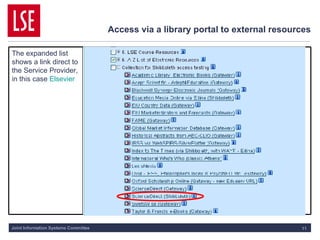
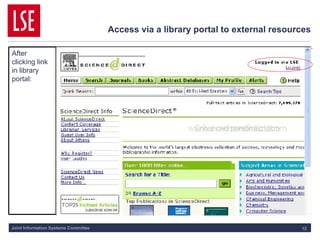
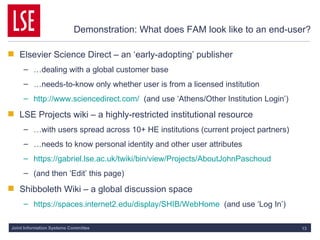
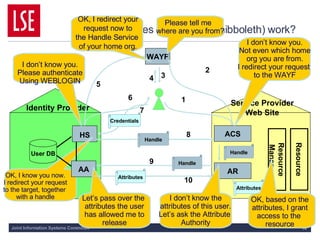
This document discusses key concepts of federated access management (FAM) including:
1) FAM allows for single sign-on access to online resources across domains through distributing authentication, authorization, and accounting functions to appropriate parties like identity providers and service providers.
2) Identity providers handle authentication of their users while service providers control authorization based on attributes like role and affiliation.
3) Standards like SAML and Shibboleth facilitate trust between identity providers and service providers so users' access is managed according to their home institution's policies.
![Federated Access Management 102 key concepts you need to become your institution’s local expert John Paschoud InfoSystems Engineer, LSE Library London School of Economics & Political Science, UK [email_address] Copyright John Paschoud 2007. This work is the intellectual property of the author. Permission is granted for this material to be shared for non-commercial, educational purposes, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author. The intellectual property of others in all contributed and referenced material is acknowledged.](https://image.slidesharecdn.com/federated-access-management-102-1199791988444381-4/85/Federated-Access-Management-102-1-320.jpg)









![www.ukfederation.org.uk www.jisc.ac.uk/federation.html http:// www.angel.ac.uk/ShibbolethAtLSE www.identity-project.info [email_address] [email_address]](https://image.slidesharecdn.com/federated-access-management-102-1199791988444381-4/85/Federated-Access-Management-102-19-320.jpg)