This document discusses how to configure HermesJMS to connect to an SSL-enabled WebSphere MQ queue manager without mutual authentication. It involves importing the self-signed certificate of the queue manager into the Java keystore and configuring HermesJMS to use the IBM MQ provider libraries and specify SSL settings to match the queue manager configuration. Testing showed that HermesJMS could successfully retrieve data over the SSL channel after making these configuration changes.
![ukplpzDWUJ/f7Kof6cizSxYgvVjKYD2f4fEfgKHPU8hs/4UO0czdOM6cPobLOU6k5I9zN8o4eFqm
V/iuPyhswriJG1gQH4f0dA1HL0Ruv9kbvt0m46qroYXU5Ka6slc=
-----END CERTIFICATE-----
HermesJMS JVM
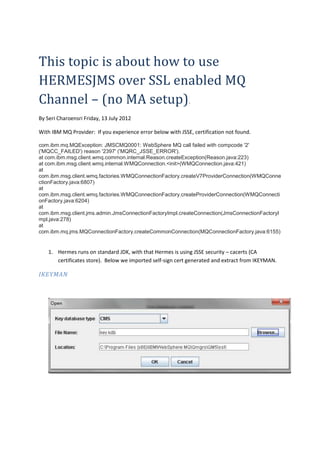
C:Program Files (x86)Javajdk1.6.0_13jrelibsecuritycacerts
Keytool
2. For self-sign cert from MQ, you will need to import the cert into cacerts keystore, so that
HERMES can hand-shake with MQ over SSL.
C:Program Files (x86)Javajdk1.6.0_13jrebin>keytool -import -trustcacerts -alias qm5
-file ..libsecurityQM12345-certQM5_cert.arm -keystore ..libsecuritycacerts
Enter keystore password: changeit (default JSSE CA keystore)
Owner: CN=qm5, C=US
Issuer: CN=qm5, C=US
Serial number: -54f5d8343411e1b8
Valid from: Fri Jul 20 21:14:59 EST 2012 until: Sun Jul 21 21:14:59 EST 2013
Certificate fingerprints:
MD5: 7A:2C:20:3A:CE:94:2B:44:F0:C4:65:C8:FD:A4:17:9F
SHA1: B5:D0:68:84:75:D2:6D:ED:61:AC:C6:32:87:F5:0C:69:28:AC:C0:6E
Signature algorithm name: MD5withRSA
Version: 3
Trust this certificate? [no]: y
Certificate was added to keystore
C:Program Files (x86)Javajdk1.6.0_13jrebin>
HERMES JMS setting
IBM MQ 7 Provider Lib: - don’t need all of those lib – I am lazy to pick just the jars required.](https://image.slidesharecdn.com/hermesjms-ibmmq-sslchannel-release1-120721192809-phpapp01/85/Hermes-jms-ibmmq-ssl-channel-release1-3-320.jpg)