and mobile apps to efficiently manage present production and delivery logistics in his workshop. This allows him to track naughty/nice statuses, present wishes, production workflows, and optimize Santa's delivery route, helping fulfill every child's wish on Christmas despite the massive scale of operations. While technology helps, the true Christmas miracle remains how Santa accomplishes this enormous task in just one night.
Viewers also liked (18)
Cloud Expo May 09 Richard Britton, Cloud Computing for SMEs

Cloud Expo May 09 Richard Britton, Cloud Computing for SMEs
Data on demand flexible archiving in a big content world

Data on demand flexible archiving in a big content world
High Performance Medical Reconstruction Using Stream Programming Paradigms

High Performance Medical Reconstruction Using Stream Programming Paradigms
Insperity Business Confidence Survey Q2 2015 [Infographic]![Insperity Business Confidence Survey Q2 2015 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Insperity Business Confidence Survey Q2 2015 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Insperity Business Confidence Survey Q2 2015 [Infographic]
iBOS Solution - Incessant Business Operations Suite 

iBOS Solution - Incessant Business Operations Suite
Call Management Services Should be Part of Every Business Telephone System

Call Management Services Should be Part of Every Business Telephone System
How marketers can leverage Ektron DXH's Exact Target for better client engage...

How marketers can leverage Ektron DXH's Exact Target for better client engage...
Similar to Infographic Protecting Patient Data
Cybersecurity

ybersecurity is an increasing
concern for many in the
medical cybersecurity and
information technology
professions. As computerized
devices in medical facilities
become increasingly networked
within their own walls and
with external facilities, the risk
of cyberattacks also increases,
threatening confidentiality,
safety, and well-being. This
article describes what health
care organizations and
imaging professionals should
do to minimize the risks.
Systems Thinking on a National Level, Part 2Drew David.docx

This document discusses various cybersecurity threats faced by the healthcare industry, including phishing emails, SQL injection attacks, eavesdropping, and viruses. Phishing emails are a major issue, accounting for 93% of breached healthcare data. Hackers use phishing emails that appear legitimate to trick staff into revealing sensitive information. The document also examines ways to better protect against these threats, such as password protection, data loss prevention, access controls, and staff training. Overall, the document analyzes the cybersecurity risks healthcare organizations face and ways to decrease breaches through education and prevention methods.
Privacy and Security by Design

Privacy and Security by Design Spotlight Presentation at HIMMS Privacy and Security Forum, December 5th 2016. Presented by Jeff R. Livingstone, PhD, Vice President and Global Lead, Life Sciences & Healthcare, Unisys Corporation.
Why healthcare is the biggest target for cyberattacks-converted.pdf

Sparity provides the Top Custom healthcare Software and Application development services for healthcare industries in USA and Across the Globe. We can help you build a leading-edge tech platform with the right UI/UX framework and functionalities. We Make a positive impact with modern healthcare services
Healthcare Cybercrime

Healthcare organizations will increasingly be targeted by cybercriminals in 2017, as hackers expand from health insurers to hospital networks, which can be more difficult to secure. Ransomware presents low-risk opportunities for attackers to obtain money from victims. This funding supports further research and development of more advanced attacks that may evade existing security systems. Proper security measures, contingency planning, and staff training are recommended to help organizations respond to emerging ransomware and other sophisticated cyber threats.
Digital Security 

This document discusses digital security and the importance of protecting personal information online. It defines digital security as electronic precautions to guarantee safety and protect digital identities. Examples of security measures include home alarm systems that notify of dangers and technology firewalls and Wi-Fi protections. Statistics show data breaches are common, with 43% of companies experiencing one in the past year, costing the global and US economies billions. The document urges vigilance in protecting personal information and provides tips to prevent security breaches like using unique passwords and antivirus software.
Digital security

This document discusses digital security and the importance of protecting personal information online. It defines digital security as electronic precautions to guarantee safety and protect digital identities. Examples of security measures include home alarm systems that notify of dangers and technology firewalls and Wi-Fi protections. Statistics show data breaches are common, with 43% of companies experiencing one in the past year, costing the global economy hundreds of billions annually. The document urges readers to take security seriously by using different passwords, antivirus software, and avoiding public Wi-Fi to prevent hacking and protect themselves from financial losses.
Cyber security threats and its solutions

There are a lot of cyber threats in the cyber world, but some of them are really disastrous for your system and data. Cyber threats are increasing rapidly so it is important to know how to prevent them.
Cyber Security Intelligence

This document summarizes a research paper on cyber security intelligence. It discusses the growth of cybercrimes and how the internet is insecure for transmitting confidential information. Various cyber attack methods in India and worldwide are presented. The document also examines cyber security technologies, issues, and challenges. It provides details on cyber defamation law, the evolution of cyber security, and the importance of managing cyber security risks.
How Vulnerable Is Your Industry to Cyber Crime?

The truth is that any company harboring sensitive customer information could become the target of a sophisticated cyber criminal. That being said, there are certainly industries that are more vulnerable to attacks. Let’s take a closer look at four of the most vulnerable industries—financial services, healthcare, insurance and retail.
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Ransomware was the top security threat in healthcare in 2016, accounting for 72% of malware attacks. Insiders and advanced persistent threats were also significant risks. Mobile devices posed a threat as 68% of healthcare breaches were due to lost or stolen devices. While cyberattacks were a leading cause of breaches, employee negligence through actions like clicking phishing emails or using infected USB devices also contributed to 91% of incidents starting with a phishing attack. Ransomware demands, lost productivity from downtime, and costs per leaked record added up to huge financial impacts for healthcare organizations from these top 5 security threats.
mHealth Security: Stats and Solutions

While mobile devices have improved efficiency and patient engagement while lowering costs, they’ve dramatically increased security risks. How can mHealth be safely implemented? View this slide show and learn:
• How mHealth increases security risks
• Where the greatest vulnerabilities lie
• How to improve mHealth security
mHealth Security: Stats and Solutions

While mobile devices have improved efficiency and patient engagement while lowering costs, they’ve dramatically increased security risks. How can mHealth be safely implemented? View this slide show and learn:
• How mHealth increases security risks
• Where the greatest vulnerabilities lie
• How to improve mHealth security
Cybercrime and the Healthcare Industry

This white paper discusses the various cyber threats targeting healthcare organizations and the challenges security professionals face in securing access to protected health information.
Cybercrime and the Healthcare Industry

This white paper discusses the various cyber threats targeting healthcare organizations and the challenges security professionals face in securing access to protected health information.
CYBER SECURITY : NEED OF THE HOUR

The document discusses the need for cyber security. It notes that while information and communication technology has enabled transformation, the growth of digital infrastructure and data also increases vulnerabilities to cyber attacks and threats. Ensuring the confidentiality, integrity and availability of digital systems and data is important. The objectives of cyber security include understanding principles, risks, threats, measures to prevent harm, and creating awareness. Cyber security is crucial for protecting sensitive information in governments, businesses and organizations from hackers.
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...The Lifesciences Magazine
Ryan Witt, who is in charge of cyber threats in healthcare at Proofpoint, says that this is why U.S. hospital defenses have always been weak. Since attackers learned this, hospitals in the United States have been a top target. Cybercriminals continue to focus on U.S. health care, and hospital information security is always trying to catch up.Cybersecurity Challenges in the Healthcare Industry.pdf

The healthcare enterprise has gone through a virtual transformation in recent years, with digital health information and IoT devices turning into integral parts of affected personal care. While these technological improvements have revolutionized healthcare transport, they have also uncovered the enterprise to a myriad of cybersecurity challenges.
Hot Topics in Privacy and Security

PYA Principal Barry Mathis presented “Hot Topics in Privacy and Security,” at the Florida Hospital Association's 14th Annual Health Care Corporate Compliance Education Retreat.
The presentation explored:
• Changes in the privacy and security ecosystem.
• Emerging technology risks and hot topics.
• What happens to hacked data.
• How to best protect data.
Data security for healthcare industry

This document provides an overview of enterprise security solutions by Data Security for the healthcare industry. It discusses how healthcare information is in high demand by cybercriminals for various fraudulent activities. The top 5 healthcare security threats are identified as ransomware, insider threats, advanced persistent threats, mobile devices, and employee negligence. The solutions offered by Data Security to mitigate these threats include Seqrite endpoint security, unified threat management, mobile device management, and data loss prevention. It also provides an overview of QuickHeal, the parent company of Seqrite, outlining its global presence and brand recognition in the cybersecurity industry.
Similar to Infographic Protecting Patient Data (20)
Systems Thinking on a National Level, Part 2Drew David.docx

Systems Thinking on a National Level, Part 2Drew David.docx
Why healthcare is the biggest target for cyberattacks-converted.pdf

Why healthcare is the biggest target for cyberattacks-converted.pdf
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] 5 Security Threats in Healthcare Industry
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...
Cybersecurity Challenges in the Healthcare Industry.pdf

Cybersecurity Challenges in the Healthcare Industry.pdf
More from Fortinet
Fortinet's Secure SD-WAN: Gartner Peer Insights Reviews

Learn more: https://www.fortinet.com/blog/business-and-technology/our-customers-emphasize-the-value-of-fortigate-secure-sd-wan-in-.html
To meet the security demands of modern networks, Fortinet’s FortiGate Secure SD-WAN solution incorporates all of the security features organizations need to protect their distributed networks. It is application aware, offers single-pane-of-glass visibility and management, includes integrated advanced threat protection, improves cloud application performance, and reduces costs by leveraging multi-broadband connectivity.
FortiGate Secure SD-WAN has been well received by the industry, earning a “Recommended” rating from NSS labs and positive feedback from users on Gartner Peer Insights.
FortiClient Fabric Agent Trial

Fabric Agent, a key module within FortiClient, integrates endpoints with FortiGate and the Fortinet Security Fabric. It strengthens enterprise security through enhanced endpoint visibility, compliance control, vulnerability scanning, and automated response.
Why Partners Who Charge for Technical Assessments Have Higher Growth and Profit

The document discusses how charging for technical assessments leads to higher growth and profits for IT solution providers. It argues that solution providers in the top quartile of financial performance typically charge for assessments, even for new customers, while lower performers usually do not charge. Charging allows for higher quality assessments and identifies more value drivers for the customer. It also helps differentiate the solution provider and access higher-level decision makers. This positions the provider to pursue and win more deals with high value customers, defined as those seeking premium solutions. The typical pre-sales process of doing free assessments often fails to differentiate the provider sufficiently. By charging for assessments, it creates an exception in the customer's procurement process that gets the provider's proposal in front of senior
The What and Why of PBM and OML 

This document discusses operational maturity levels (OMLs) and predominant business models (PBMs) for solution provider companies. It finds that companies in the top quartile of financial performance have OMLs of 4 or 5, implementing best practices more effectively across strategy, marketing, sales, services and finance. PBMs are identified based on revenue mix, as this determines the appropriate benchmarks and best practices for a company. Higher OMLs are achieved by mastering traits across five functional areas. Understanding one's own PBM is critical for solution providers to improve performance by selecting the right benchmarks and best practices for their specific business model.
The Importance of Targeting your Customers - Cross Selling Execution

This document discusses the importance of targeting customers and cross-selling for IT solution providers. It states that top-performing solution providers carefully define their target customer profile so that all of their solutions can be consumed by those customers. They then focus on winning only customers that match the target profile. These solution providers also integrate cross-selling goals into sales compensation and do account planning to identify cross-selling opportunities, which are then incorporated into marketing and sales efforts. The primary impacts of this approach are aligning solutions to the target customer profile and targeting customers so they are increasingly similar in characteristics.
Fortinet Connected UTM

This document provides 4 tips for finding a quality unified threat management (UTM) security solution:
1. Look for independent lab testing to ensure the solution is proven effective at security.
2. Consider solutions that consolidate other functions like switching or email security to streamline management.
3. Look for solutions that are easy to manage with quick installation, recommended default settings, and low ongoing effort.
4. Consider market adoption and sales trends to find solutions that are proven successes in the real world.
Forrester Research on OT Cybersecurity

In the new digital economy, data – and what you do with that data – is the key to success. Consumers and employees alike now demand instant access to critical information that allows them to solve problems, make informed decisions, or conduct transactions. But that’s just the part of the data equation most of us can see.
To effectively compete in today’s digital market, and capitalize on the data being collected and processed, organizations need to be able to respond quickly to market shifts and consumer demands, fine tune production, realign resources, and manage infrastructure. Which is why nearly three-fourths of all organizations have begun to converge their information technology (IT) infrastructure with their traditionally isolated operational technology (OT) networks.
Fortinet Icon Library

Use our free icon library to add industry-relevant icons to your next cybersecurity presentation!
https://www.fortinet.com/resources/icon-library.html
Infographic: Bringing Your Cloud Visibility Back Into Focus

Like data center sprawl, virtualization sprawl occurs when the numbers, locations, and functions of virtual machines distributed across a network grow to the point that they can no longer be managed effectively.
Securing the Internet of Things 2017

Cyber criminals are actively targeting billions of IoT devices and are successfully ramping up efforts to turn the Internet of things into an Internet of Threats.
Infographic: Fortinet Q1 2017 Threat Landscape Report

Malicious ransomware like WannaCry spread rapidly across hundreds of organizations worldwide in Q1 2017, likely using automated tools to methodically scan the internet. The use of BYOD policies and mobile devices makes protecting against mobile malware more difficult as its prevalence rose in every region except the Middle East. Encrypted traffic increased significantly from Q4 2016 to Q1 2017, diminishing network visibility and control for defensive tools.
Protecting Higher Education Data

The proliferation of global network connectivity thanks to technological advances and a growing number of connected devices has had a number of positive impacts on today’s higher education institutions. From cloud services to the Internet of Things (IoT), students and faculty are now able to stay connected while outside the classroom or laboratories to improve learning and research.
More from Fortinet (12)
Fortinet's Secure SD-WAN: Gartner Peer Insights Reviews

Fortinet's Secure SD-WAN: Gartner Peer Insights Reviews
Why Partners Who Charge for Technical Assessments Have Higher Growth and Profit

Why Partners Who Charge for Technical Assessments Have Higher Growth and Profit
The Importance of Targeting your Customers - Cross Selling Execution

The Importance of Targeting your Customers - Cross Selling Execution
Infographic: Bringing Your Cloud Visibility Back Into Focus

Infographic: Bringing Your Cloud Visibility Back Into Focus
Infographic: Fortinet Q1 2017 Threat Landscape Report

Infographic: Fortinet Q1 2017 Threat Landscape Report
Recently uploaded
Friendly Massage in Ajman - Malayali Kerala Spa Ajman

At Malayali Kerala Spa Ajman, Full Service includes individualized care for every client. We specifically design each massage session for the individual needs of the client. Our therapists are always willing to adjust the treatments based on the client's instruction and feedback. This guarantees that every client receives the treatment they expect.
By offering a variety of massage services, our Ajman Spa Massage Center can tackle physical, mental, and emotional illnesses. In addition, efficient identification of specific health conditions and designing treatment plans accordingly can significantly enhance the quality of massaging.
At Malayali Kerala Spa Ajman, we firmly believe that everyone should have the option to experience top-quality massage services regularly. To achieve that goal we offer cheap massage services in Ajman.
If you are interested in experiencing transformative massage treatment at Malayali Kerala Spa Ajman, you can use our Ajman Massage Center WhatsApp Number to schedule your next massage session.
Contact @ +971 529818279
Visit @ https://malayalikeralaspaajman.com/
English Drug and Alcohol Commissioners June 2024.pptx

Presentation made by Mat Southwell to the Harm Reduction Working Group of the English Drug and Alcohol Commissioners. Discuss stimulants, OAMT, NSP coverage and community-led approach to DCRs. Focussing on active drug user perspectives and interests
一比一原版(UoA毕业证)昆士兰科技大学毕业证如何办理

UoA毕业证学历书【微信95270640】办文凭{昆士兰科技大学毕业证}Q微Q微信95270640UoA毕业证书成绩单/学历认证UoA Diploma未毕业、挂科怎么办?+QQ微信:Q微信95270640-大学Offer(申请大学)、成绩单(申请考研)、语言证书、在读证明、使馆公证、办真实留信网认证、真实大使馆认证、学历认证
办理国外昆士兰科技大学毕业证书 #成绩单改成绩 #教育部学历学位认证 #毕业证认证 #留服认证 #使馆认证(留学回国人员证明) #(证)等
真实教育部认证教育部存档中国教育部留学服务中心认证(即教育部留服认证)网站100%可查.
真实使馆认证(即留学人员回国证明)使馆存档可通过大使馆查询确认.
留信网认证国家专业人才认证中心颁发入库证书留信网永久存档可查.
昆士兰科技大学昆士兰科技大学毕业证文凭证书毕业证 #成绩单等全套材料从防伪到印刷从水印到钢印烫金跟学校原版100%相同.
国际留学归国服务中心:实体公司注册经营行业标杆精益求精!
国外毕业证学位证成绩单办理流程:
1客户提供办理昆士兰科技大学昆士兰科技大学毕业证文凭证书信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作昆士兰科技大学毕业证成绩单电子图;
3昆士兰科技大学毕业证成绩单电子版做好以后发送给您确认;
4昆士兰科技大学毕业证成绩单电子版您确认信息无误之后安排制作成品;
5昆士兰科技大学成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快递邮寄昆士兰科技大学昆士兰科技大学毕业证文凭证书)。闷不乐的样子父亲特意带山娃去找三楼房东家的儿子小伍玩小伍比山娃小一岁虎头虎脑的很霸气父亲让山娃跟小伍去夏令营听课山娃很高兴夏令营就设在附近一所小学山娃发现那所小学比自己的学校更大更美操场上还铺有塑胶跑道呢里面很多小朋友一班一班的快快乐乐原来城里娃都藏这儿来了怪不得平时见不到他们山娃恍然大悟起来吹拉弹唱琴棋书画山娃都不懂却什么都想学山娃怨自己太笨什么都不会斟酌再三山娃终于选定了学美术当听说每月要交感
R3 Stem Cell Therapy: A New Hope for Women with Ovarian Failure

Discover the groundbreaking advancements in stem cell therapy by R3 Stem Cell, offering new hope for women with ovarian failure. This innovative treatment aims to restore ovarian function, improve fertility, and enhance overall well-being, revolutionizing reproductive health for women worldwide.
一比一原版(USF毕业证)旧金山大学毕业证如何办理

USF毕业证offer【微信95270640】《旧金山大学毕业证购买》《如何办理USF毕业证旧金山大学文凭学历》Q微信95270640实体公司,专业可靠,办理毕业证办美国成绩单,做加拿大文凭学历认证,办新西兰学位证,学位证书是什么?《制作旧金山大学毕业证多少钱》《USF学历证书丢了怎么办理》办澳洲文凭认证,办留信网认证(网上可查,实体公司,专业可靠)
专业为留学生办理旧金山大学旧金山大学硕士学位证成绩单【100%存档可查】留学全套申请材料办理。本公司承诺所有毕业证成绩单成品全部按照学校原版工艺对照一比一制作和学校一样的羊皮纸张保证您证书的质量!
如果你回国在学历认证方面有以下难题请联系我们我们将竭诚为你解决认证瓶颈
1所有材料真实但资料不全无法提供完全齐整的原件。【如:成绩单丶毕业证丶回国证明等材料中有遗失的。】
2获得真实的国外最终学历学位但国外本科学历就读经历存在问题或缺陷。【如:国外本科是教育部不承认的或者是联合办学项目教育部没有备案的或者外本科没有正常毕业的。】
3学分转移联合办学等情况复杂不知道怎么整理材料的。时间紧迫自己不清楚递交流程的。
如果你是以上情况之一请联系我们我们将在第一时间内给你免费咨询相关信息。我们将帮助你整理认证所需的各种材料.帮你解决国外学历认证难题。
国外旧金山大学旧金山大学硕士学位证成绩单办理方法:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询旧金山大学旧金山大学硕士学位证成绩单);
2开始安排制作旧金山大学毕业证成绩单电子图;
3旧金山大学毕业证成绩单电子版做好以后发送给您确认;
4旧金山大学毕业证成绩单电子版您确认信息无误之后安排制作成品;
5旧金山大学成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。头贼脑的倒也逗人喜爱日上三竿时山娃总爱窜进自家瓜棚里跟小伙伴们坐着聊天聊着聊着便忍不住往瓜田里逡巡一番抱起一只硕大的西瓜用石刀劈开抑或用拳头砸开每人抱起一大块就啃啃得满嘴满脸猴屁股般的红艳大家一个劲地指着对方吃吃地笑瓜裂得古怪奇形怪状却丝毫不影响瓜味甜丝丝的满嘴生津遍地都是瓜横七竖八的活像掷满了一地的大石块摘走二三只爷爷是断然发现不了的即便发现爷爷也不恼反而教山娃辨认孰熟孰嫩孰甜孰淡名义上是护瓜吃
Management of Post Operative Pain: to make doctors conscious about the benefi...

Multimodal analgesia.
NURSING MANAGEMENT OF PATIENT WITH EMPHYSEMA .PPT

Prepared by Prof. BLESSY THOMAS, VICE PRINCIPAL, FNCON, SPN.
Emphysema is a disease condition of respiratory system.
Emphysema is an abnormal permanent enlargement of the air spaces distal to terminal bronchioles, accompanied by destruction of their walls and without obvious fibrosis.
Emphysema of lung is defined as hyper inflation of the lung ais spaces due to obstruction of non respiratory bronchioles as due to loss of elasticity of alveoli.
It is a type of chronic obstructive
pulmonary disease.
It is a progressive disease of lungs.
Innovative Minds France's Most Impactful Healthcare Leaders.pdf

This edition features a handful of Innovative Minds: France's Most Impactful Healthcare Leaders that are leading us into a better future.
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - ...

TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - ...rightmanforbloodline
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - 34.
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - 34.
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - 34.FACIAL NERVE

The facial nerve, also known as cranial nerve VII, is one of the 12 cranial nerves originating from the brain. It's a mixed nerve, meaning it contains both sensory and motor fibres, and it plays a crucial role in controlling various facial muscles, as well as conveying sensory information from the taste buds on the anterior two-thirds of the tongue.
PrudentRx: A Resource for Patient Education and Engagement

PrudentRx enhances healthcare by educating patients and ensuring effective medication management in a complex, evolving landscape.
Sexual Disorders.gender identity disorderspptx

Gender identity disorder, paraphilias , sexual dysfunction
Pneumothorax and role of Physiotherapy in it.

This particular slides consist of- what is Pneumothorax,what are it's causes and it's effect on body, risk factors, symptoms,complications, diagnosis and role of physiotherapy in it.
This slide is very helpful for physiotherapy students and also for other medical and healthcare students.
Here is a summary of Pneumothorax:
Pneumothorax, also known as a collapsed lung, is a condition that occurs when air leaks into the space between the lung and chest wall. This air buildup puts pressure on the lung, preventing it from expanding fully when you breathe. A pneumothorax can cause a complete or partial collapse of the lung.
Data-Driven Dispensing- Rise of AI in Pharmacies.pdf

Imagine AI making your pharmacy experience smoother, safer, and more personalized.
U Part Wigs_ A Natural Look with Minimal Effort Jokerwigs.in.pdf

Joker Wigs has been a one-stop-shop for hair products for over 26 years. We provide high-quality hair wigs, hair extensions, hair toppers, hair patch, and more for both men and women.
Fit to Fly PCR Covid Testing at our Clinic Near You

A Fit-to-Fly PCR Test is a crucial service for travelers needing to meet the entry requirements of various countries or airlines. This test involves a polymerase chain reaction (PCR) test for COVID-19, which is considered the gold standard for detecting active infections. At our travel clinic in Leeds, we offer fast and reliable Fit to Fly PCR testing, providing you with an official certificate verifying your negative COVID-19 status. Our process is designed for convenience and accuracy, with quick turnaround times to ensure you receive your results and certificate in time for your departure. Trust our professional and experienced medical team to help you travel safely and compliantly, giving you peace of mind for your journey.www.nxhealthcare.co.uk
Michigan HealthTech Market Map 2024 with Policy Makers, Academic Innovation C...

Michigan HealthTech Market Map 2024. Includes 7 categories: Policy Makers, Academic Innovation Centers, Digital Health Providers, Healthcare Providers, Payers / Insurance, Device Companies, Life Science Companies, Innovation Accelerators. Developed by the Michigan-Israel Business Accelerator
Recently uploaded (20)
Friendly Massage in Ajman - Malayali Kerala Spa Ajman

Friendly Massage in Ajman - Malayali Kerala Spa Ajman
English Drug and Alcohol Commissioners June 2024.pptx

English Drug and Alcohol Commissioners June 2024.pptx
R3 Stem Cell Therapy: A New Hope for Women with Ovarian Failure

R3 Stem Cell Therapy: A New Hope for Women with Ovarian Failure
Management of Post Operative Pain: to make doctors conscious about the benefi...

Management of Post Operative Pain: to make doctors conscious about the benefi...
Innovative Minds France's Most Impactful Healthcare Leaders.pdf

Innovative Minds France's Most Impactful Healthcare Leaders.pdf
TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - ...

TEST BANK FOR Health Assessment in Nursing 7th Edition by Weber Chapters 1 - ...
PrudentRx: A Resource for Patient Education and Engagement

PrudentRx: A Resource for Patient Education and Engagement
Data-Driven Dispensing- Rise of AI in Pharmacies.pdf

Data-Driven Dispensing- Rise of AI in Pharmacies.pdf
U Part Wigs_ A Natural Look with Minimal Effort Jokerwigs.in.pdf

U Part Wigs_ A Natural Look with Minimal Effort Jokerwigs.in.pdf
Fit to Fly PCR Covid Testing at our Clinic Near You

Fit to Fly PCR Covid Testing at our Clinic Near You
Michigan HealthTech Market Map 2024 with Policy Makers, Academic Innovation C...

Michigan HealthTech Market Map 2024 with Policy Makers, Academic Innovation C...
Infographic Protecting Patient Data
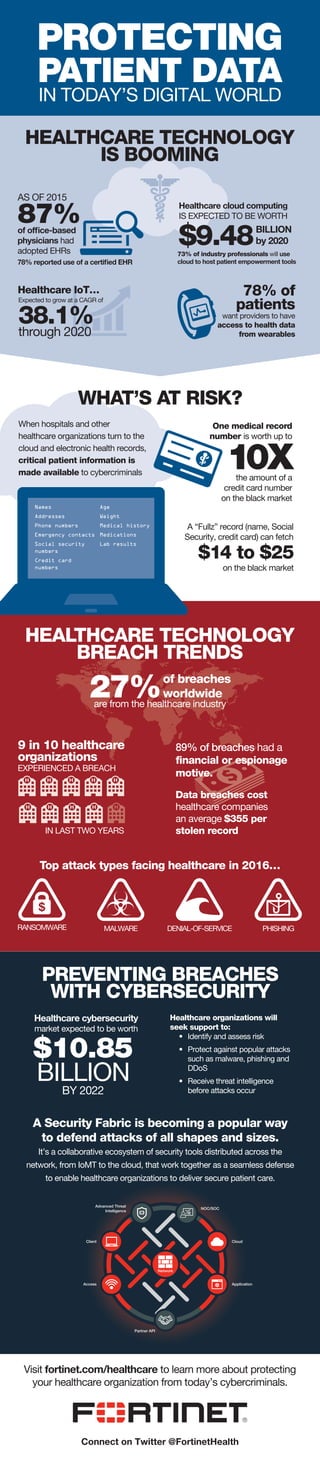
- 1. PROTECTING PATIENT DATA IN TODAY’S DIGITAL WORLD HEALTHCARE TECHNOLOGY IS BOOMING WHAT’S AT RISK? PREVENTING BREACHES WITH CYBERSECURITY HEALTHCARE TECHNOLOGY BREACH TRENDS When hospitals and other healthcare organizations turn to the cloud and electronic health records, critical patient information is made available to cybercriminals One medical record number is worth up to A “Fullz” record (name, Social Security, credit card) can fetch 89% of breaches had a financial or espionage motive. Top attack types facing healthcare in 2016… Data breaches cost healthcare companies an average $355 per stolen record Healthcare cybersecurity market expected to be worth Healthcare organizations will seek support to: • Identify and assess risk • Protect against popular attacks such as malware, phishing and DDoS • Receive threat intelligence before attacks occur A Security Fabric is becoming a popular way to defend attacks of all shapes and sizes. It’s a collaborative ecosystem of security tools distributed across the network, from IoMT to the cloud, that work together as a seamless defense to enable healthcare organizations to deliver secure patient care. Visit fortinet.com/healthcare to learn more about protecting your healthcare organization from today’s cybercriminals. AS OF 2015 87%of office-based physicians had adopted EHRs 78% reported use of a certified EHR Healthcare cloud computing IS EXPECTED TO BE WORTH BILLION by 2020 73% of industry professionals will use cloud to host patient empowerment tools $9.48 Healthcare IoT… Expected to grow at a CAGR of 38.1%through 2020 78% of patients want providers to have access to health data from wearables 10Xthe amount of a credit card number on the black market $14 to $25 on the black market Names Addresses Phone numbers Emergency contacts Social security numbers Credit card numbers Age Weight Medical history Medications Lab results 9 in 10 healthcare organizations EXPERIENCED A BREACH IN LAST TWO YEARS RANSOMWARE MALWARE DENIAL-OF-SERVICE PHISHING $10.85 BILLION BY 2022 NOC/SOC Cloud Partner API Access Client Advanced Threat Intelligence Application Network 27%are from the healthcare industry of breaches worldwide Connect on Twitter @FortinetHealth
