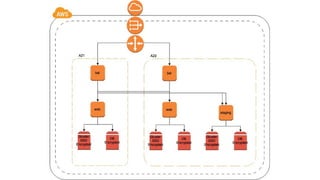
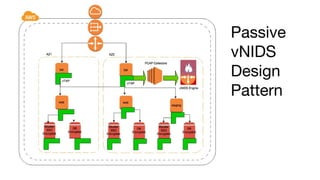
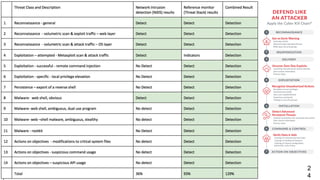
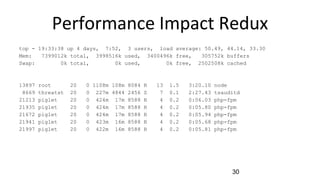
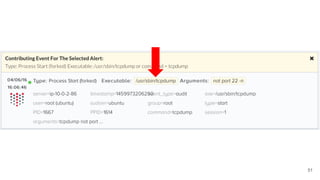
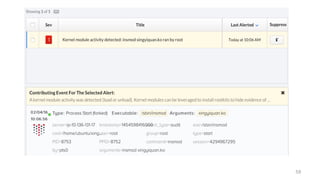
The document outlines the extensive security experience of an individual, highlighting their roles in cloud security and contributions to several successful startups and security products. It details their technical expertise, including a focus on incident response and monitoring, as well as behavioral detection methods. Additionally, it compares traditional forensic investigation approaches with a new 'spacefolding' technology for faster incident analysis.