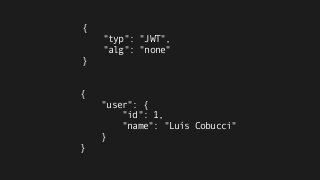
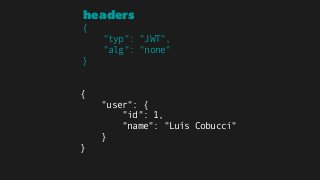
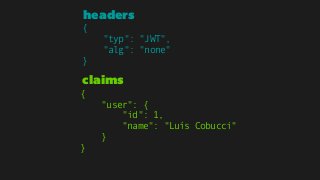
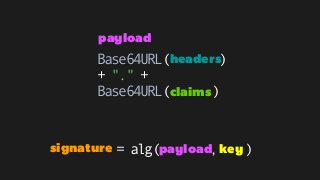
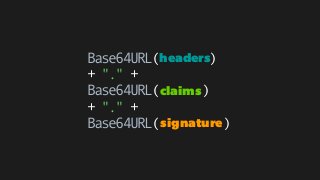
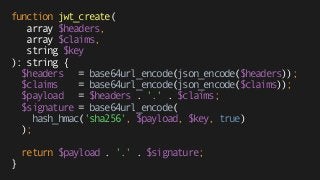
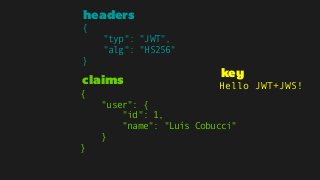
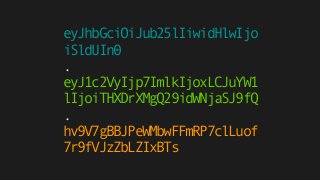
The document explains the authentication process using JSON Web Tokens (JWT), detailing how tokens are created, validated, and utilized for maintaining session integrity in APIs. It highlights the advantages of using JWT for client-side session management while addressing potential drawbacks of traditional session storage. Key functions for encoding and decoding tokens are also provided to illustrate the technical implementation.











![{
"token": "abc123", "uid": 1, "expiration": "…",
"scope": ["a", "b", "c"]
}](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-12-320.jpg)
![{
"token": "abc123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-13-320.jpg)
![{
"token": "abc123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-14-320.jpg)
![{
"token": "abc123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "def789", "uid": 6,
"expiration": "…", "scope": ["a"]
}
{
"token": "ghi123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "jkl789", "uid": 6,
"expiration": "…", "scope": ["a"]
}](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-15-320.jpg)
![{
"token": "abc123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "def789", "uid": 6,
"expiration": "…", "scope": ["a"]
}
{
"token": "ghi123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "jkl789", "uid": 6,
"expiration": "…", "scope": ["a"]
}
{
"token": "abc123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "def789", "uid": 6,
"expiration": "…", "scope": ["a"]
}
{
"token": "ghi123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "jkl789", "uid": 6,
"expiration": "…", "scope": ["a"]
}
{
"token": "abc123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "def789", "uid": 6,
"expiration": "…", "scope": ["a"]
}
{
"token": "ghi123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "jkl789", "uid": 6,
"expiration": "…", "scope": ["a"]
}
{
"token": "abc123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "def456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "abc789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "def789", "uid": 6,
"expiration": "…", "scope": ["a"]
}
{
"token": "ghi123", "uid": 1,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl123", "uid": 2,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi456", "uid": 3,
"expiration": "…", "scope": ["a", "b", "c"]
}
{
"token": "jkl456", "uid": 4,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "ghi789", "uid": 5,
"expiration": "…", "scope": ["a", "b"]
}
{
"token": "jkl789", "uid": 6,
"expiration": "…", "scope": ["a"]
}](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-16-320.jpg)
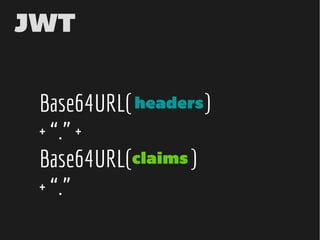


















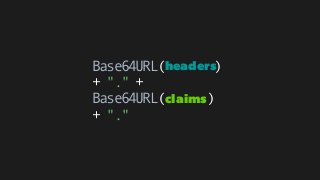



![iat (NumericDate)
exp (NumericDate)
nbf (NumericDate)
jti (String)
iss (StringOrUri)
aud (StringOrUri[])
sub (StringOrUri)](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-69-320.jpg)
![iat (NumericDate)
exp (NumericDate)
nbf (NumericDate)
jti (String)
iss (StringOrUri)
aud (StringOrUri[])
sub (StringOrUri)
case-sensitive](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-70-320.jpg)


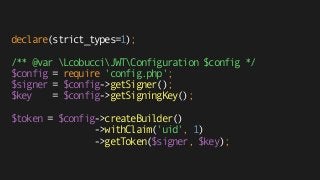
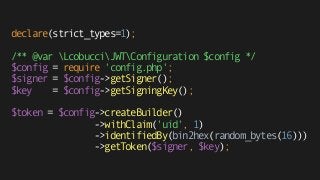
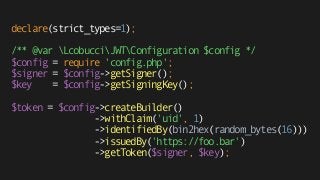
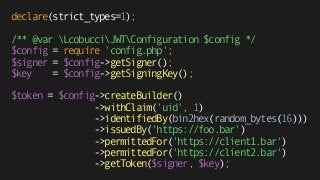
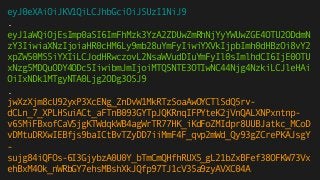
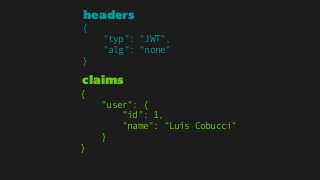
![{
"typ": "JWT",
"alg": "RS256"
}
{
"uid": 1,
"jti": "aa397c06d50fda662ae0da895687f767",
"iss": "https://foo.bar",
"aud": ["https://client1.bar", “https://client2.bar”],
"iat": "1495178904.868879",
"nbf": "1495179204.868879",
"exp": "1495182504.868879"
}](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-83-320.jpg)
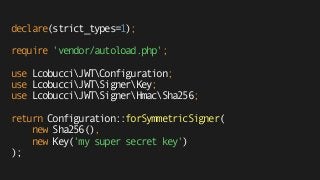
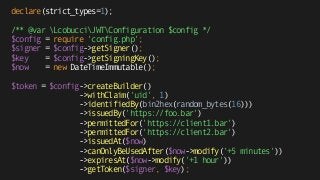
![declare(strict_types=1);
use LcobucciClockSystemClock;
use LcobucciJWTValidationConstraint;
/** @var LcobucciJWTConfiguration $config */
$config = require 'config.php';
$signer = $config->getSigner();
$key = $config->getVerificationKey();
$token = $config->getParser()->parse('eyJ0eNiJ9 (...)');
$constraints = [
new ConstraintIssuedBy('https://foo.bar', 'https://bar.foo'),
new ConstraintPermittedFor('https://client2.bar'),
new ConstraintValidAt(new SystemClock()),
new ConstraintSignedWith($signer, $key)
];
$config->getValidator()->assert($token, ...$constraints);](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-85-320.jpg)
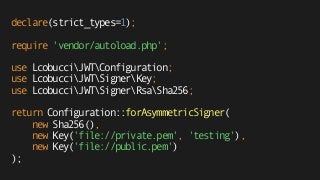
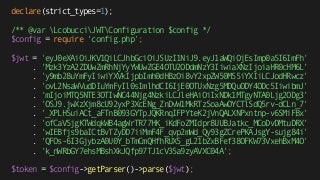
![declare(strict_types=1);
use LcobucciClockSystemClock;
use LcobucciJWTValidationConstraint;
/** @var LcobucciJWTConfiguration $config */
$config = require 'config.php';
$signer = $config->getSigner();
$key = $config->getVerificationKey();
$token = $config->getParser()->parse('eyJ0eNiJ9 (...)');
$constraints = [
new ConstraintIssuedBy('https://foo.bar', 'https://bar.foo'),
new ConstraintPermittedFor('https://client2.bar'),
new ConstraintValidAt(new SystemClock()),
new ConstraintSignedWith($signer, $key)
];
var_dump($config->getValidator()->validate($token, ...$constraints));](https://image.slidesharecdn.com/jwt-toauthandbeyond-150513153320-lva1-app6891/85/JWT-To-authentication-and-beyond-86-320.jpg)