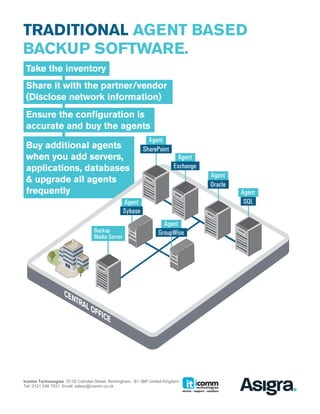
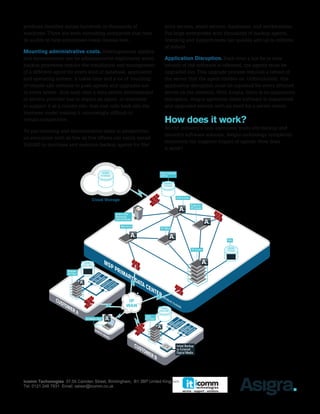
Asigra offers an agentless backup solution that simplifies installation and management while reducing administrative complexities associated with traditional agent-based systems. This approach enhances data security and recoverability, minimizes resource drain on servers, and lowers operational costs by eliminating the need for numerous backup agents. With features like automatic upgrades and robust encryption, Asigra's system is designed for scalability and efficiency across diverse IT environments.