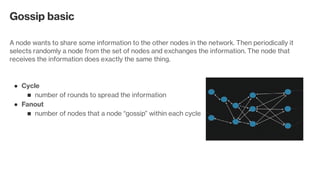
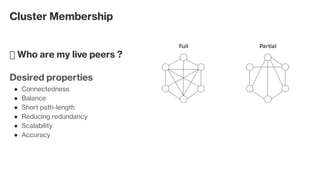
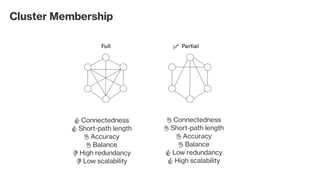
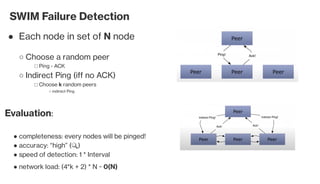
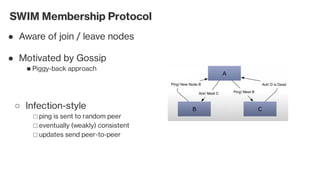
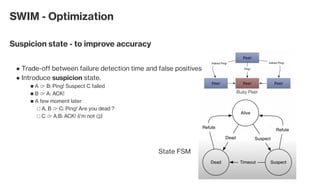
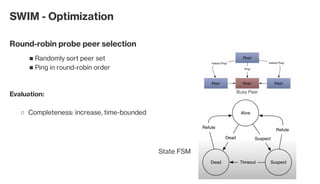
The document discusses the gossip protocol in computer science, which facilitates peer-to-peer communication by mimicking the way rumors spread in society. It highlights the protocol's advantages, including scalability, fault tolerance, and robustness, and outlines its applications in areas like failure detection, database replication, and cluster membership. Additionally, it reviews key models and properties of gossip protocols, and mentions specific implementations and applications such as the SWIM protocol and associations with systems like Cassandra and AWS.