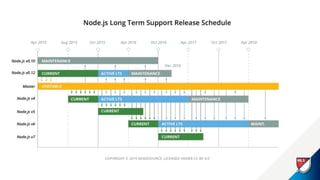
This document discusses securing an enterprise Node.js environment. It recommends using Node LTS versions for stability, containerizing applications for isolation, and securing dependencies by whitelisting modules. It also covers authenticating users with JWT, authorizing access with scopes and roles, validating input data, encrypting sensitive data, and ensuring HTTPS is used everywhere. Securing the runtime is important to protect the company from threats, improve confidence, and meet regulations.