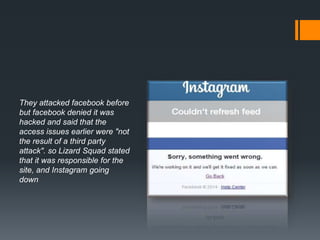
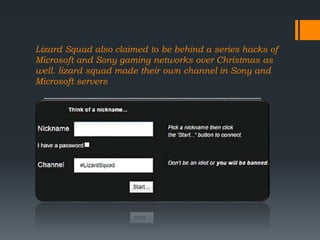
Hackers can be classified into three main types: white hat hackers who hack to find security vulnerabilities, black hat hackers who hack with malicious intent, and grey hat hackers whose intentions are unclear. The document discusses different hacking techniques like using Trojan horses to gain access to systems. It provides examples of hacking incidents like the Sony Pictures hack believed to be done by North Korea in response to a movie, and attacks on gaming networks by the hacking group Lizard Squad over Christmas to demonstrate security weaknesses in large companies like Microsoft and Sony.