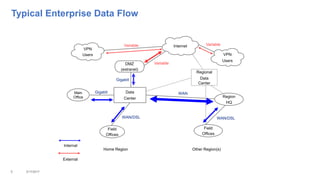
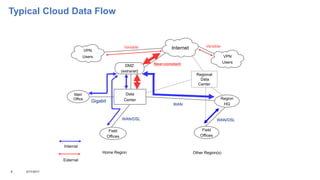
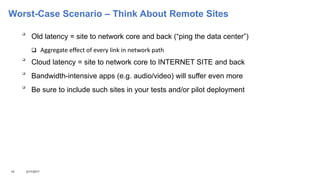
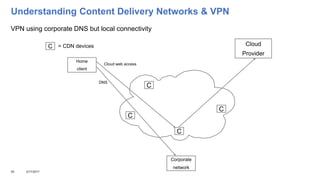
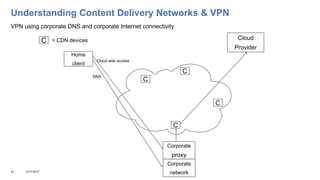
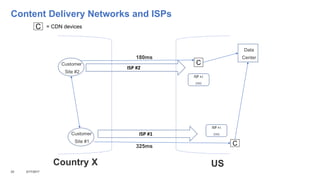
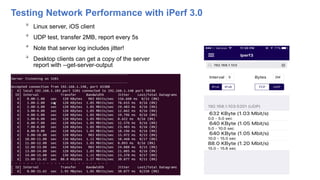
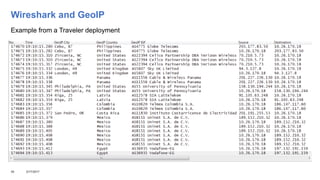
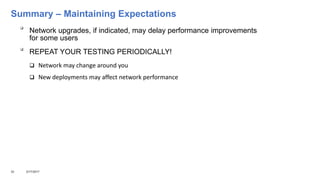
This document addresses the complexities enterprises face with cloud and mobile transitions, focusing on data flow, security, and performance issues across networks. Key challenges include managing VPN user traffic, latency at remote sites, and the impact of security policies on cloud engagement. Best practices are suggested for optimizing network performance, including understanding content delivery networks and implementing Quality of Service (QoS) strategies.