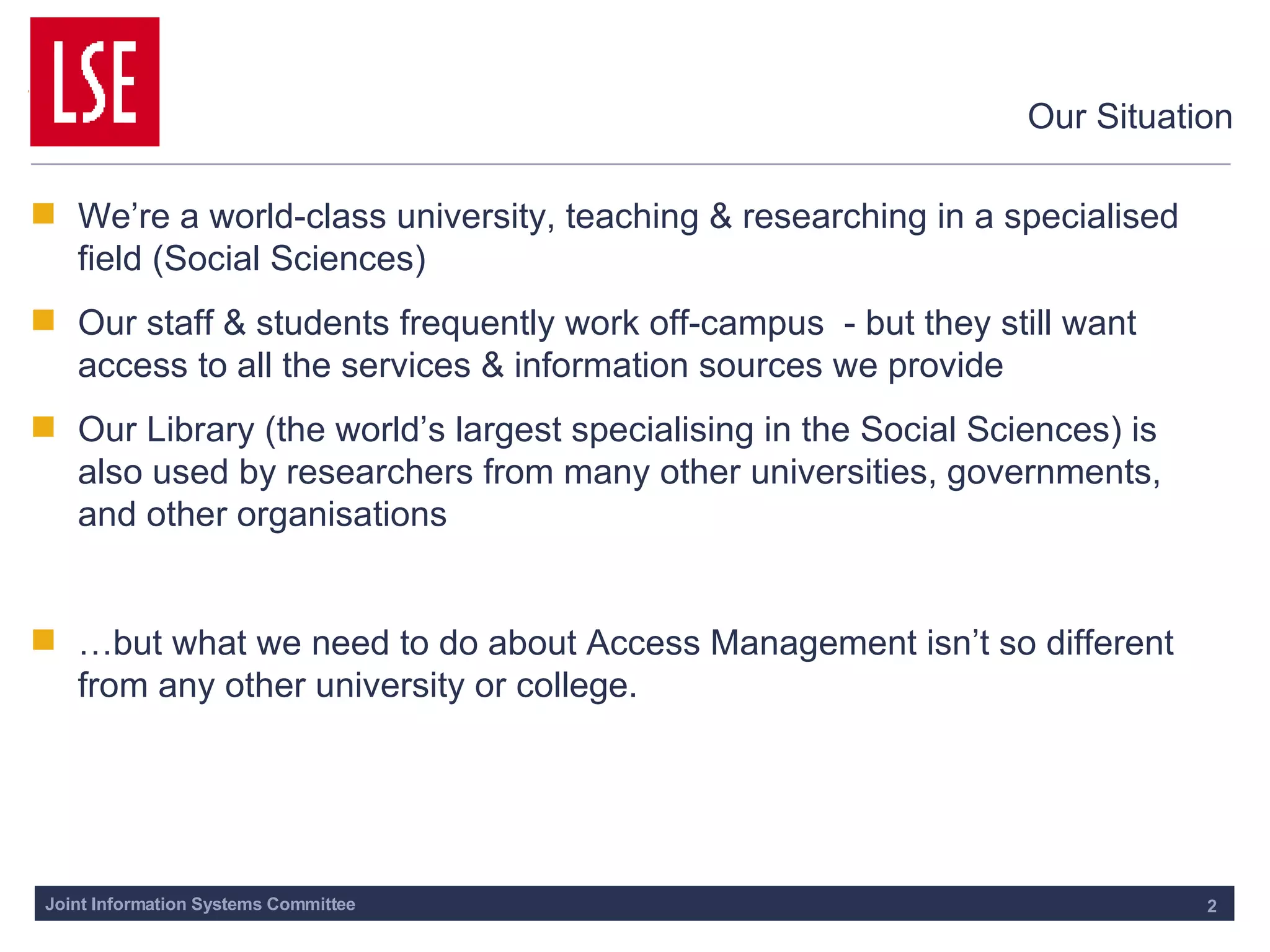
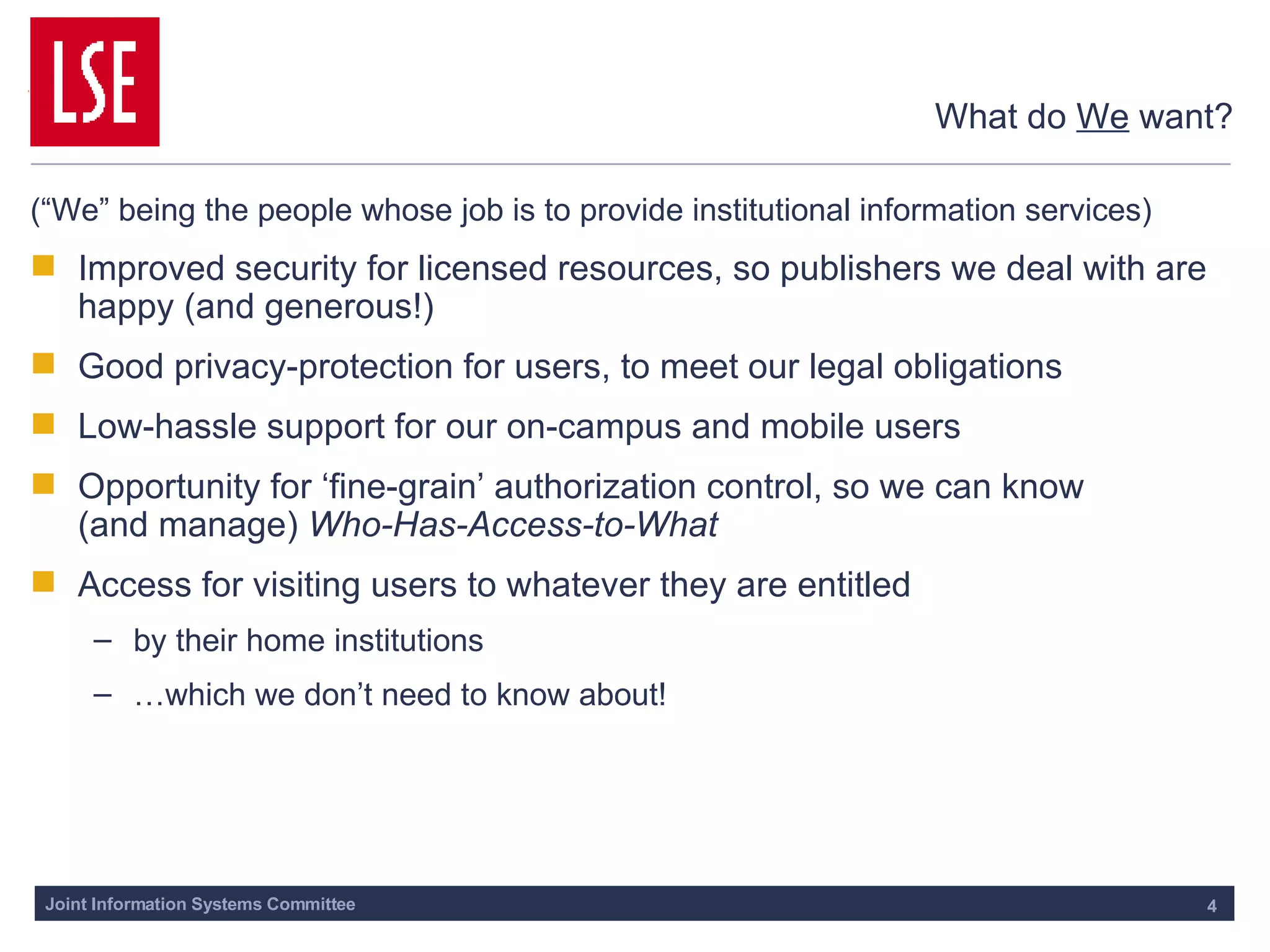
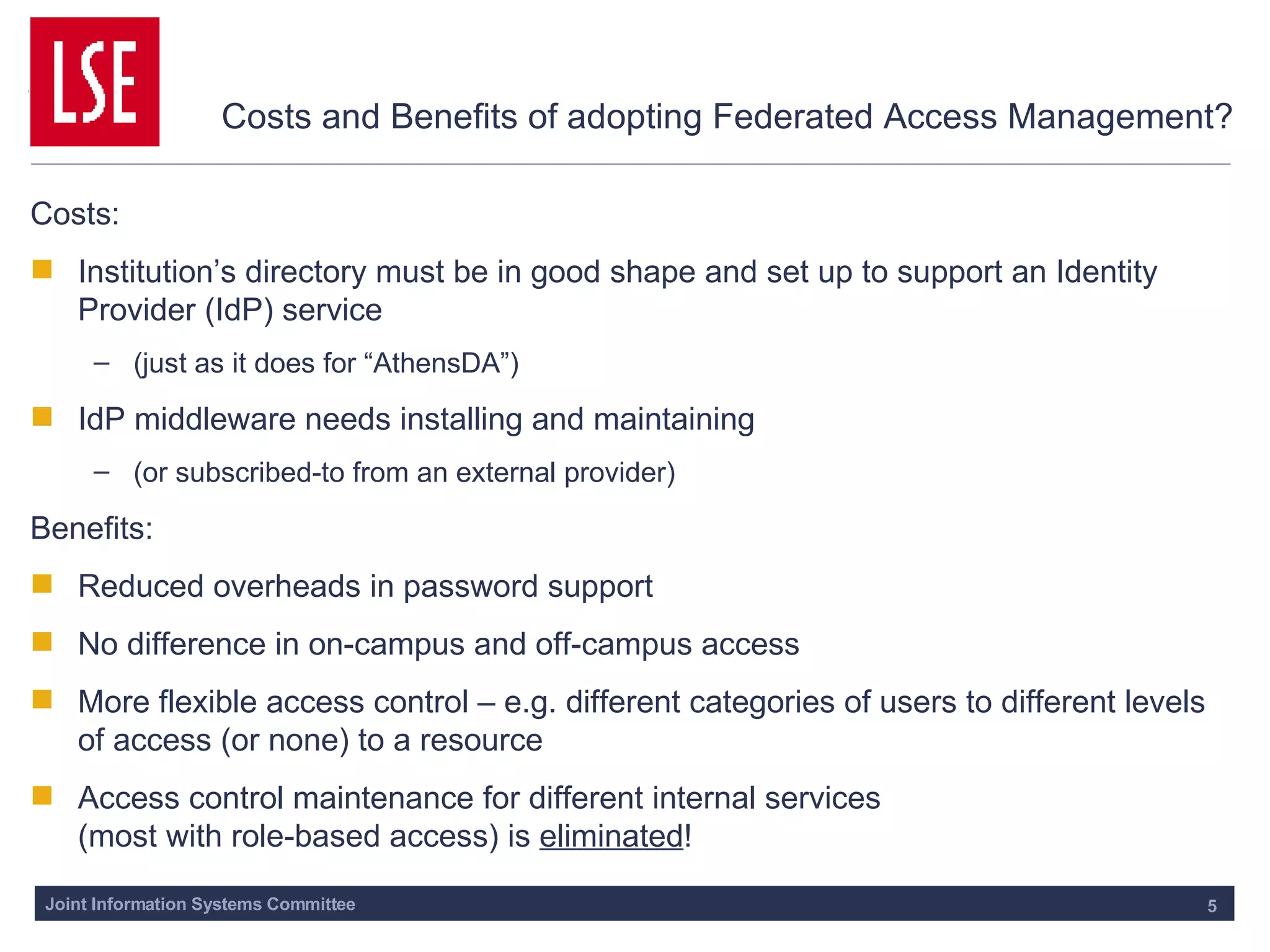
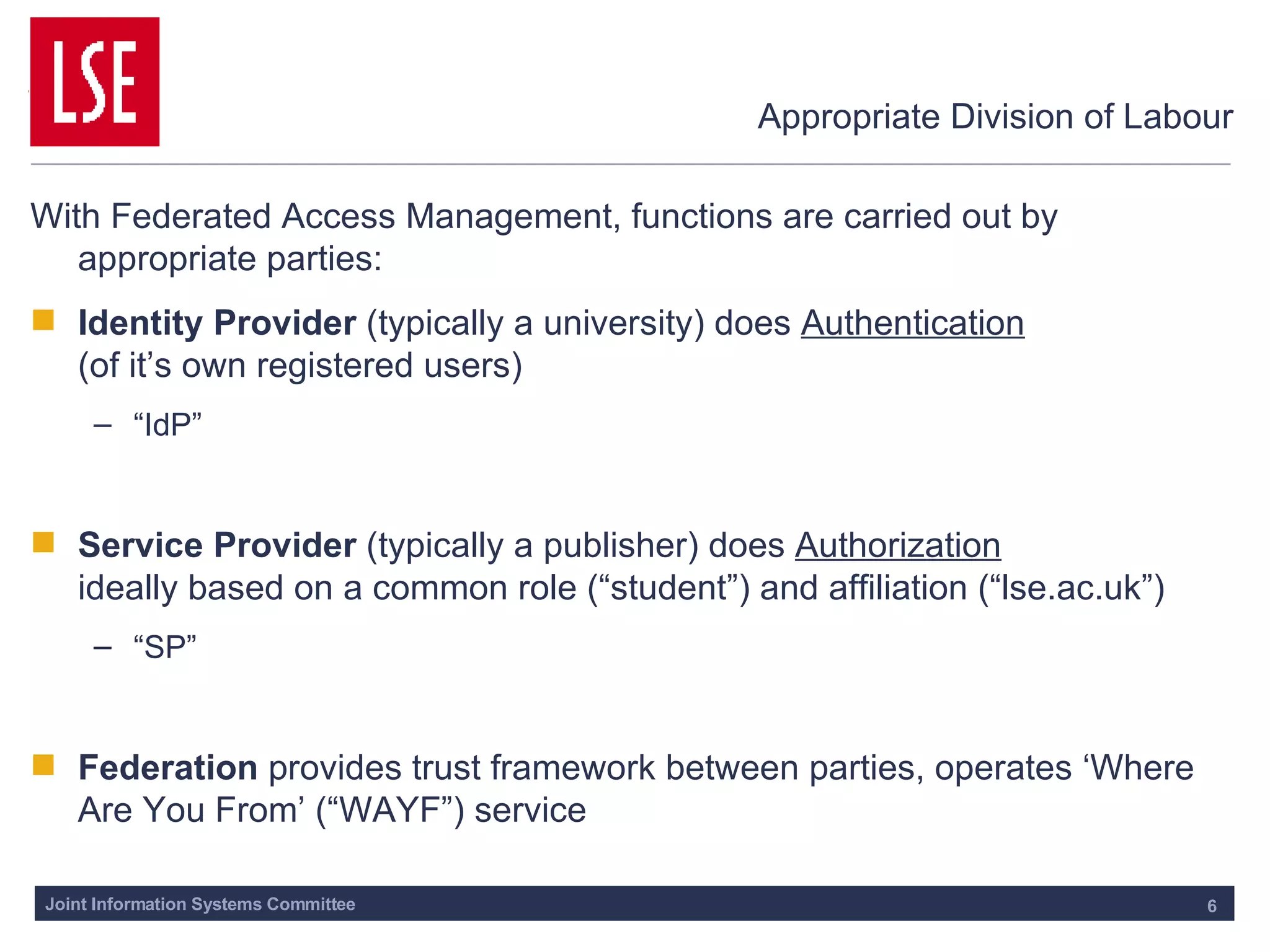
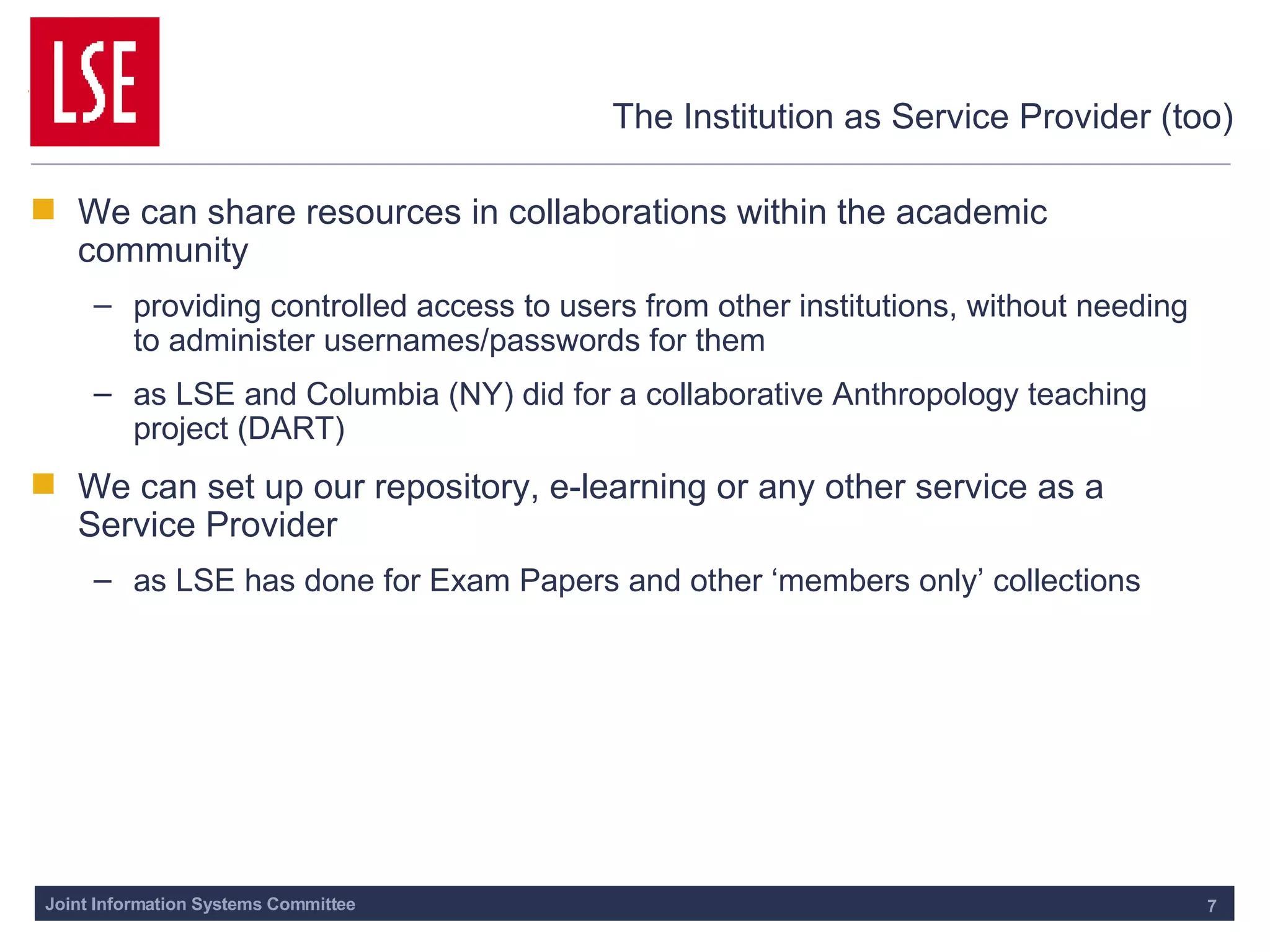
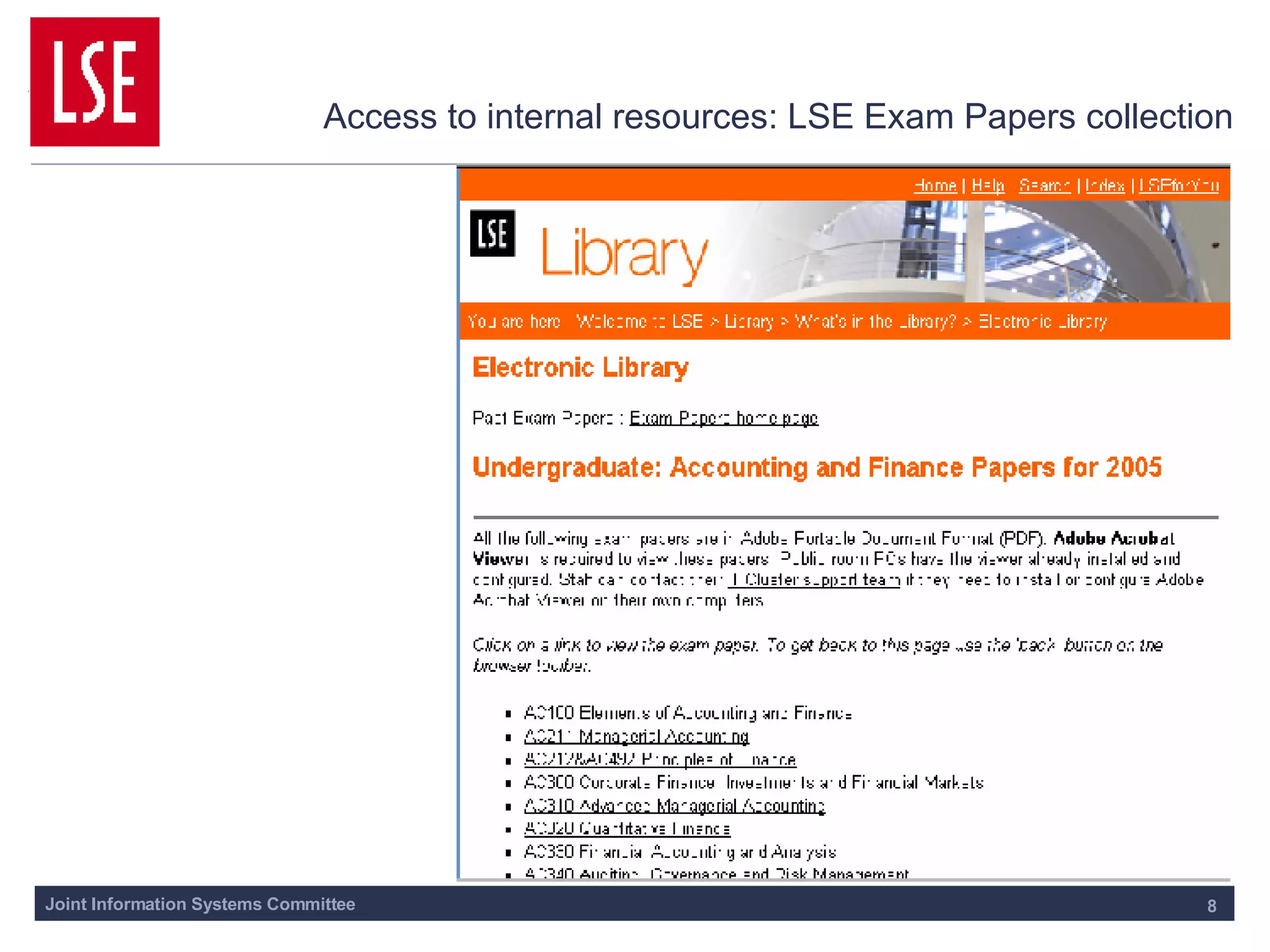
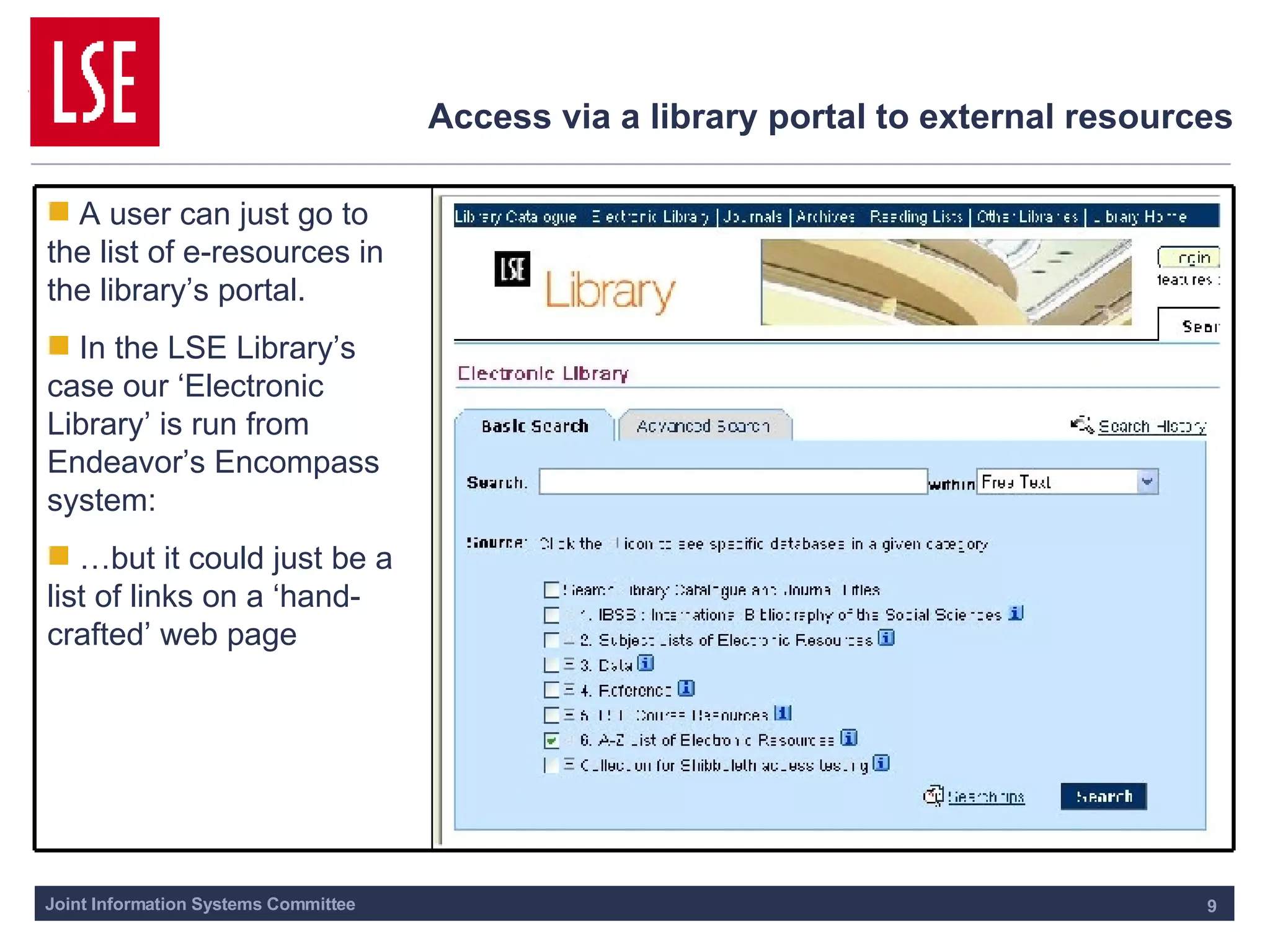
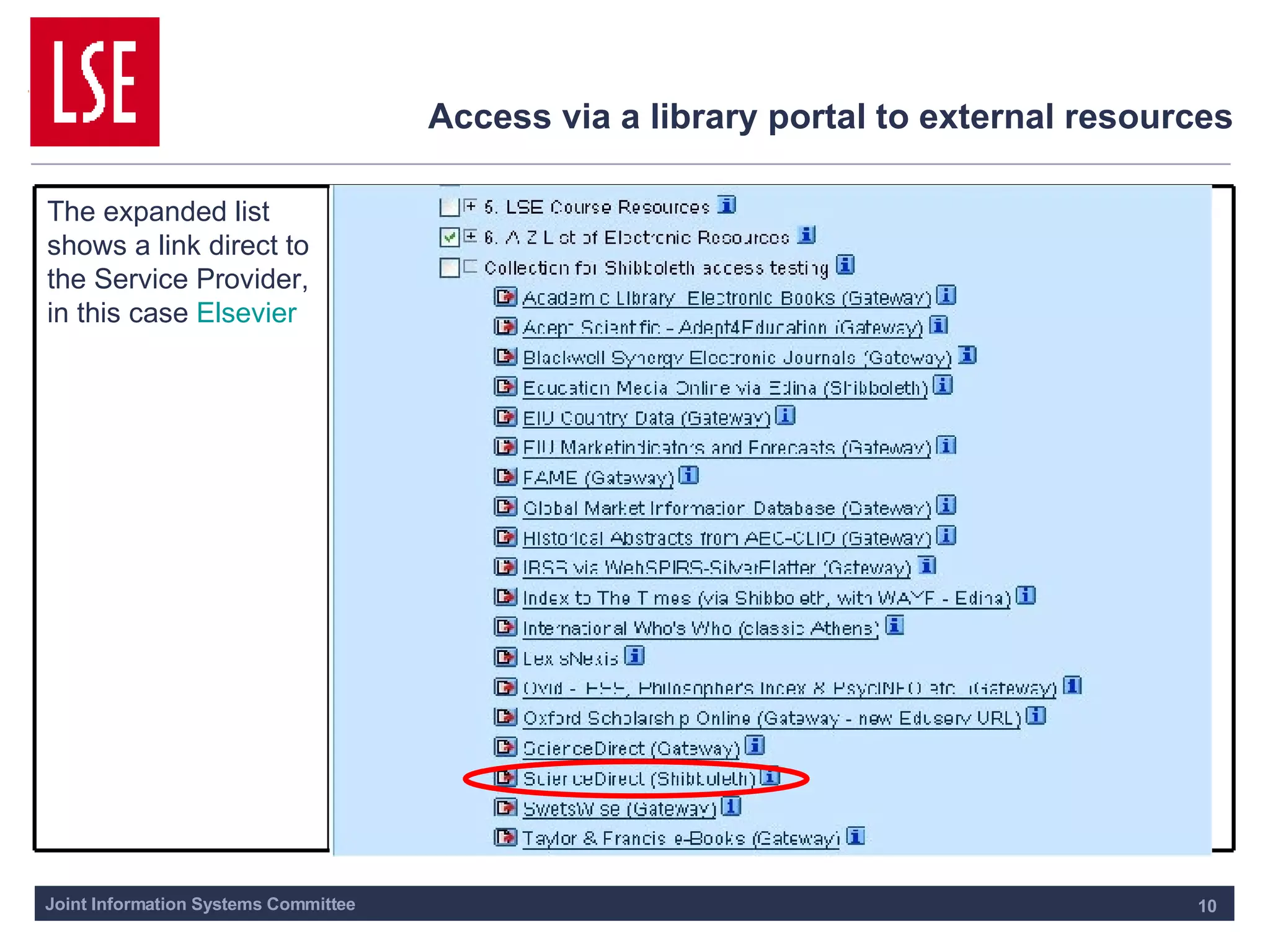
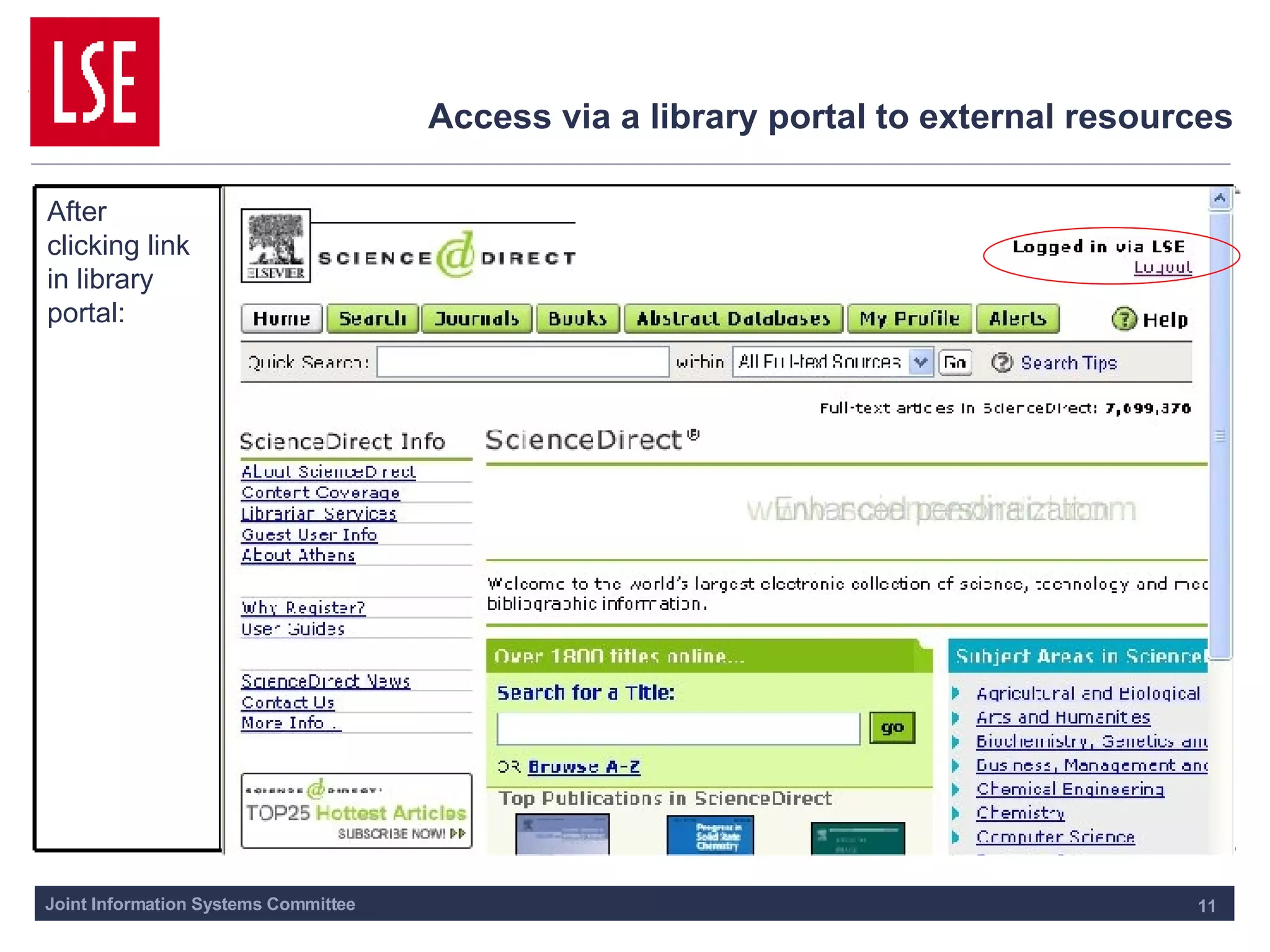
This document outlines the requirements for access management in universities and colleges in the UK, emphasizing the need for improved user access through single sign-on and better privacy controls. The transition to federated access management, supported by the UK Access Management Federation, aims to enhance security while simplifying login processes for users off-campus. Jisc's strategy involves moving away from the Athens service, with a focus on using SAML-compliant technologies to facilitate collaboration and resource sharing across institutions.
![What Universities & Colleges Need from Access Management … and How the UK Access Management Federation will provide it John Paschoud InfoSystems Engineer, LSE Library London School of Economics & Political Science, UK [email_address] Copyright John Paschoud 2007. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author. The intellectual property of others in all contributed and referenced material is acknowledged.](https://image.slidesharecdn.com/federated-access-management-1199791983488400-2/75/Federated-Access-Management-SFEU-1-2048.jpg)

![What Universities & Colleges Need from Access Management …and How the UK Access Management Federation will provide it John Paschoud JISC Access Management Outreach Team [email_address] (with grateful acknowledgement to Nicole Harris & Masha Garibyan for some of the following material) Copyright John Paschoud 2007. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author. The intellectual property of others in all contributed and referenced material is acknowledged.](https://image.slidesharecdn.com/federated-access-management-1199791983488400-2/75/Federated-Access-Management-SFEU-13-2048.jpg)











![www.ukfederation.org.uk www.jisc.ac.uk/federation.html www.identity-project.info [email_address] [email_address]](https://image.slidesharecdn.com/federated-access-management-1199791983488400-2/75/Federated-Access-Management-SFEU-25-2048.jpg)