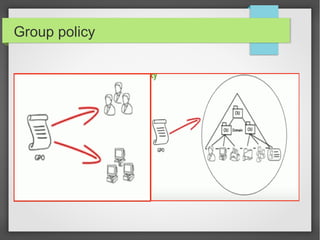
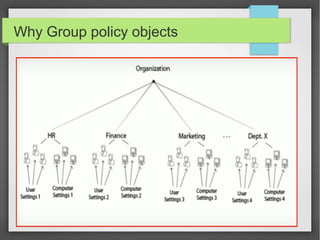
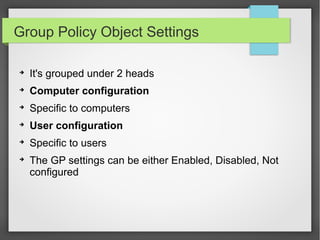
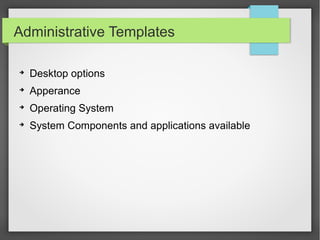
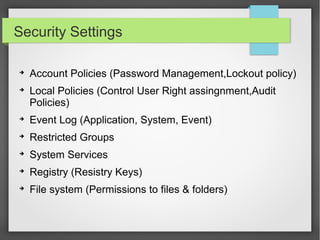
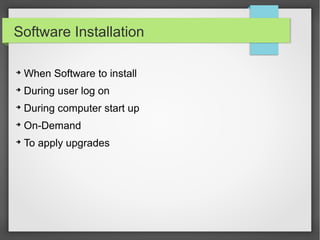
This document discusses group policy objects in Active Directory. It covers the components of group policy including the server and client components. The server component uses the Microsoft Management Console to specify policies while the client component interprets and applies the settings. Group policies can be applied in many areas like administrative templates, security settings, software installation, and scripts. Administering group policies involves using the Group Policy Management Console and Group Policy Object Editor. Group policies provide benefits like centralized control, reliable security, cost savings, and reduced technicians.