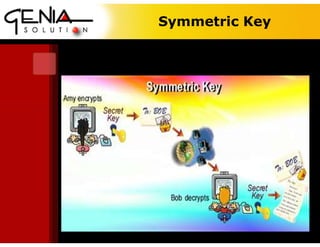
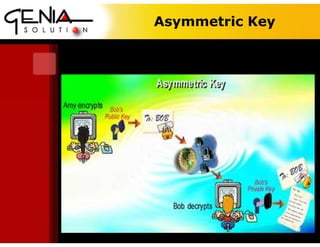
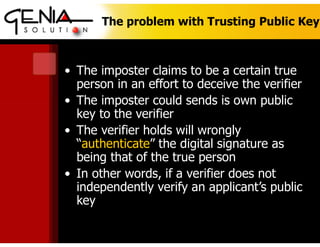
This digital certificate is for Dr. Wisanu Tuntawiroon of Genia Solution in Thailand. It discusses symmetric and asymmetric encryption keys. Symmetric encryption uses a shared key for encryption and decryption, while asymmetric encryption uses a public key for encryption and a private key for decryption. Digital certificates help verify identities and provide security, confidentiality, and integrity for online messages. They normally follow the X.509 standard and can help prevent impersonation by independently verifying public keys. Signatures on documents provide legal evidence of approval and help prevent disputes.