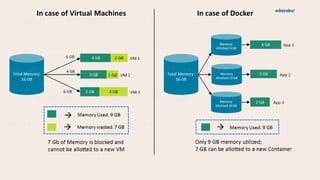
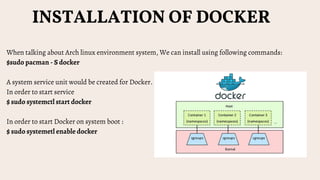
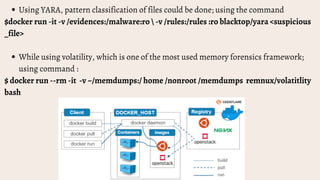
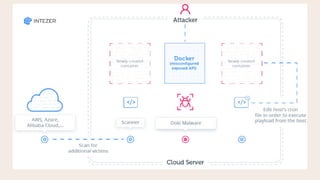
This document provides an overview of using Docker for forensic analysis and malware analysis. It defines Docker as a tool to create and run applications using containers. This allows applications to run consistently on any Linux machine. Instructions are provided on installing Docker on Arch Linux. Several common forensic analysis and malware analysis tools that can be run within Docker containers are listed, such as PEscanner, JSdetox, YARA, and Volatility, along with example commands. The key advantages of using Docker for forensic analysis are also summarized, including portability, isolation, traceability, and being lightweight.

![WHAT IS DOCKER?
Docker is a tool designed to make it esaier to create, deploy and run
applications by using containers.
With the help of containers, the developer can be assured about the application
being run on any other Linux machine regardless of the customised
setting[differing from the mavhine used for writing and testing of code]
A virtual machine but with a slight difference.
Gives a significant performance boost and reduces the size of application.
Open source.](https://image.slidesharecdn.com/dockerandmalwarepresentation-201128142836/85/Forensic-basics-of-Docker-and-Malware-2-320.jpg)