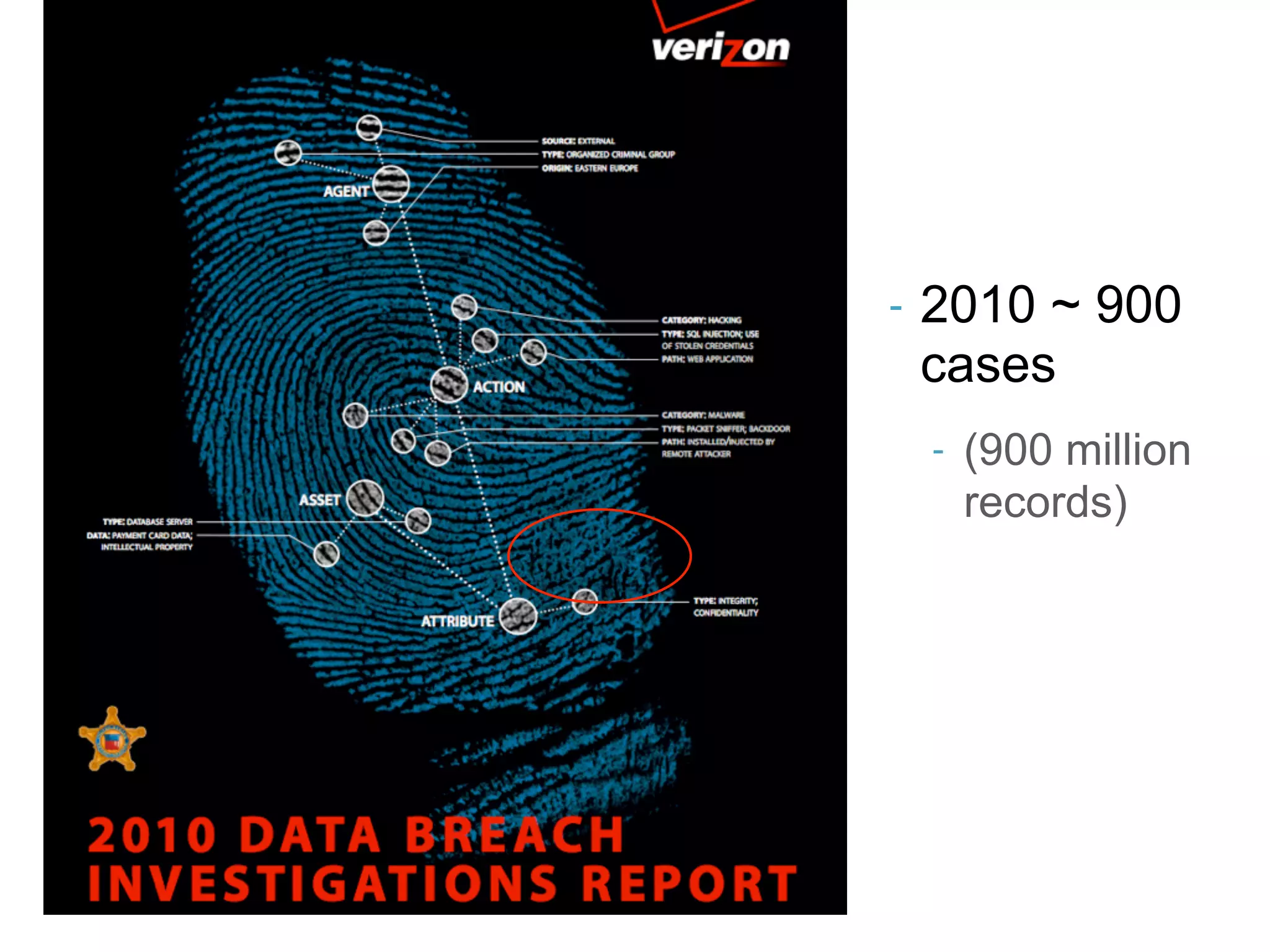
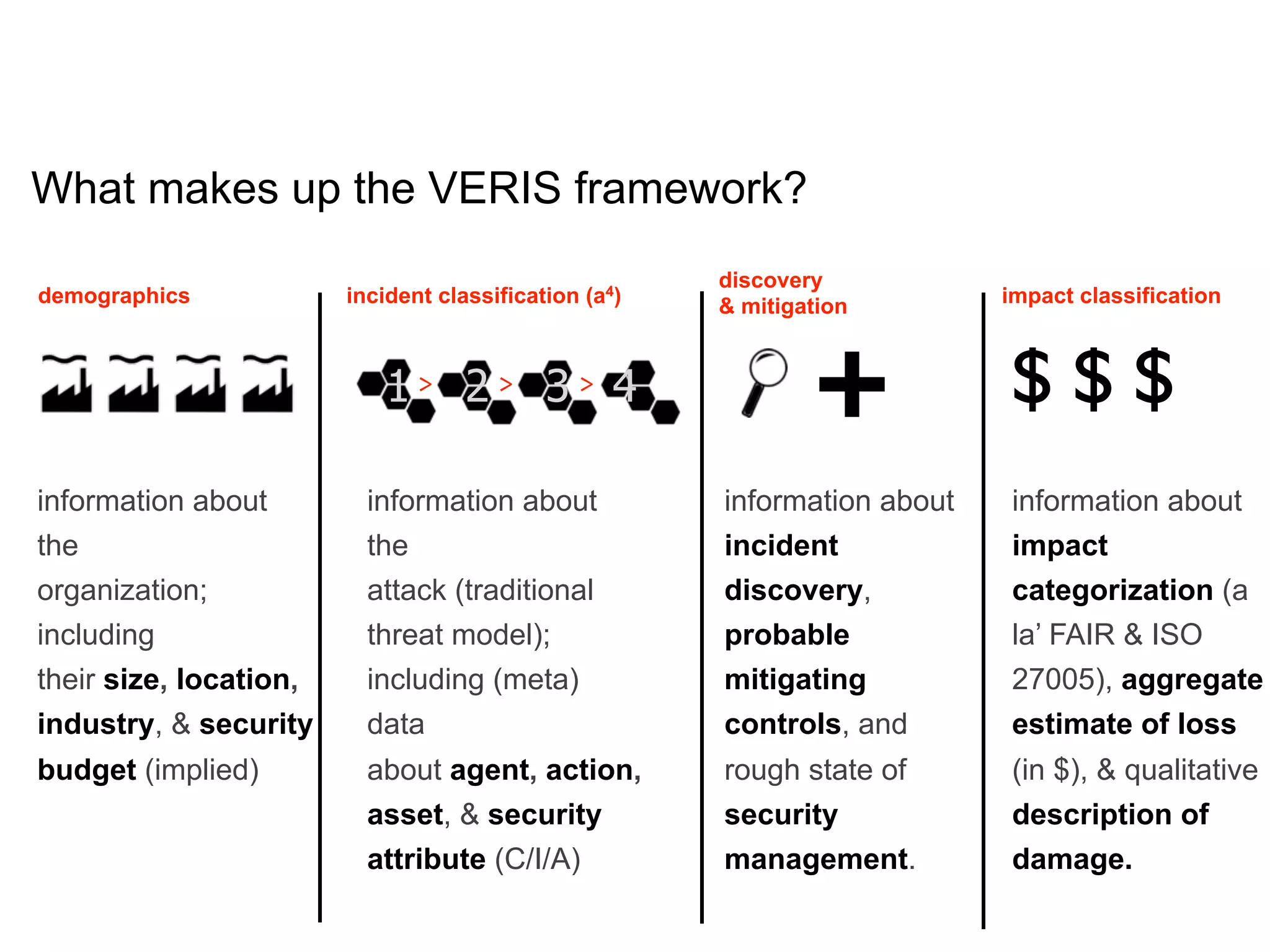
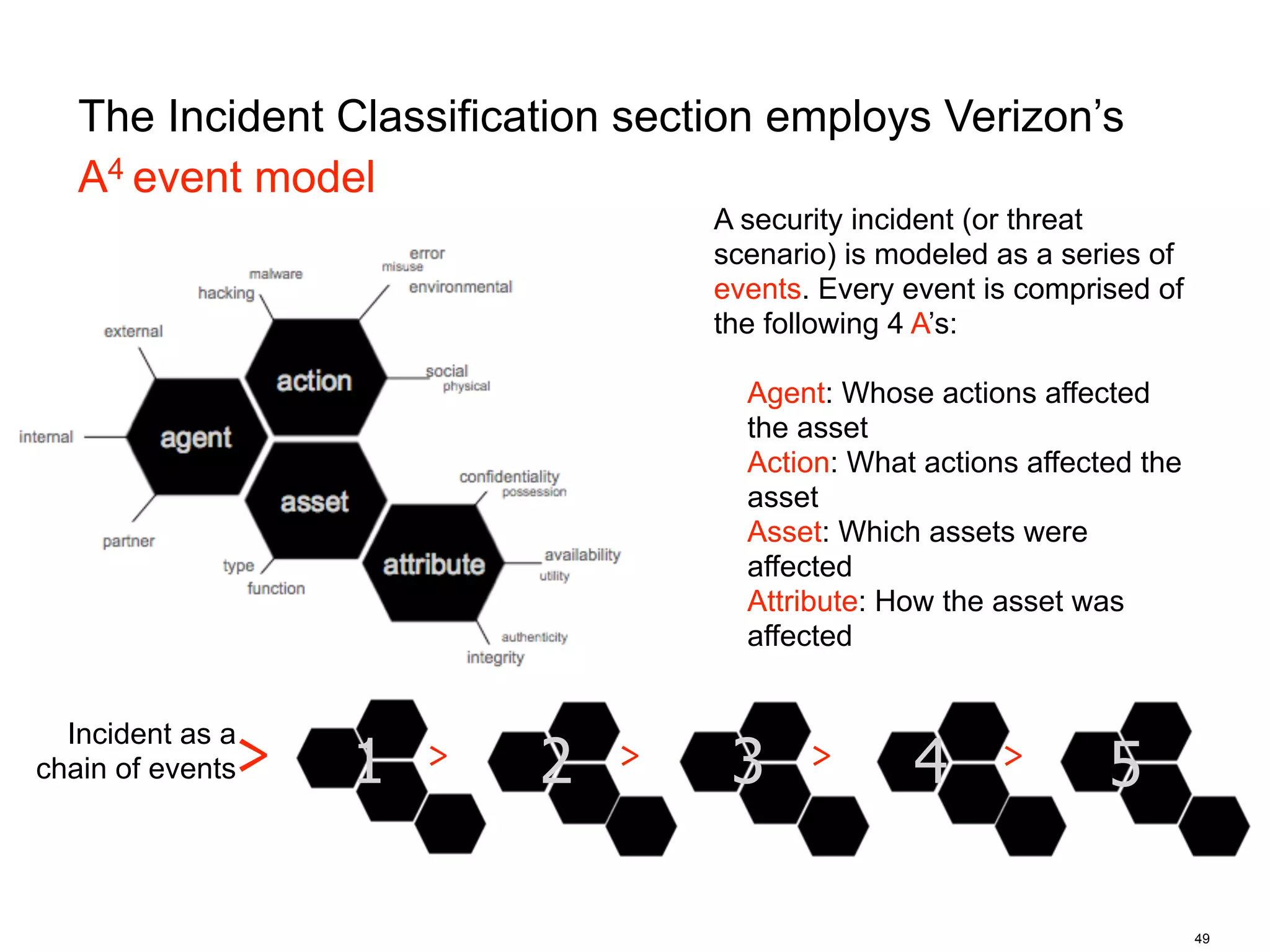
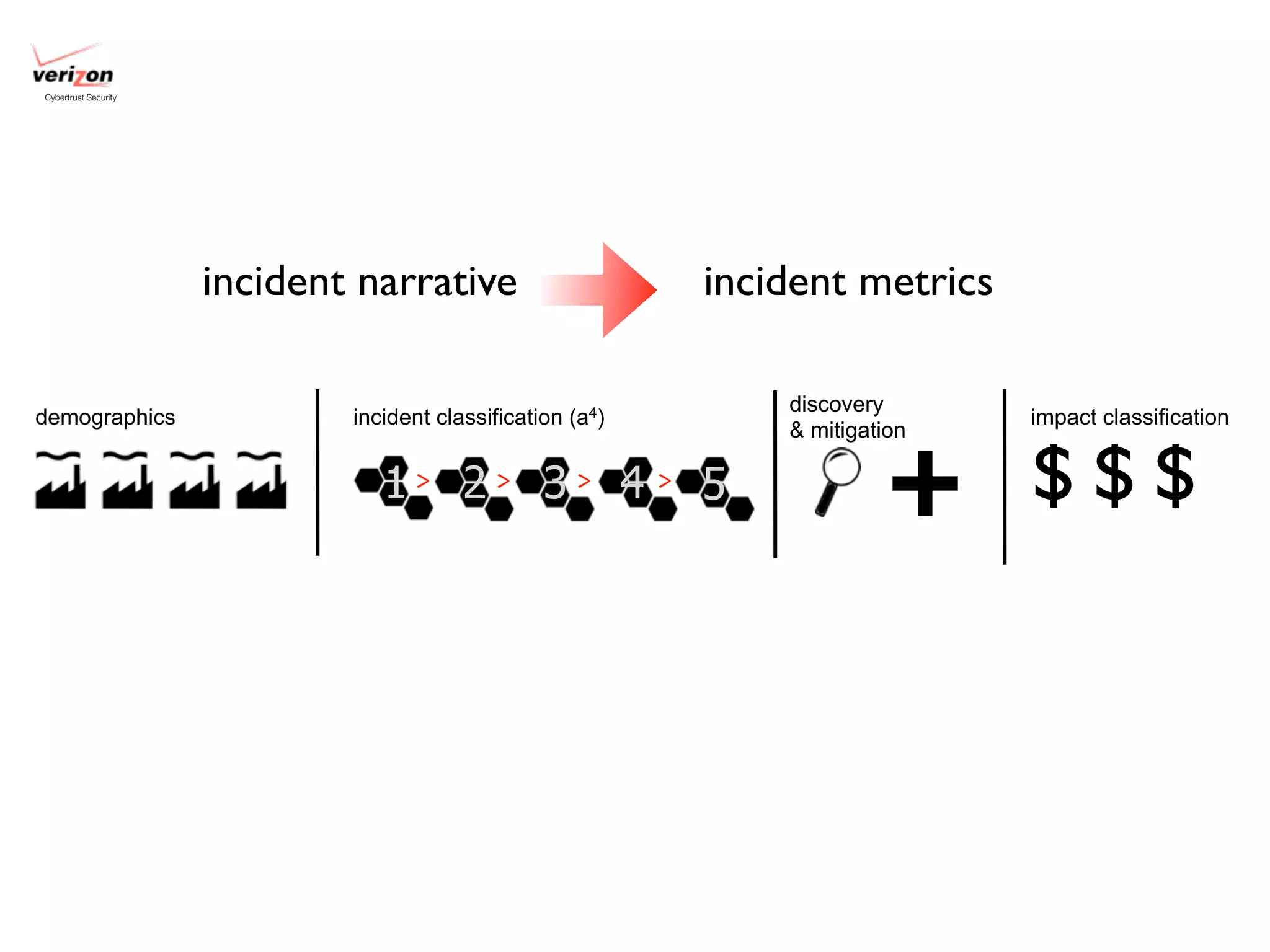
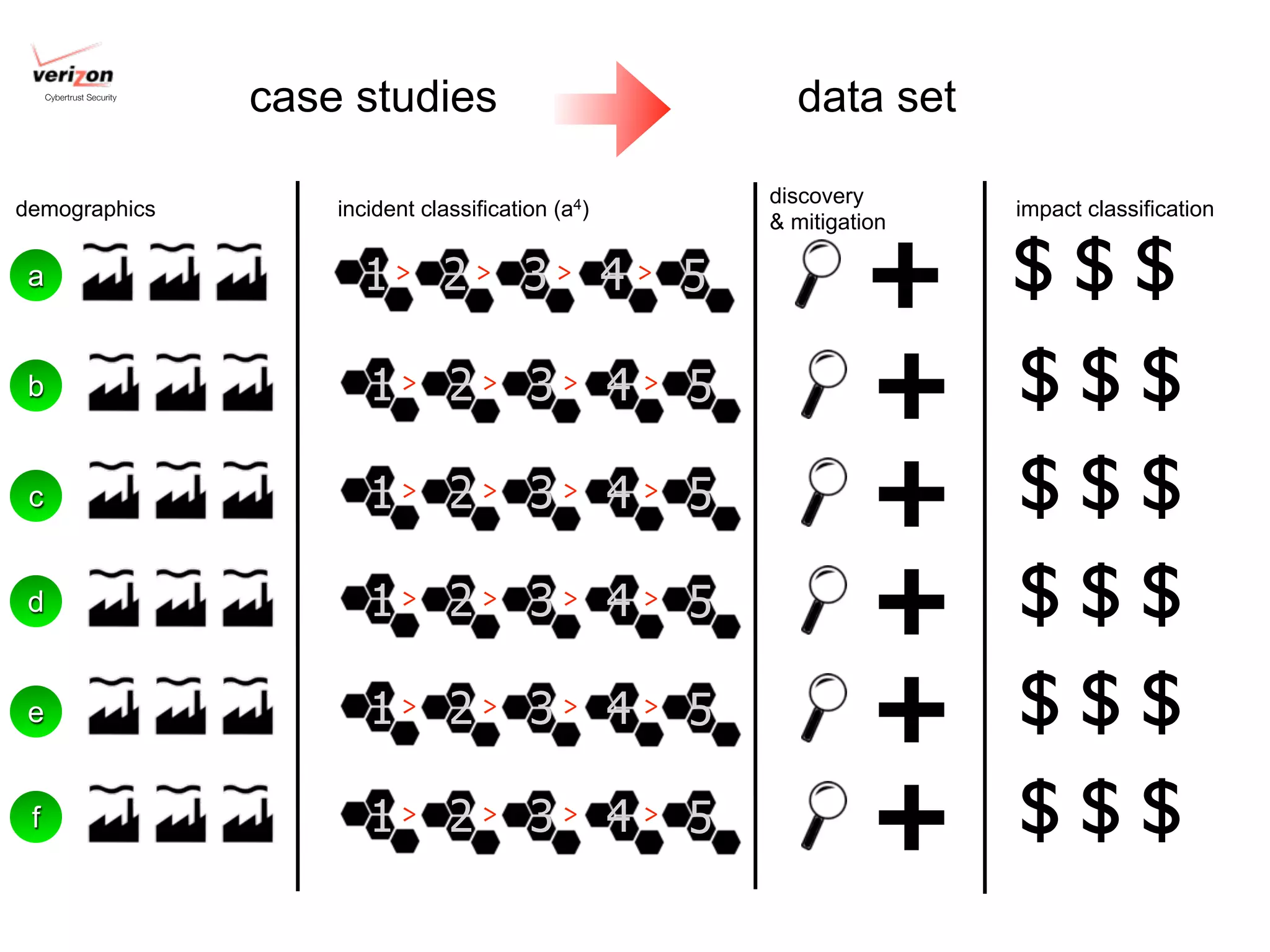
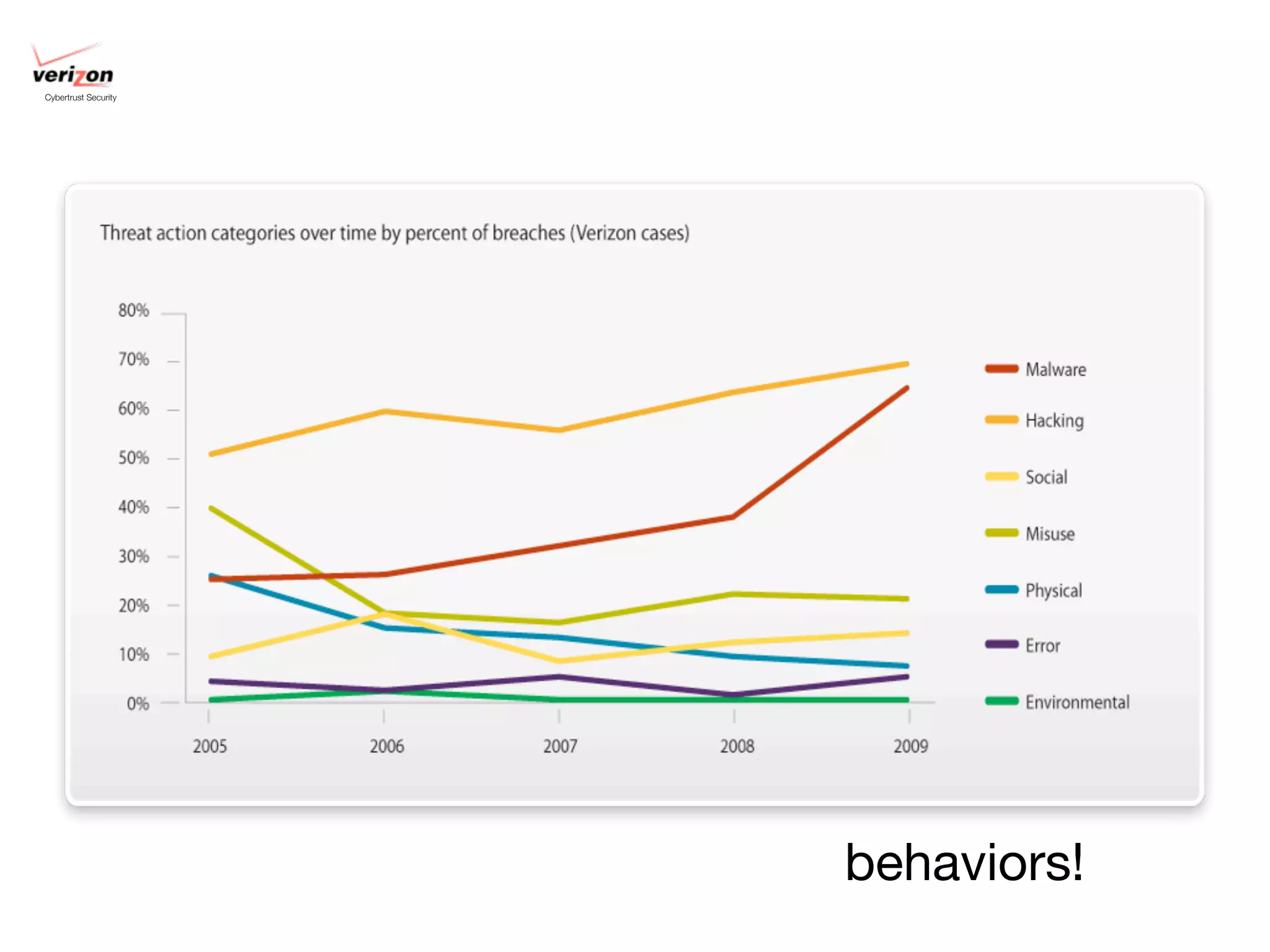
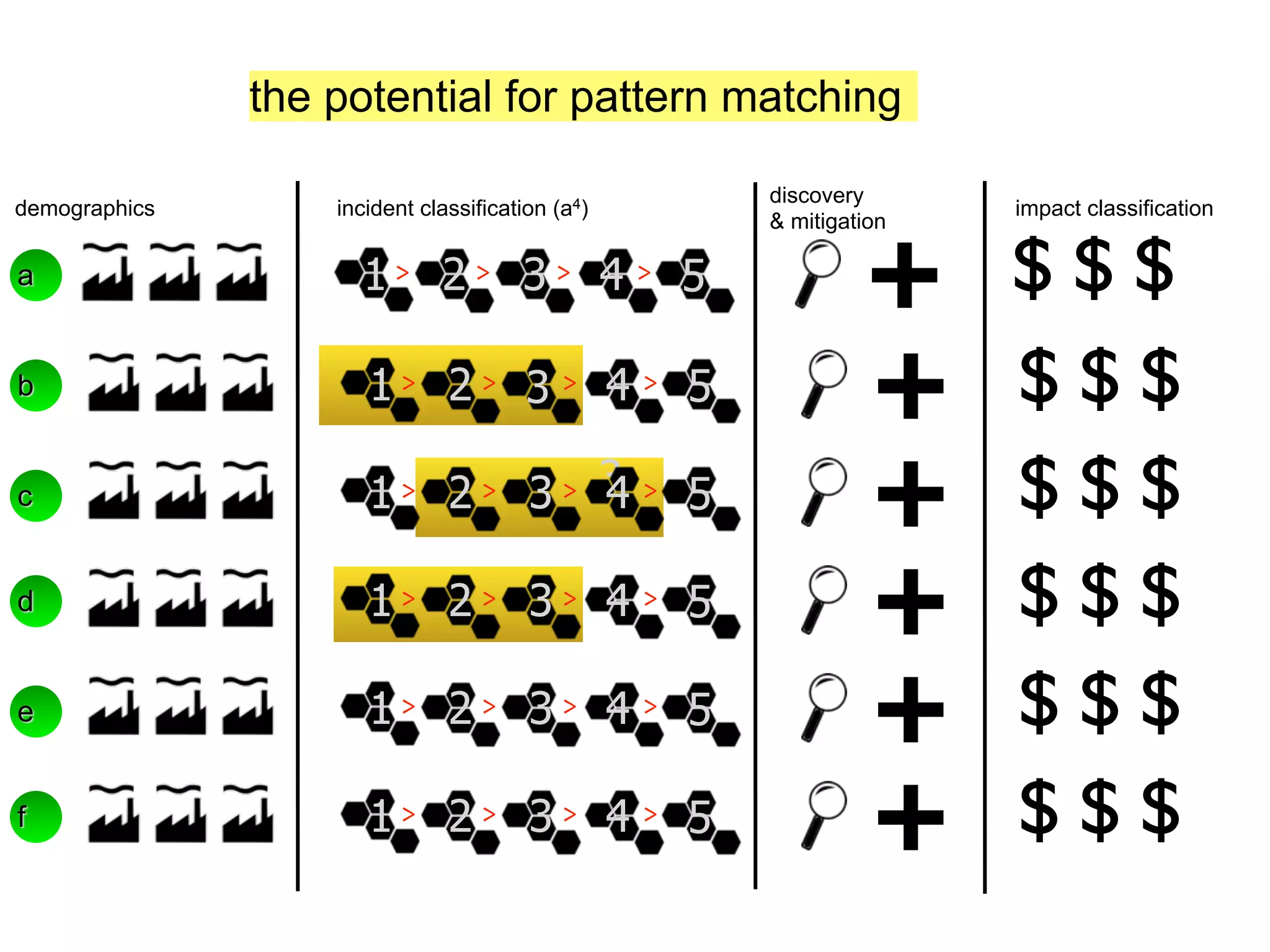
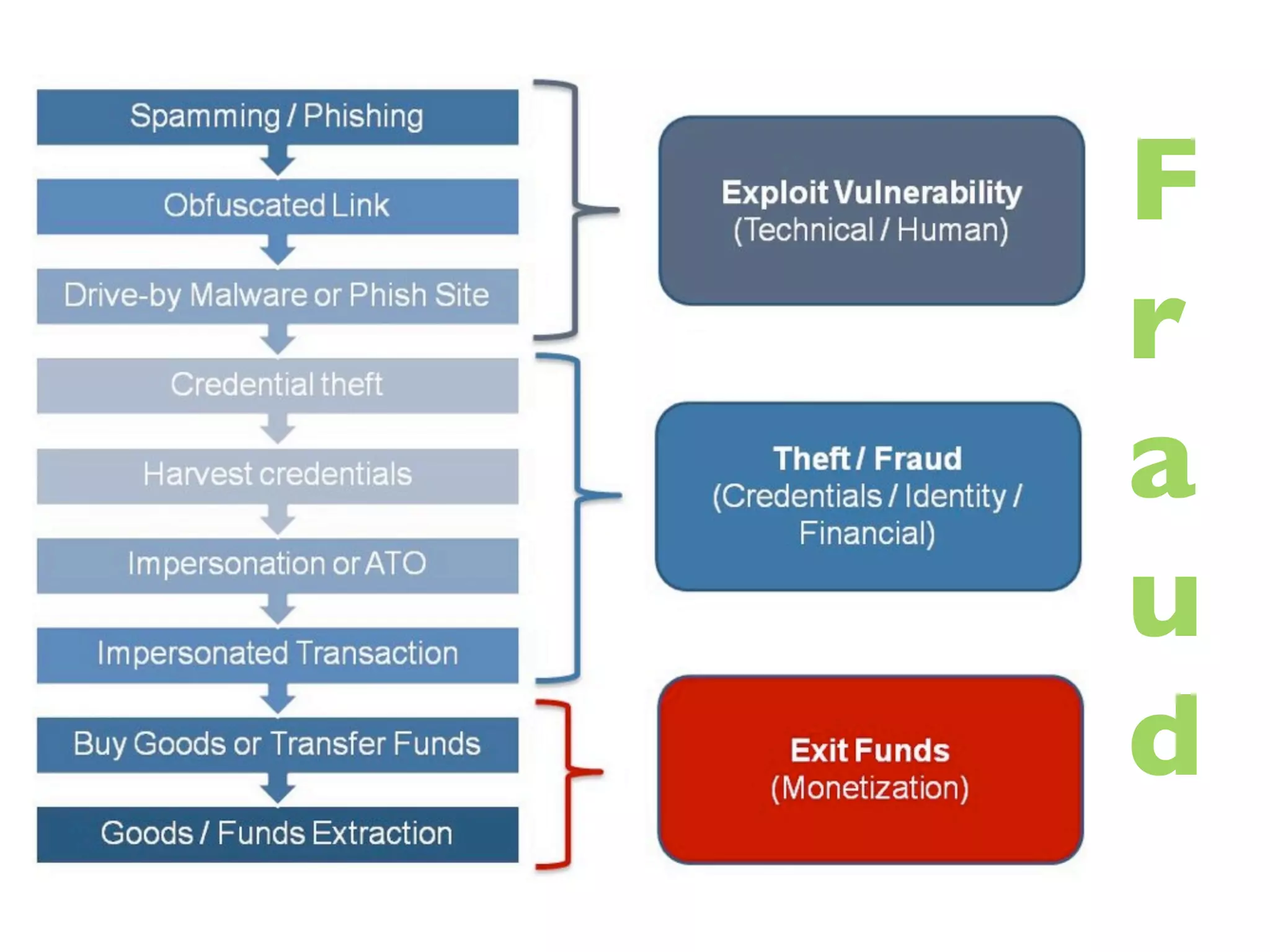
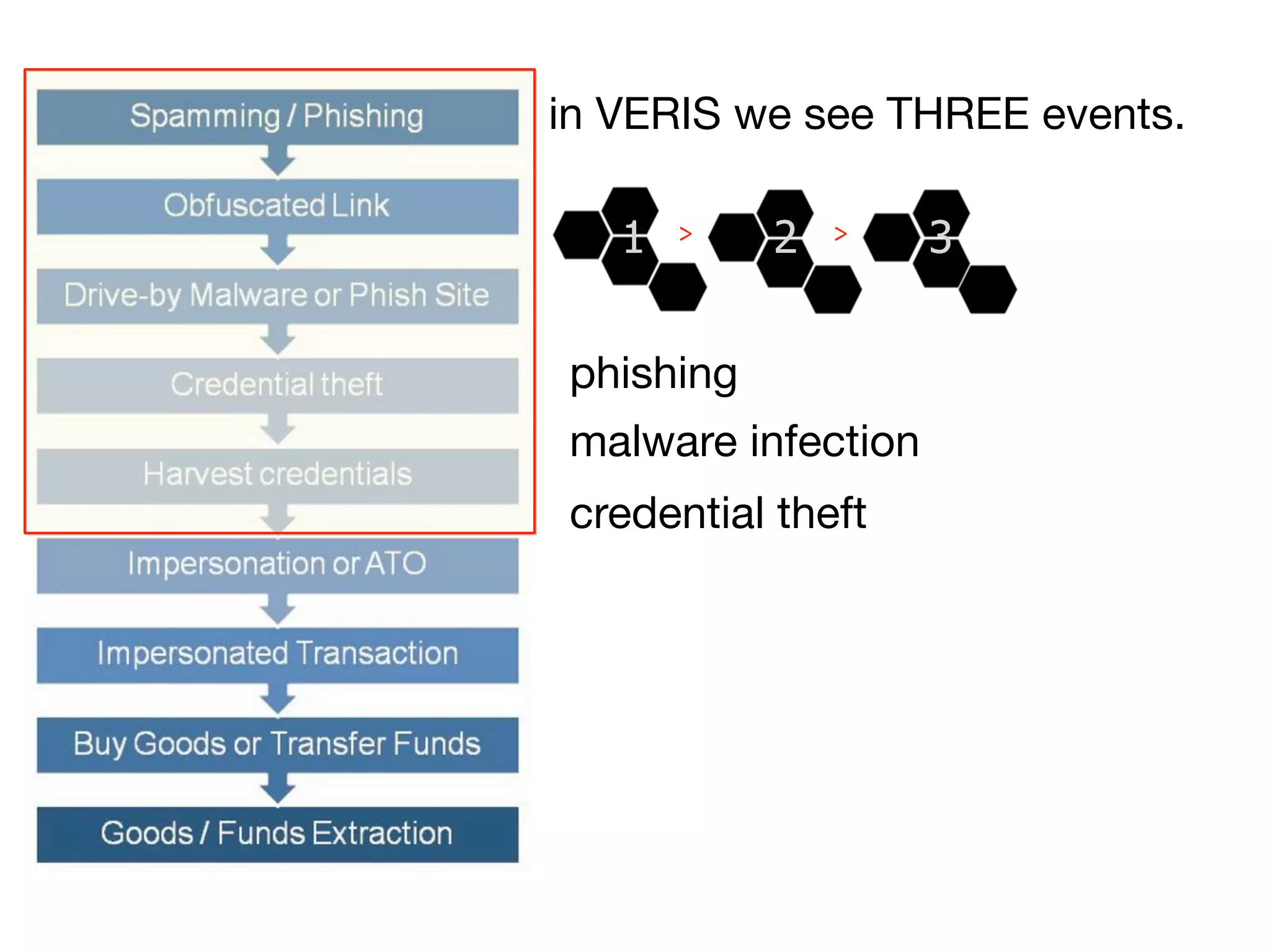
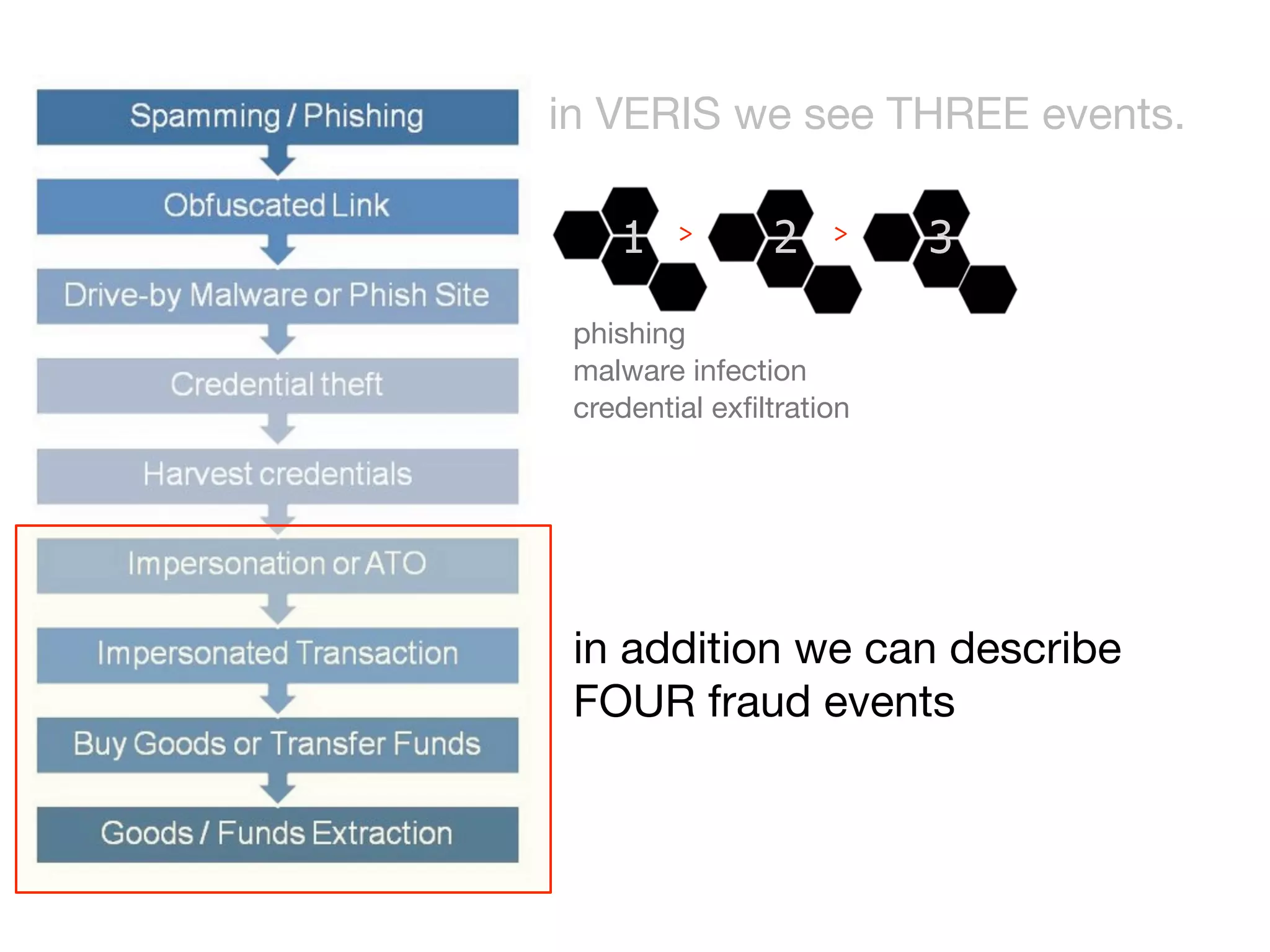
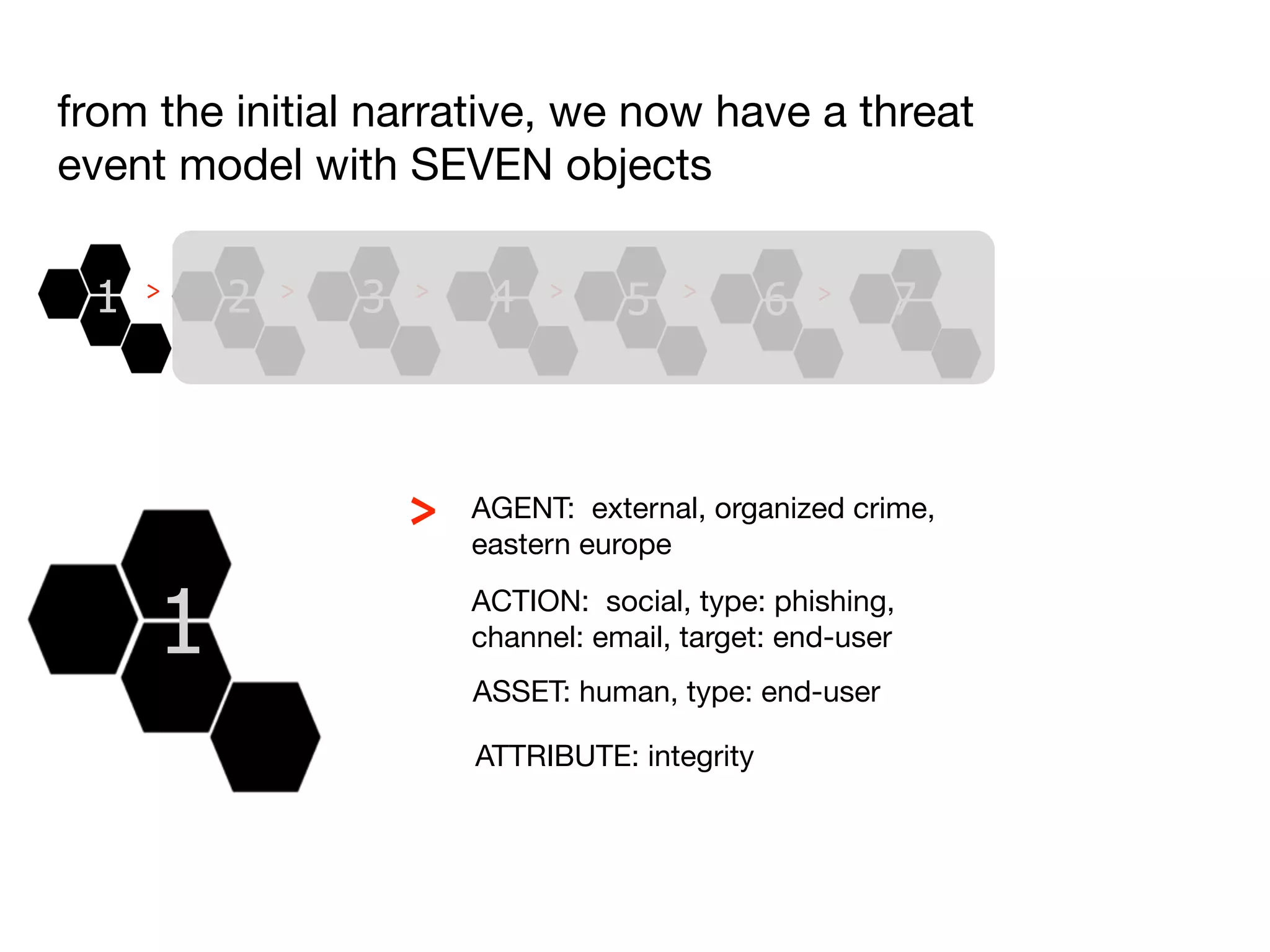
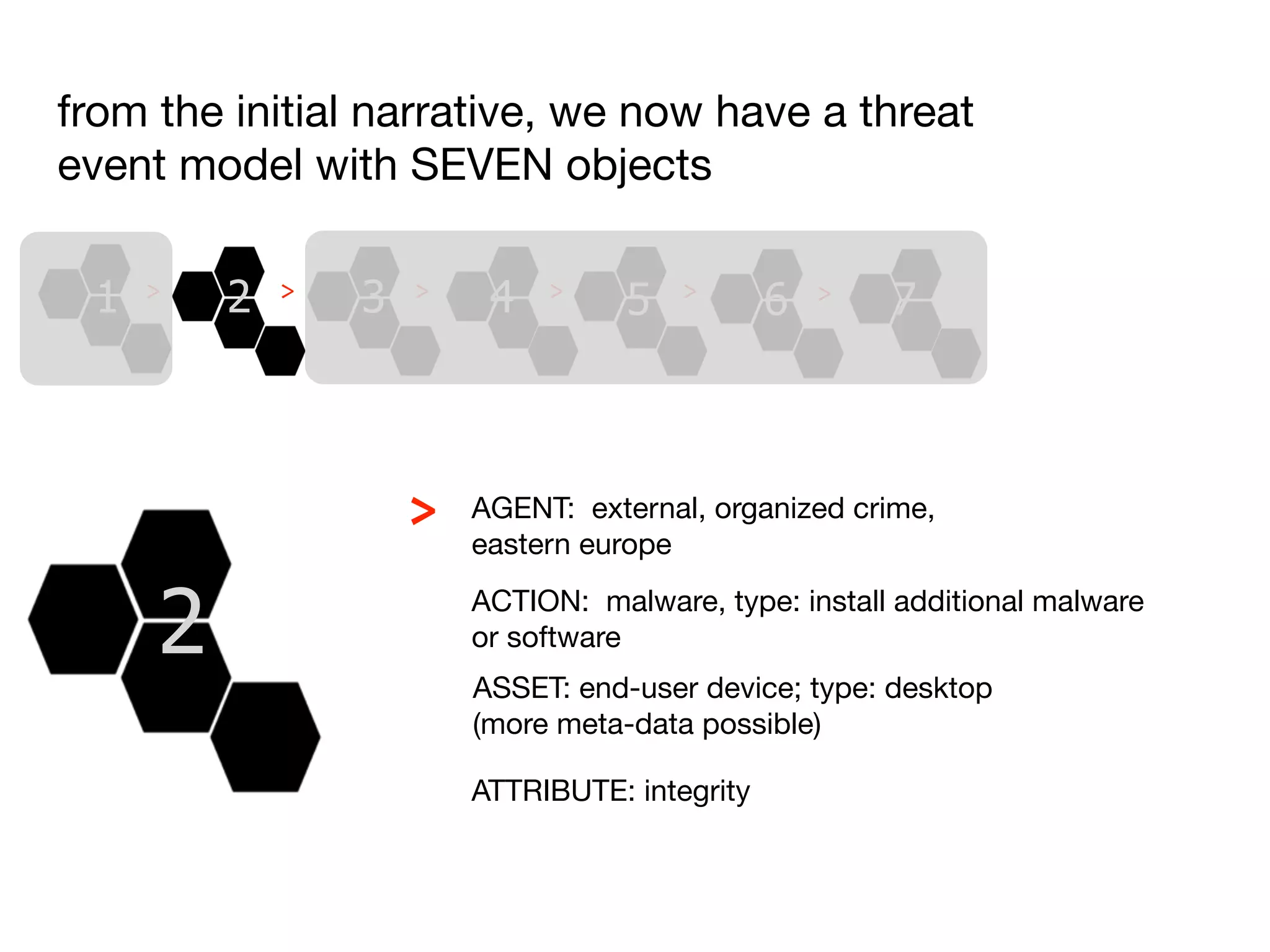
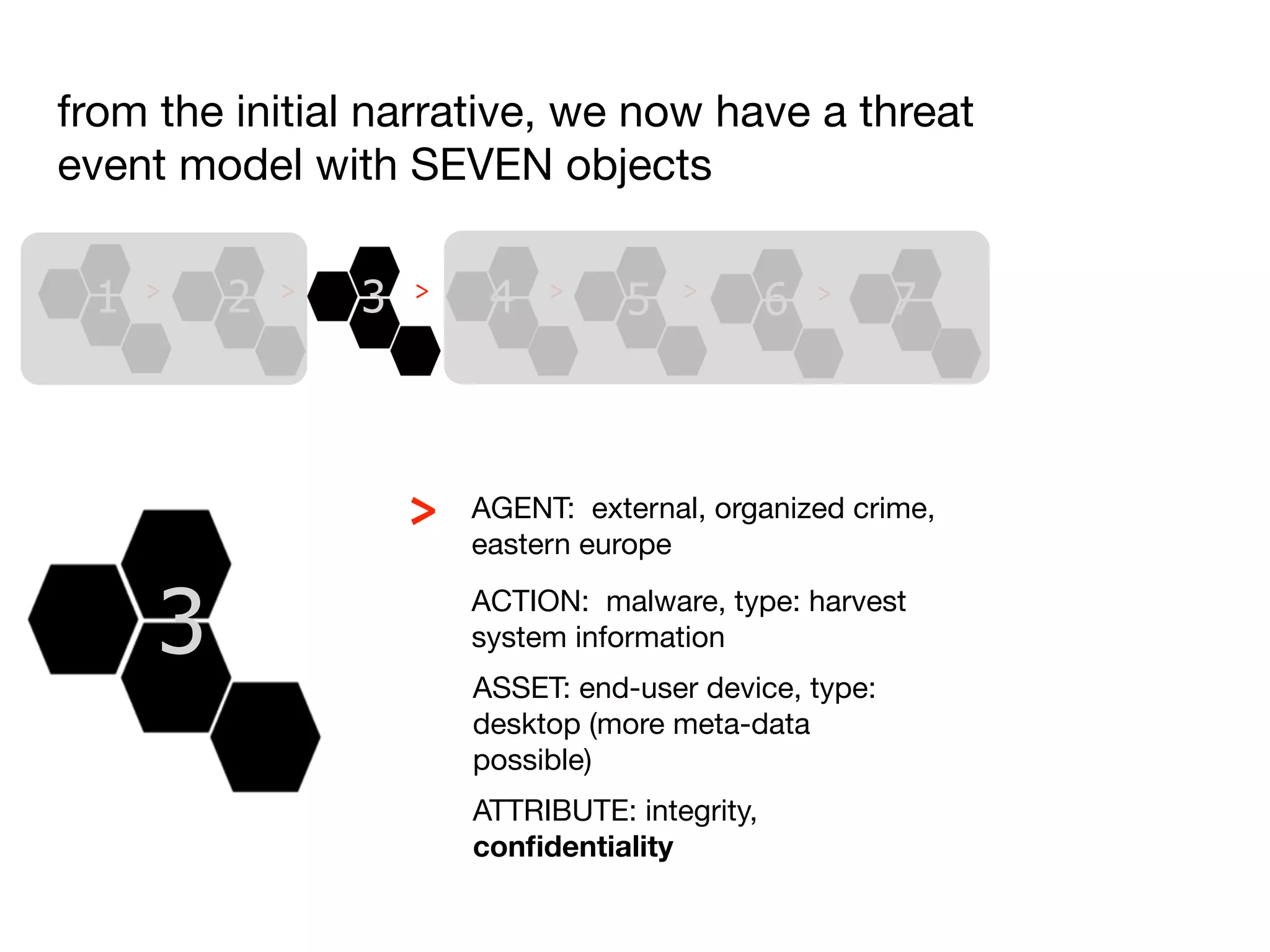
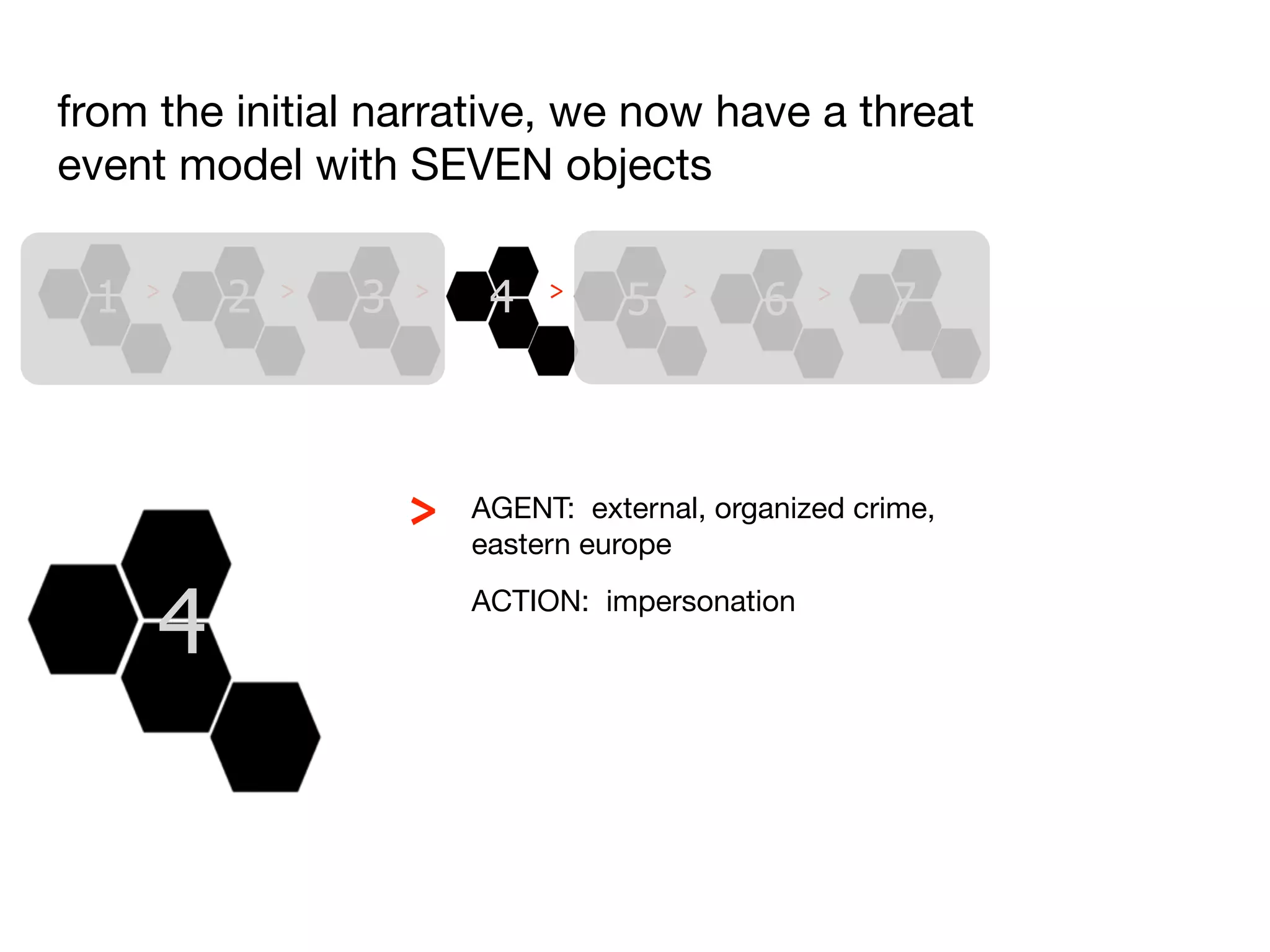
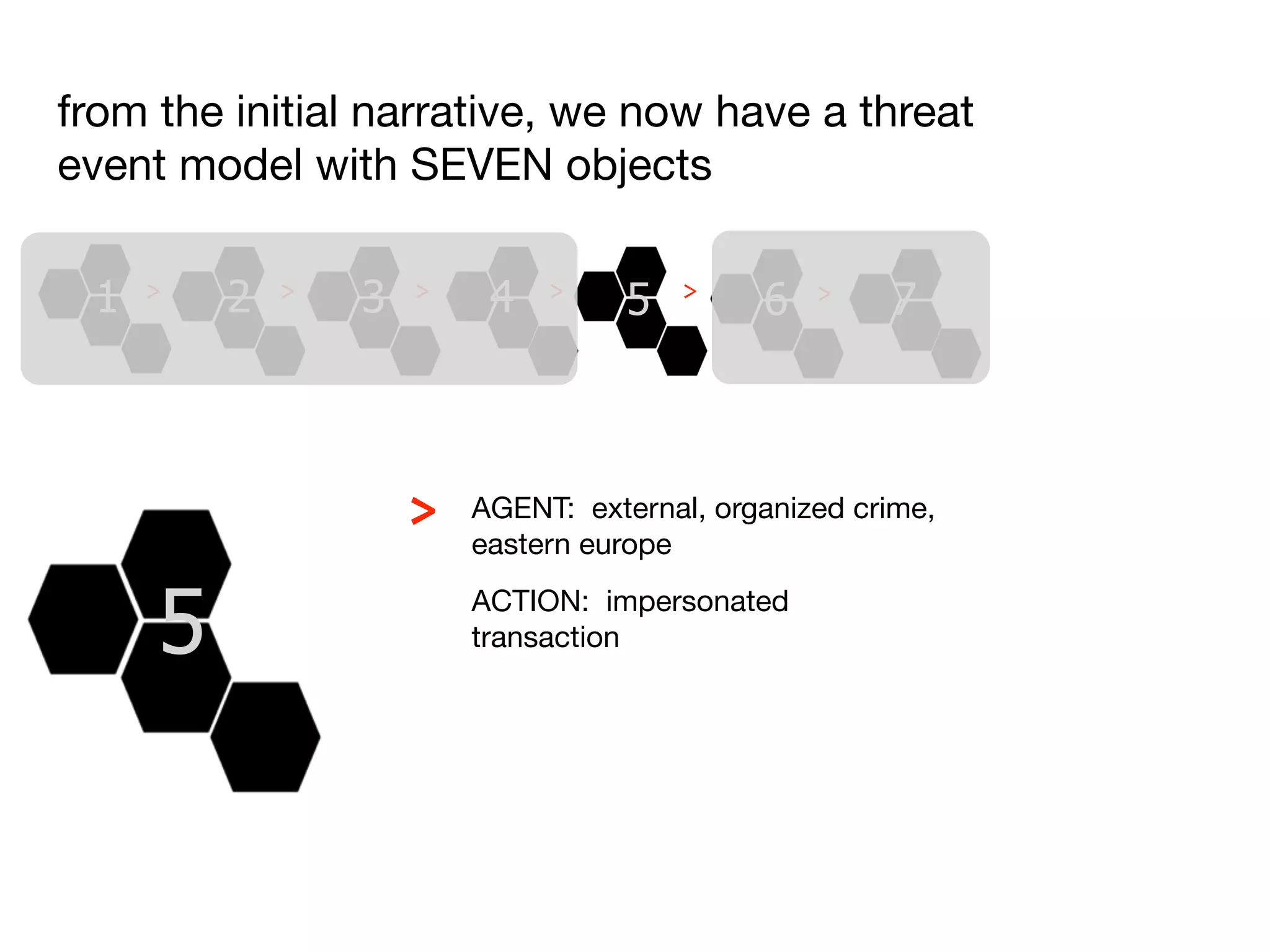
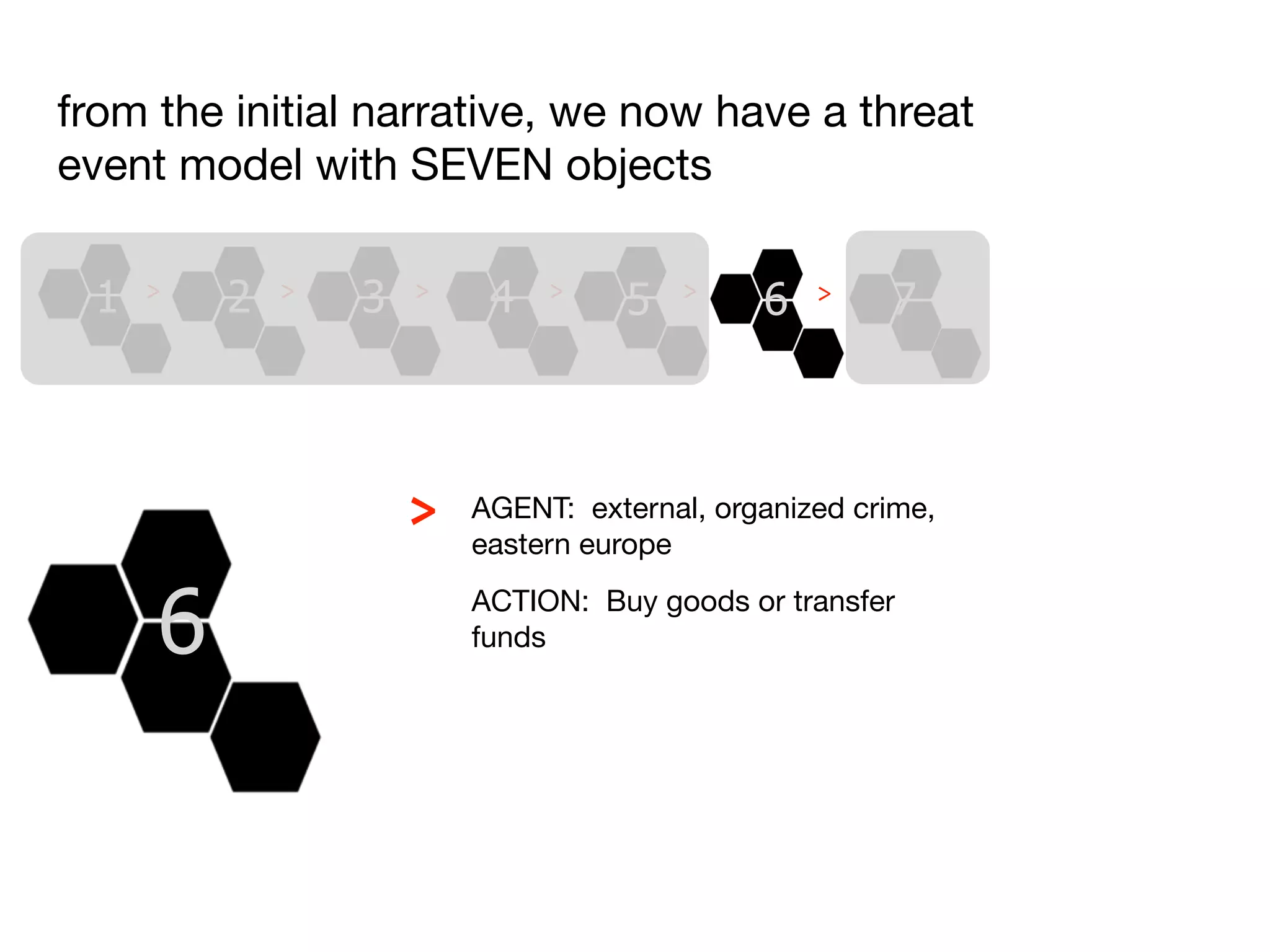
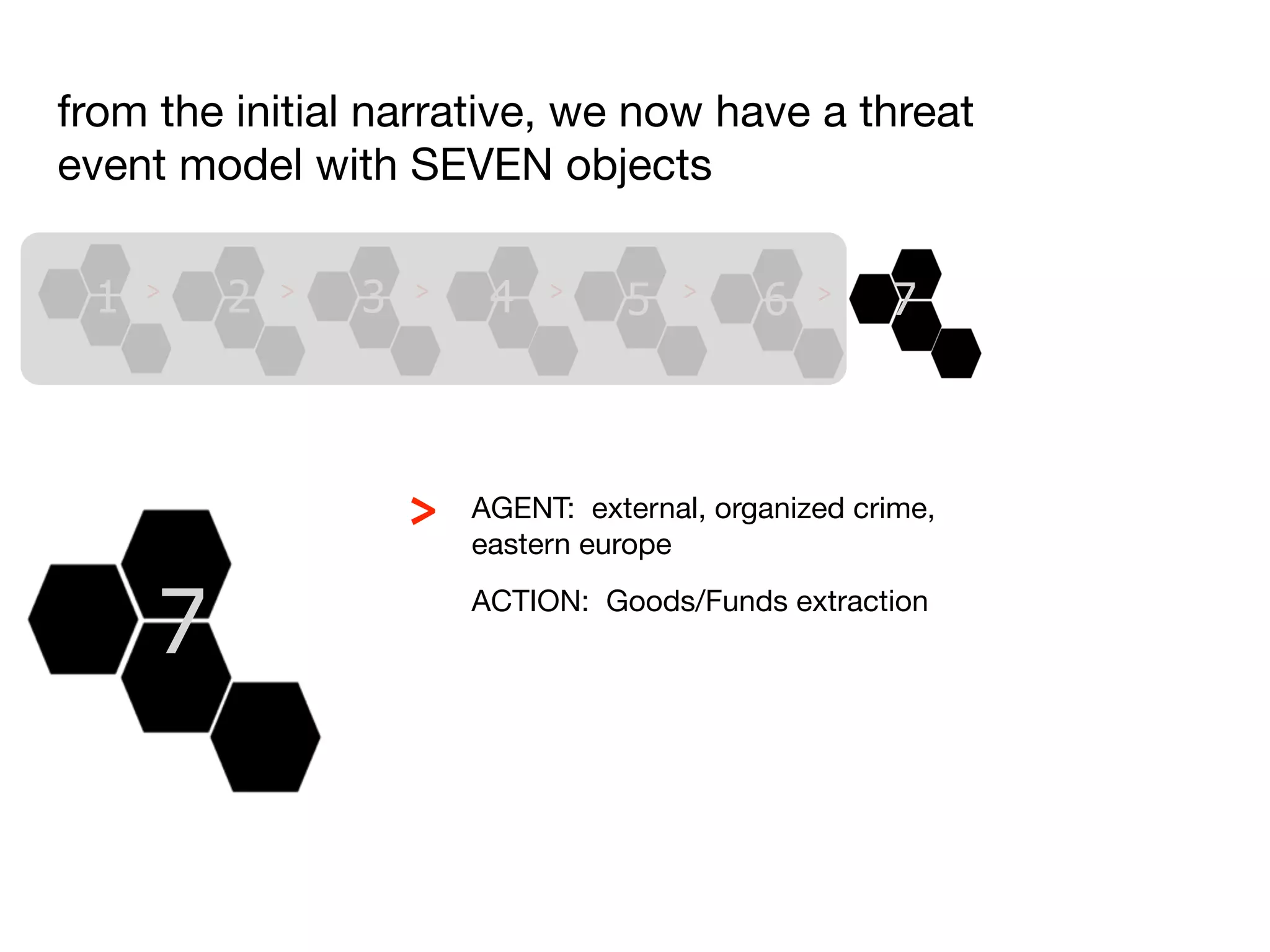
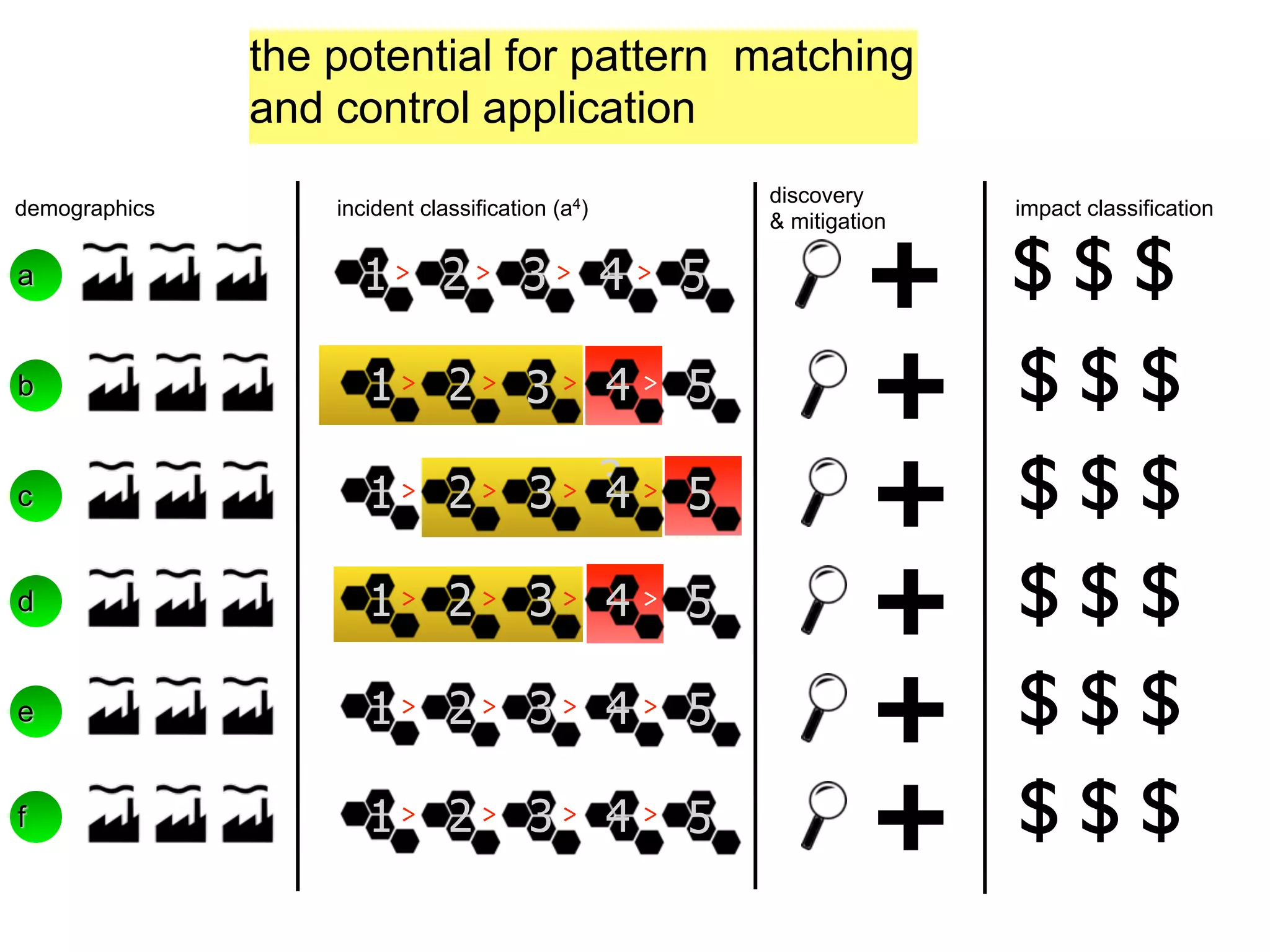
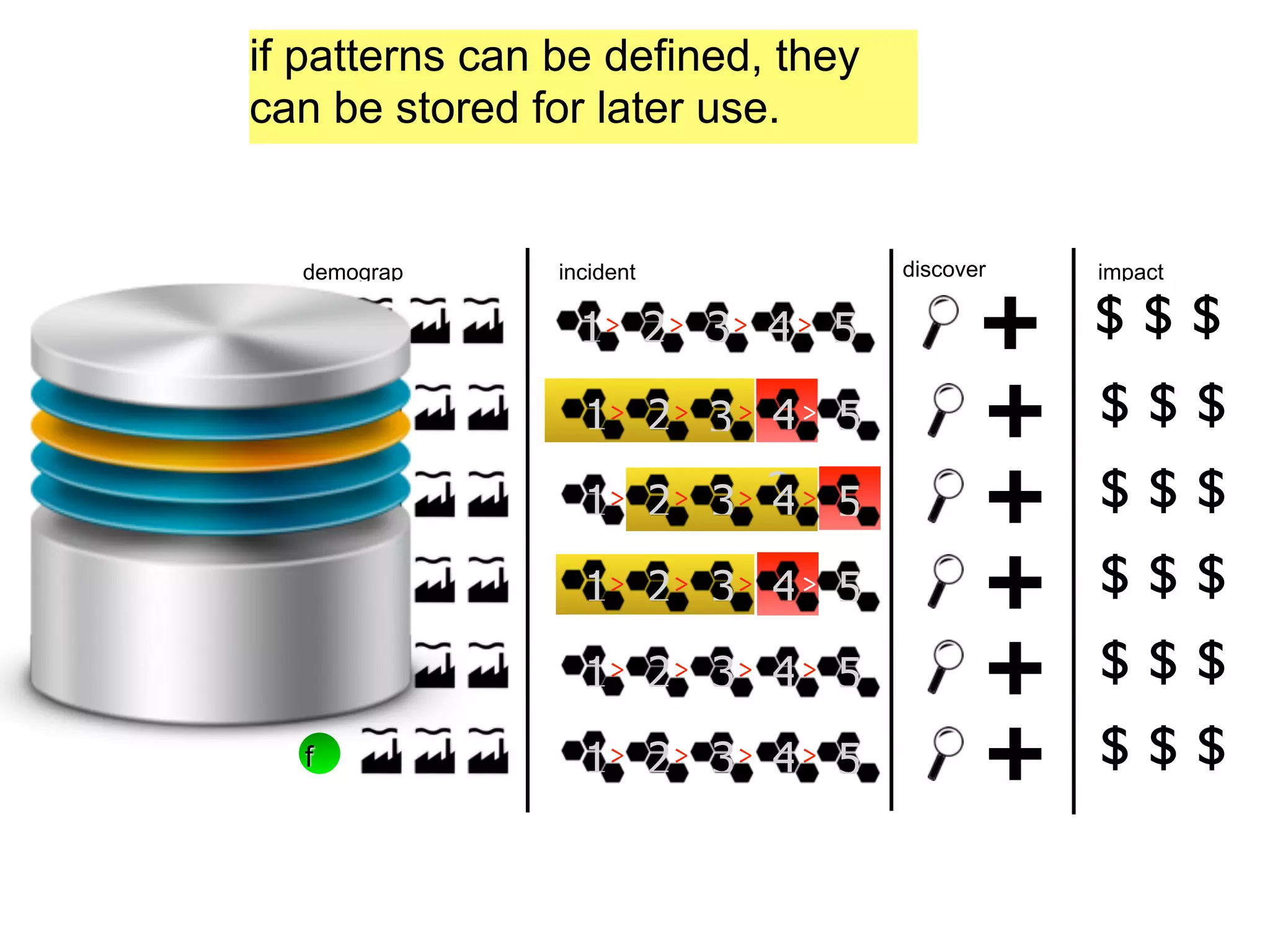
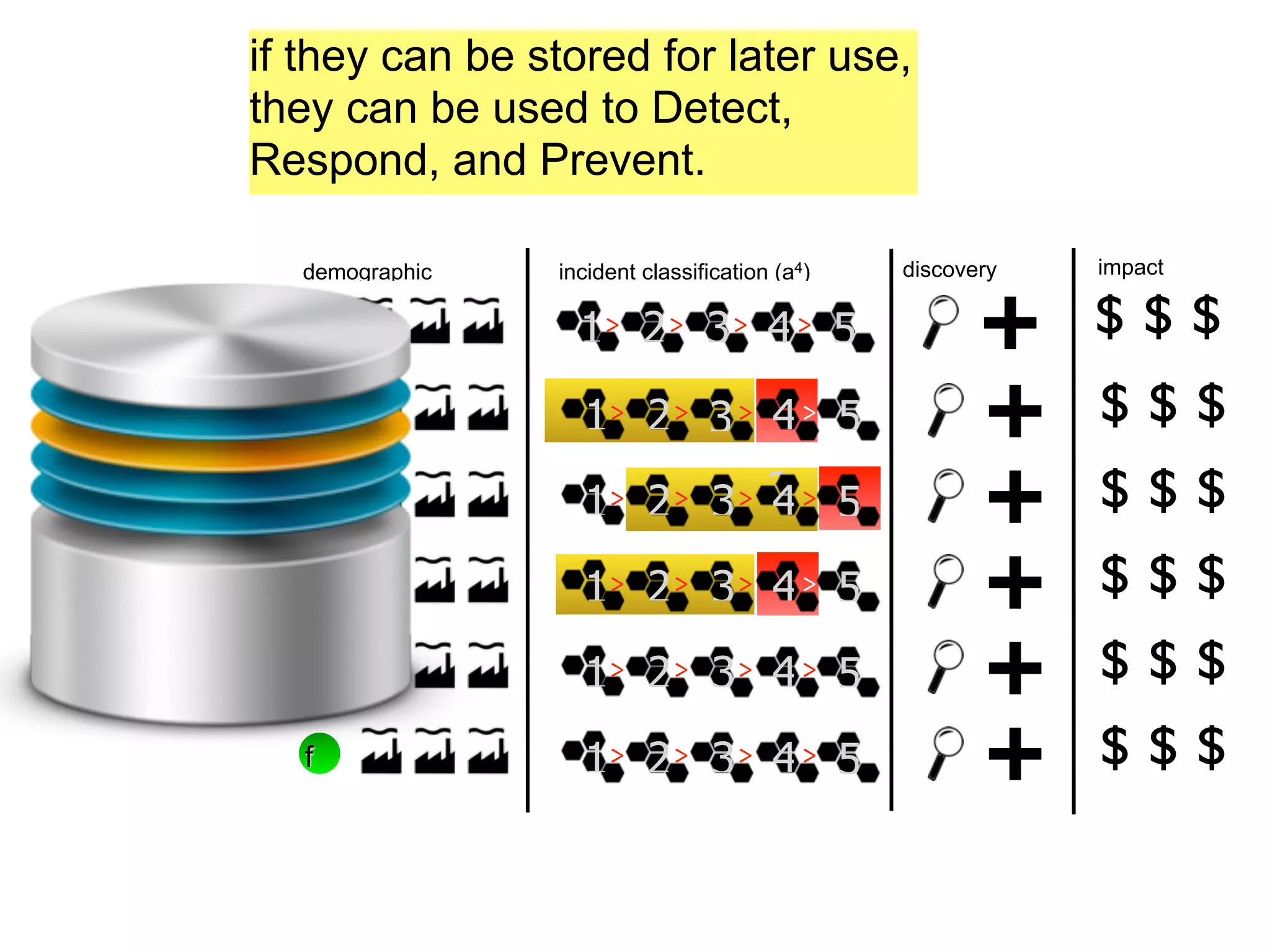
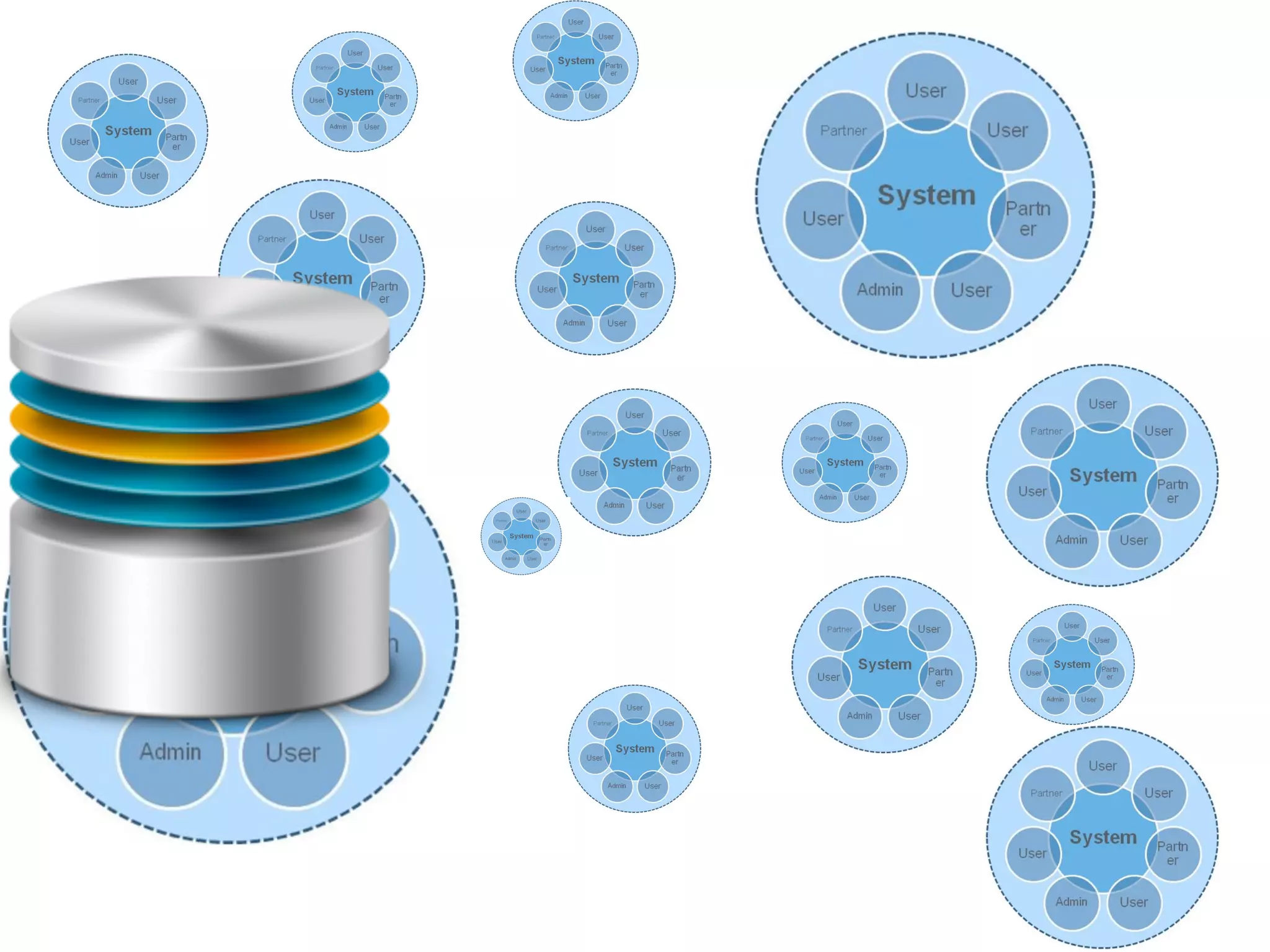
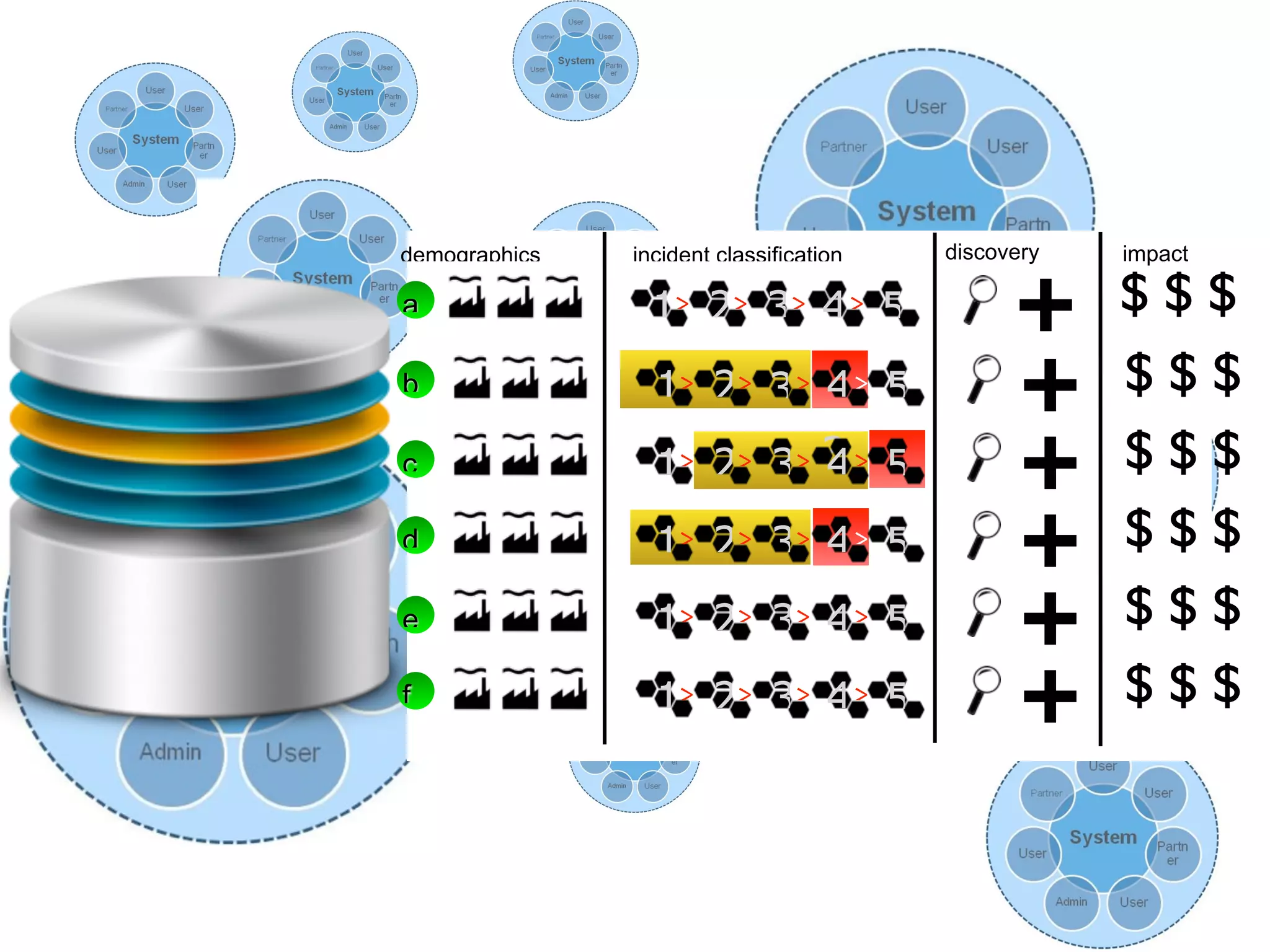
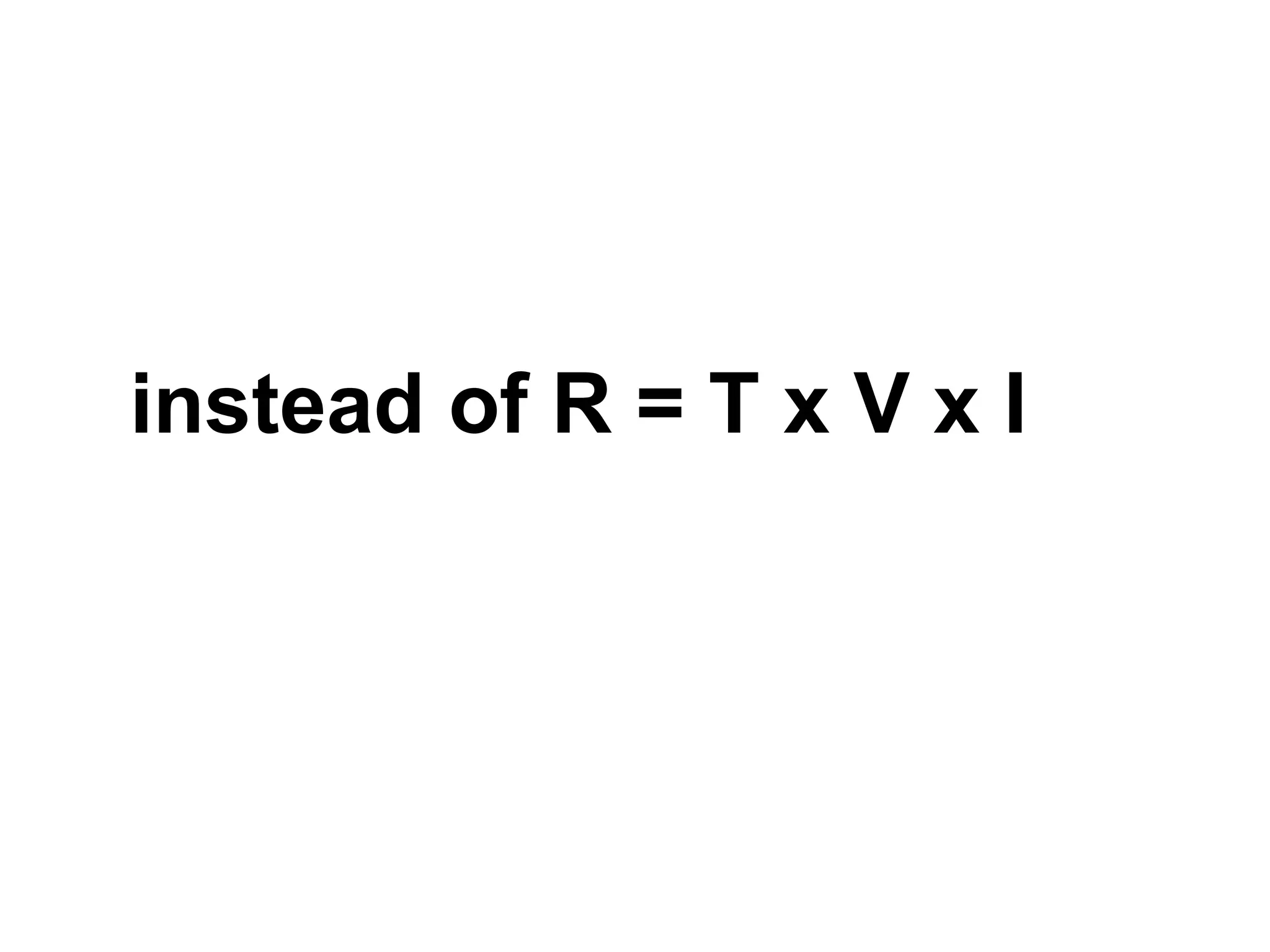The document discusses threat modeling and risk management. It introduces VERIS, an open framework developed by Verizon for categorizing cyber security incidents. VERIS breaks incidents down into metrics including demographics, a classification of the incident using an "A3" model of agents, actions and assets, details on discovery and mitigation, and impact classification including estimated losses. VERIS aims to enable pattern matching across incidents to better understand behaviors and risks. The presentation argues that a data-driven, behavioral approach is needed for effective risk management of complex adaptive systems.