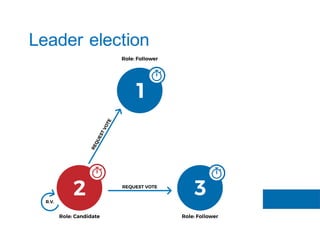
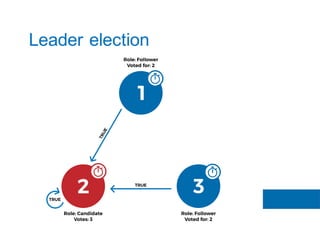
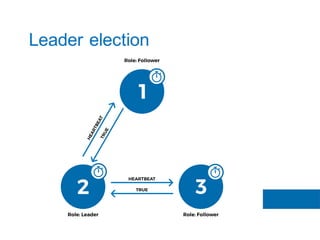
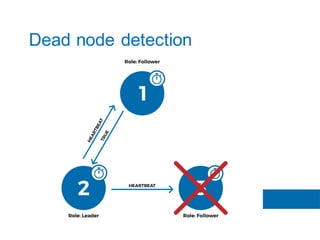
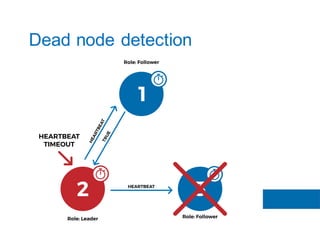
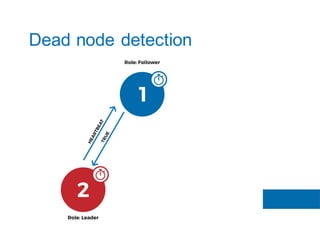
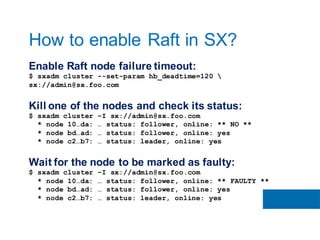
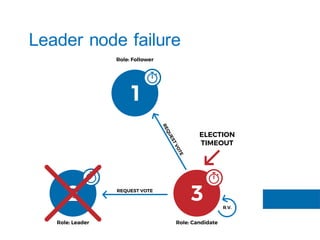
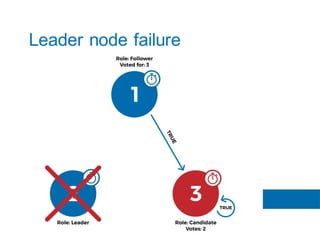
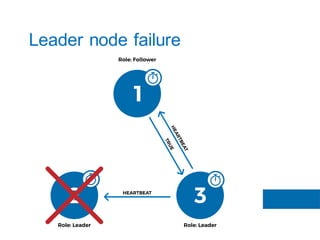
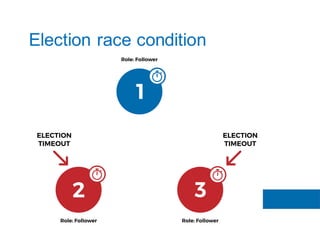
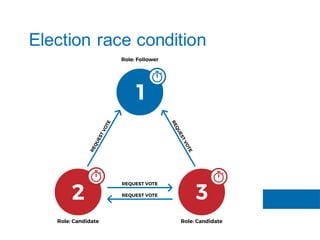
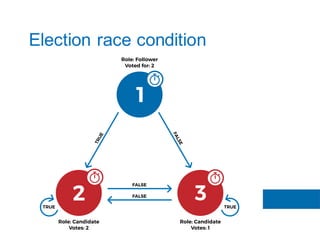
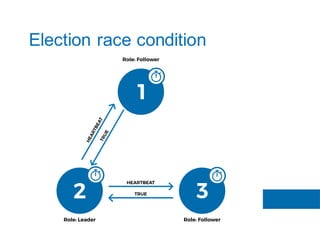
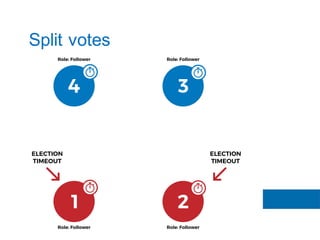
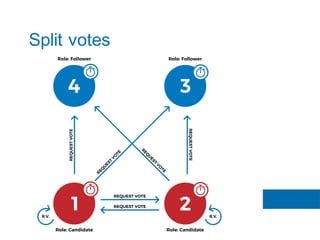
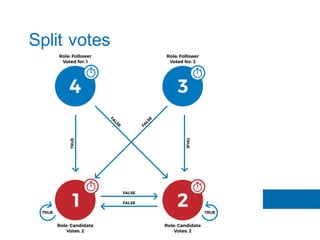
The document discusses the implementation of the Raft consensus algorithm to save three months of development time when building an S3-compatible cluster with high availability and fault tolerance. Raft was chosen over Paxos due to its straightforward implementation and comprehensive specifications. It includes details on leader election, node failure detection, and configuration parameters for enabling Raft in the SX cluster.