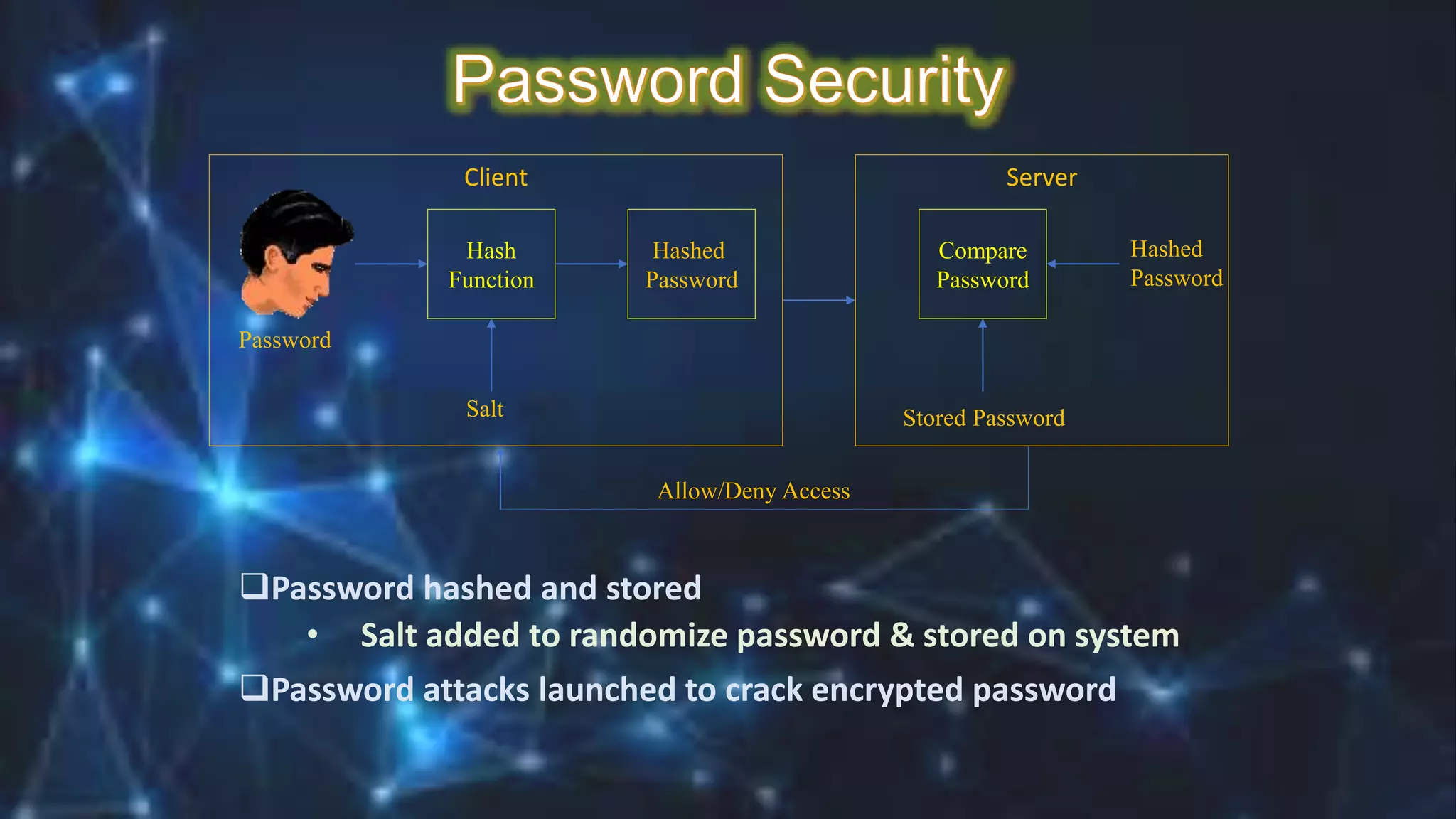
This document contains a student's details - name, roll number, department, semester and subject code. It then discusses various types of cyber attacks like hacking, spoofing, denial of service attacks and password cracking techniques. It explains concepts like IP spoofing, email spoofing, session hijacking and different methods used by hackers to conduct password cracking like dictionary attacks and brute force methods.