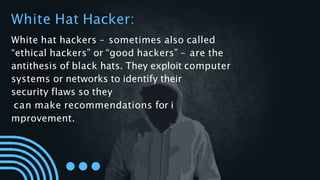
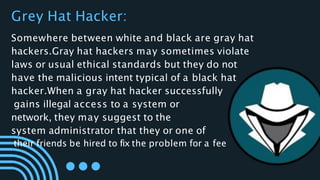
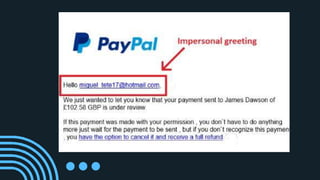
The document outlines the concept of cyber security, emphasizing its role in defending electronic systems from malicious attacks. It details various aspects of cyber security including network, application, information, and cloud security, as well as different types of hackers and hacking methods. Key hacking techniques such as phishing, malware injection, and password cracking are also discussed, along with recommendations for protection.