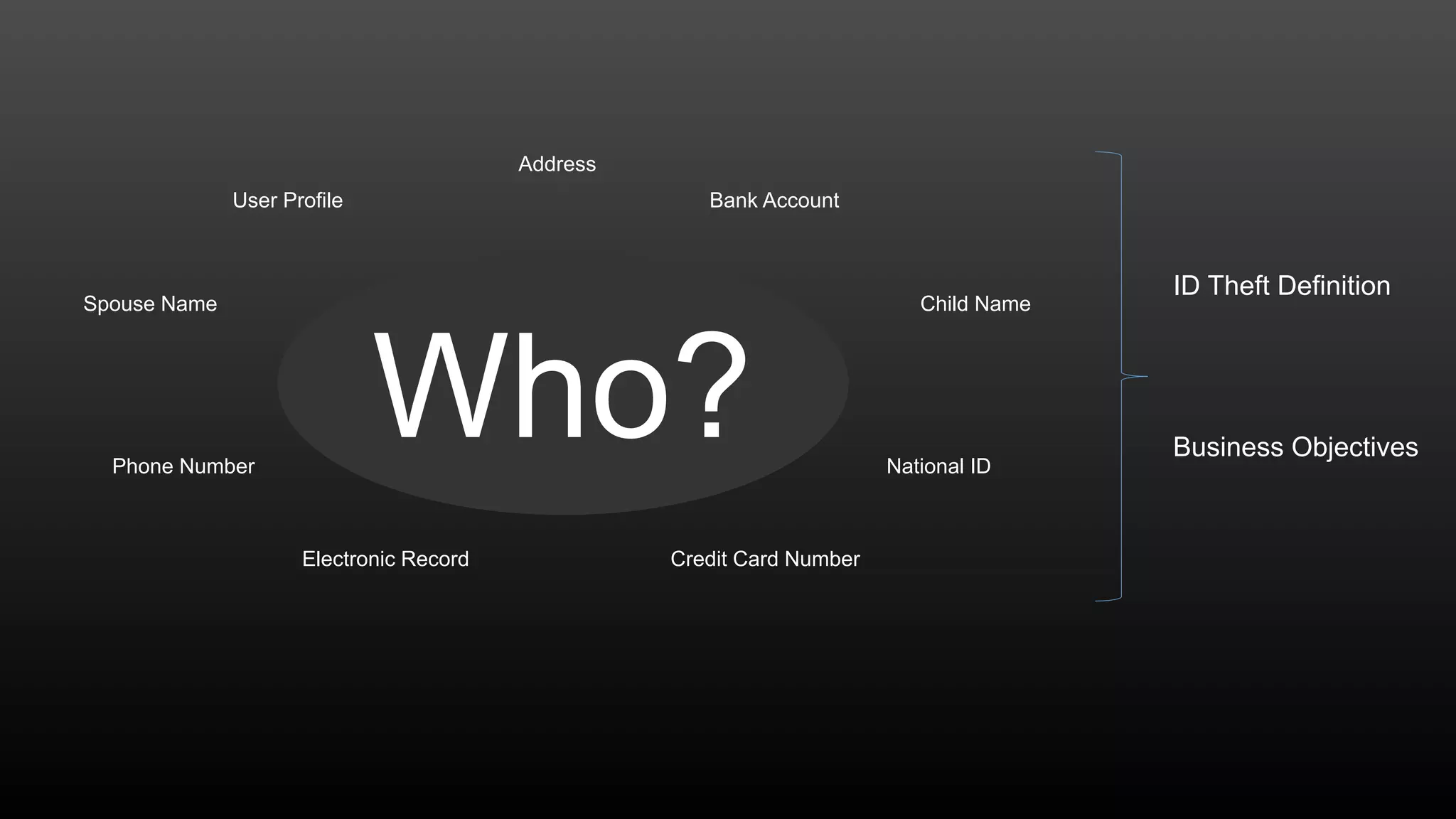
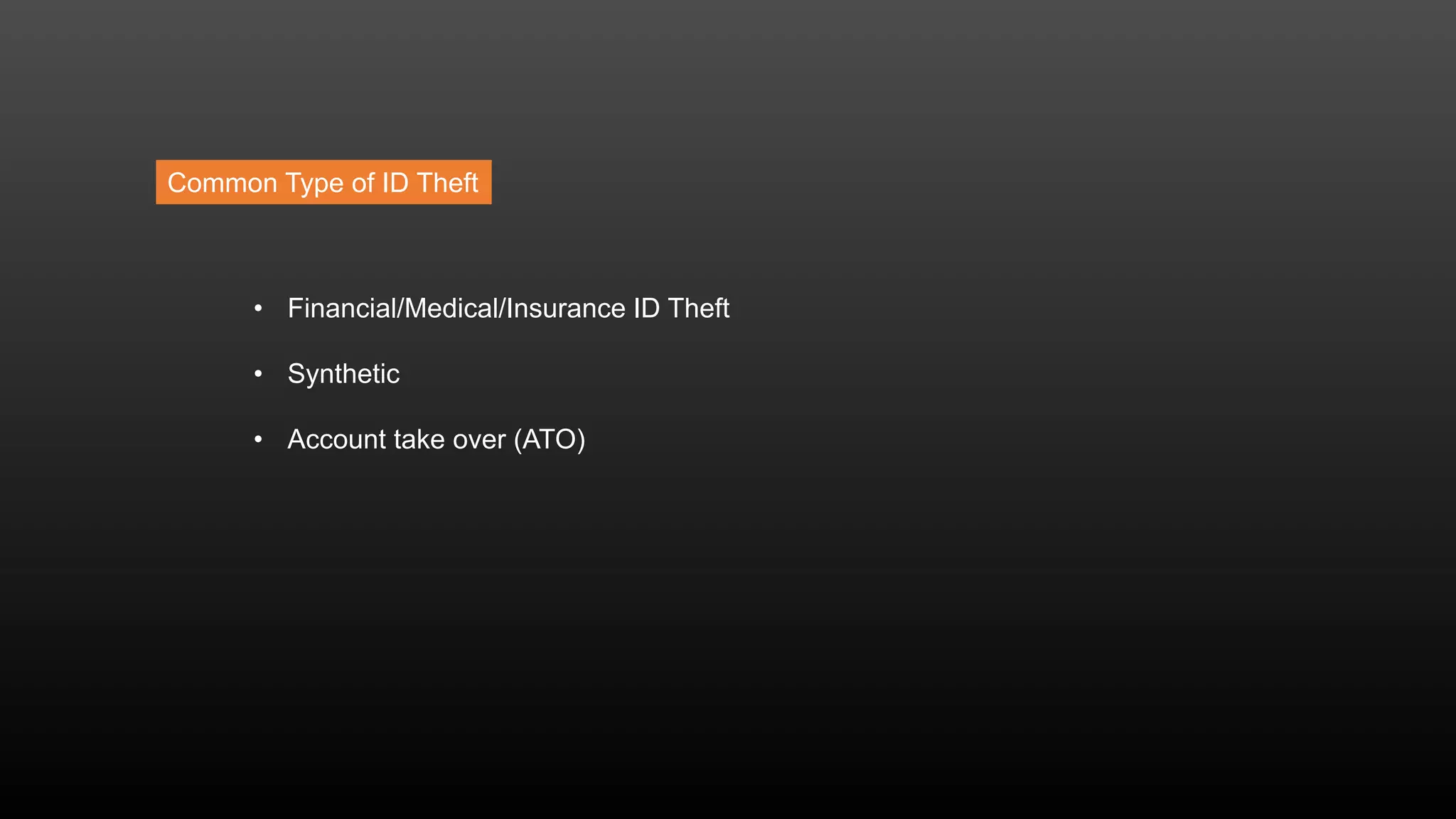
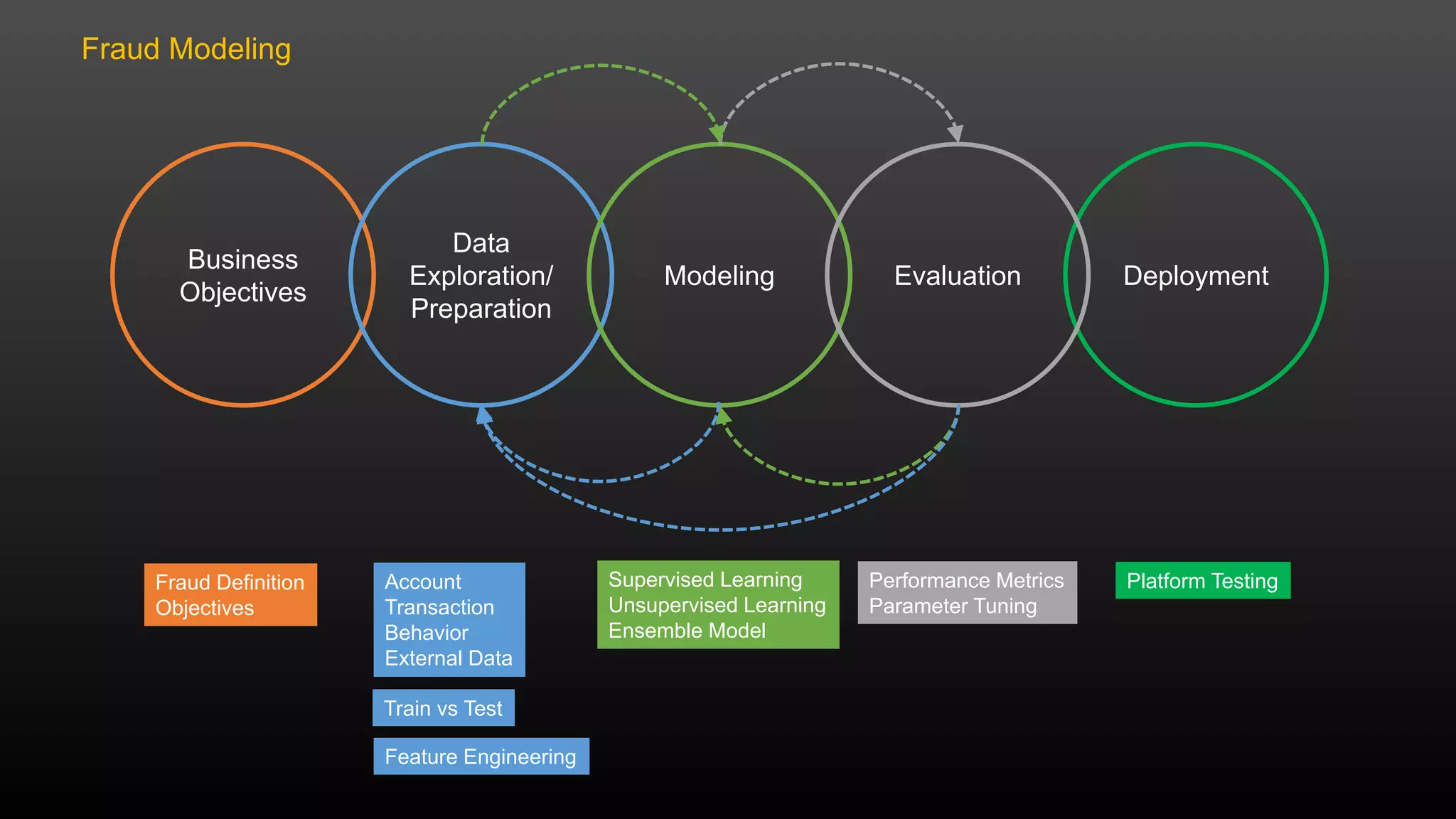
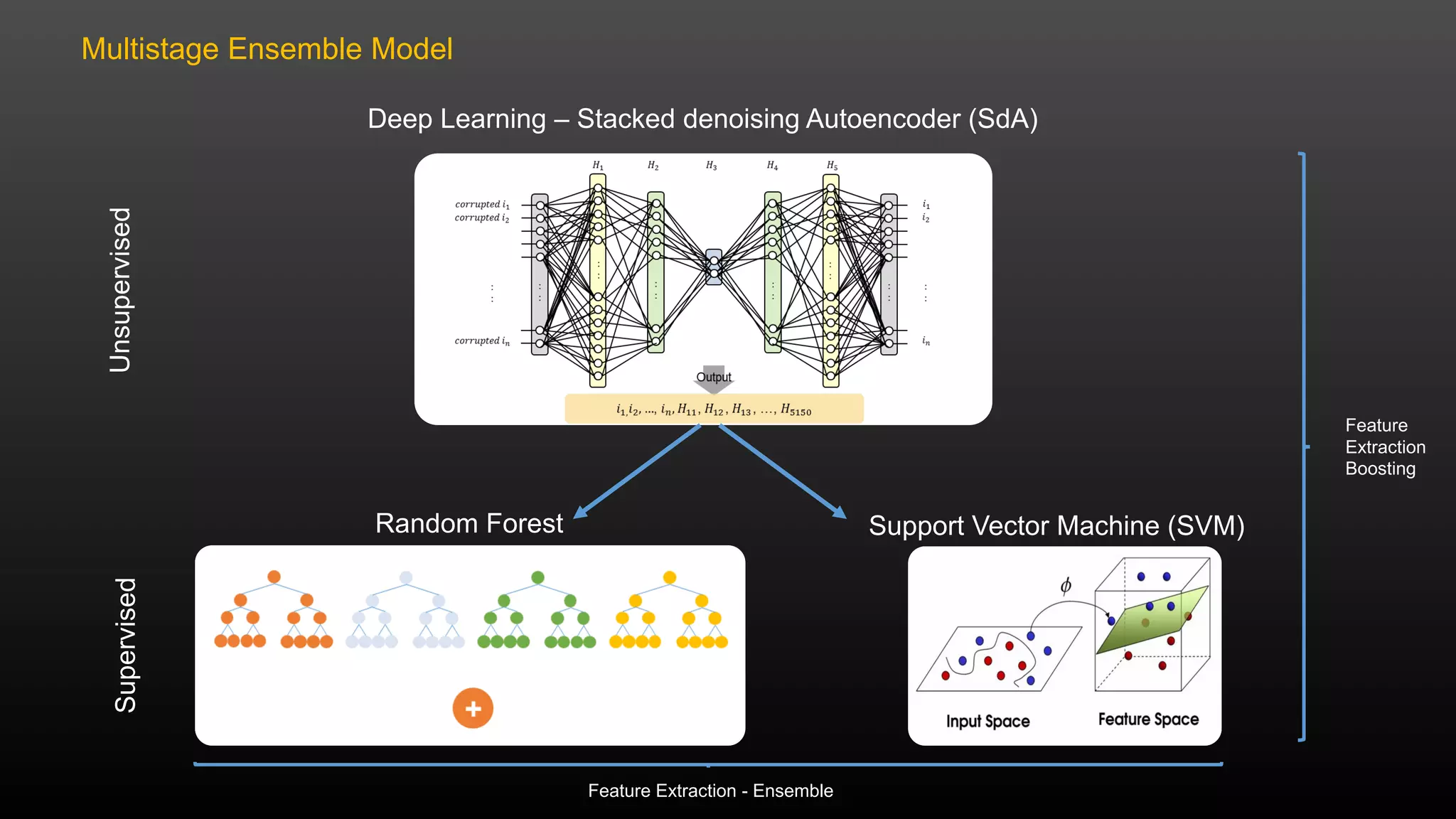
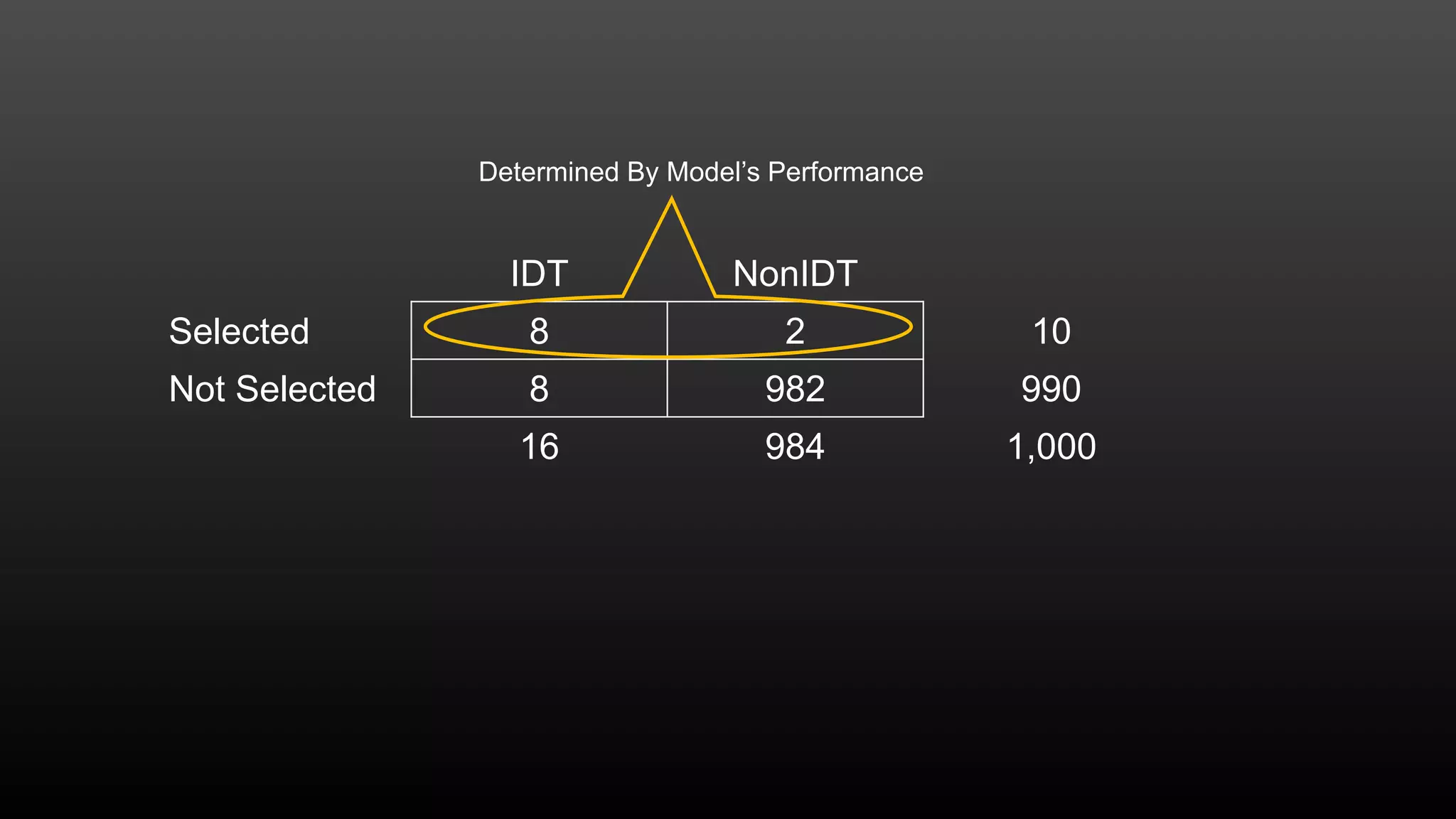
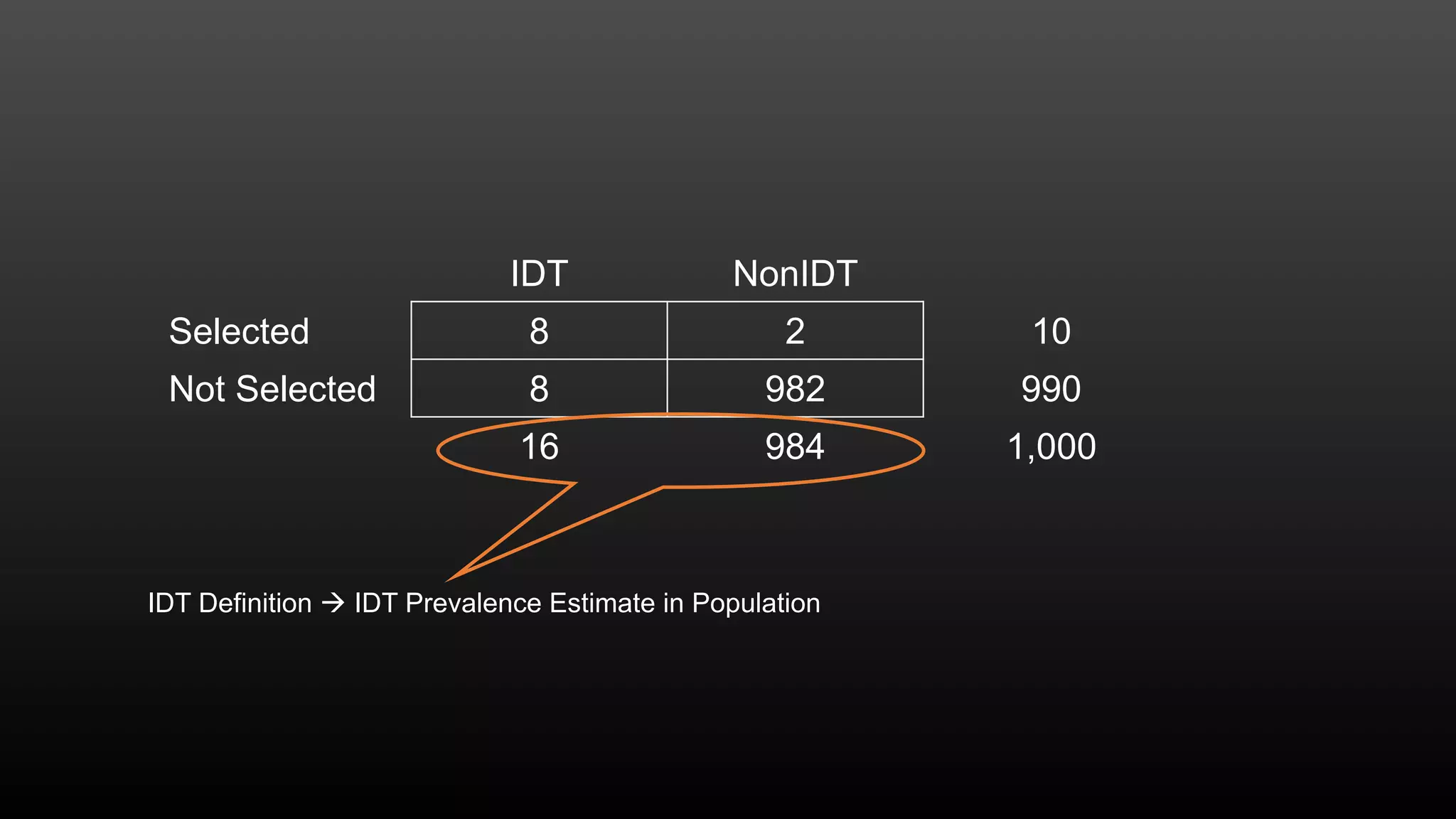
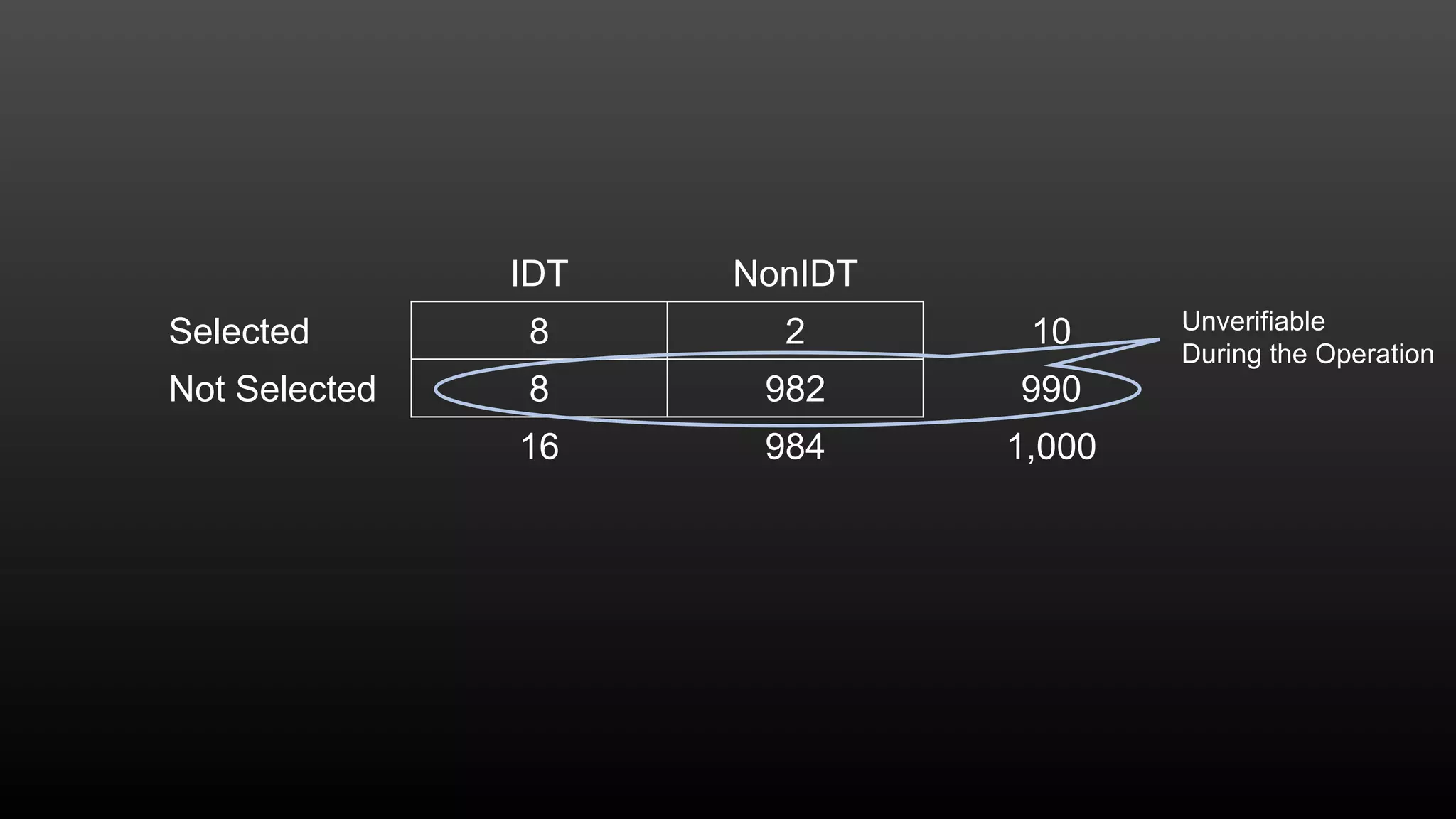
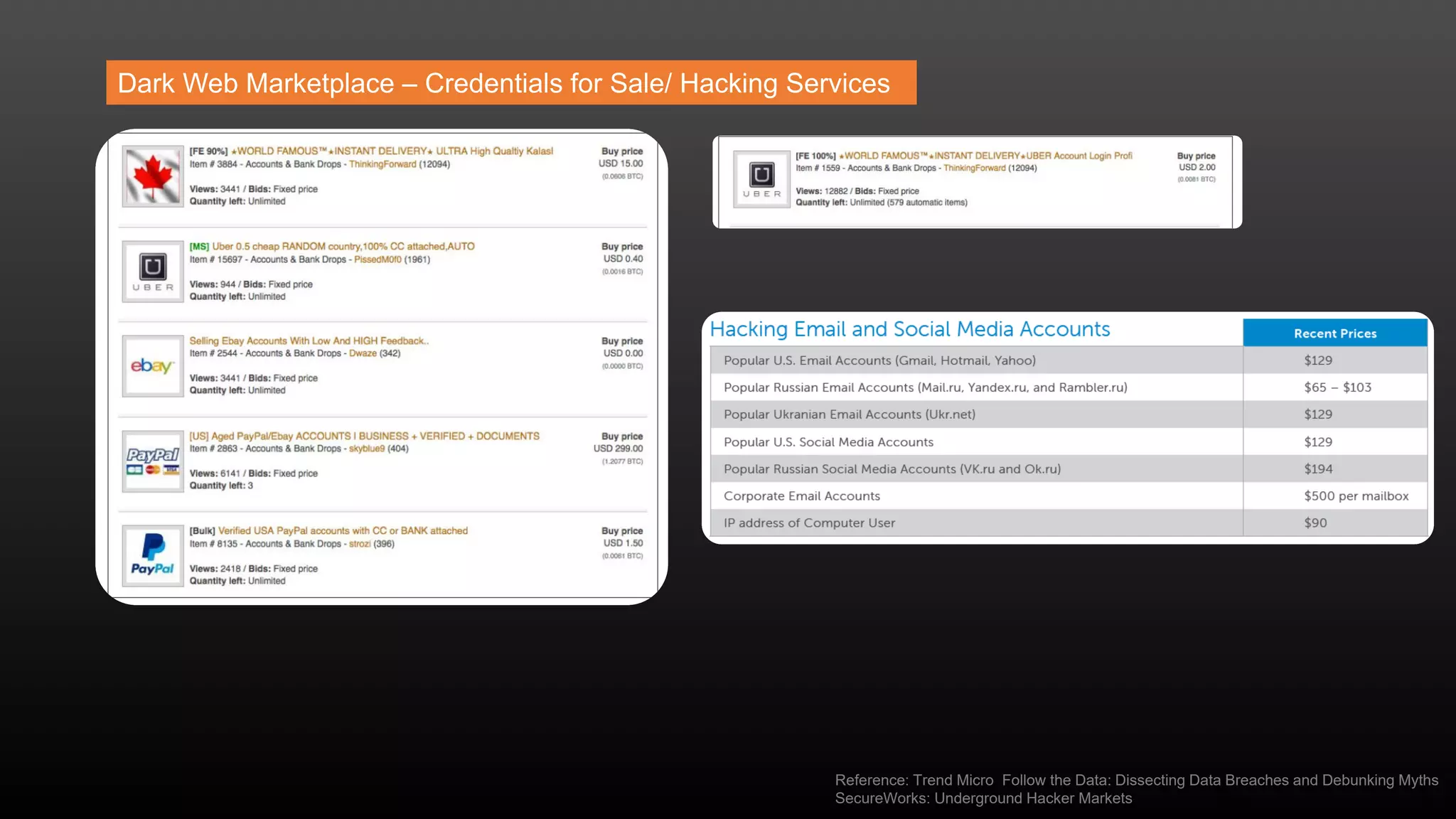
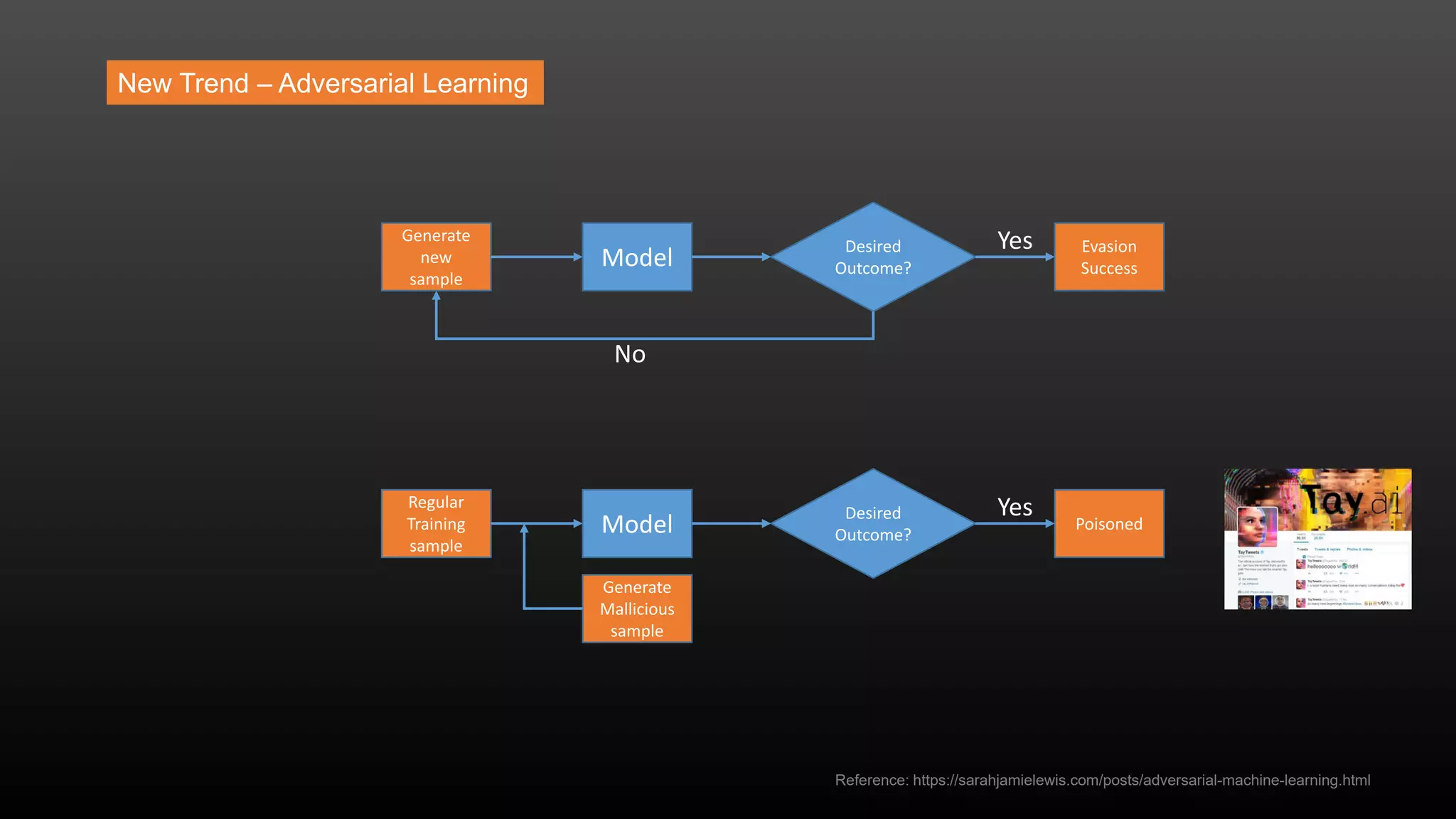
The document discusses a conference held on September 1-2, 2016, focusing on advancements in fraud detection and adversarial learning. It presents various techniques for identifying identity theft, including the use of machine learning models and data analytics. The content emphasizes the evolving nature of fraud and the importance of robust data science methods in combating these threats.