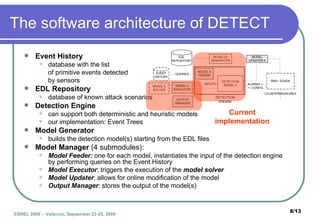
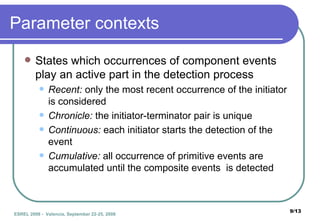
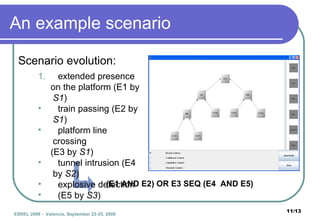
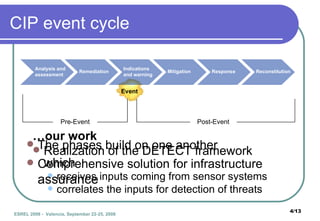
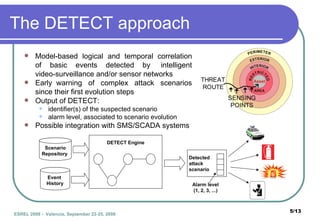
The document presents DETECT, a framework for detecting attacks on critical infrastructures. It uses an Event Description Language to model attack scenarios as combinations of primitive and composite events. The DETECT architecture receives input from sensors, correlates events using event tree models of scenarios, and outputs detected scenario identifiers and alarm levels. An example scenario of a terrorist attack in a subway station is shown. Future work includes improving detection models and integrating DETECT with other frameworks.
![F. Flammini, A. Gaglione, N. Mazzocca, C. Pragliola DETECT: a novel framework for the detection of attacks to critical infrastructures presented by Andrea Gaglione Dipartimento di Informatica e Sistemistica Università di Napoli “Federico II” Via Claudio 21, 80125 Napoli Email: [email_address] Web: http://wpage.unina.it/andrea.gaglione European Safety & Reliability Conference, ESREL’08 22-25 September 2008 , Valencia, Spain](https://image.slidesharecdn.com/esrel08final-1233737368513839-3/75/Esrel08-Final-1-2048.jpg)
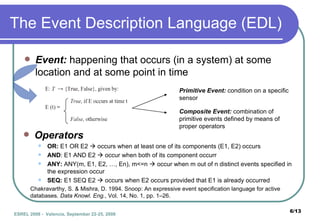
![Event Trees Composite events are represented by event trees Example: E7 = (E1 OR E2) AND (E2 SEQ (E4 AND E6)) Temporal Constraints define a validity interval for a composite event can be added to any operator Example: ( E1 AND E2 ) = True Leaf: primitive event internal node: EDL operator formal expression t1< t | ( E1(t) E2(t1) E1(t1) E2(t) ) [T] |t – t1| ≤ T](https://image.slidesharecdn.com/esrel08final-1233737368513839-3/85/Esrel08-Final-7-320.jpg)