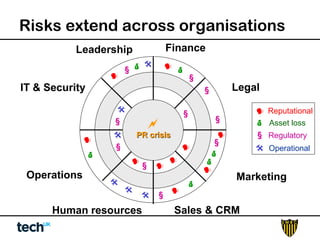
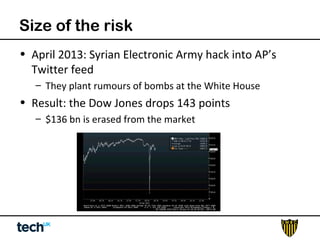
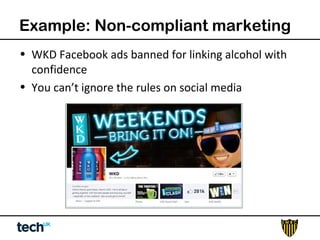
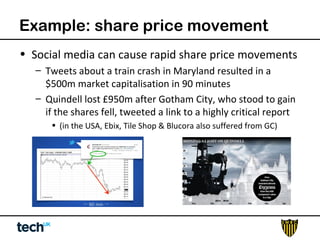
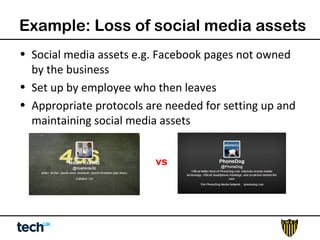
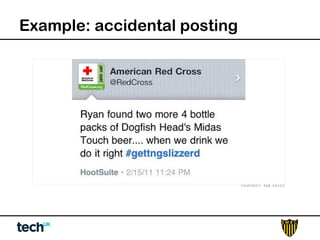
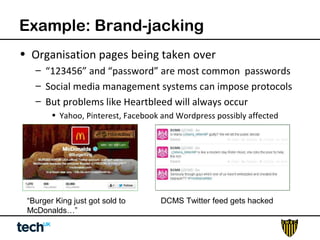
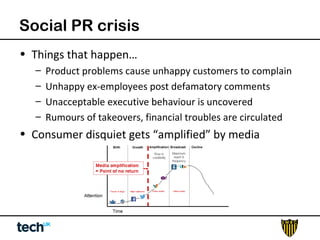
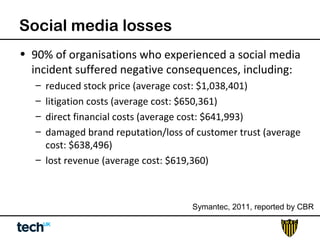
Social media risk exists across entire organizations and can impact areas like leadership, marketing, operations, and human resources. The document discusses how a lack of control over private social media accounts and use of personal devices increases risks. It provides examples of how risks have impacted companies through regulatory fines, loss of employees or market value. The document recommends organizations audit social media use, listen for potential issues, manage social media guidelines and content, prepare crisis responses, and archive social media conversations to manage growing online risks.