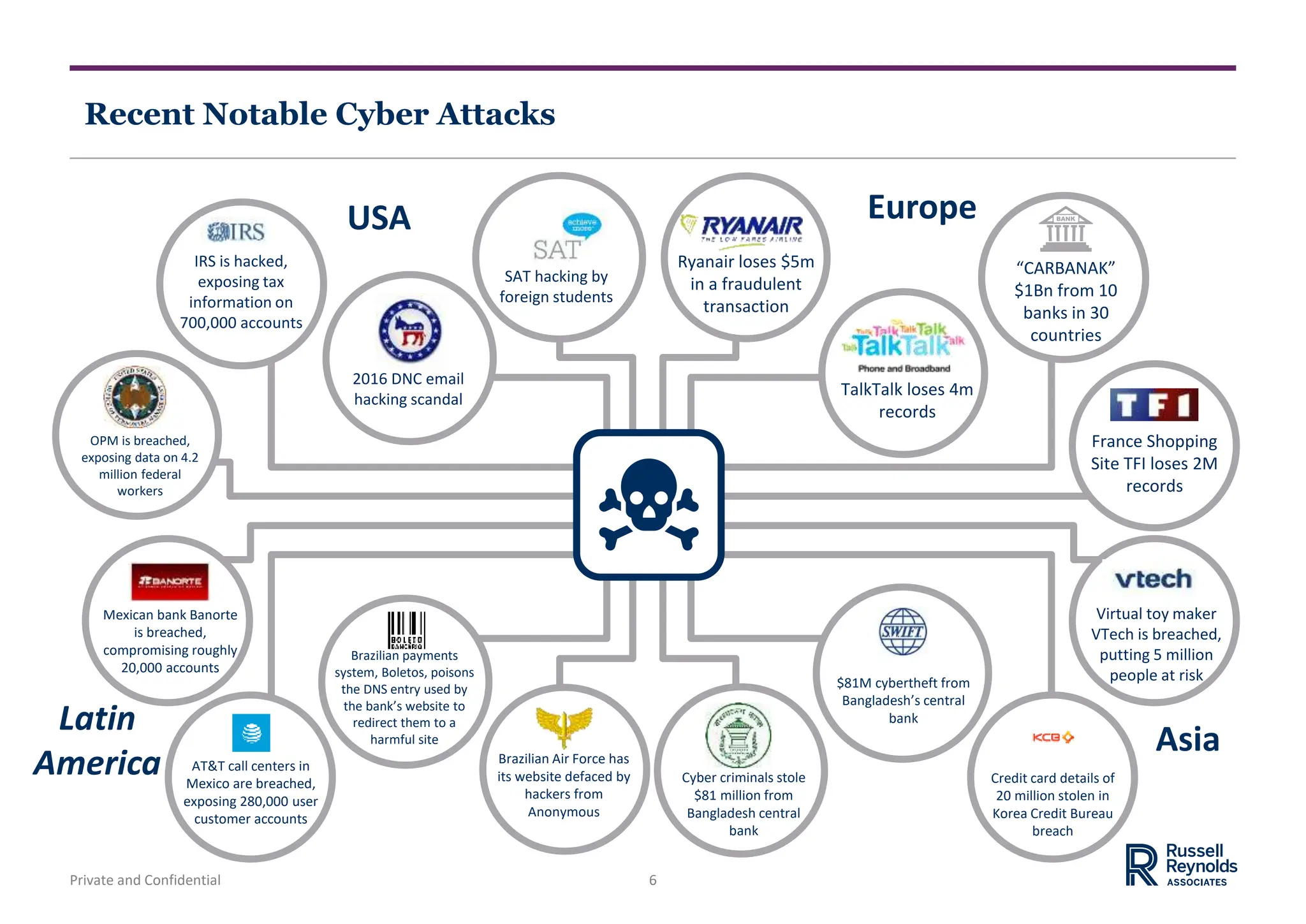
The document discusses trends in the cyber security market and the chief information security officer (CISO) role. It notes the growing threat of cyber attacks and increasing importance of the CISO position. The CISO role has evolved from a technical role to require business skills to communicate cyber risk to executives. The document also discusses cyber security organization structures, emerging CISO profiles, and competencies for different types of CISOs. Finally, it briefly mentions the talent implications of digital transformation, including new roles in data analytics and existing roles requiring digital skills.