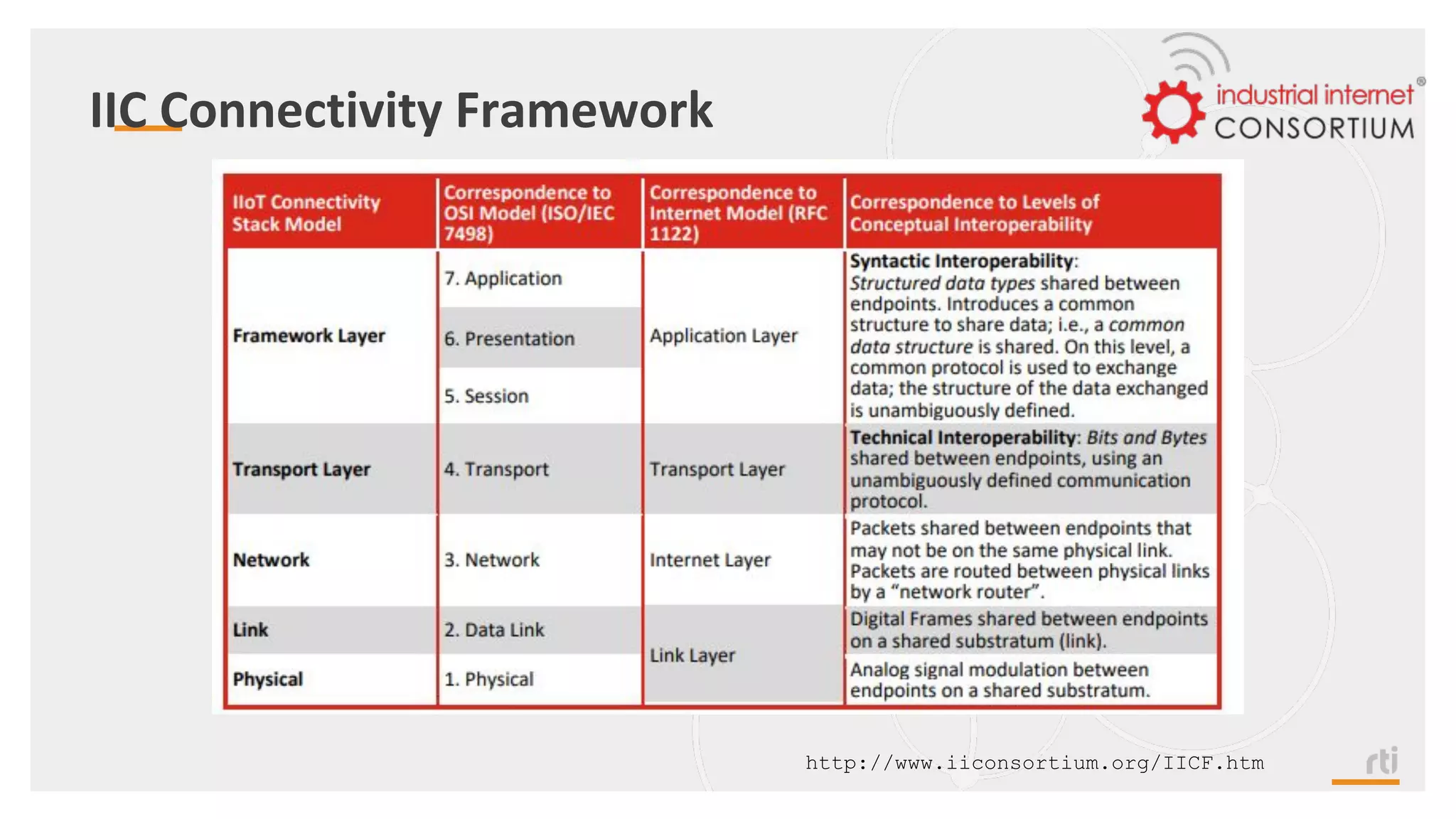
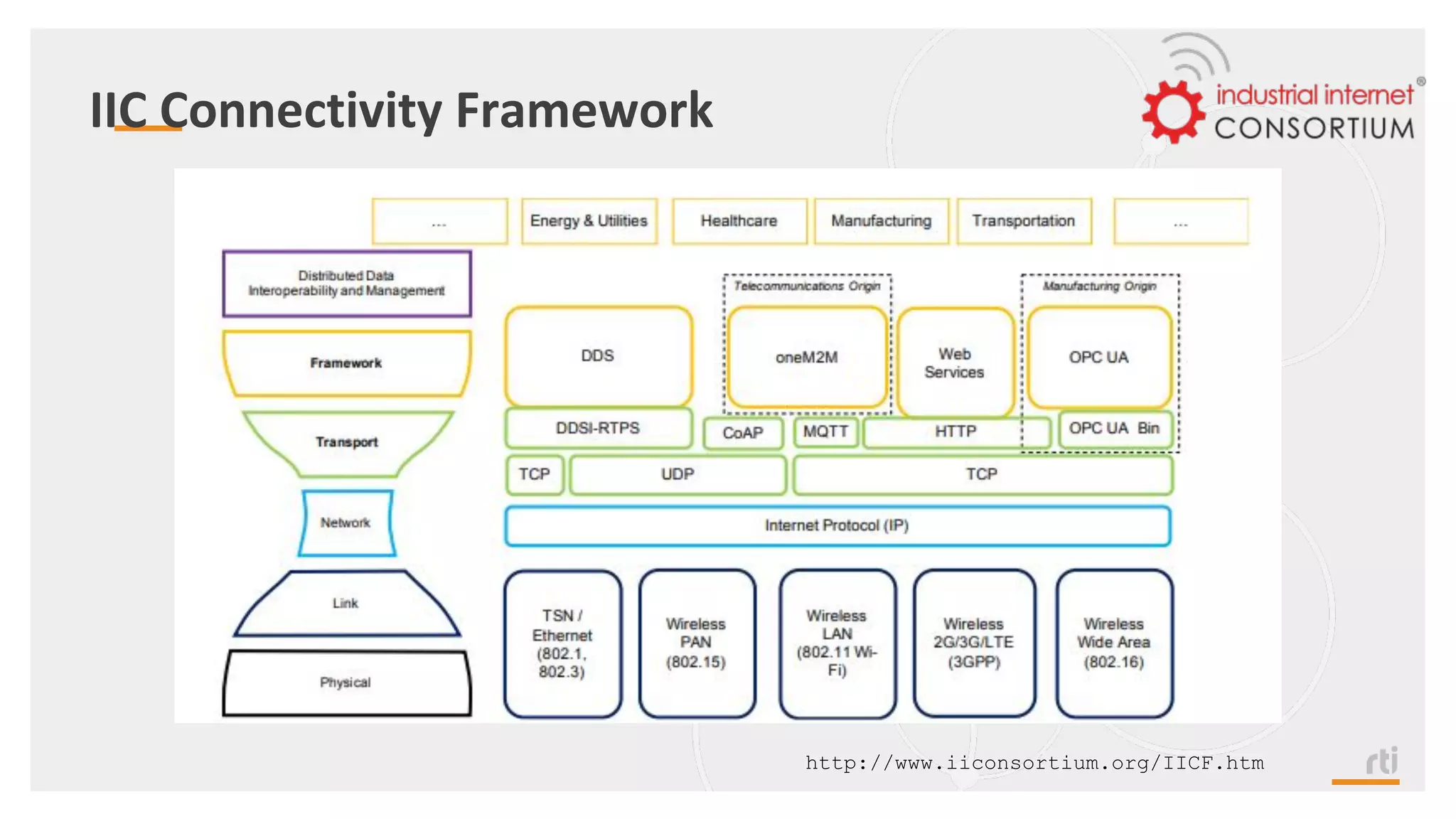
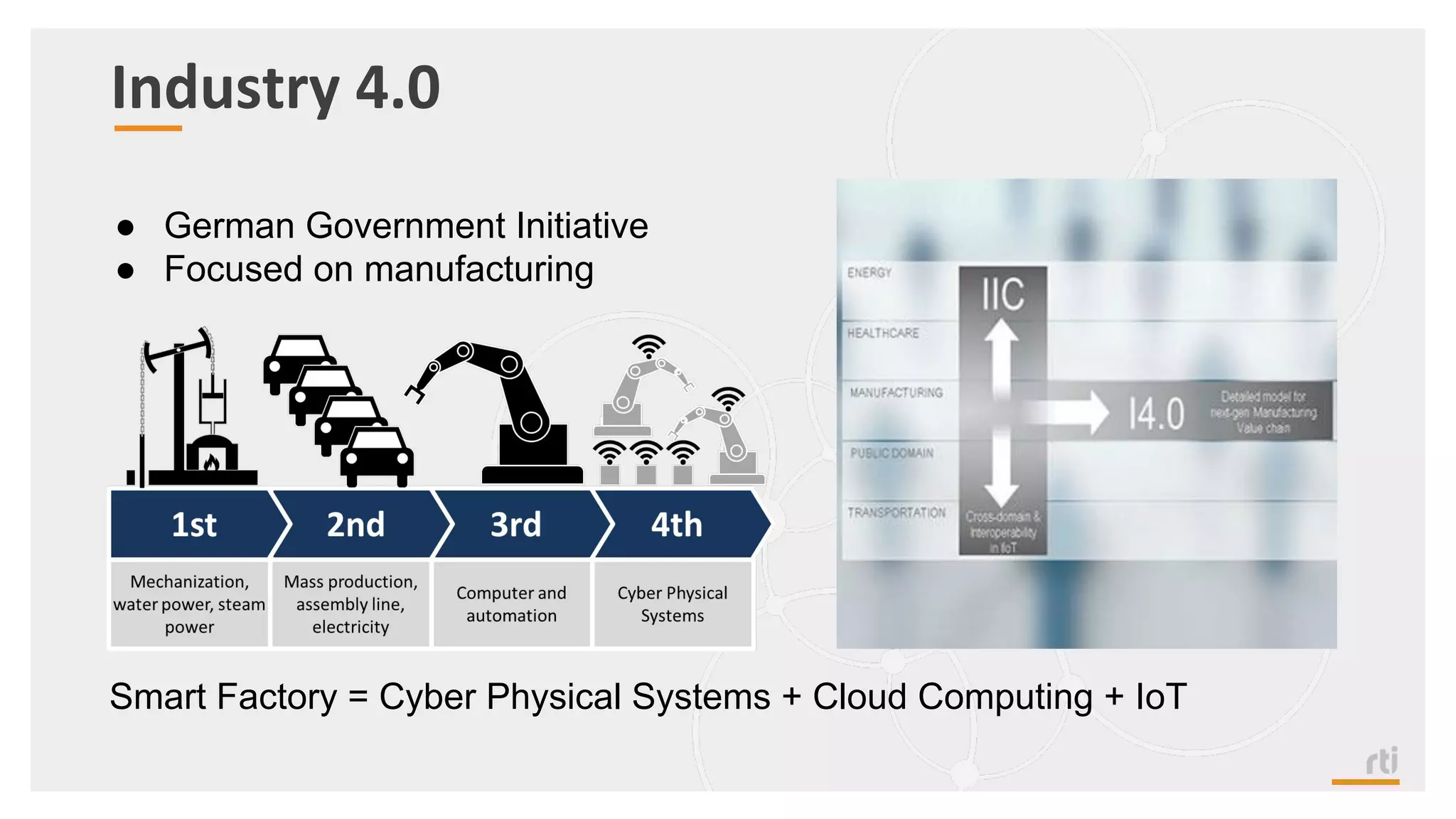
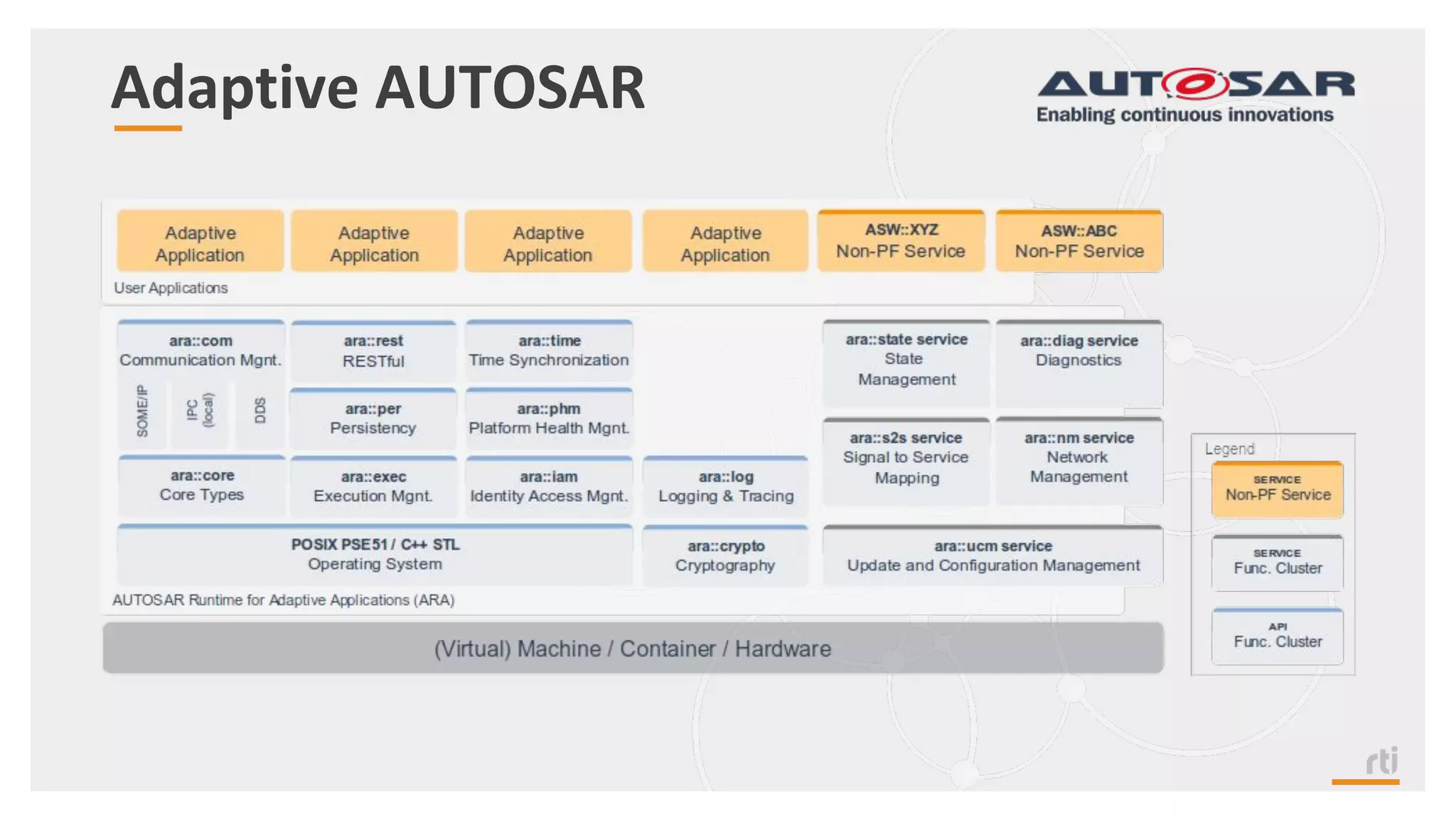
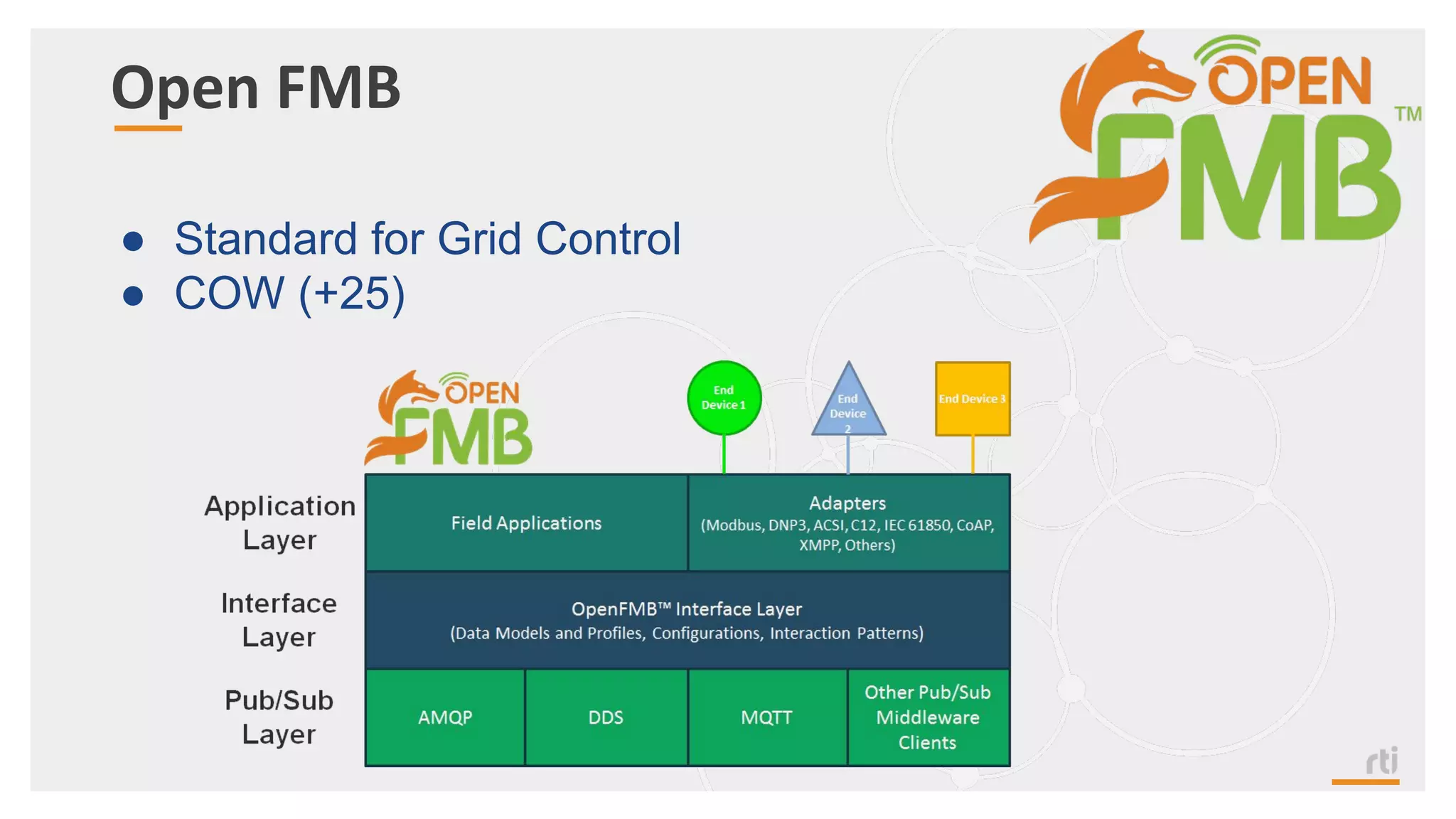
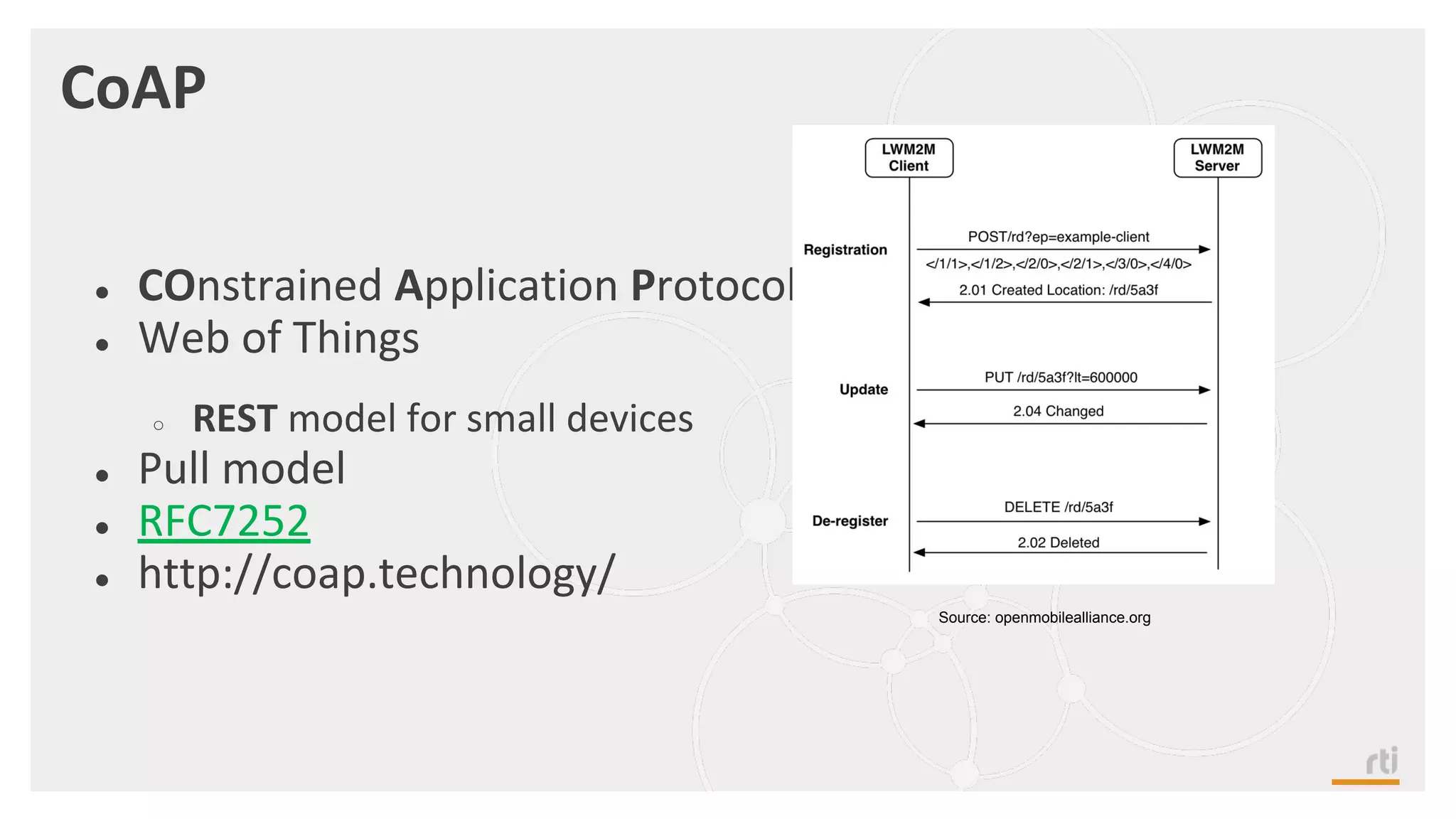
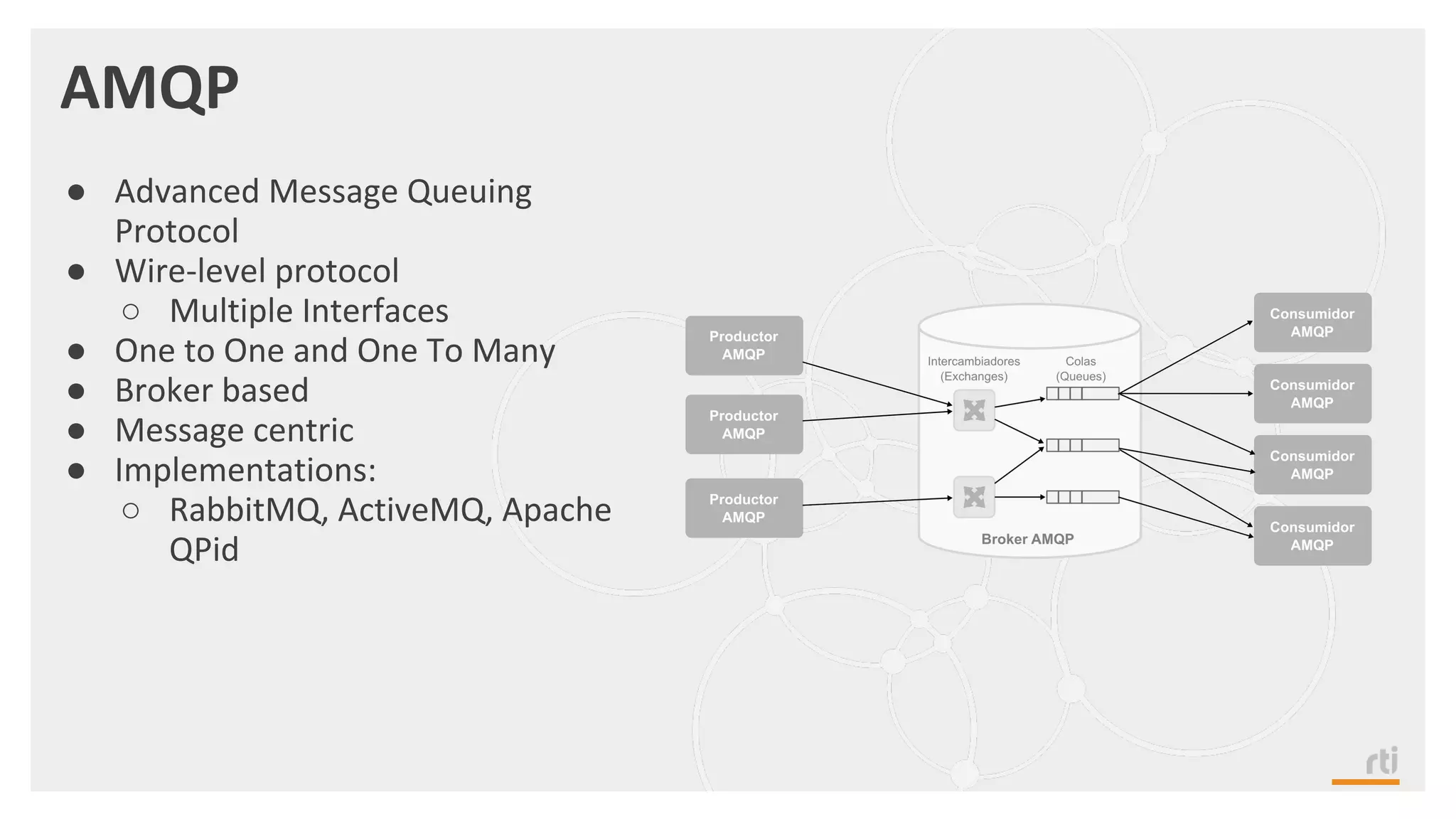
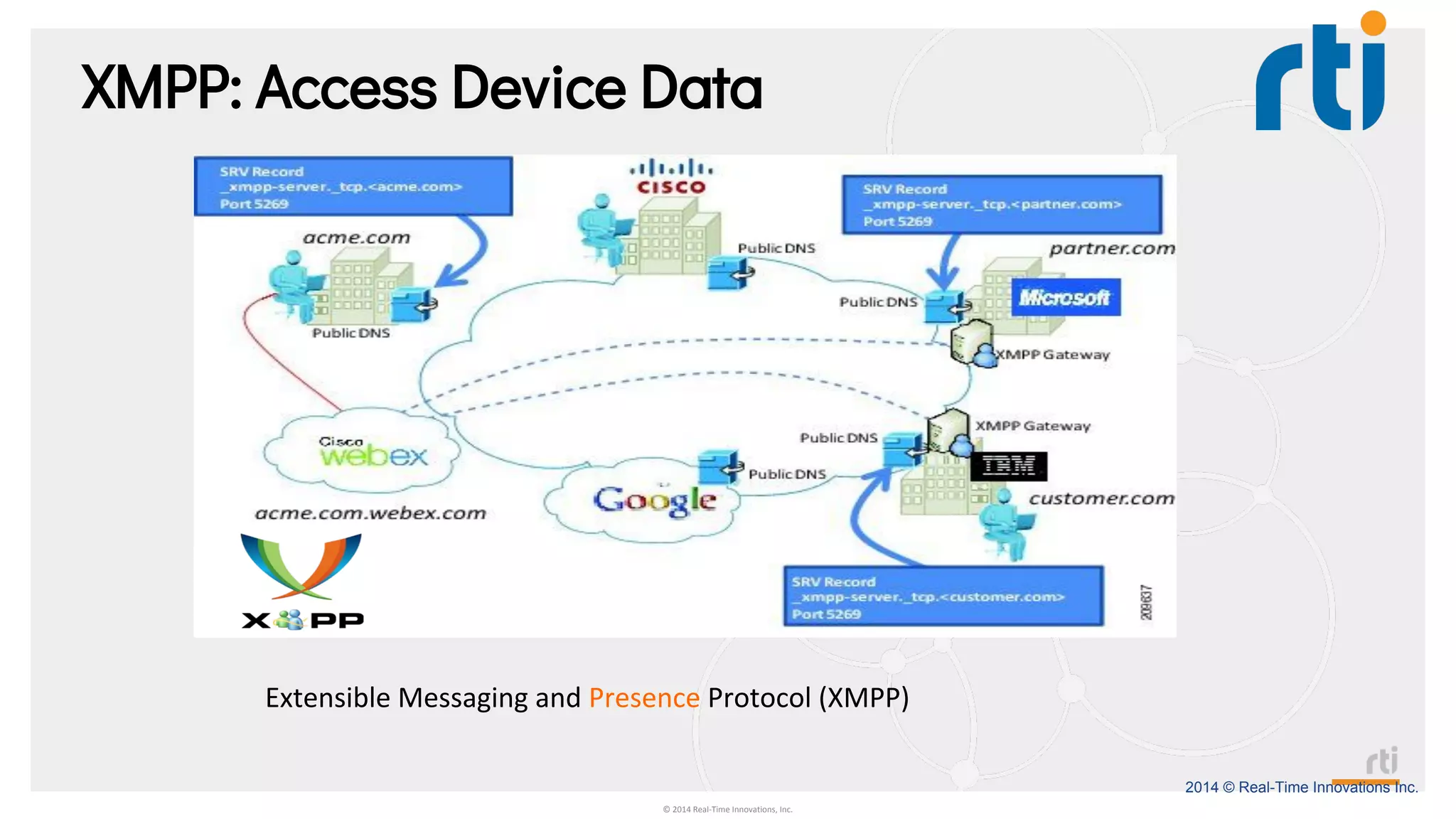
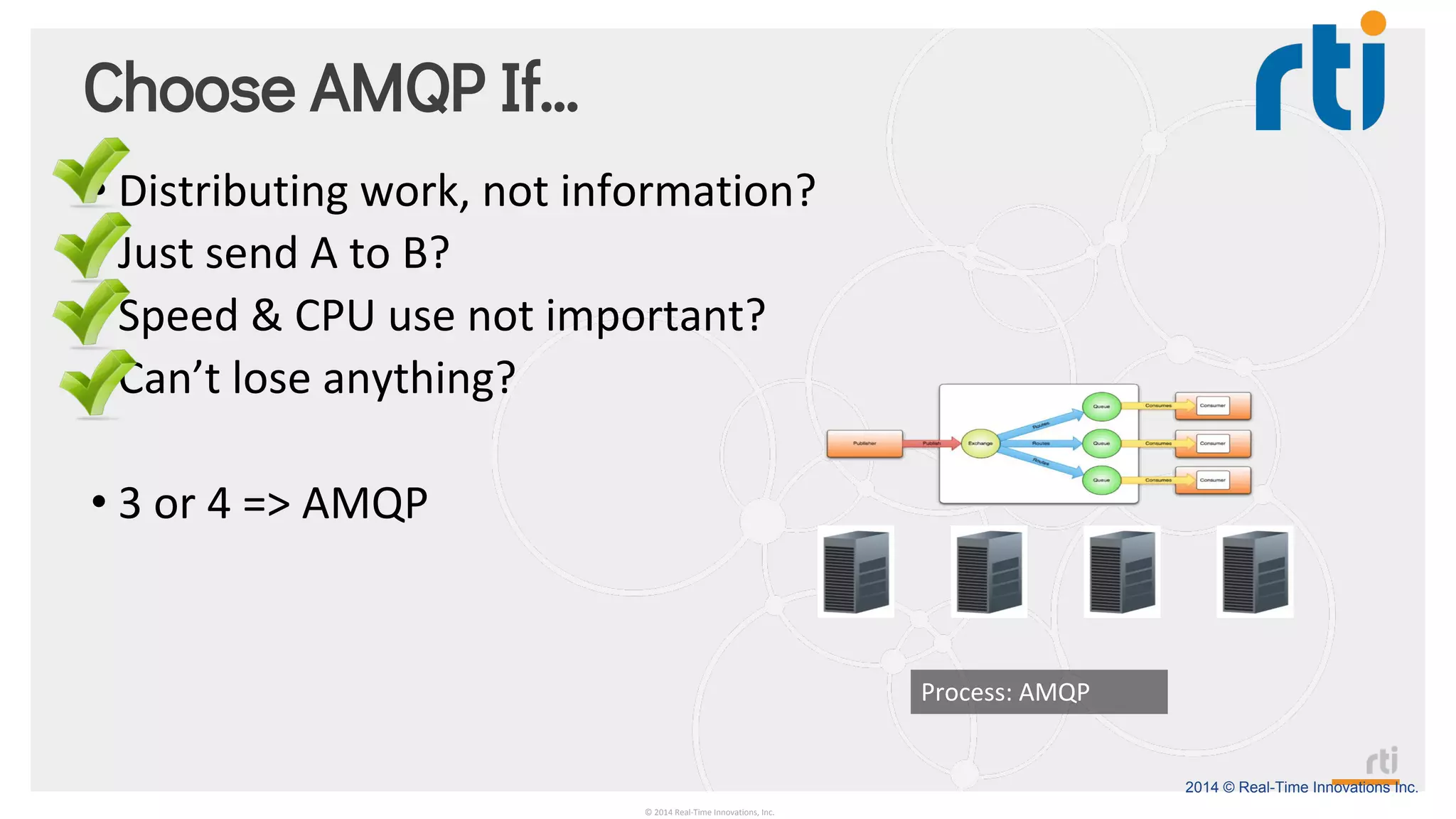
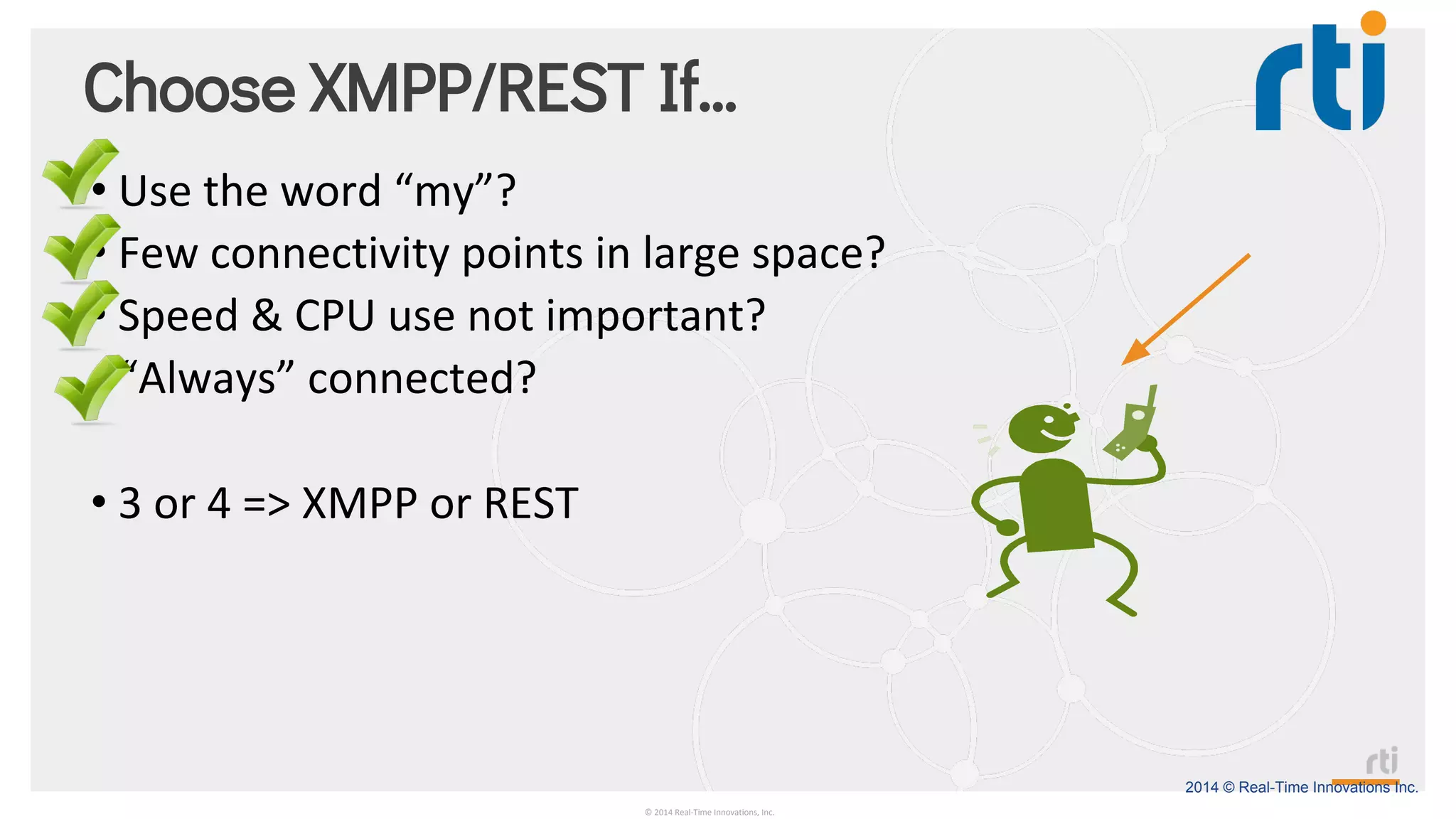
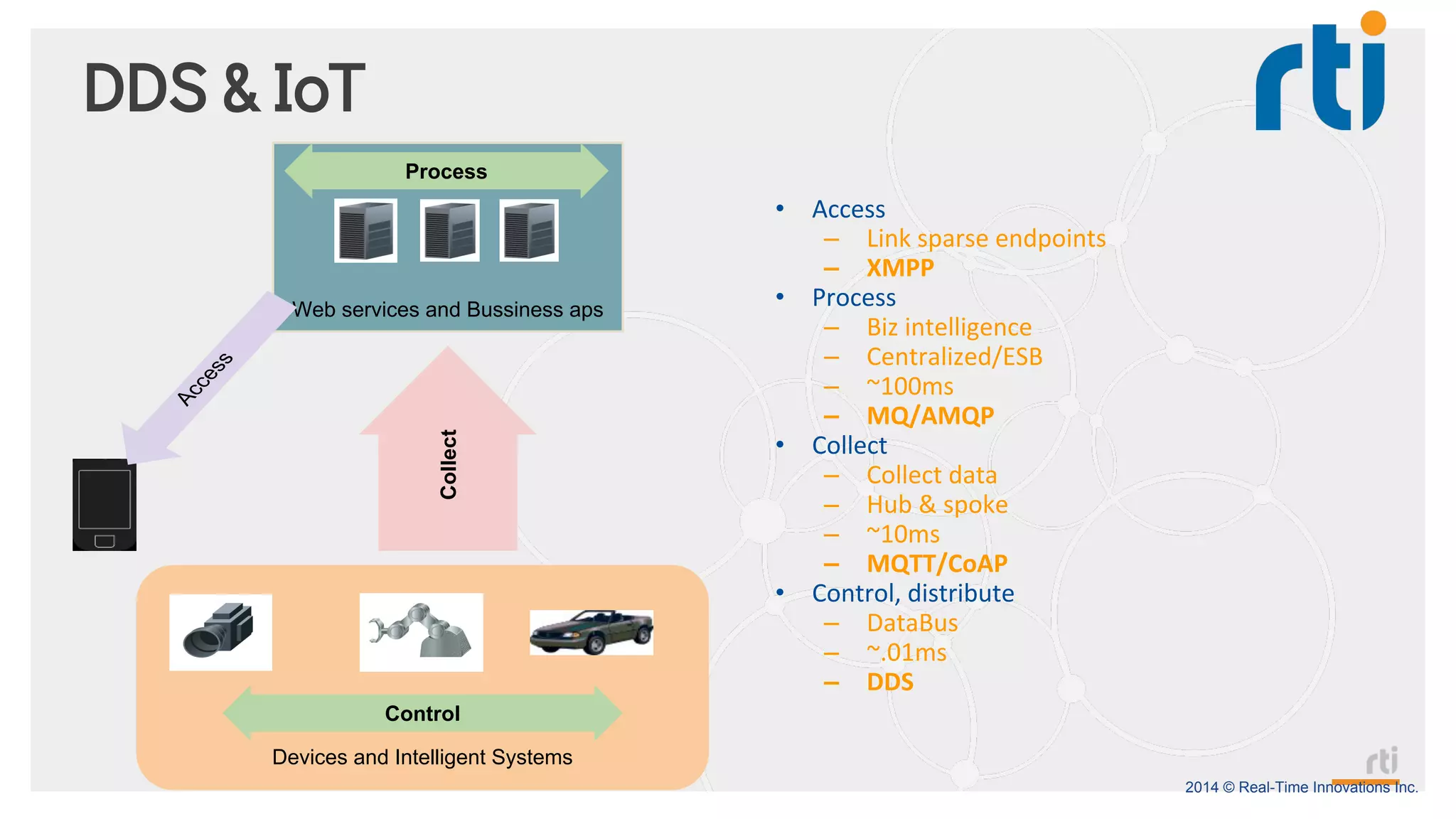
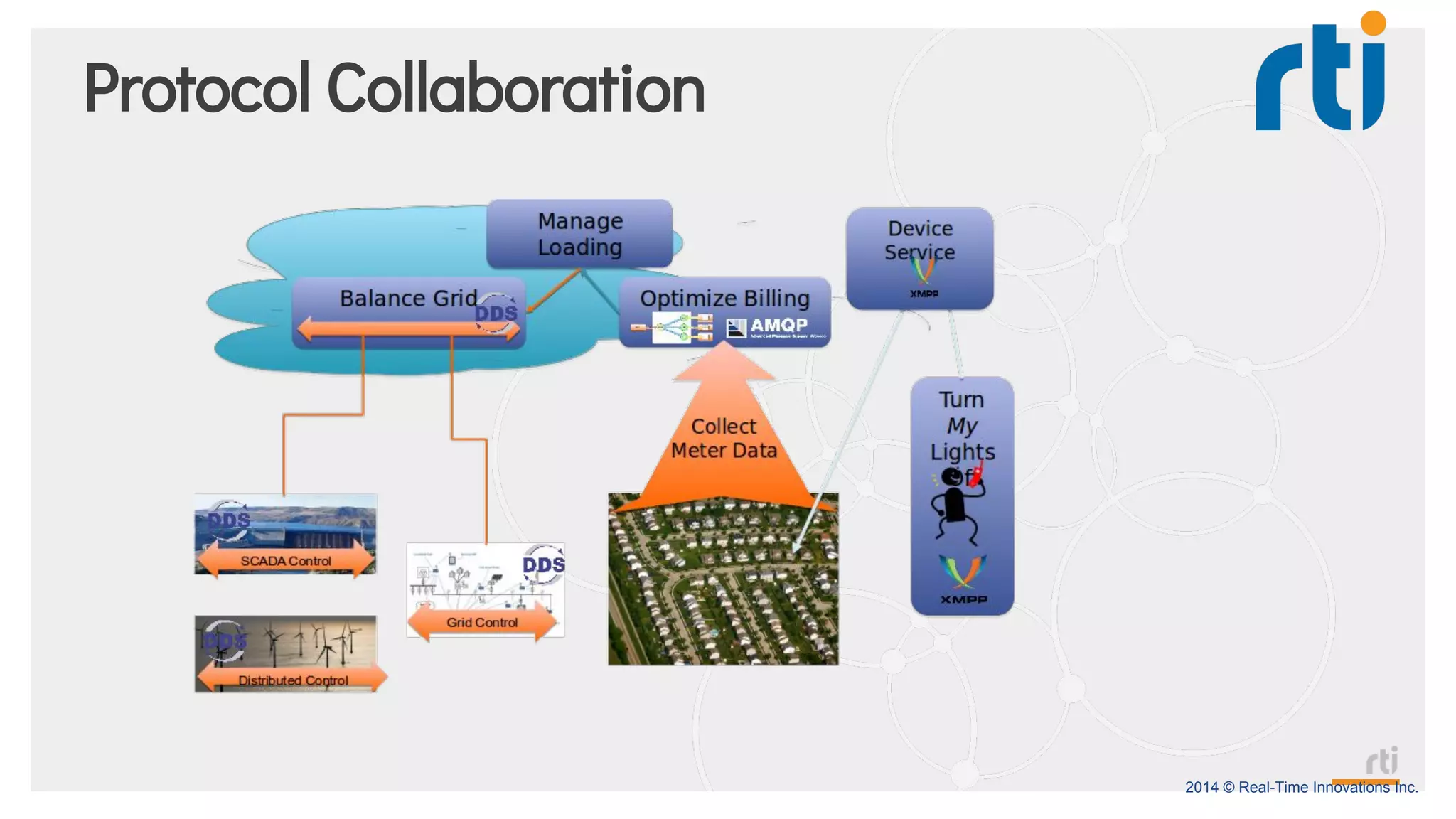
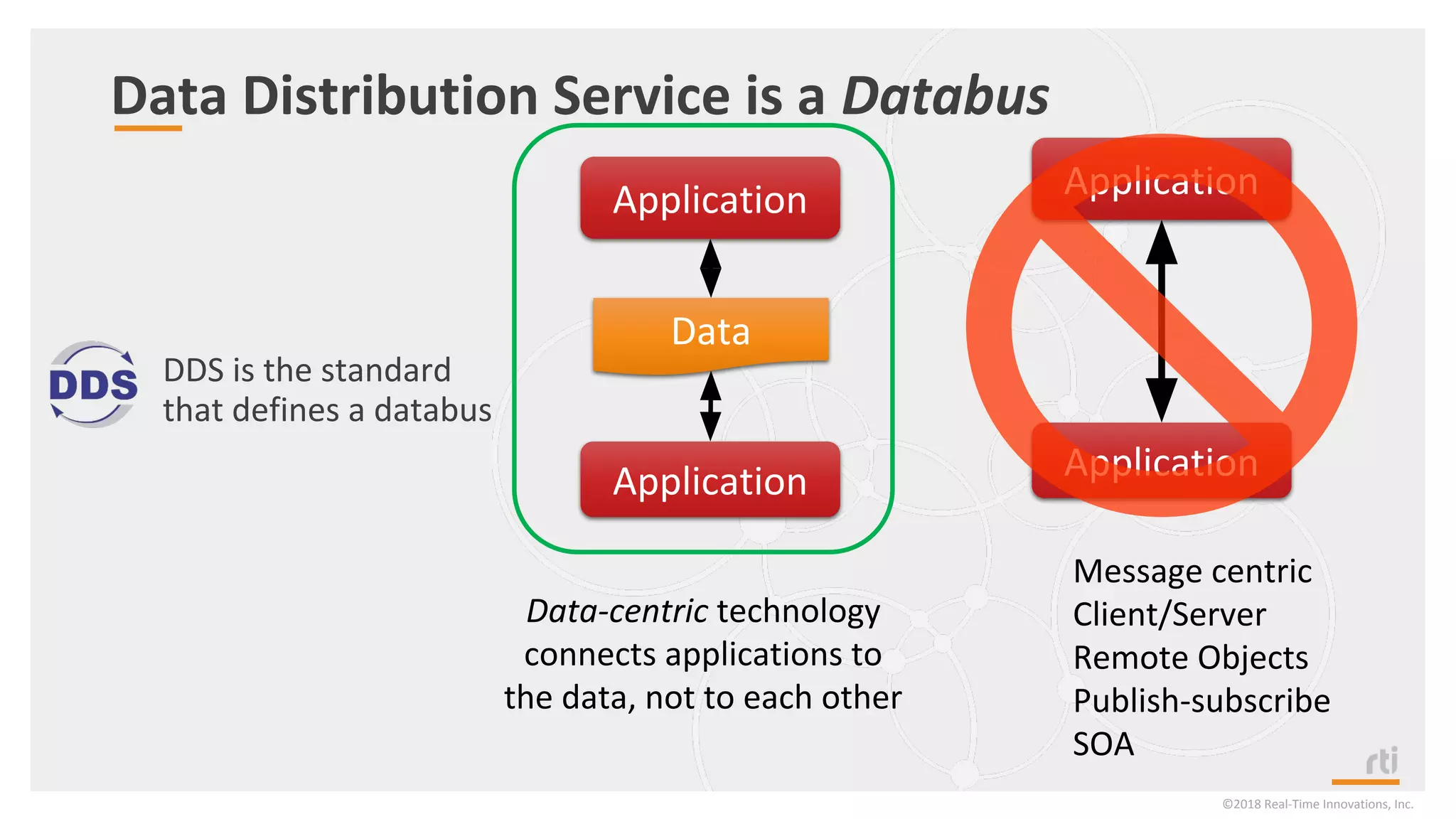
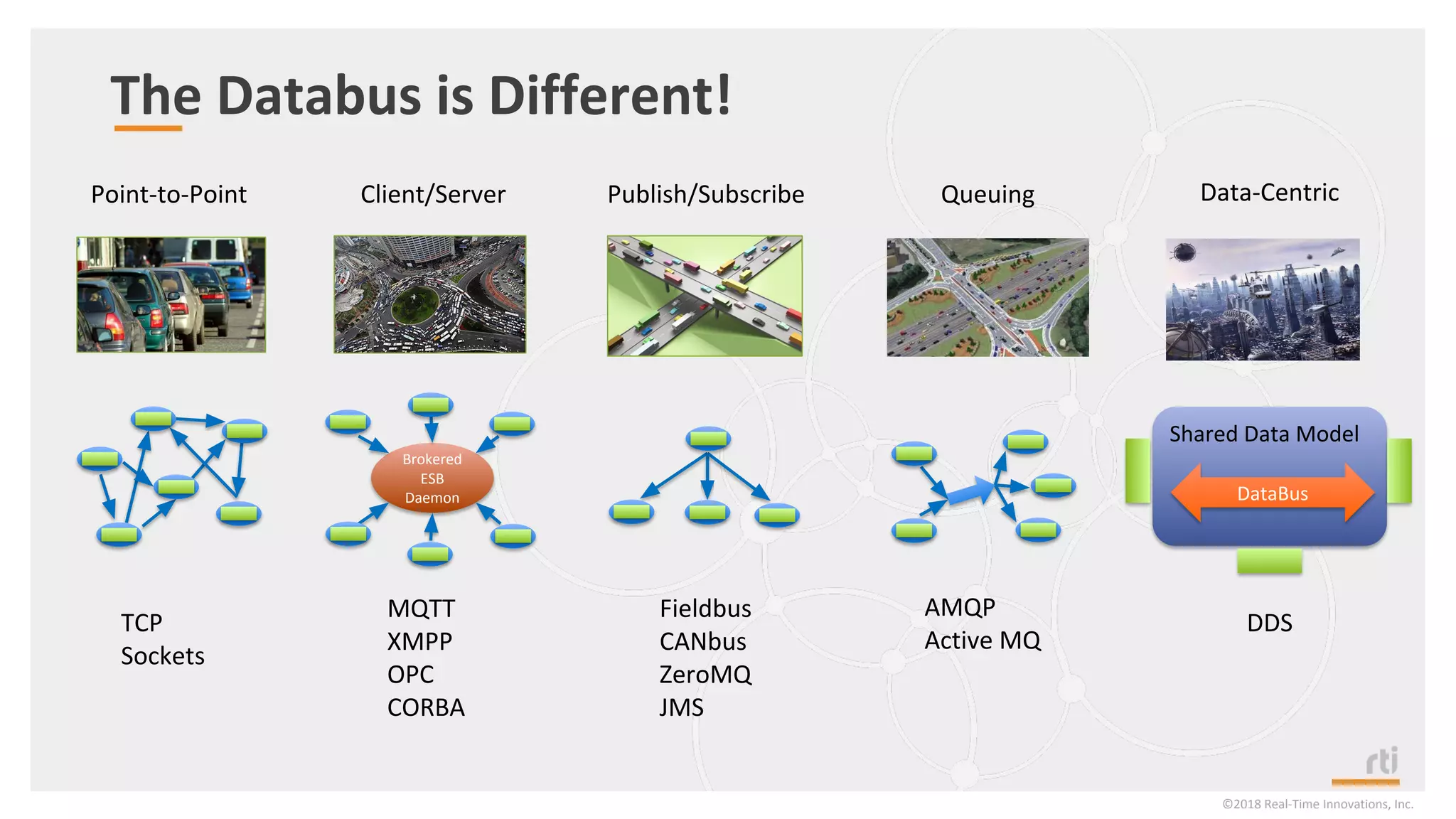
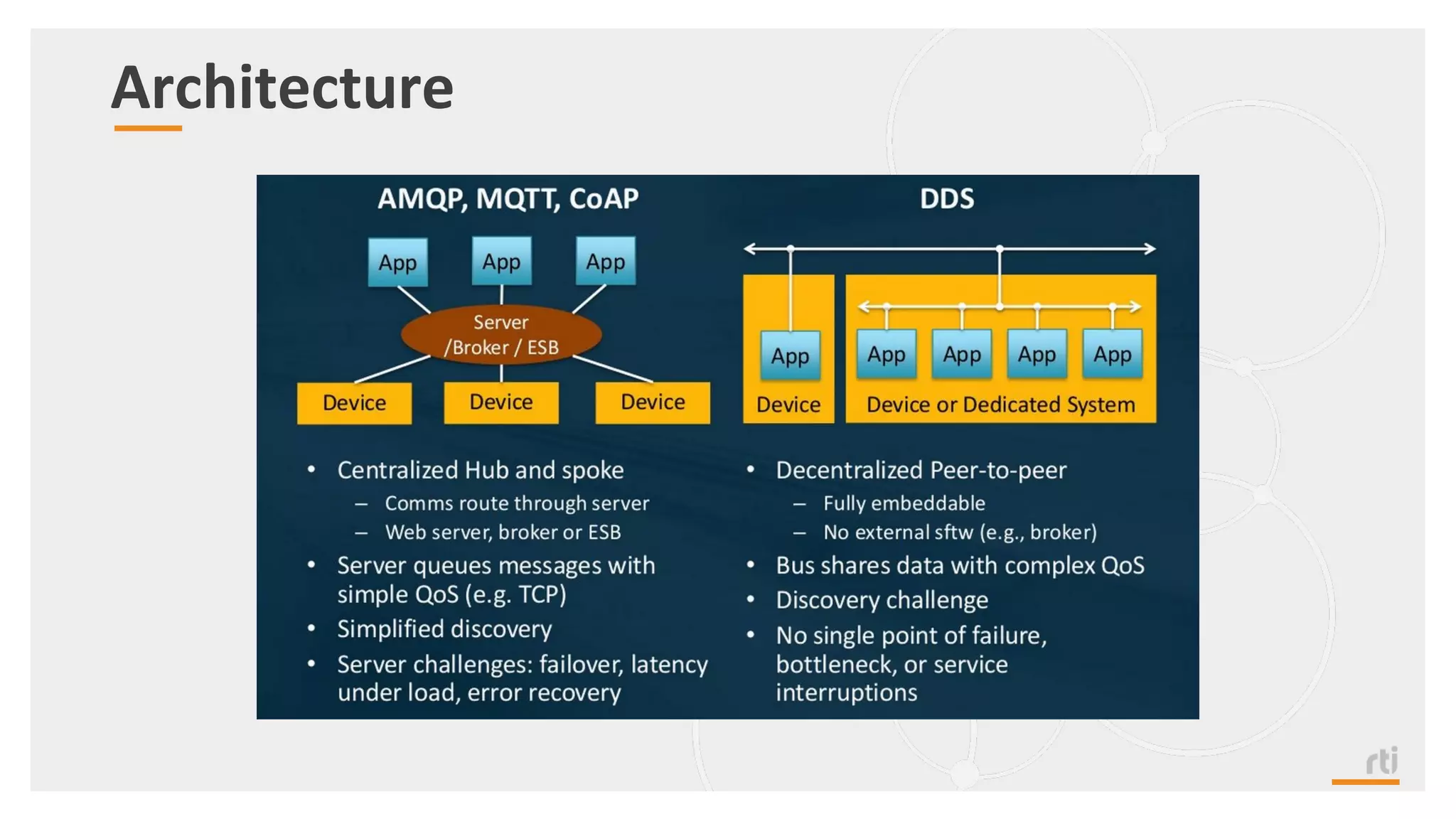
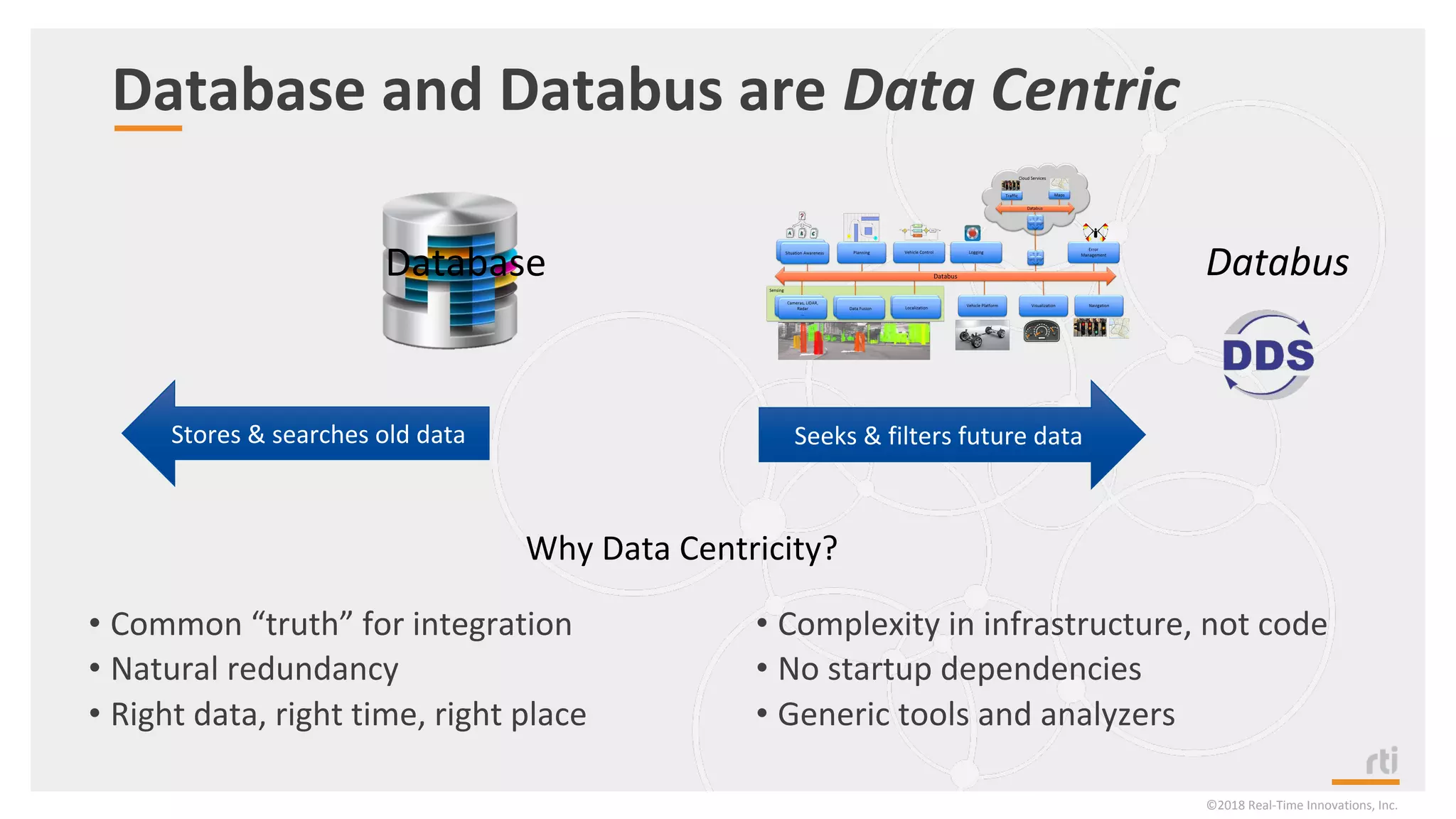
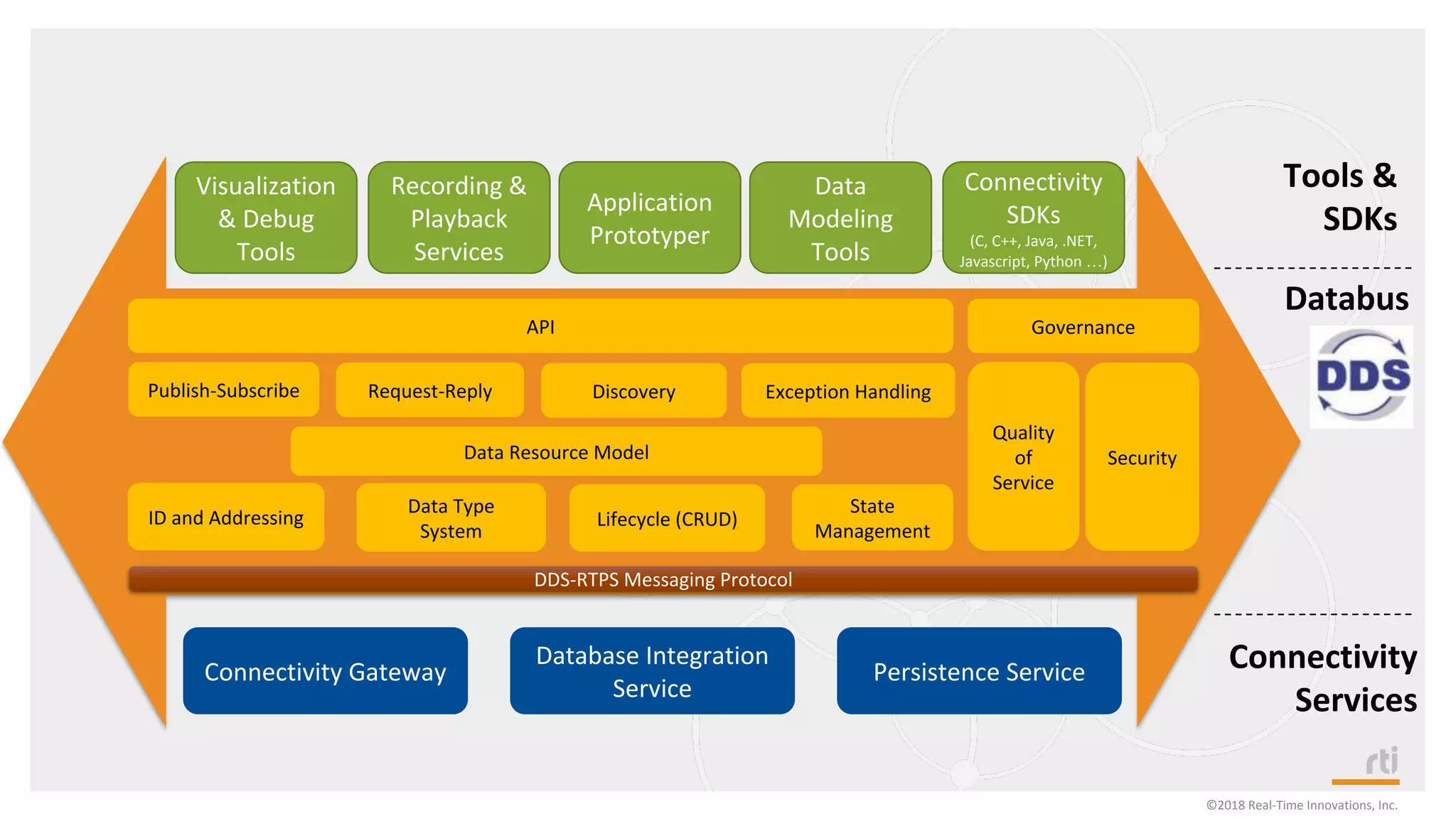
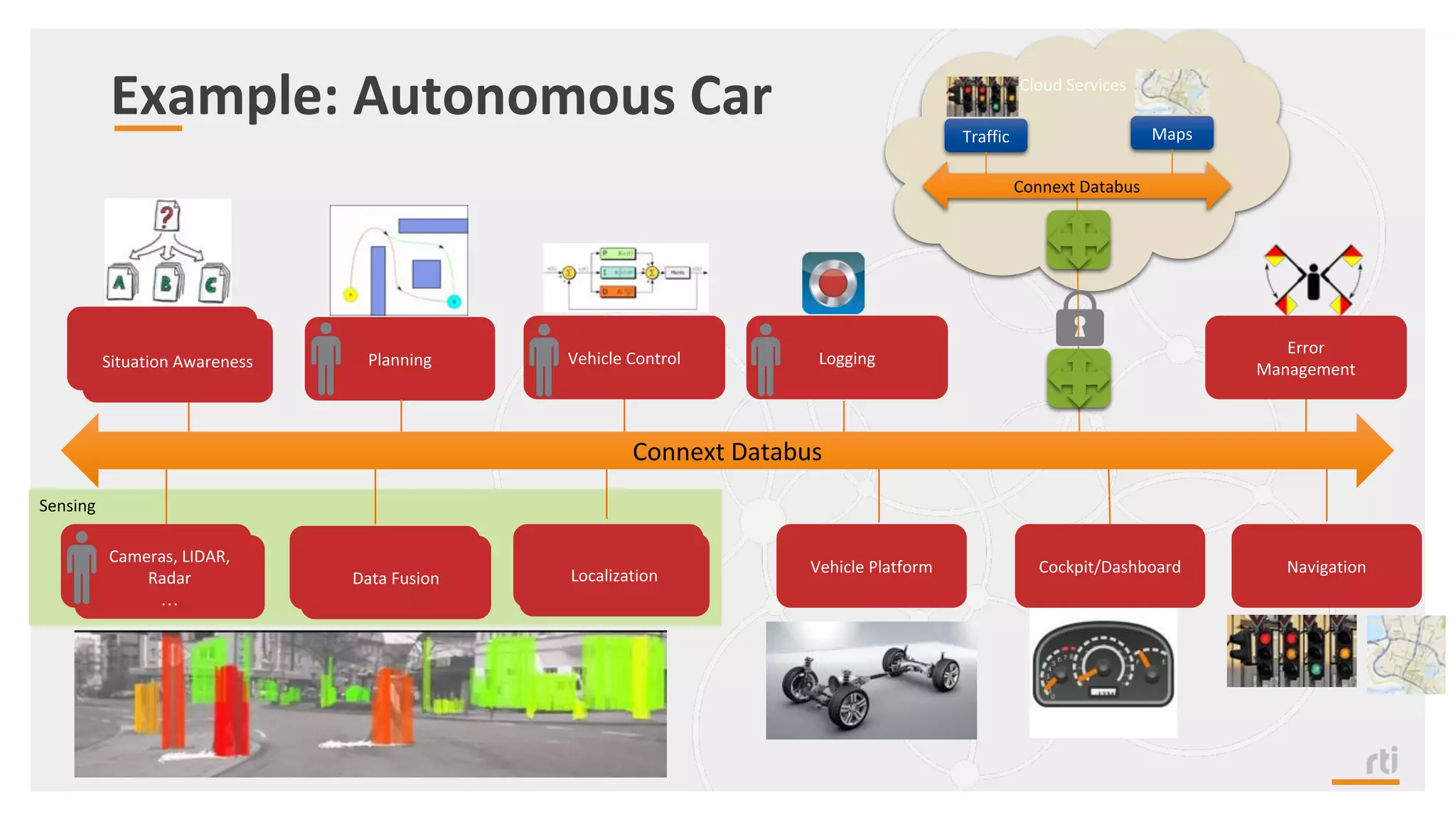
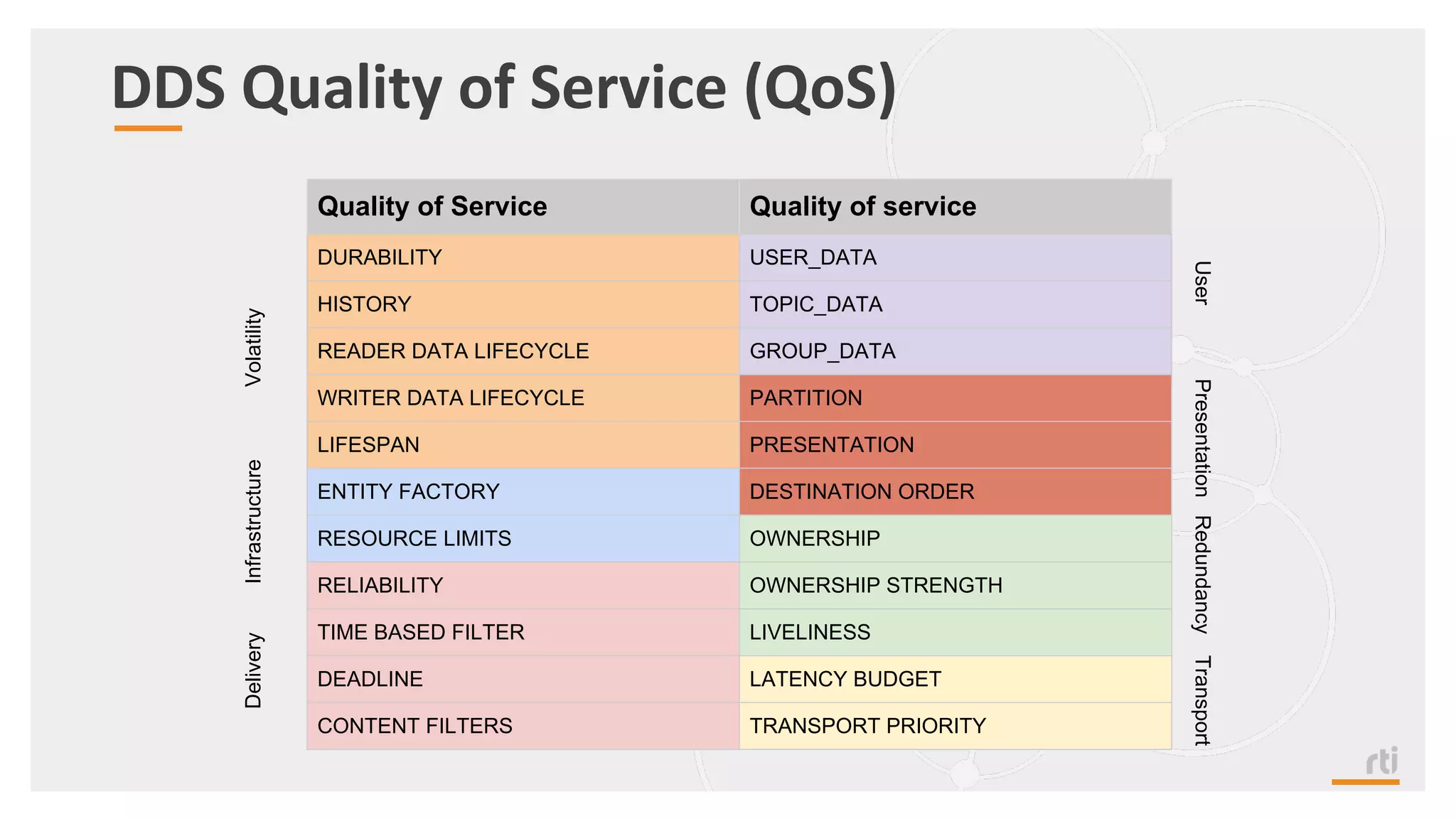
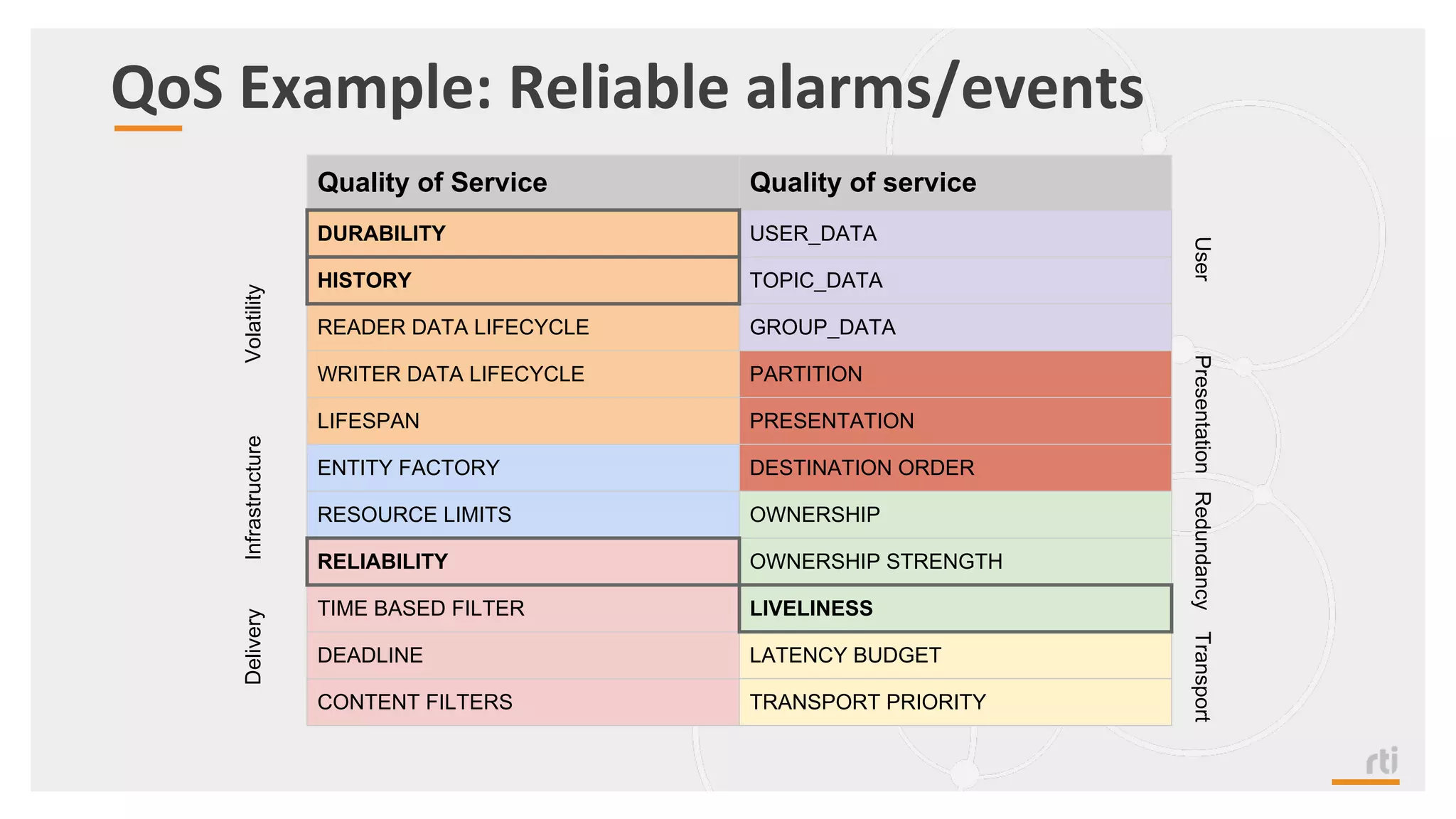
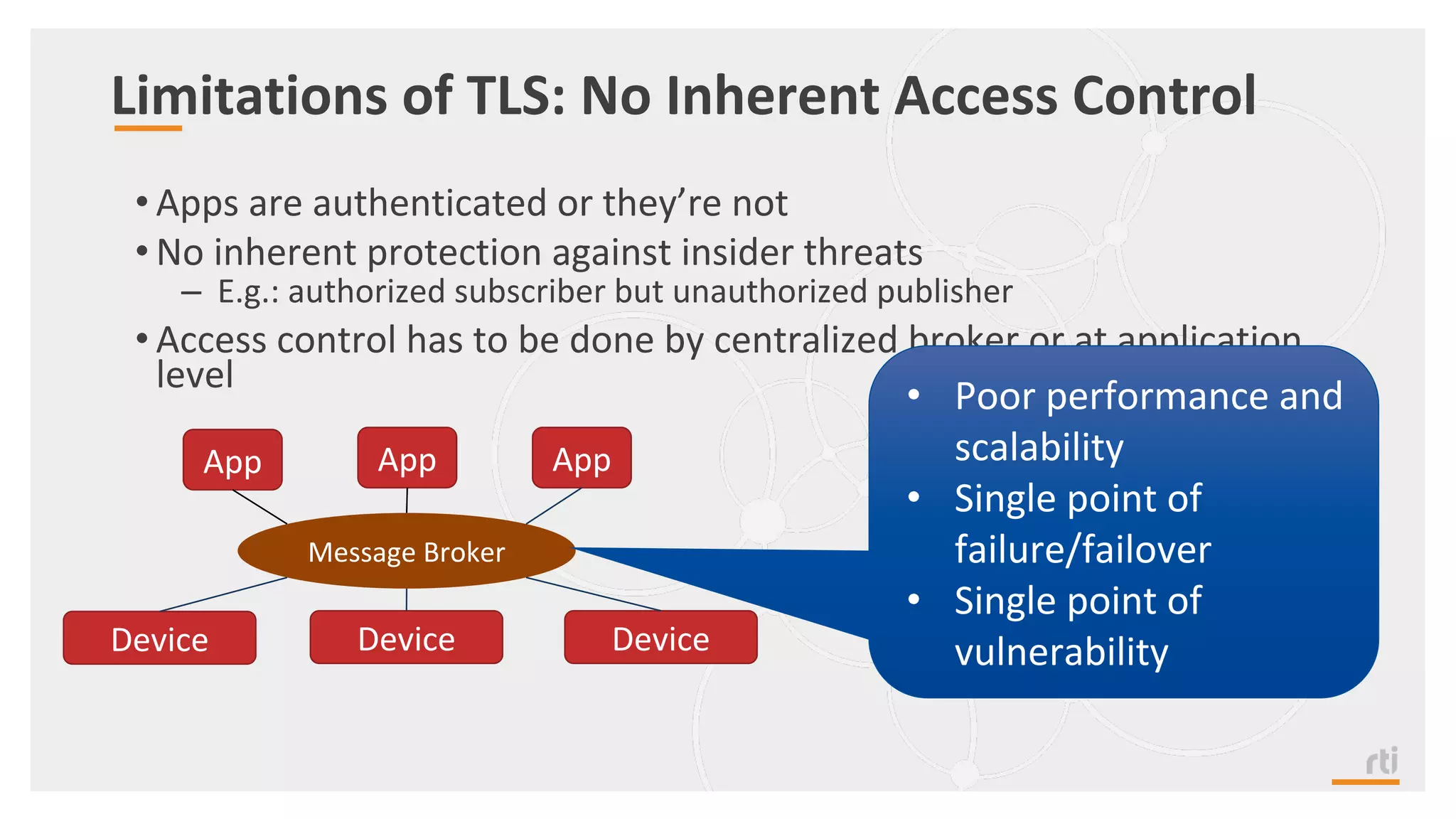
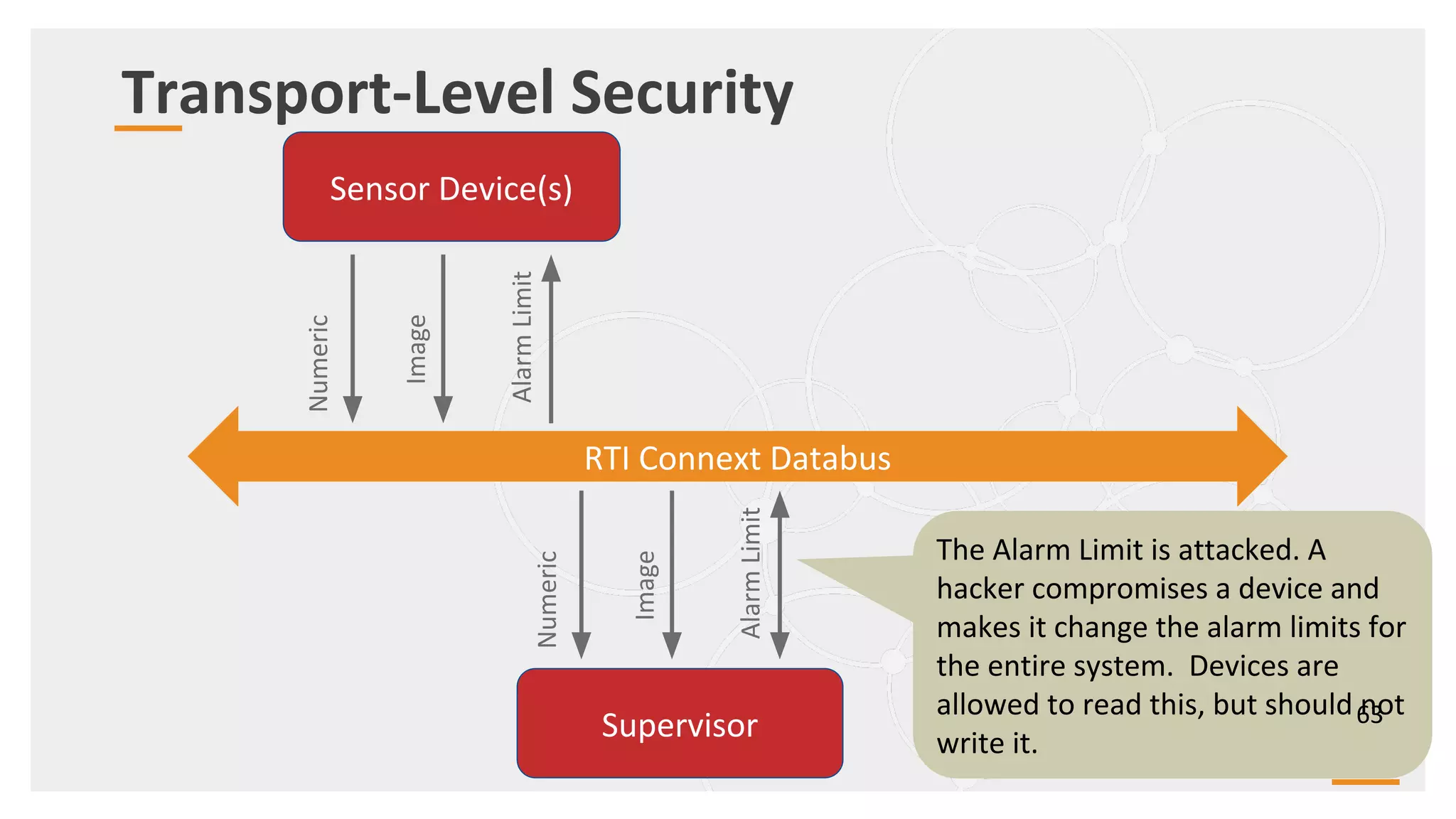
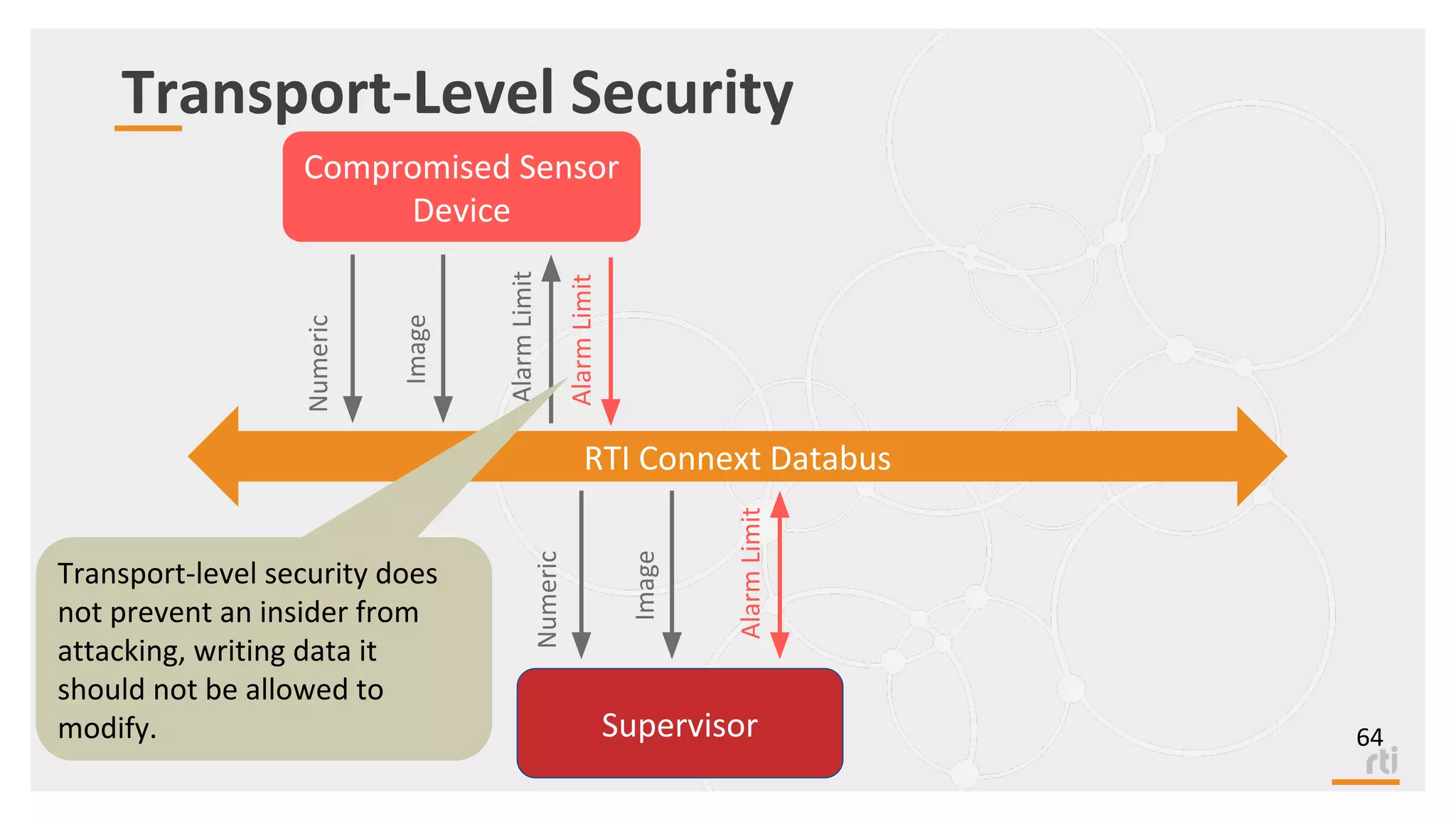
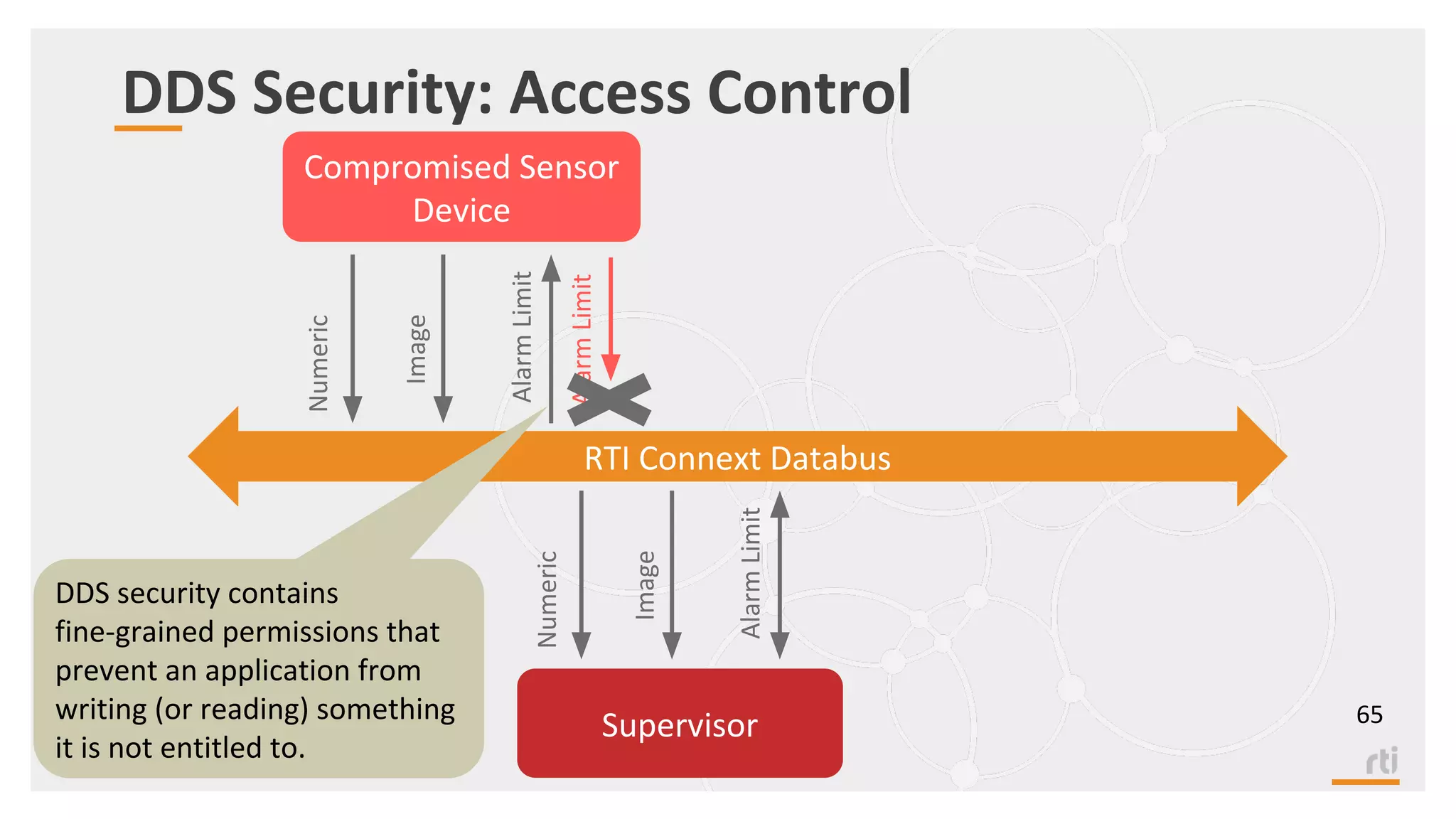
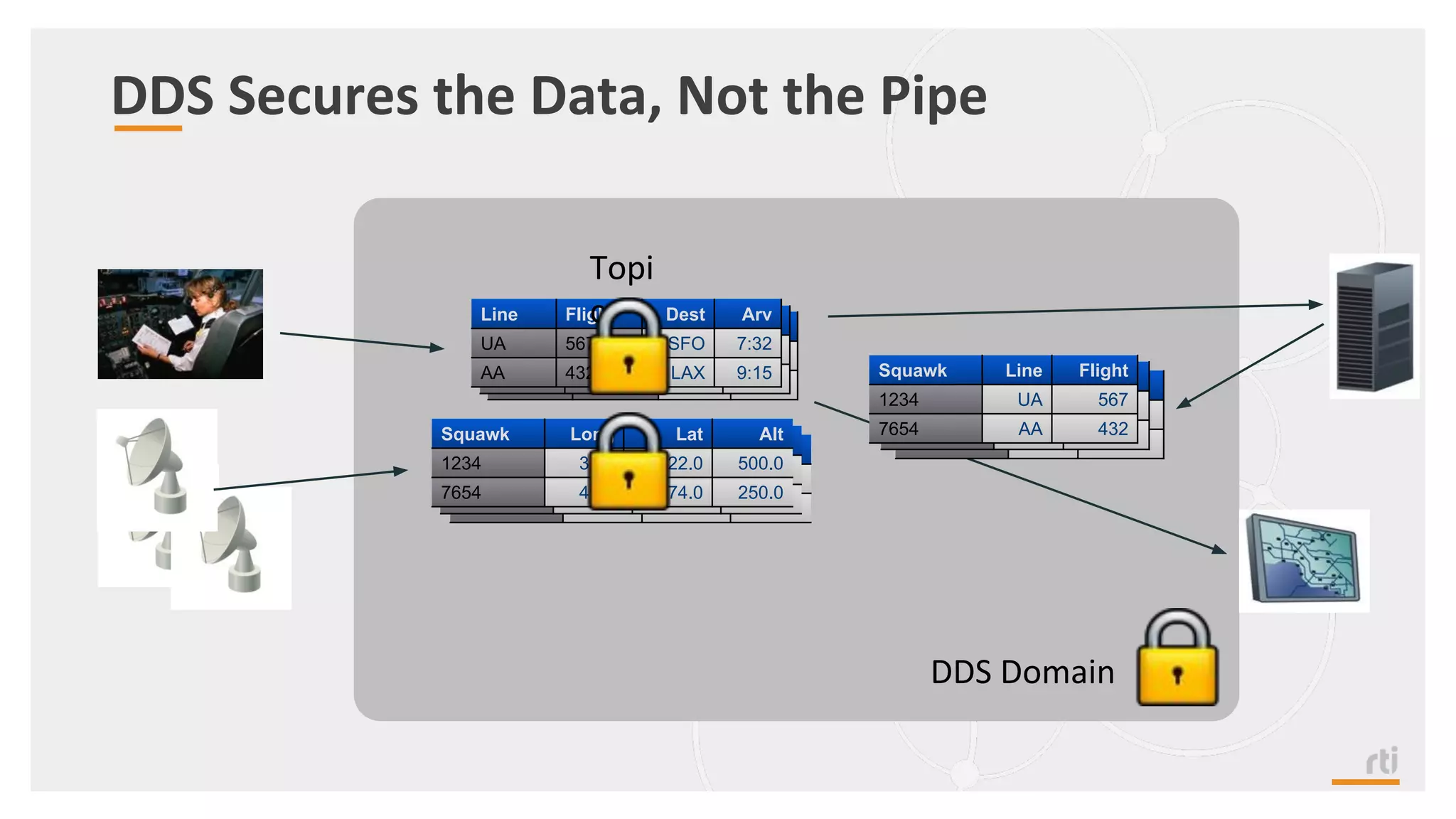
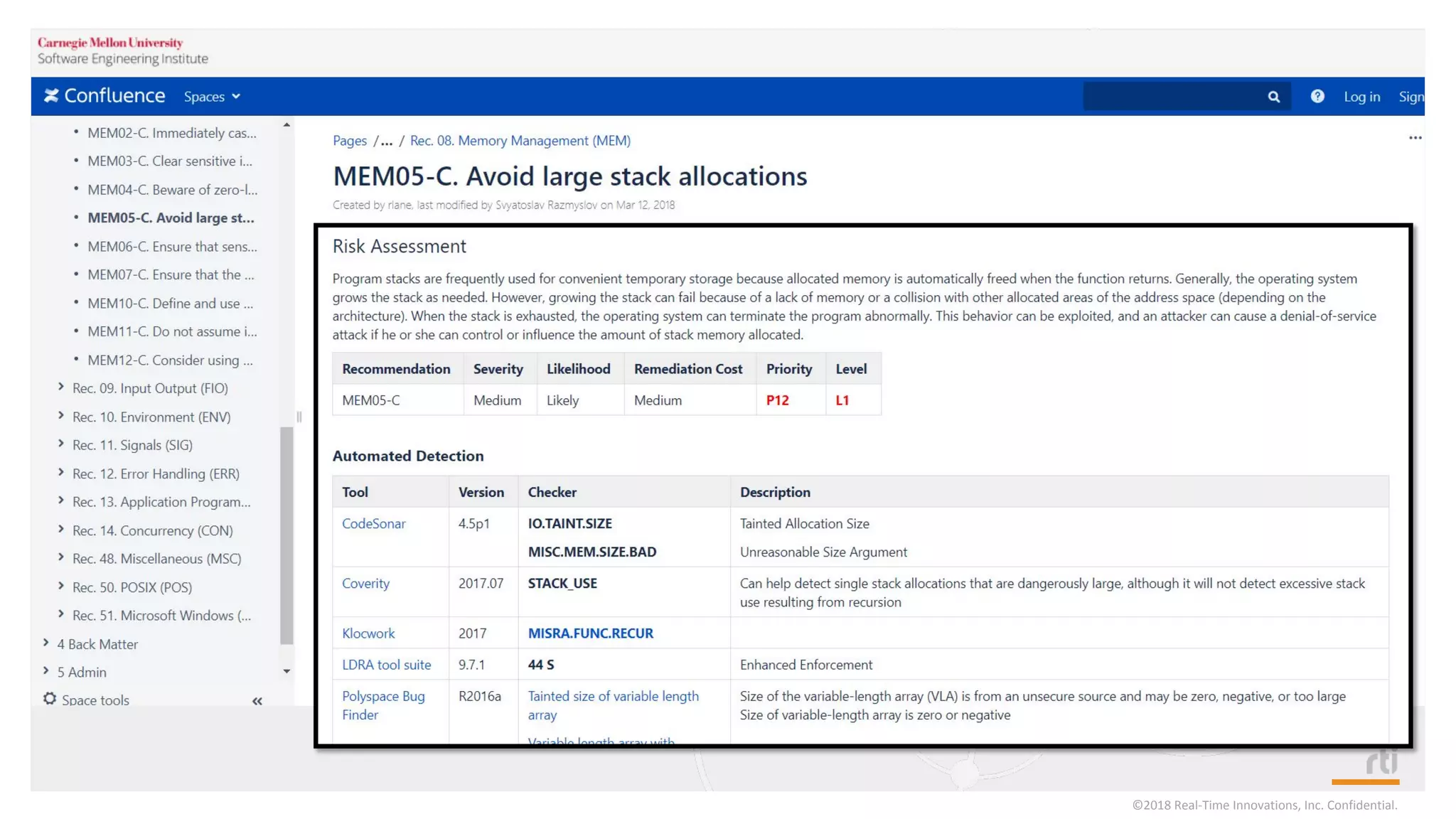
The document provides an overview of the Industrial Internet of Things (IIoT) focusing on its protocols, standards, and applications across various industries such as healthcare and transportation. It discusses key standards like DDS, MQTT, and AMQP, outlining their specific use cases and benefits for device communication. Additionally, it emphasizes the importance of data-centric approaches and security measures necessary for effective implementation in IIoT systems.







![Medical and HealthCare
Patient Monitoring:
Can NASA-inspired
Command Centers
help the hospital of
the future? This
hospital thinks so [2]
Connected Medical
Devices
Image: source](https://image.slidesharecdn.com/industrialinternetofthingsdistributedsystemsmasteruco-180903093604/75/Industrial-Internet-of-Things-Protocols-an-Standards-15-2048.jpg)