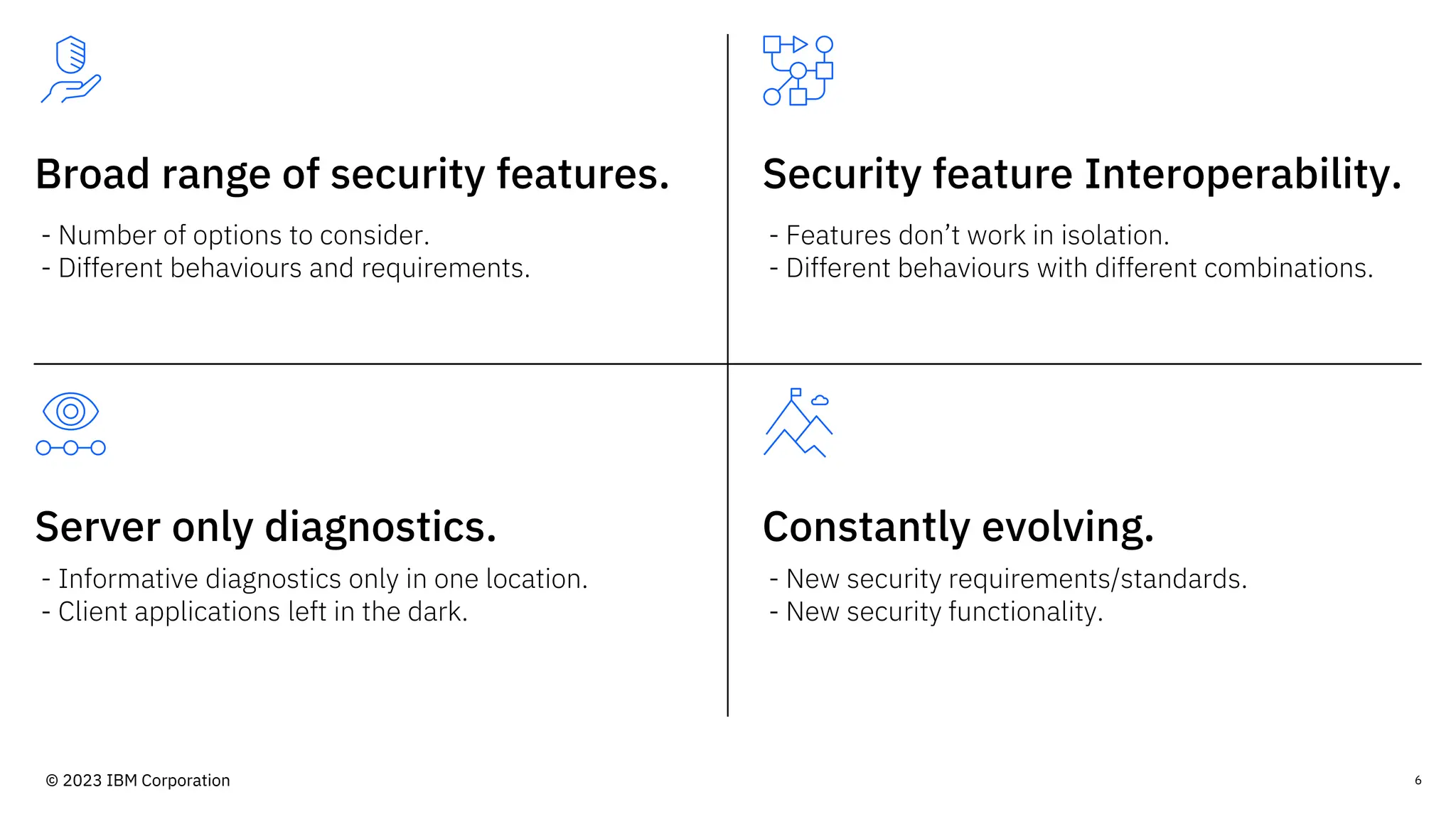
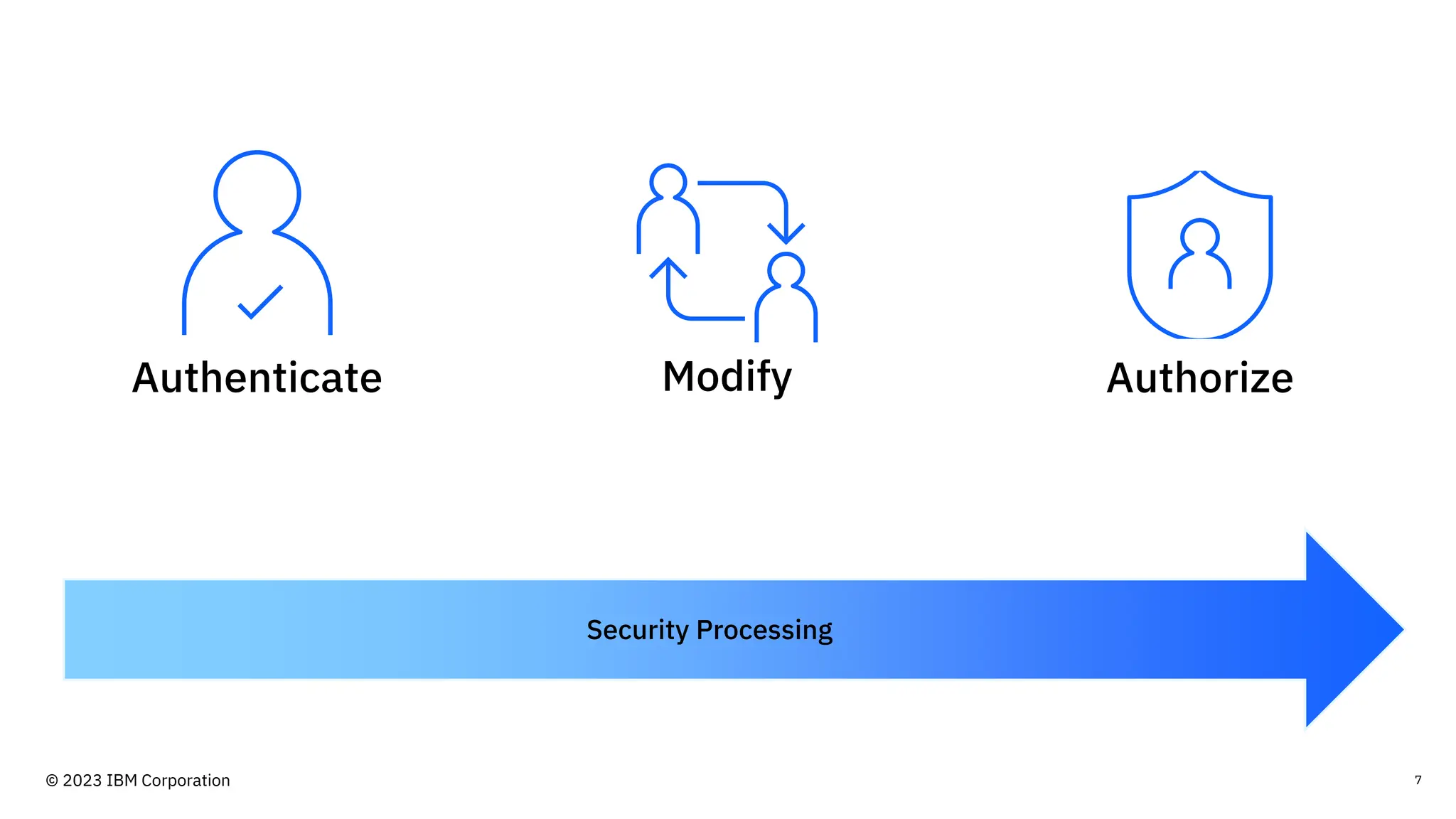
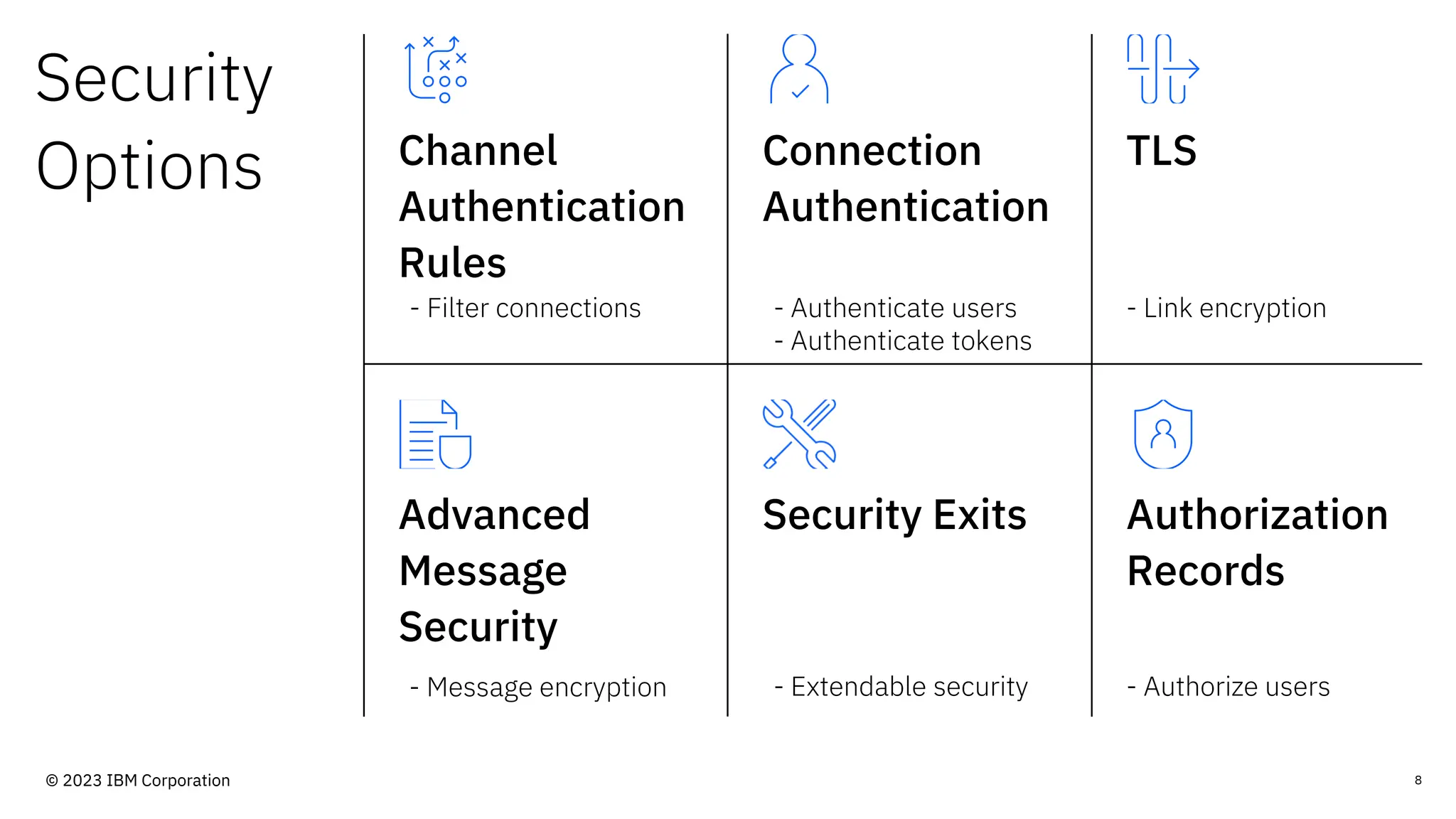
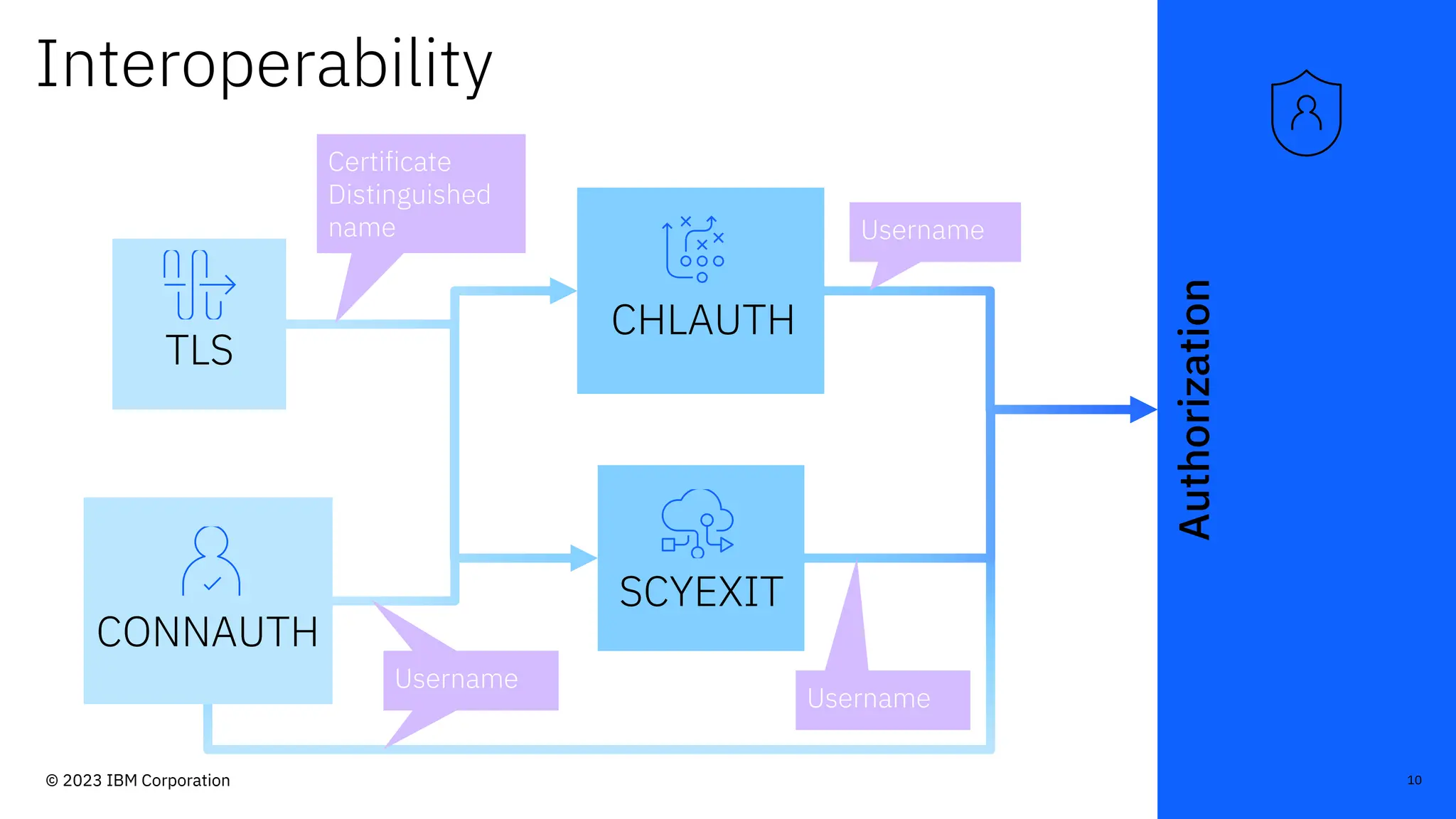
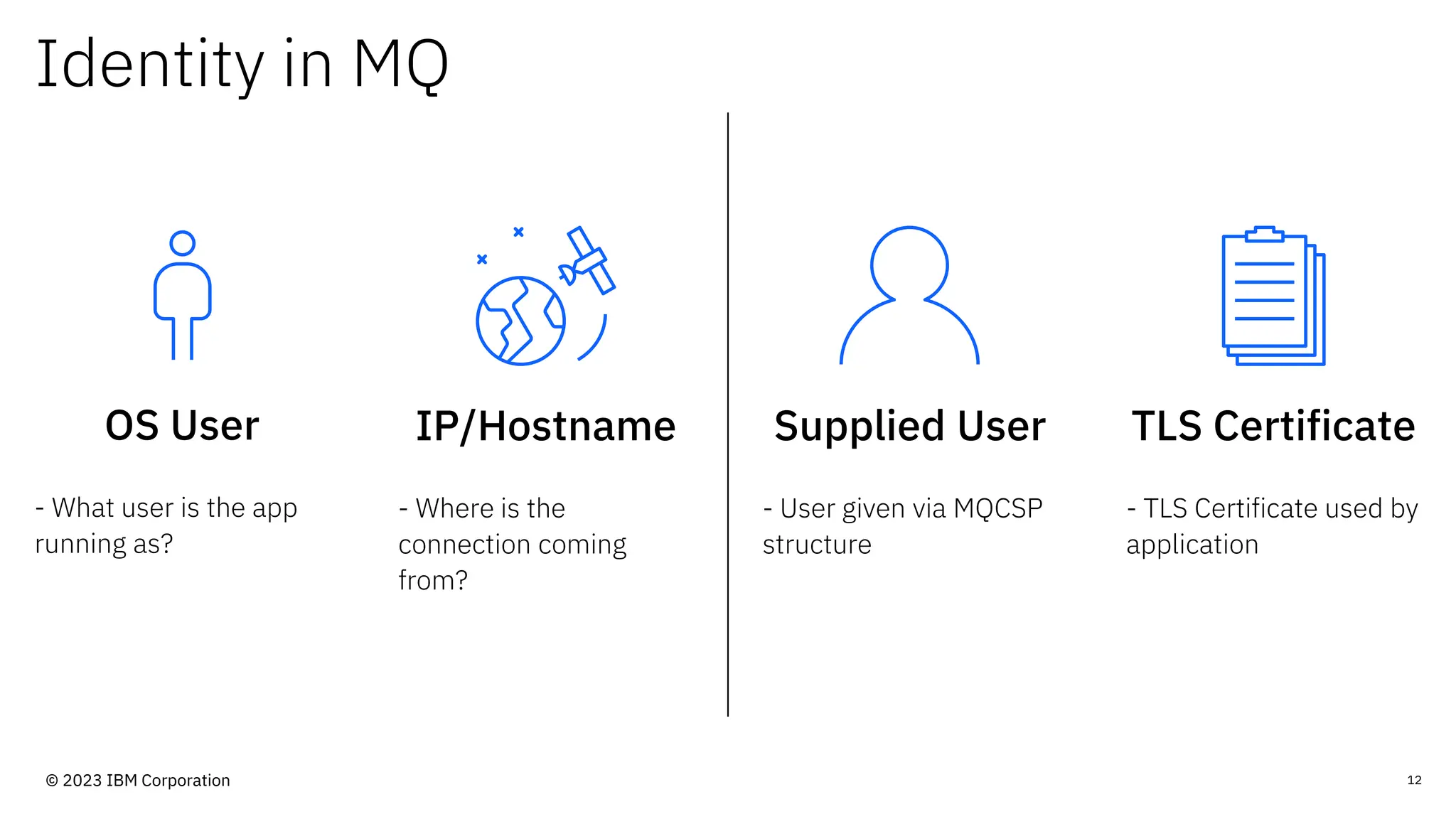
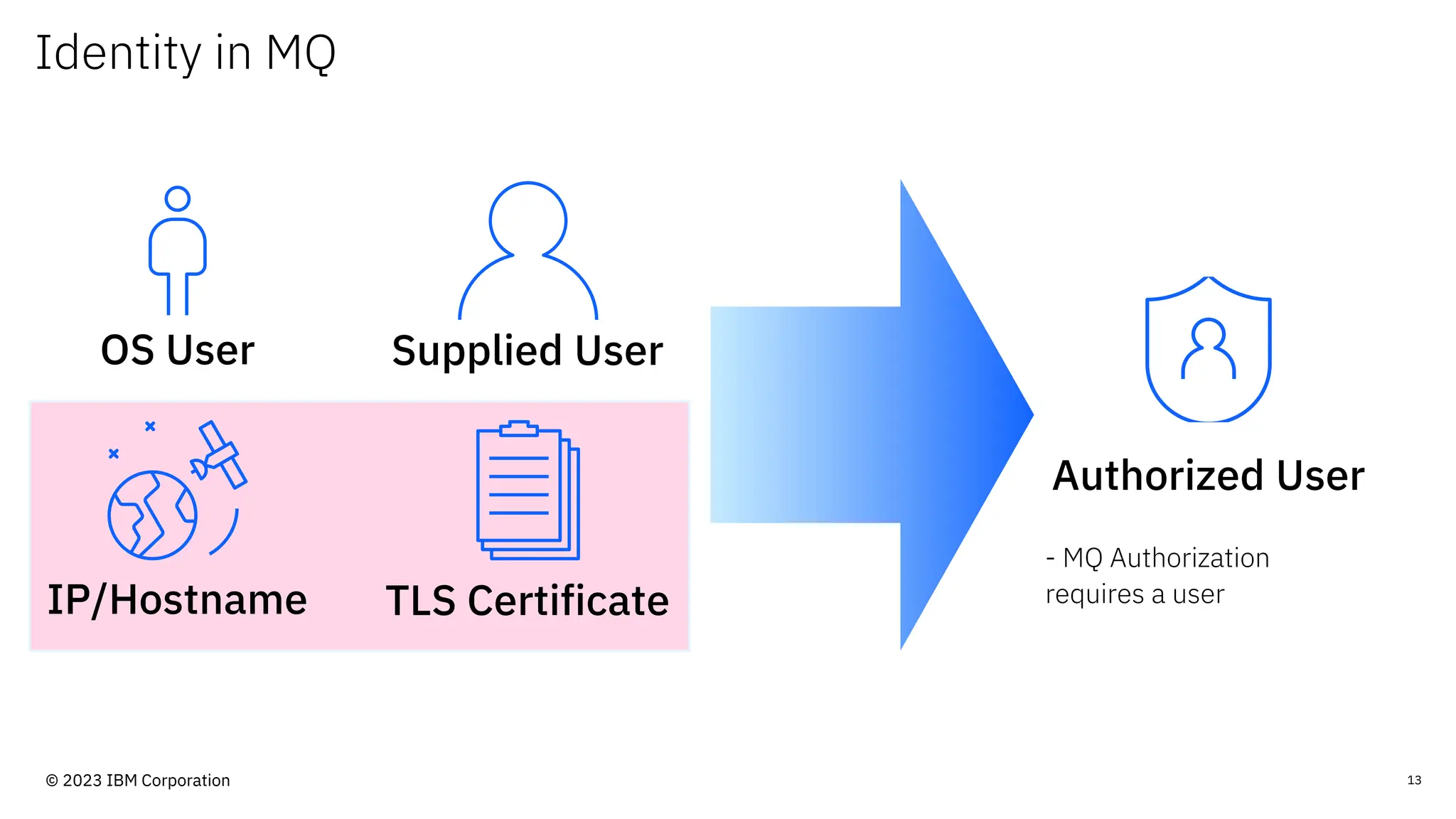
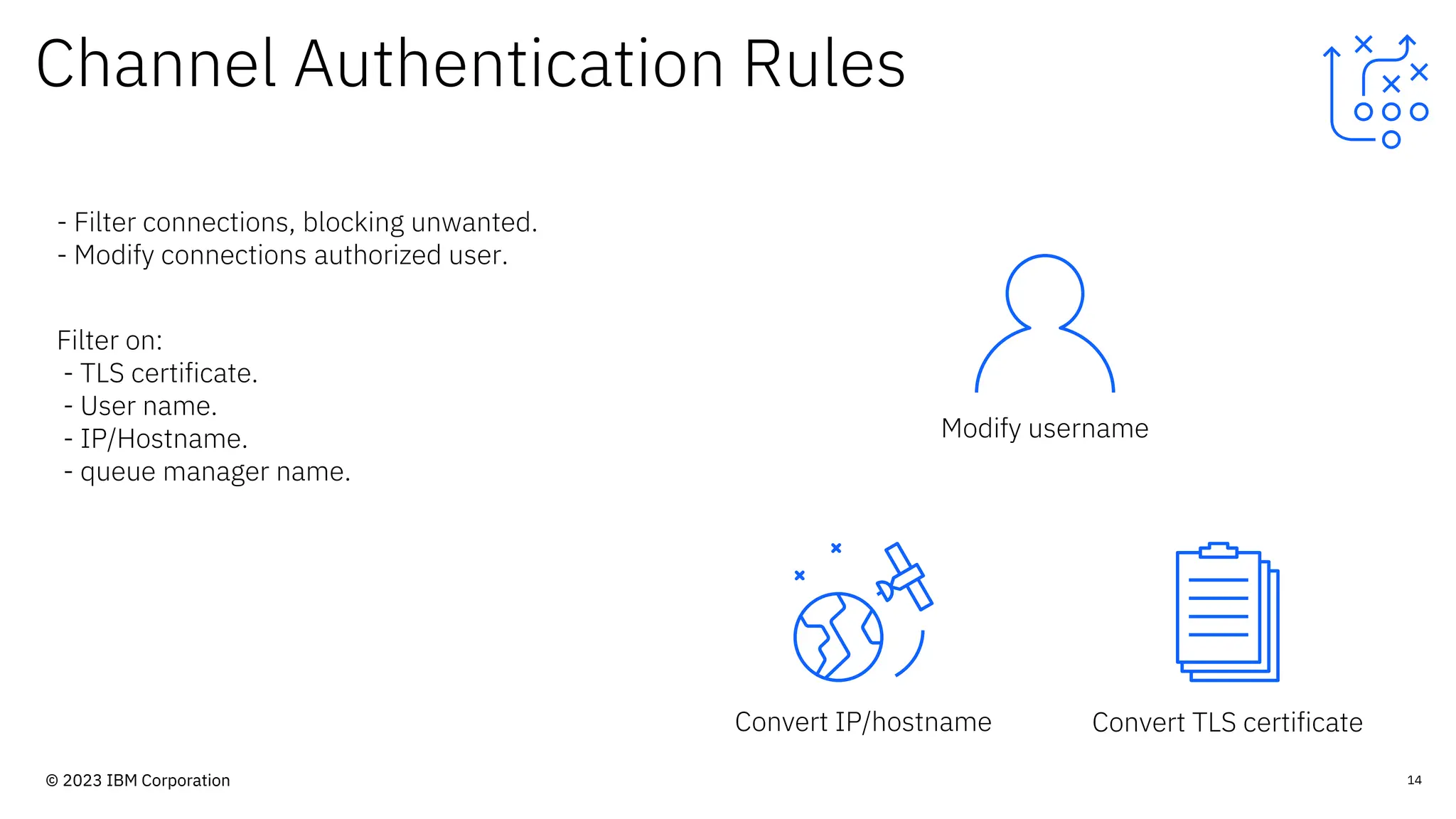
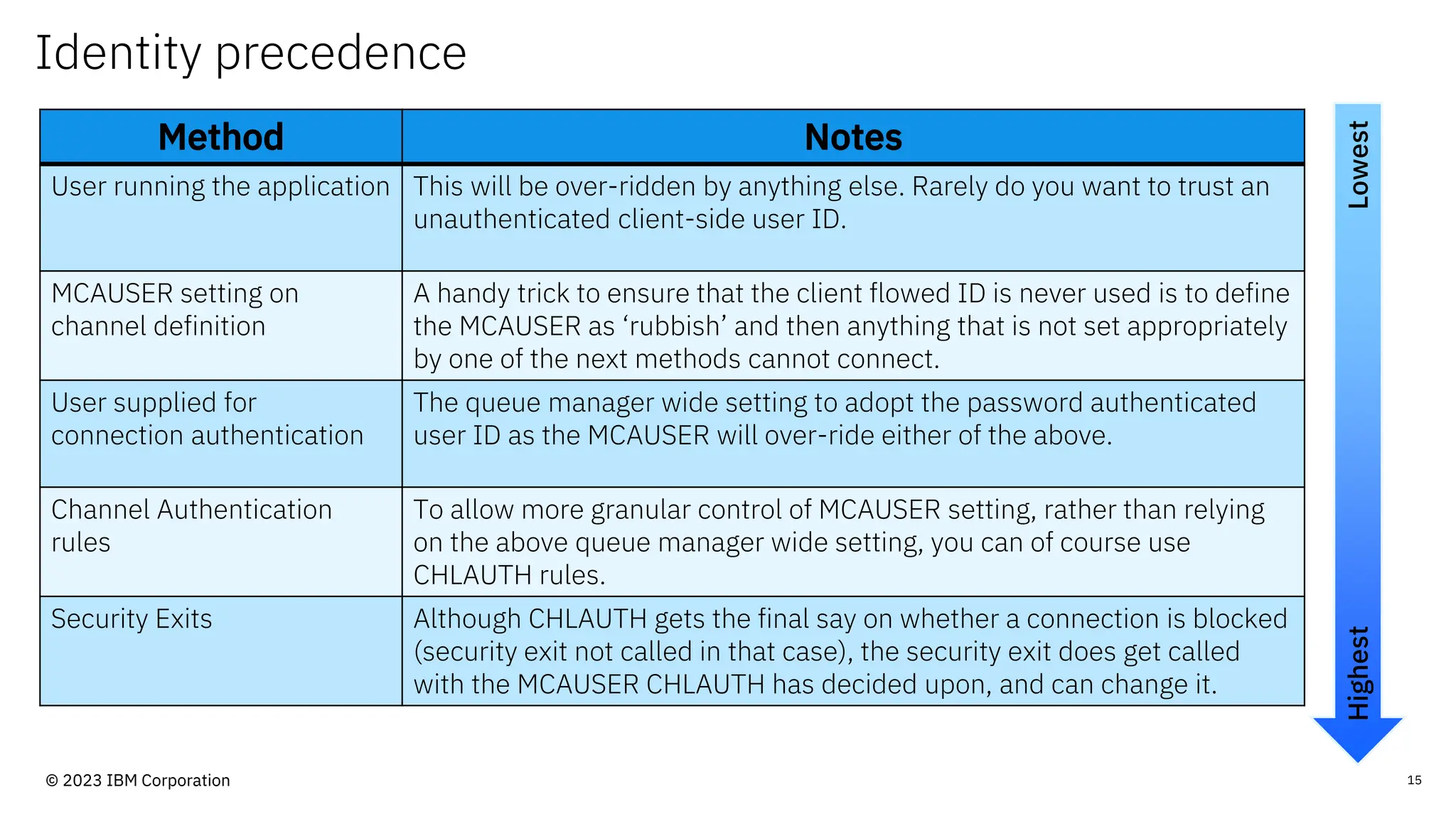
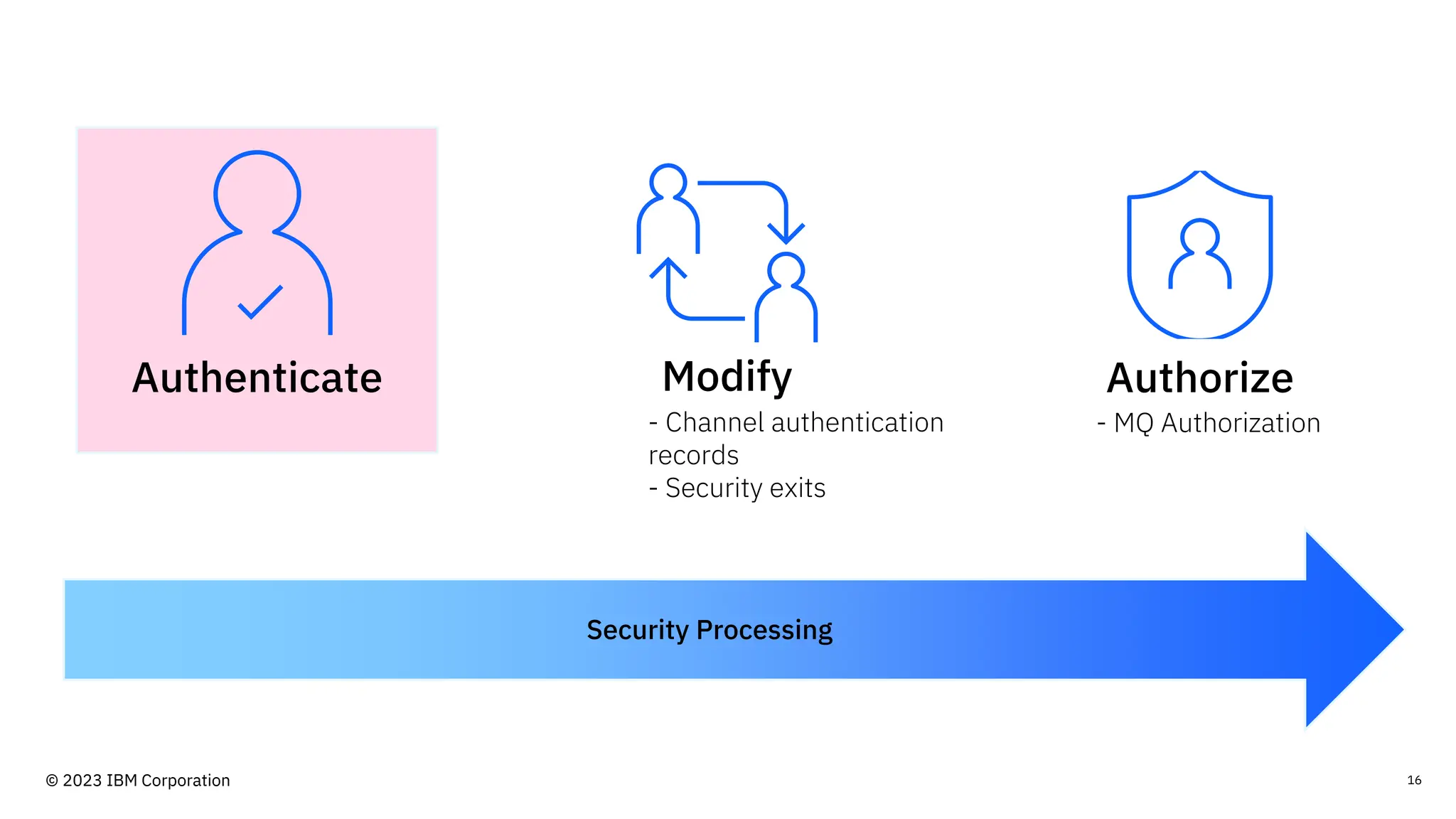
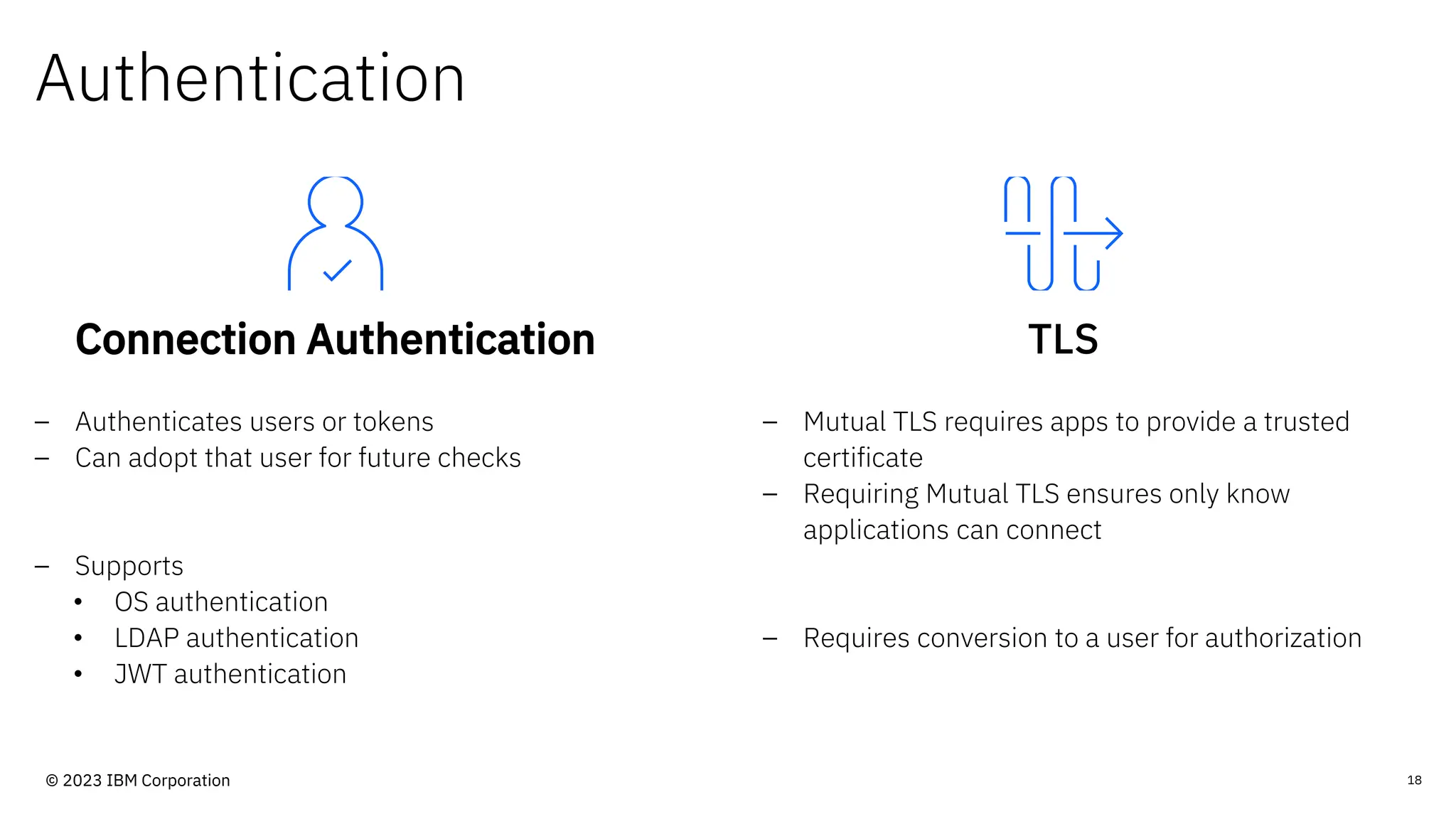
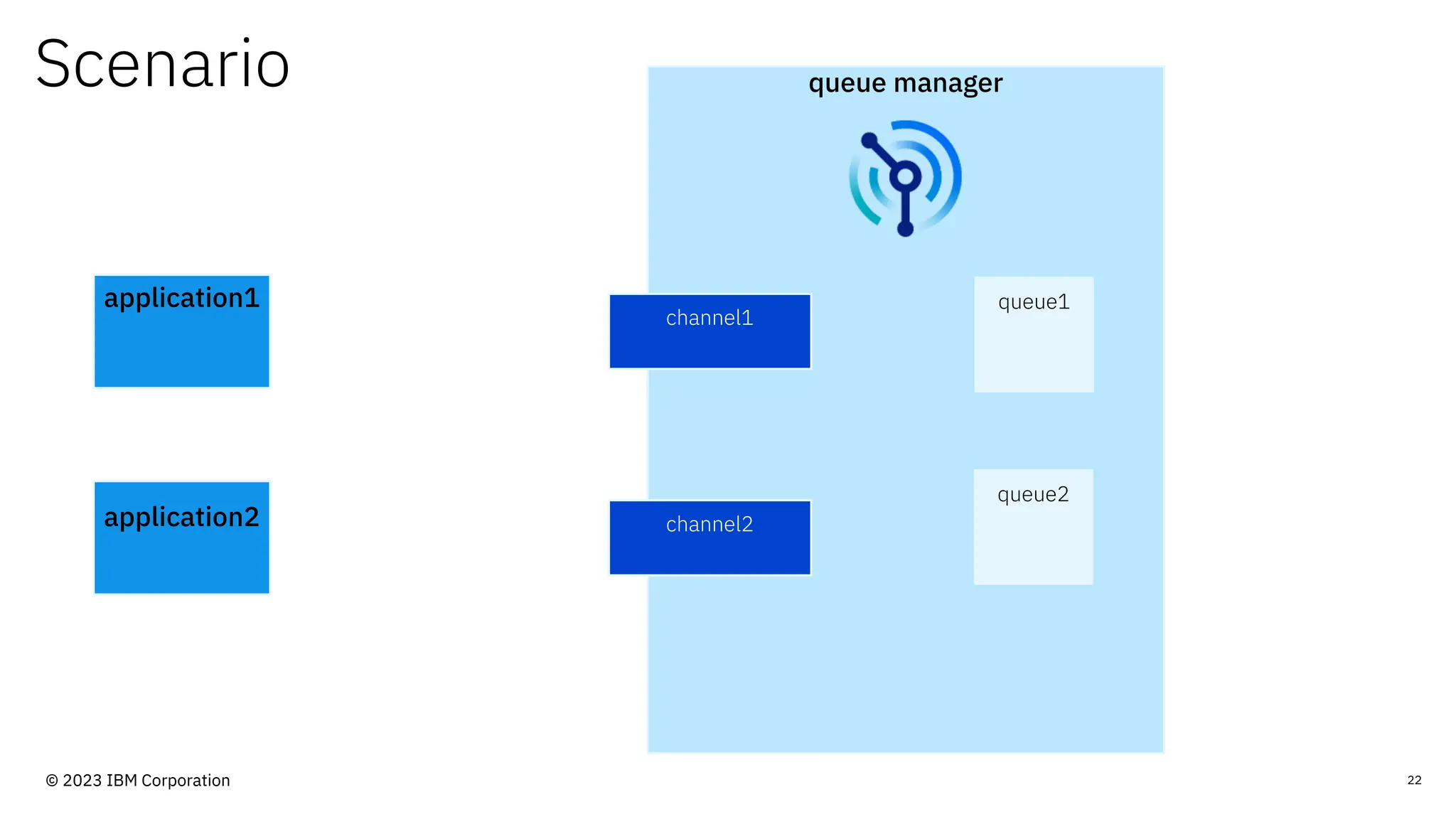
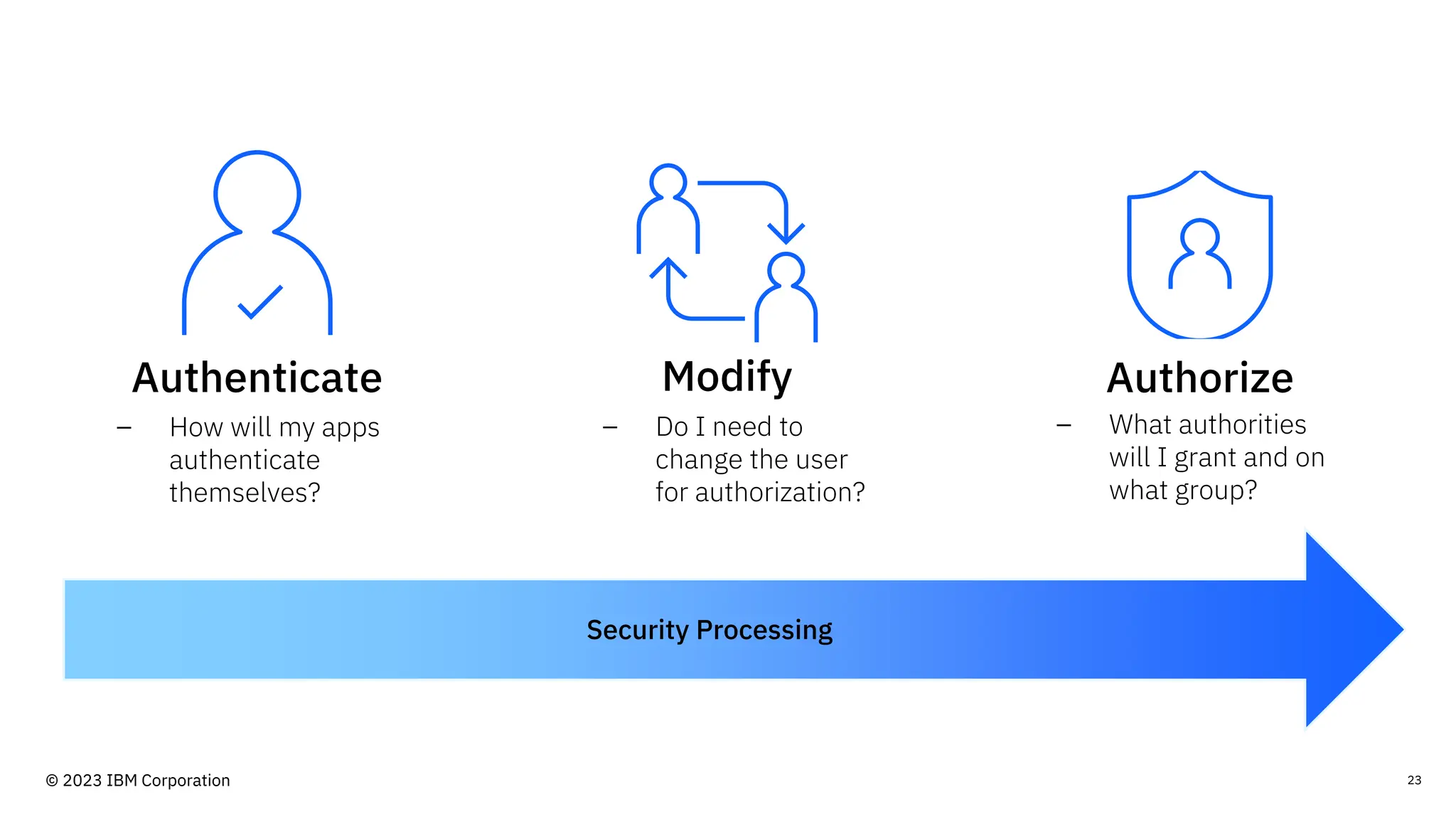
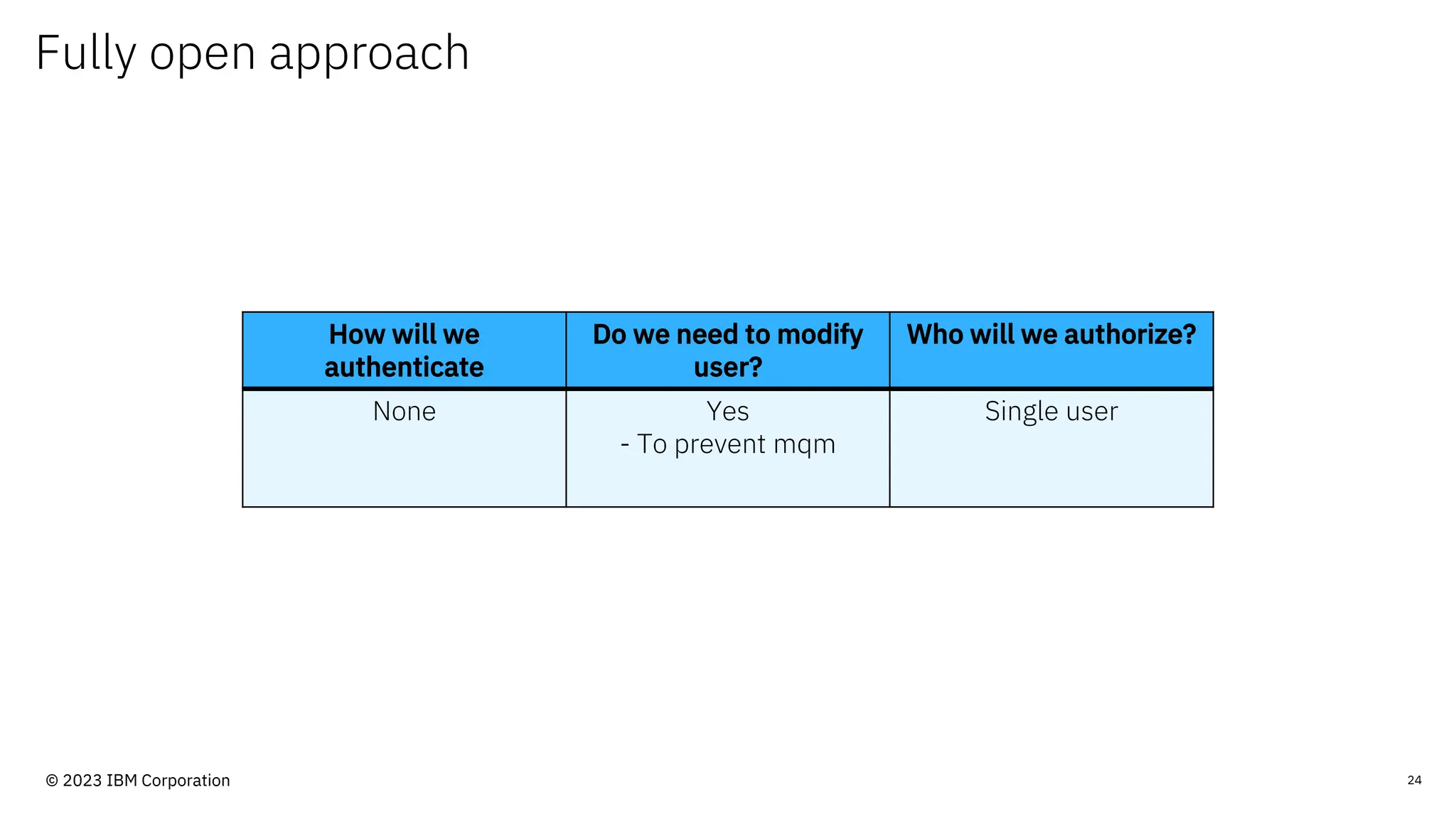
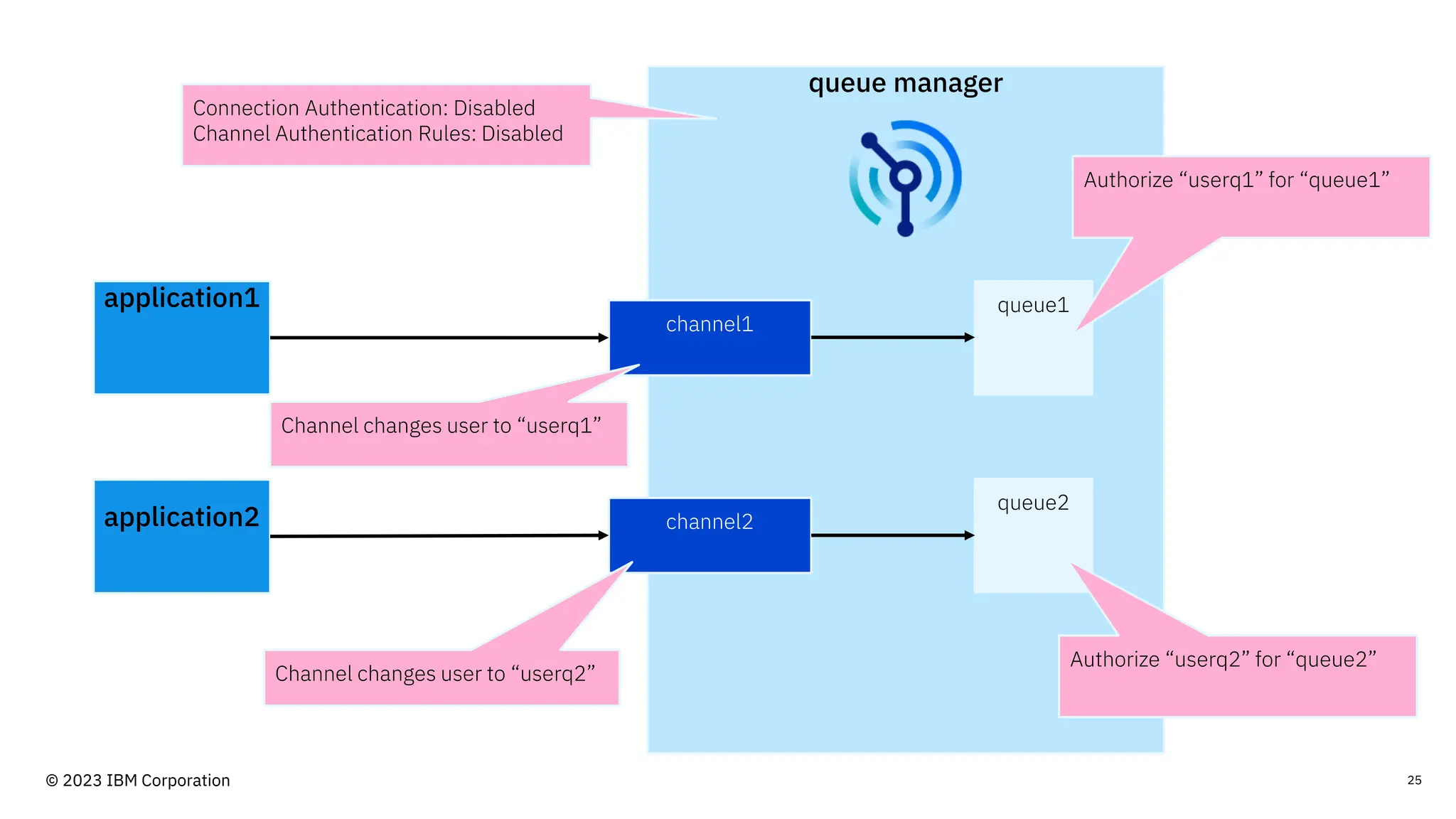
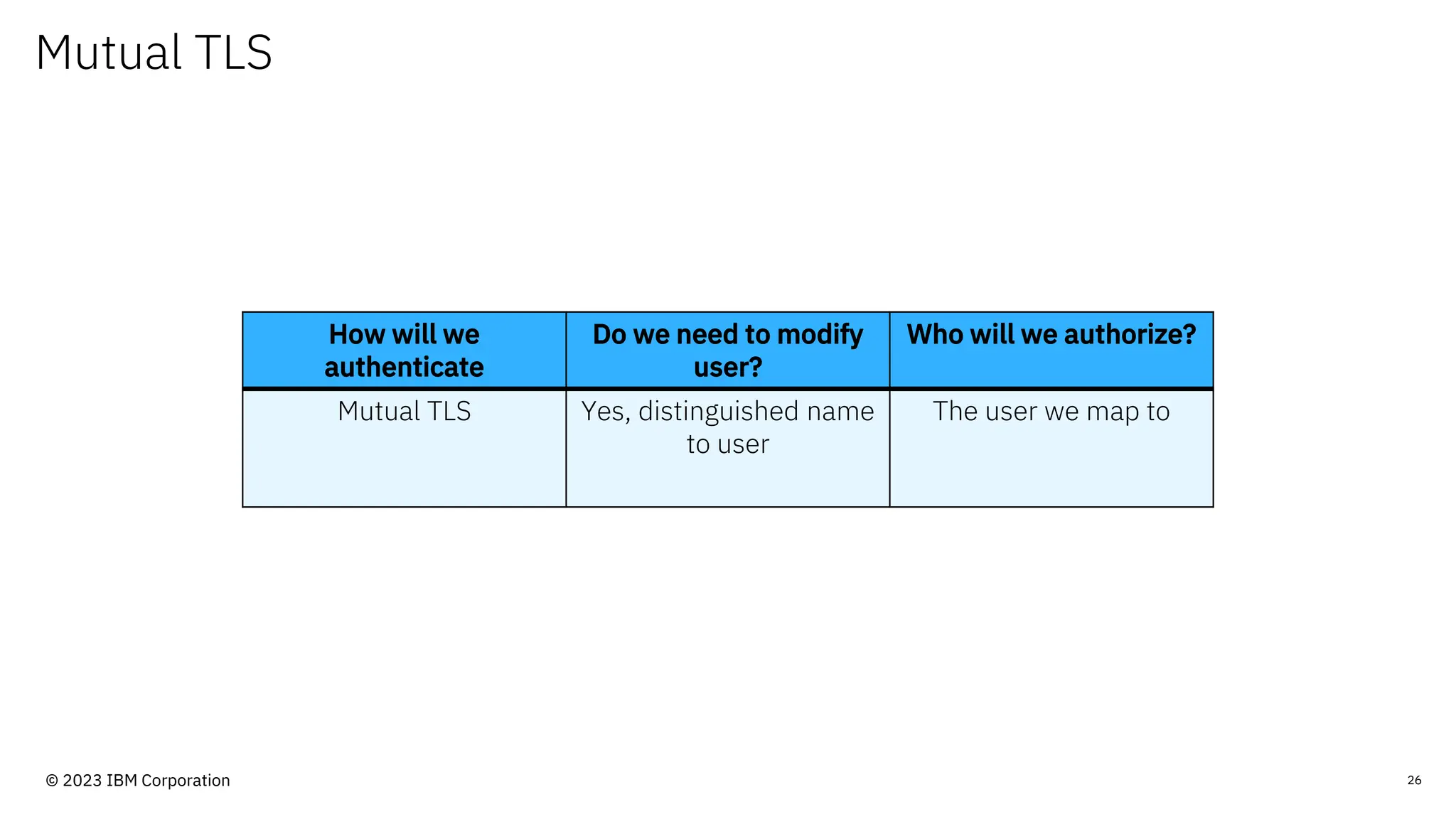
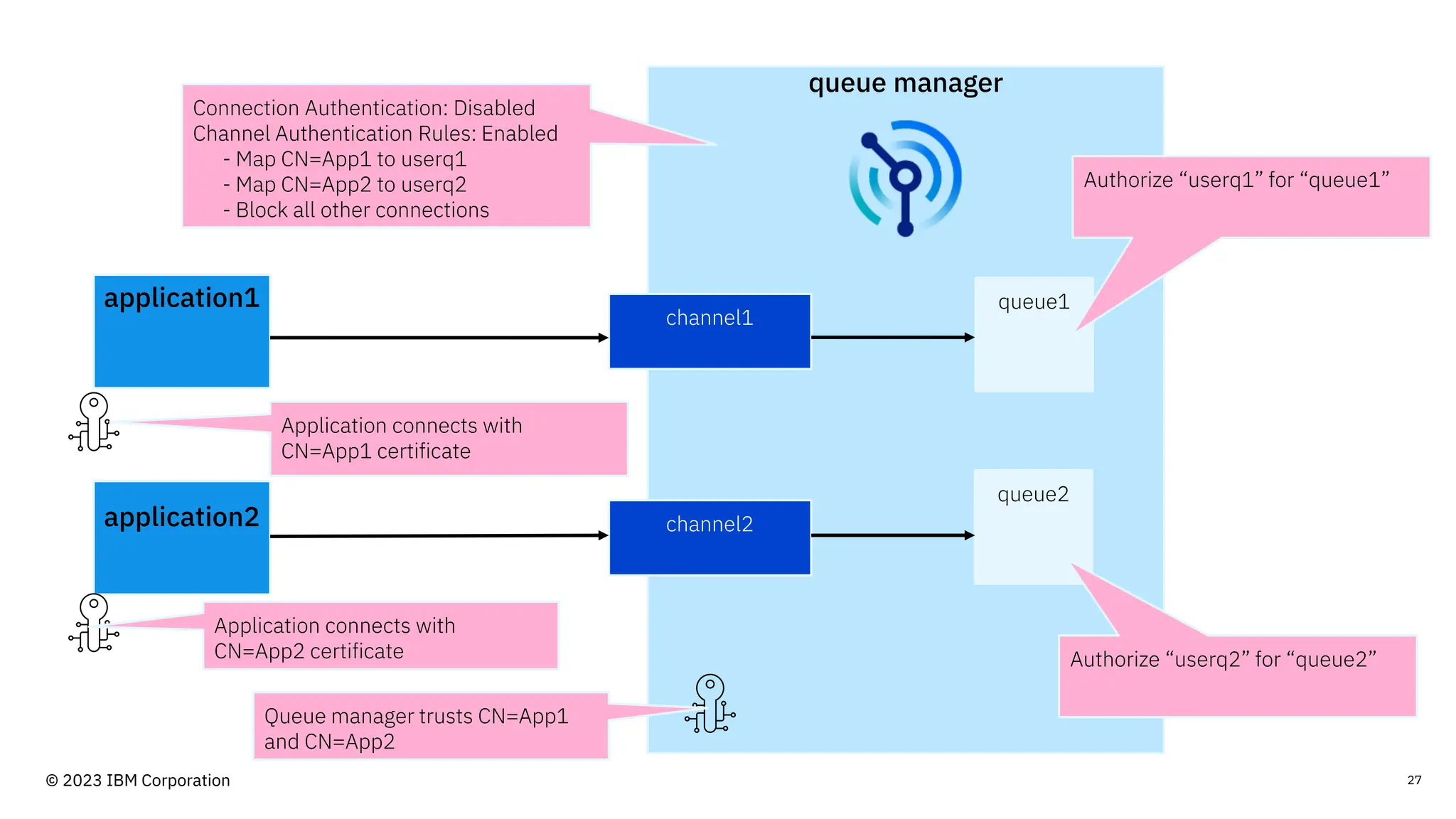
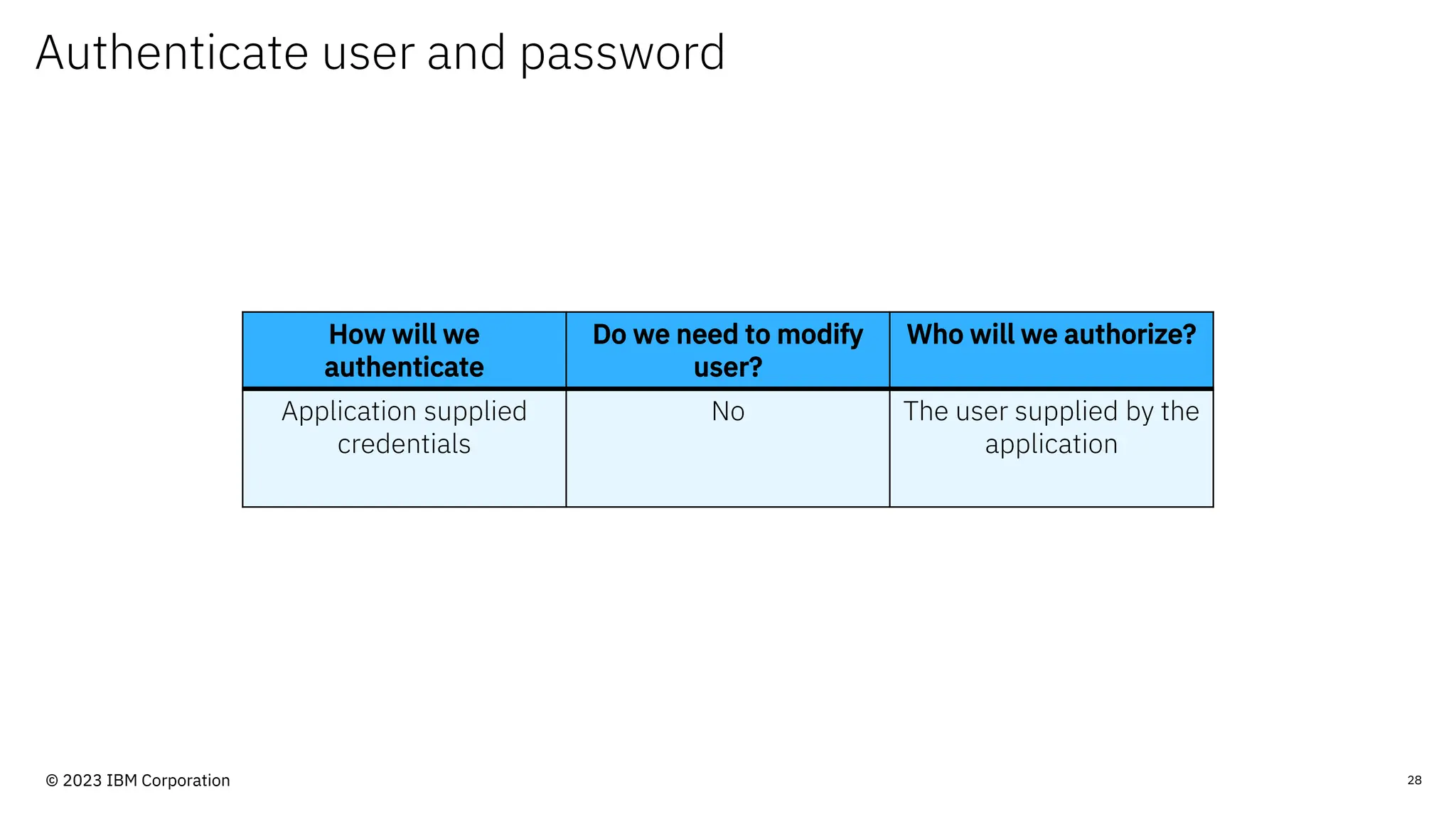
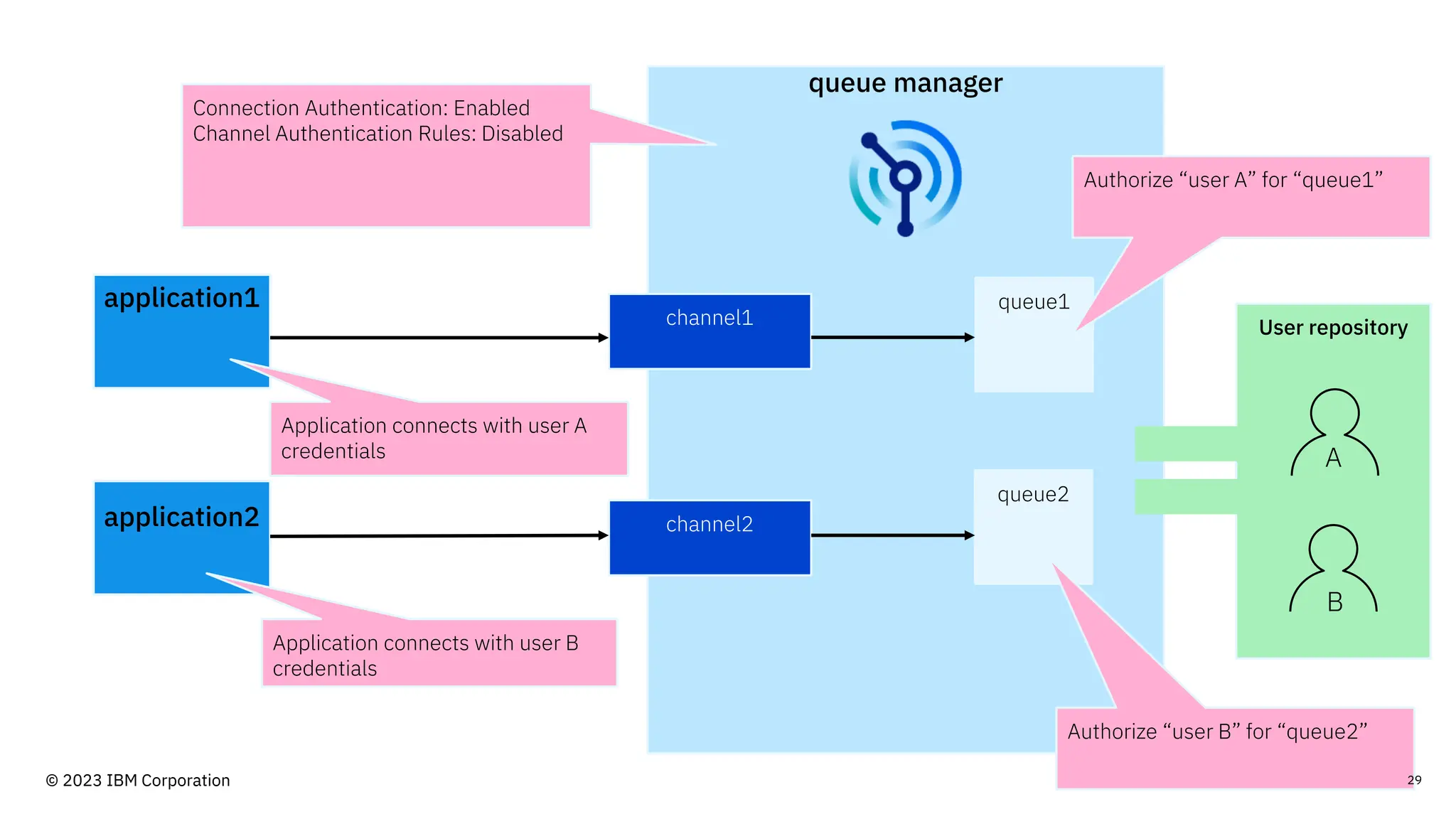
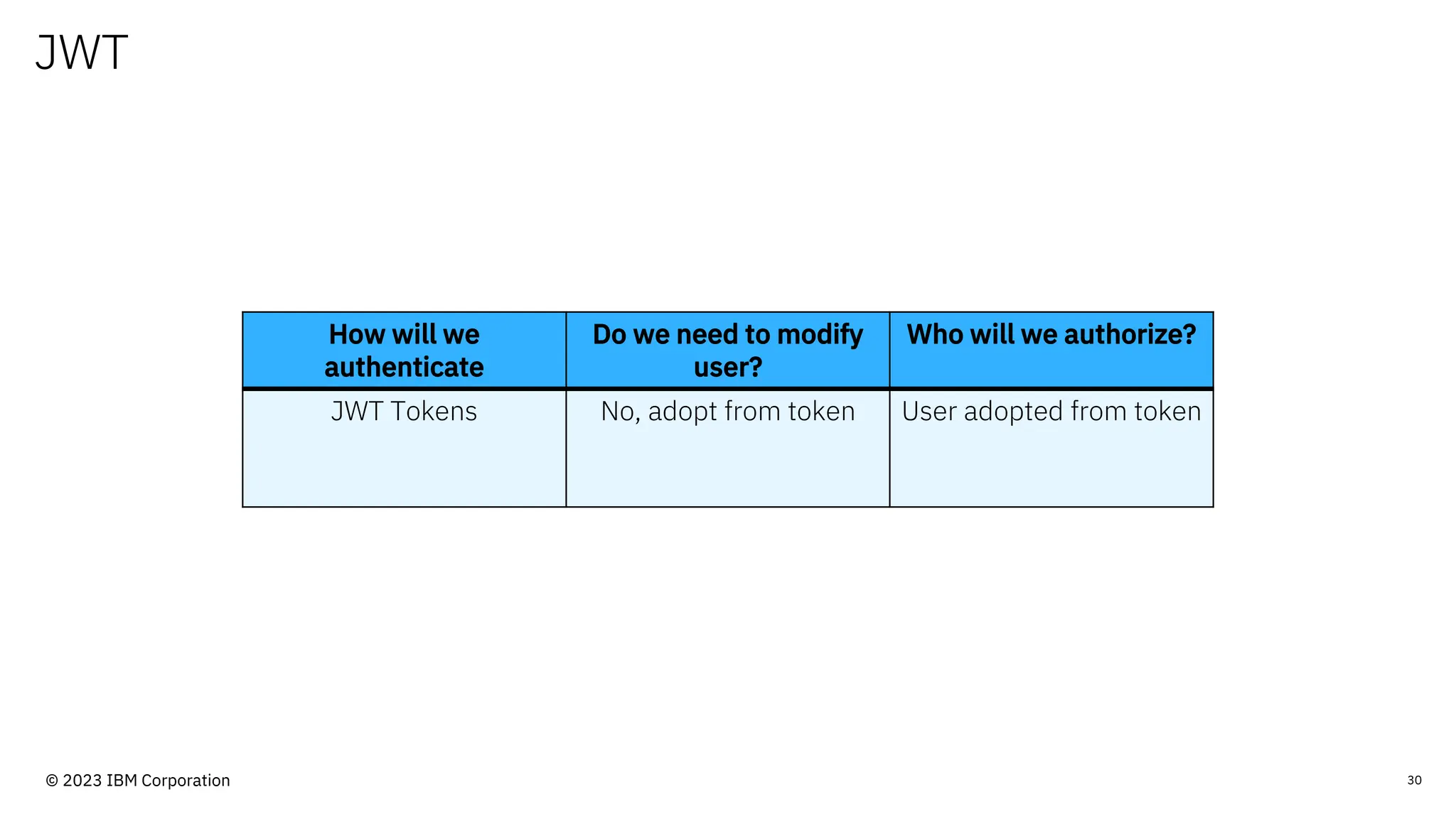
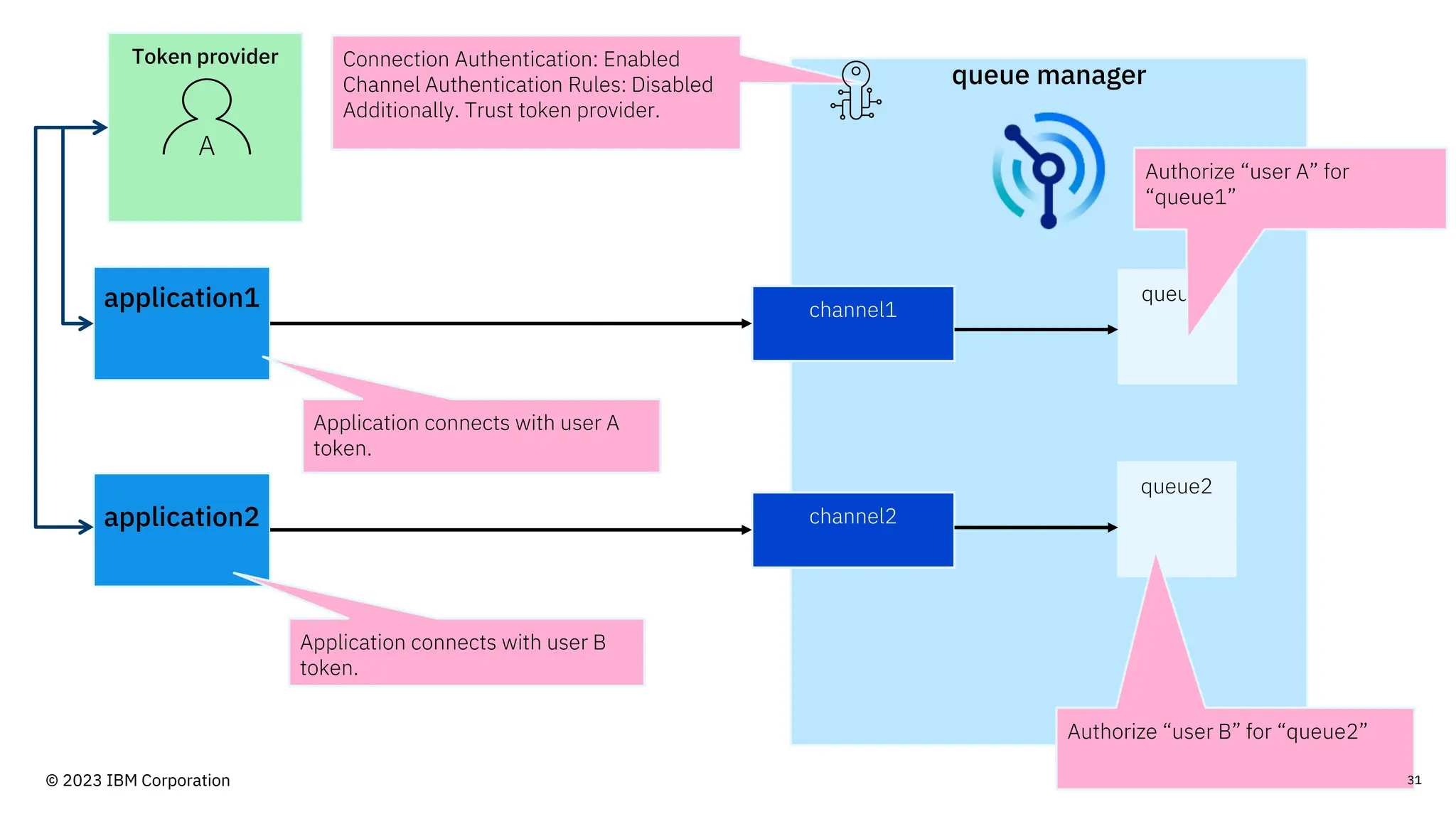
The document discusses IBM MQ security, outlining various security options, authentication methods, and configuration examples. It emphasizes the importance of understanding interoperability among security features and the evolving nature of security requirements. Additionally, it highlights practical use cases for implementing authentication and authorization within the MQ environment.