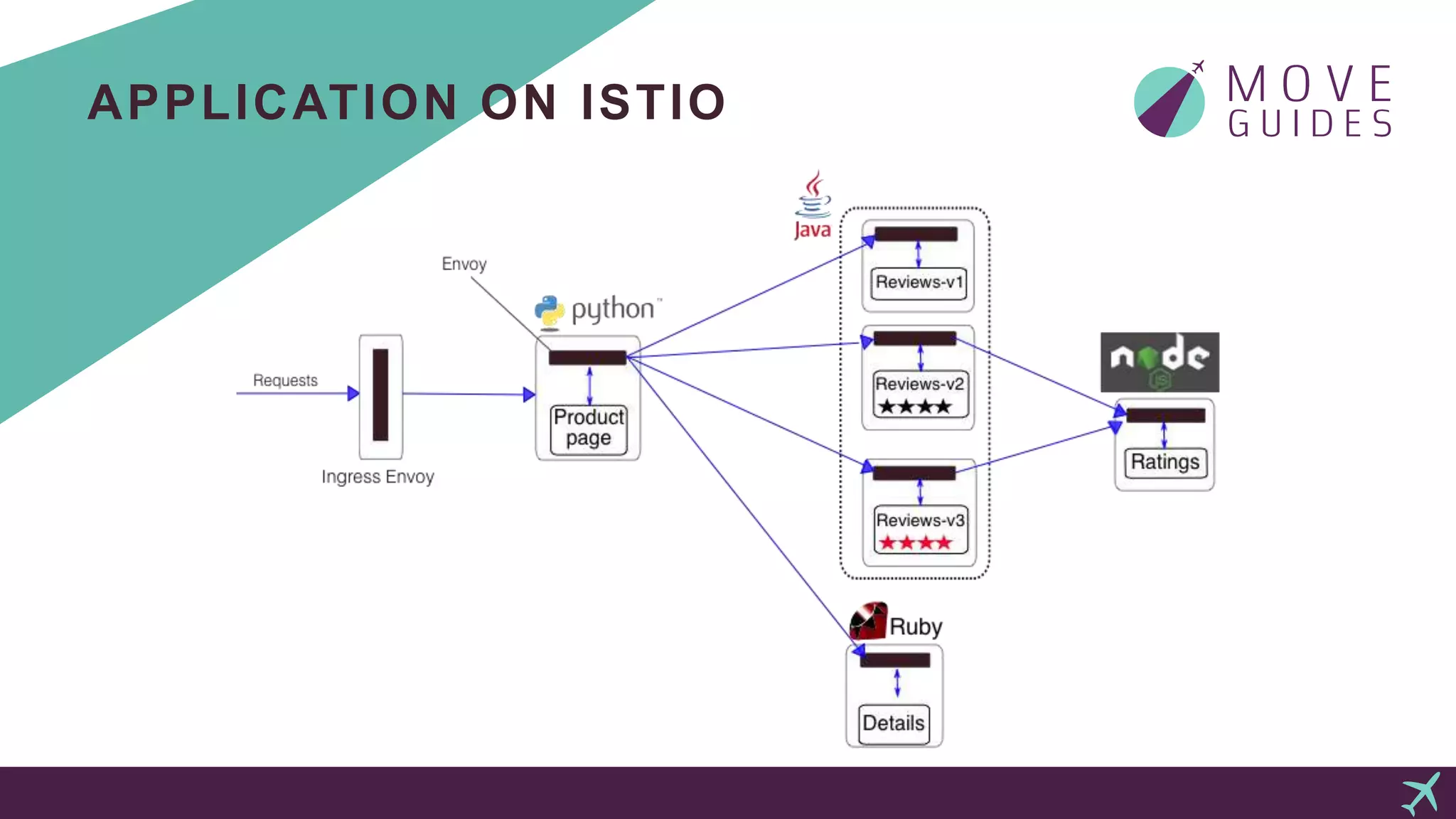
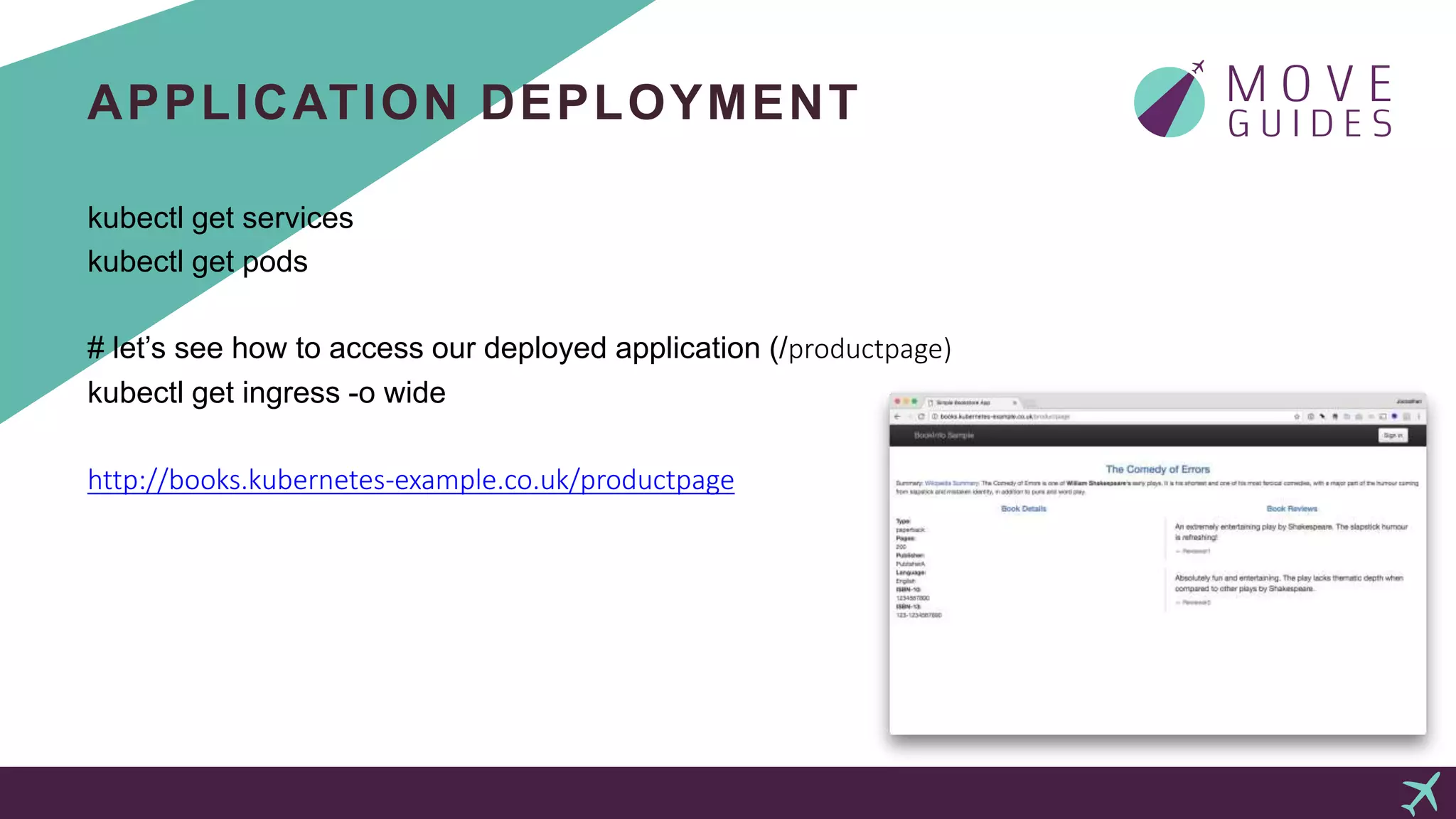
The document provides an overview of using Kubernetes and Istio for managing containerized applications, emphasizing that Kubernetes is production-ready and Istio complements it by enhancing microservice management. It details the steps for launching a Kubernetes cluster on AWS using kops, including necessary permissions and commands for configuration, installation, and validation. It also touches on deploying applications on the Istio-enabled cluster, traffic management, and monitoring tools like Grafana and Jaeger, encouraging further exploration of Kubernetes and Istio resources.











![GRAFANA
# let’s look at some metrics in grafana coming in
kubectl -n istio-system port-forward $(kubectl -n istio-system get pod -l app=grafana -o
jsonpath='{.items[0].metadata.name}') 3000:3000
http://localhost:3000/dashboard/db/istio-dashboard](https://image.slidesharecdn.com/joonathanmagi-from0to60withkubernetesandistio-171122070227/75/From-0-to-60-with-kubernetes-and-istio-21-2048.jpg)
![DOTVIZ
# how are our services connected?
kubectl -n istio-system port-forward $(kubectl -n istio-system get pod -l app=servicegraph -o
jsonpath='{.items[0].metadata.name}') 8088:8088
http://localhost:8088/dotviz](https://image.slidesharecdn.com/joonathanmagi-from0to60withkubernetesandistio-171122070227/75/From-0-to-60-with-kubernetes-and-istio-22-2048.jpg)
![JAEGER
# distributed tracing using Jaeger
kubectl port-forward -n istio-system $(kubectl get pod -n istio-system -l app=jaeger -o
jsonpath='{.items[0].metadata.name}') 16686:16686
http://localhost:16686](https://image.slidesharecdn.com/joonathanmagi-from0to60withkubernetesandistio-171122070227/75/From-0-to-60-with-kubernetes-and-istio-23-2048.jpg)