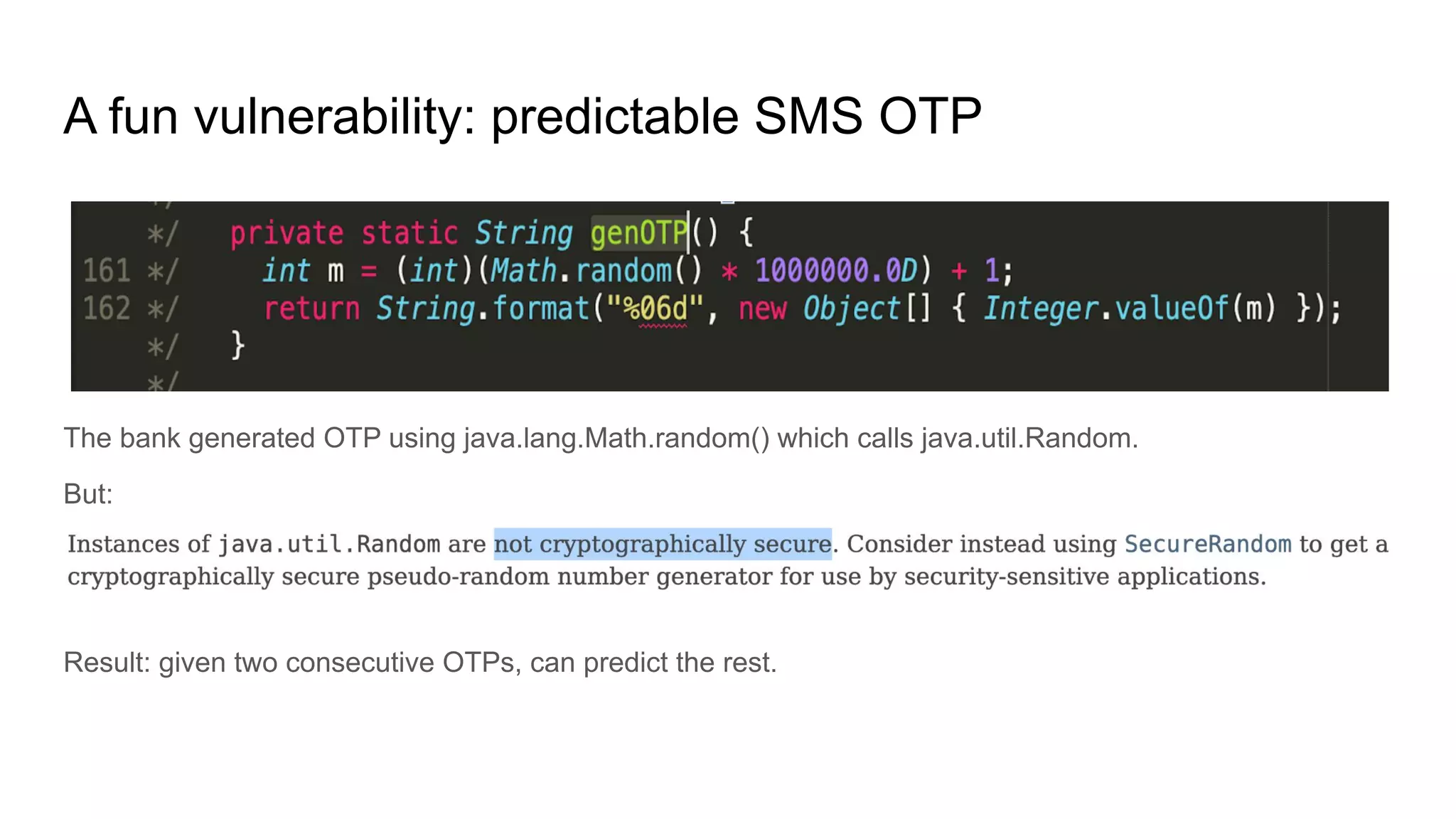
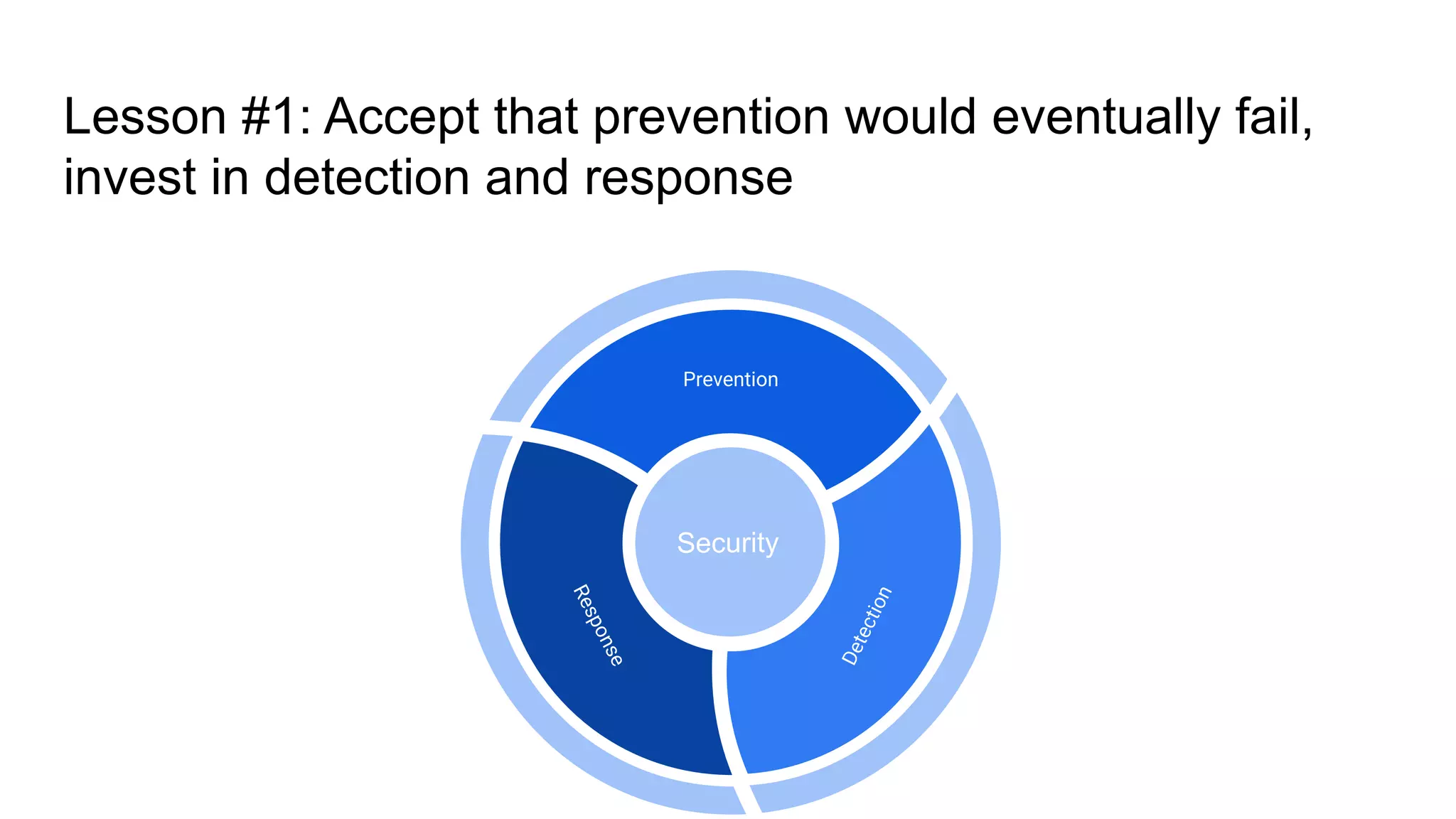
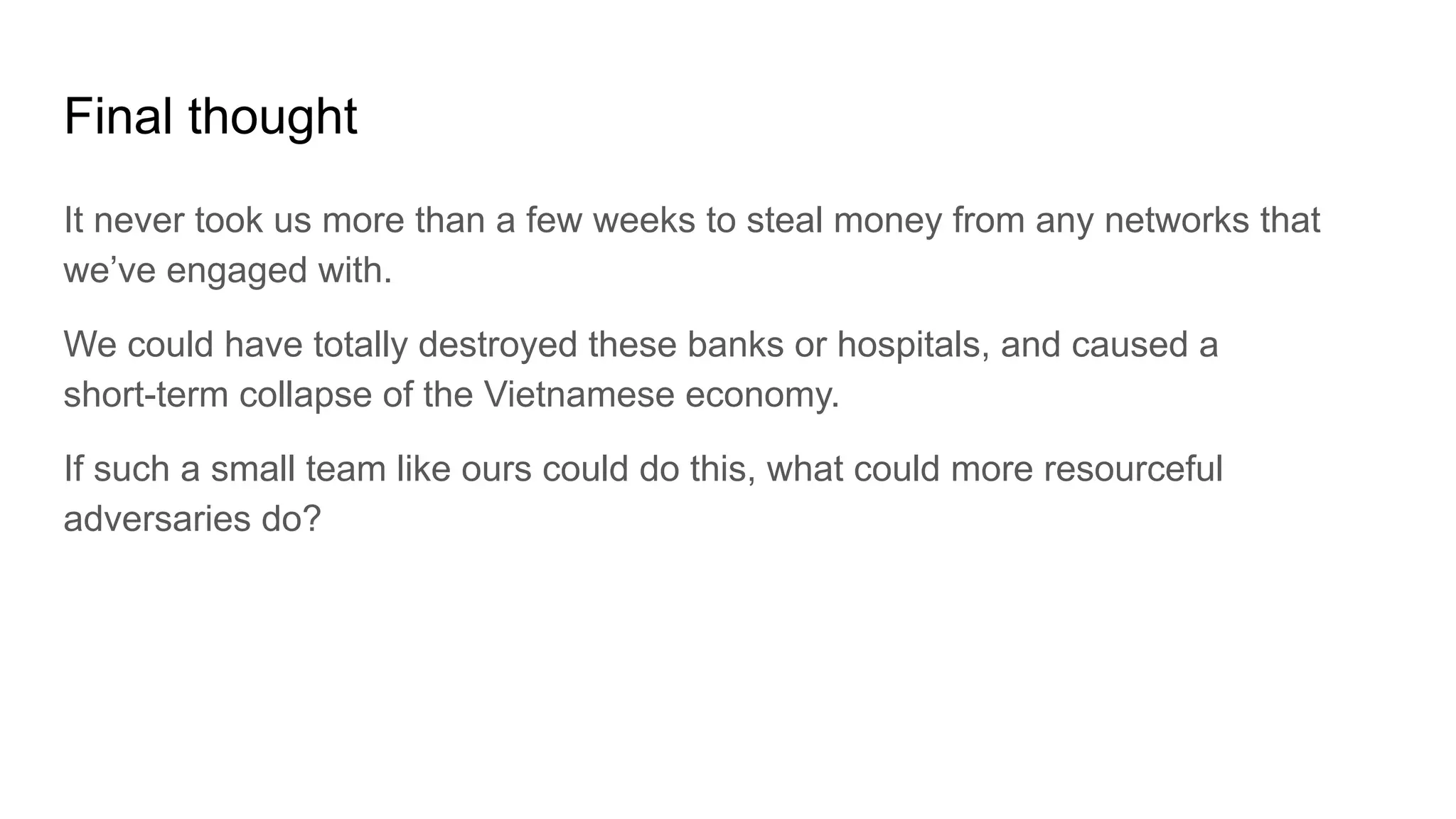
Tài liệu trình bày những bài học từ việc hack và bảo vệ các mạng máy tính của ngân hàng Việt Nam, nhấn mạnh rằng sự phụ thuộc vào an toàn thông qua sự mơ hồ đã dẫn đến nhiều lỗ hổng bảo mật nghiêm trọng. Các tác giả đã thành công trong việc chiếm đoạt tiền từ tài khoản ngân hàng thông qua các phương pháp kỹ thuật phá vỡ mã và đã đưa ra nhiều khuyến nghị nhằm cải thiện an ninh mạng. Cuối cùng, tài liệu cảnh báo về việc các nhóm tội phạm có khả năng gây thiệt hại lớn nếu có đủ nguồn lực.






![“Instead of reverse engineering, why don’t
we just hack [the bank] to steal their
source code?”
An Trịnh](https://image.slidesharecdn.com/publiclessonsfromyearshackinganddefendingvietnamesebanks-220906055218-91525f7f/75/Grokking-Techtalk-46-Lessons-from-years-hacking-and-defending-Vietnamese-banks-14-2048.jpg)