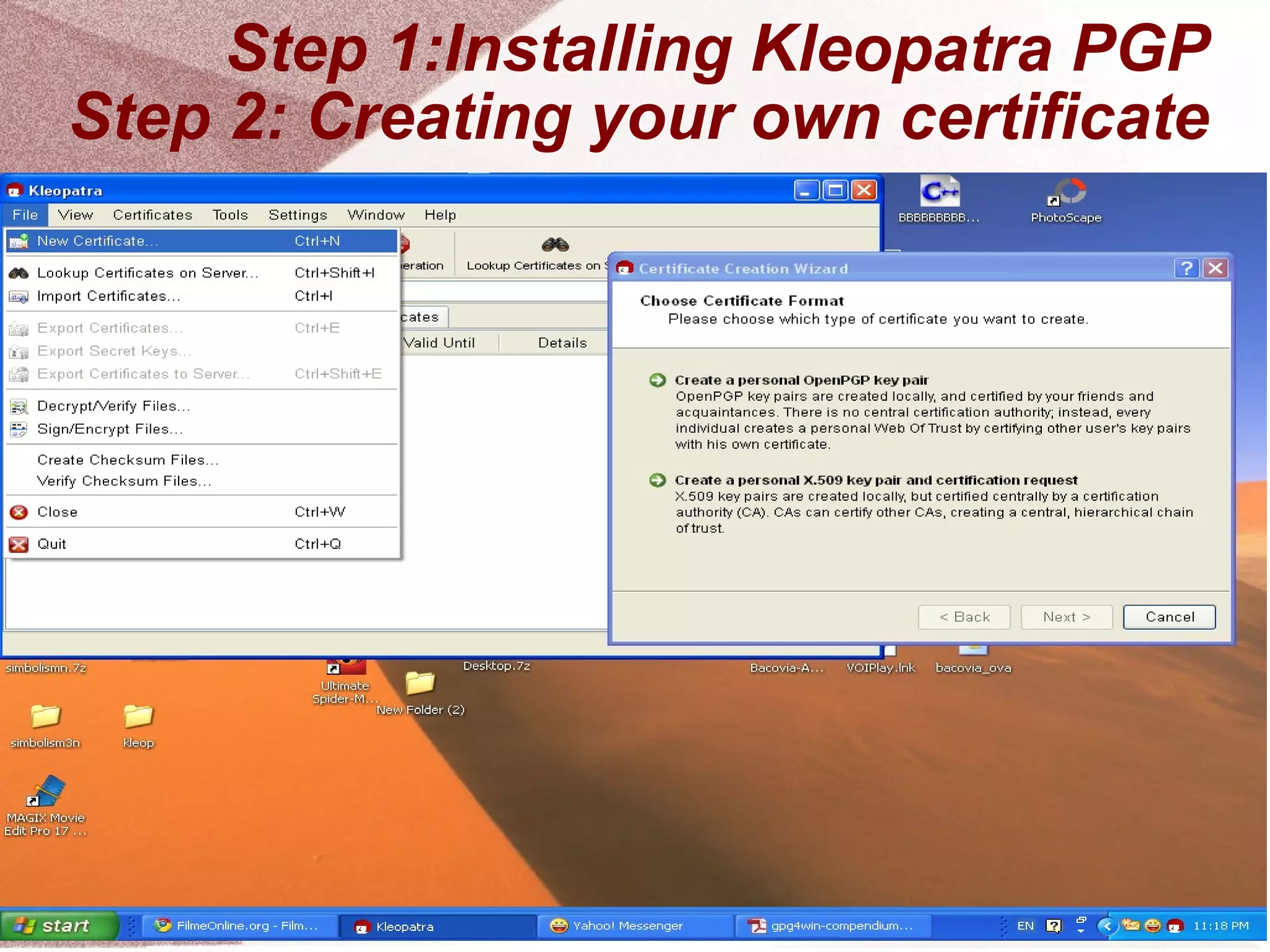
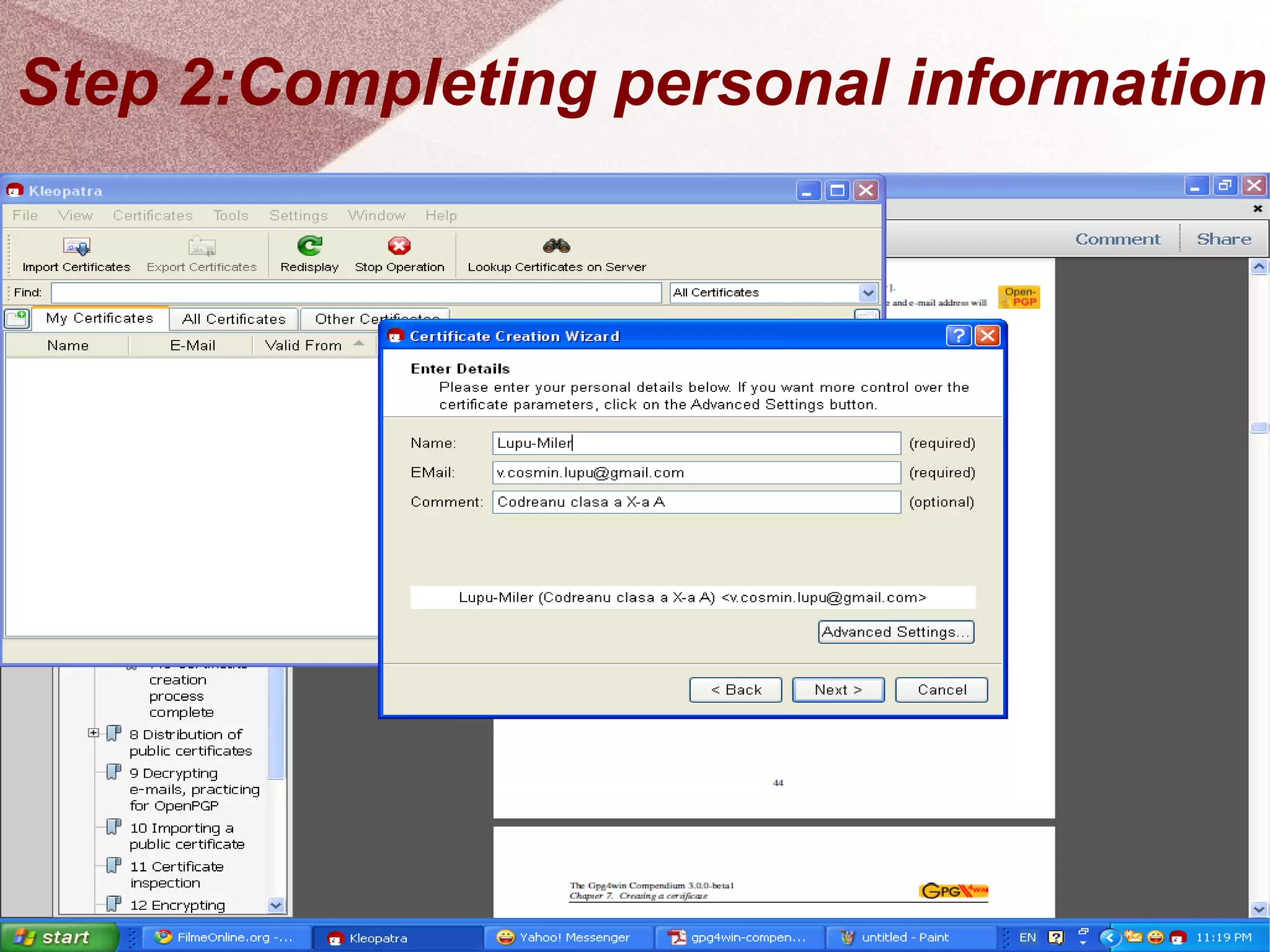
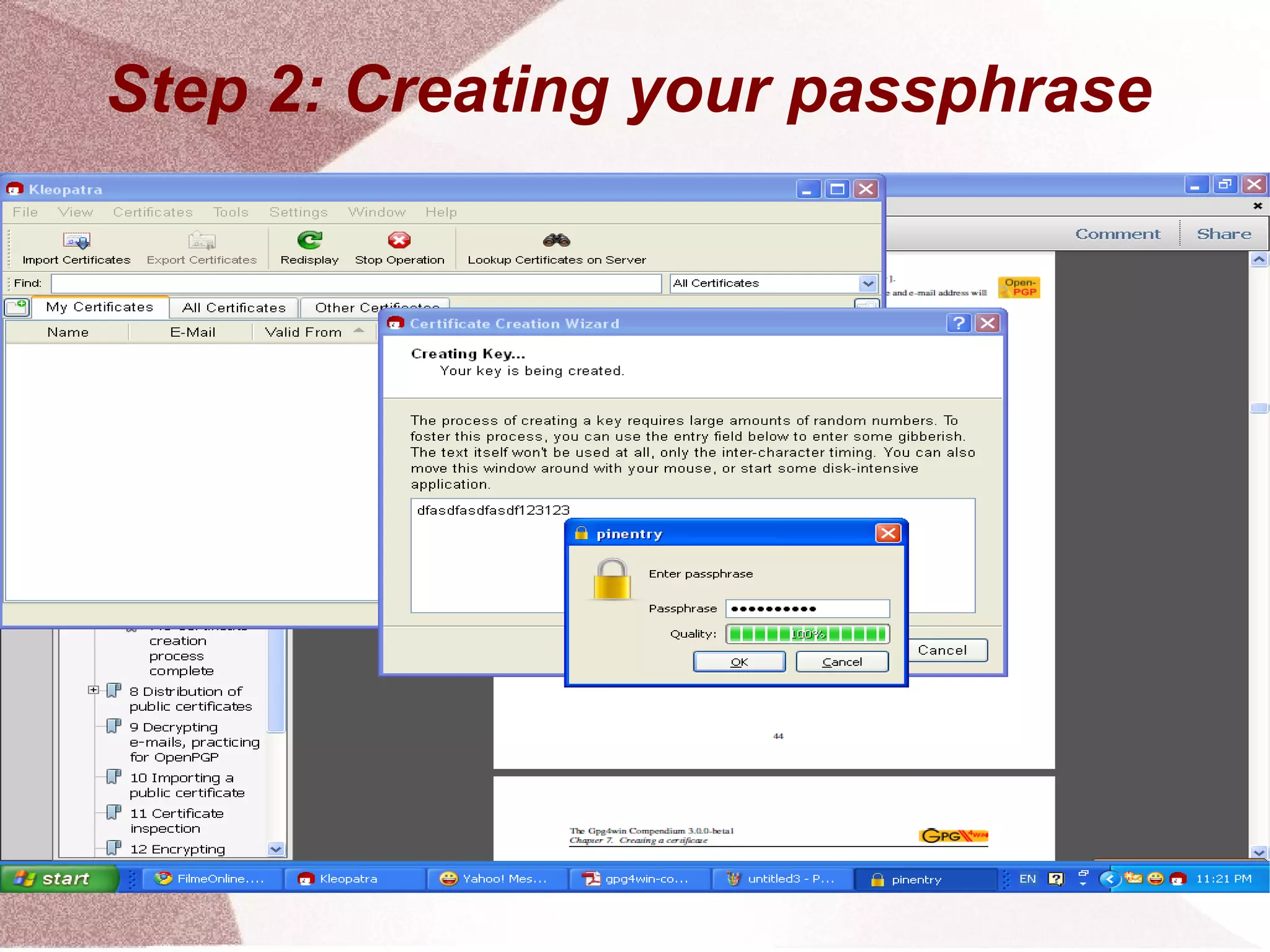
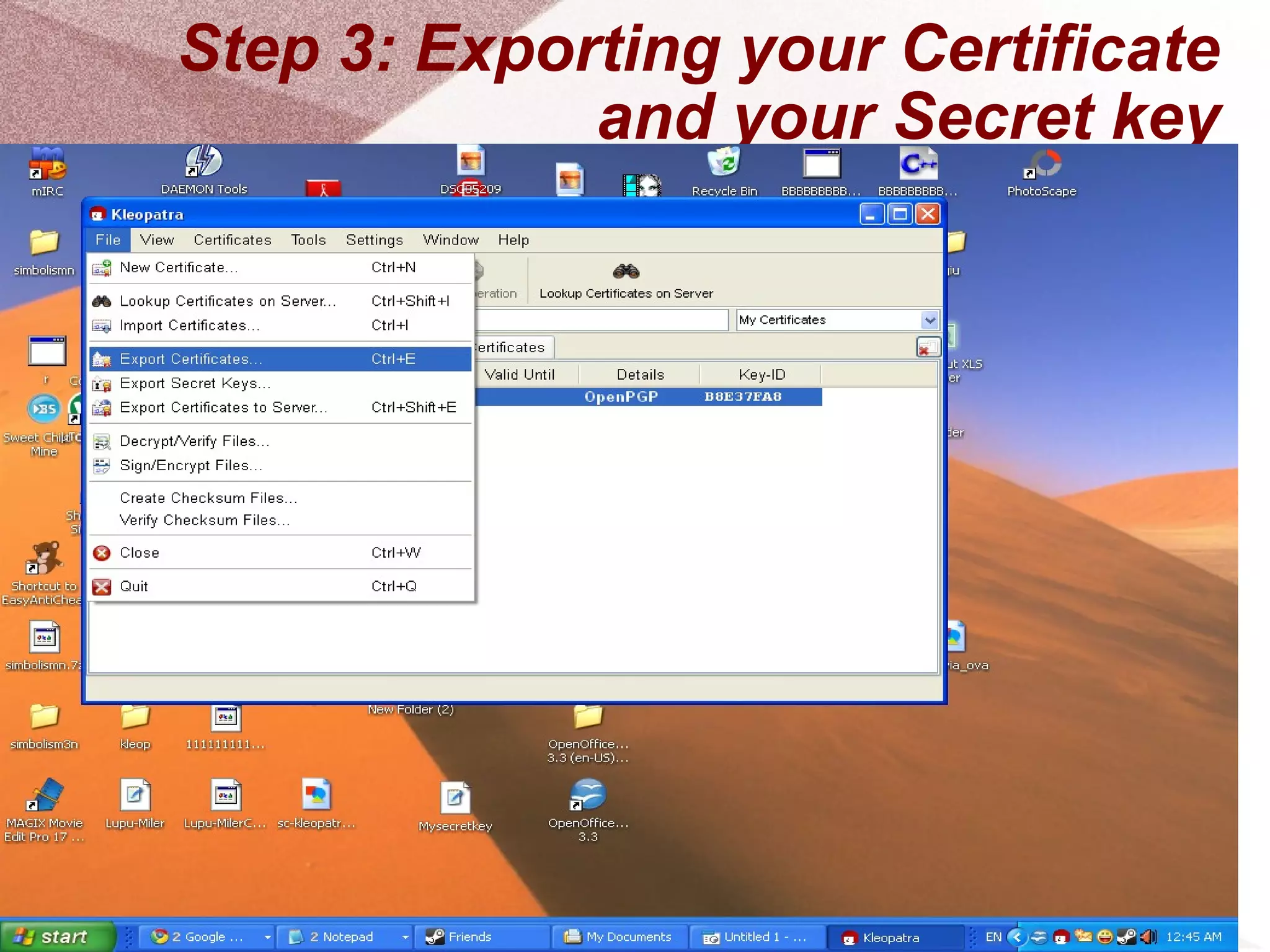
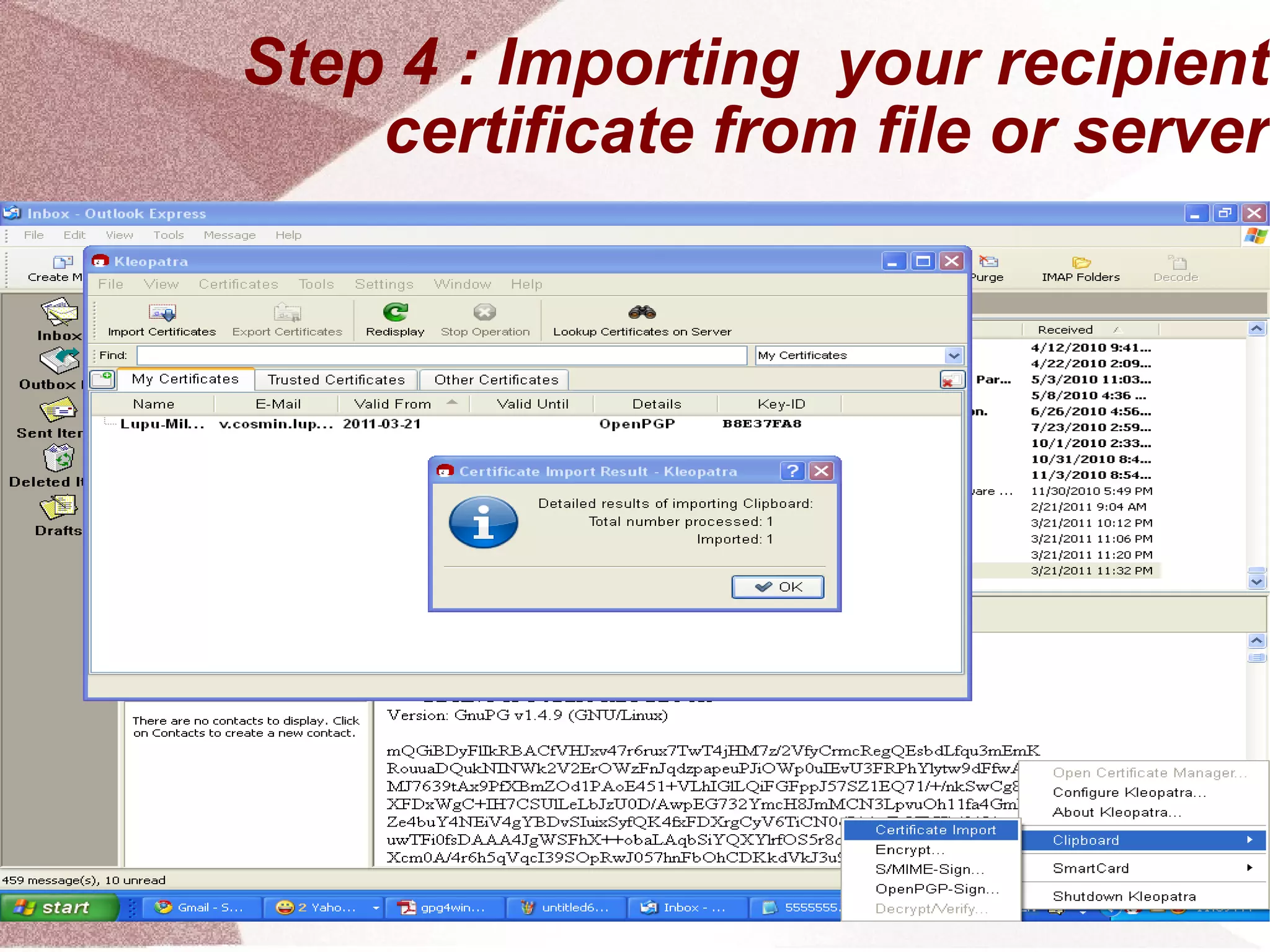
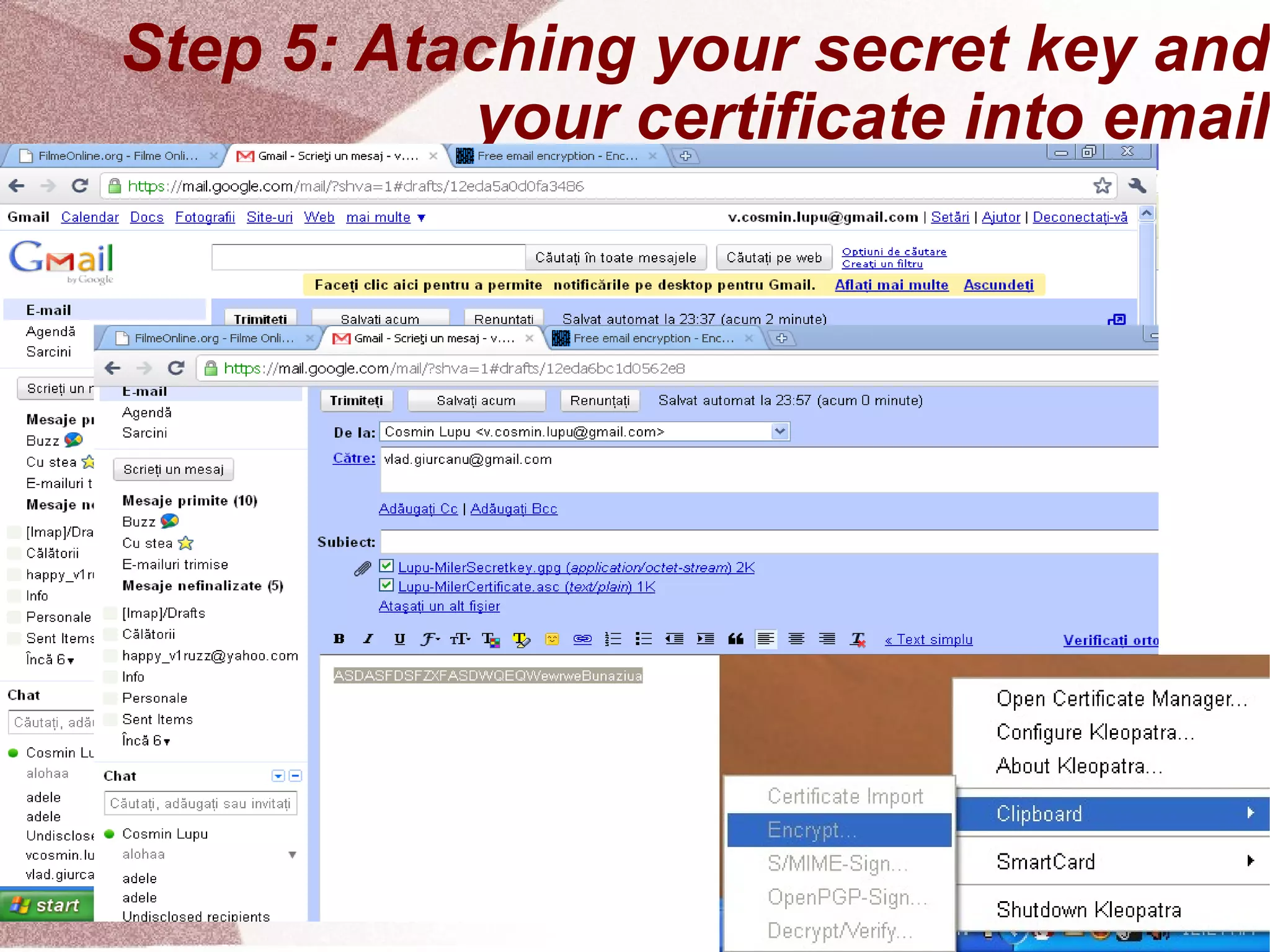
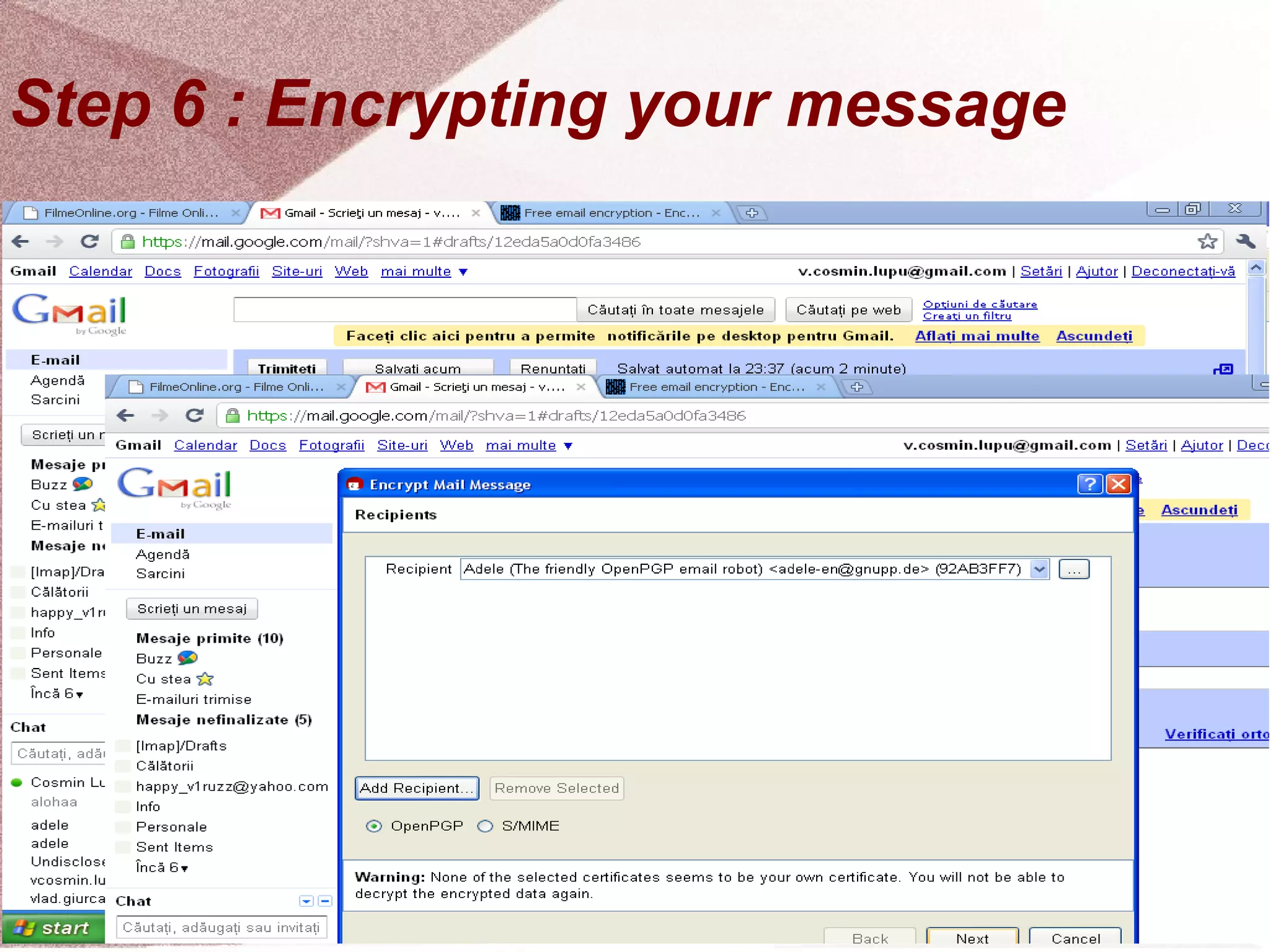
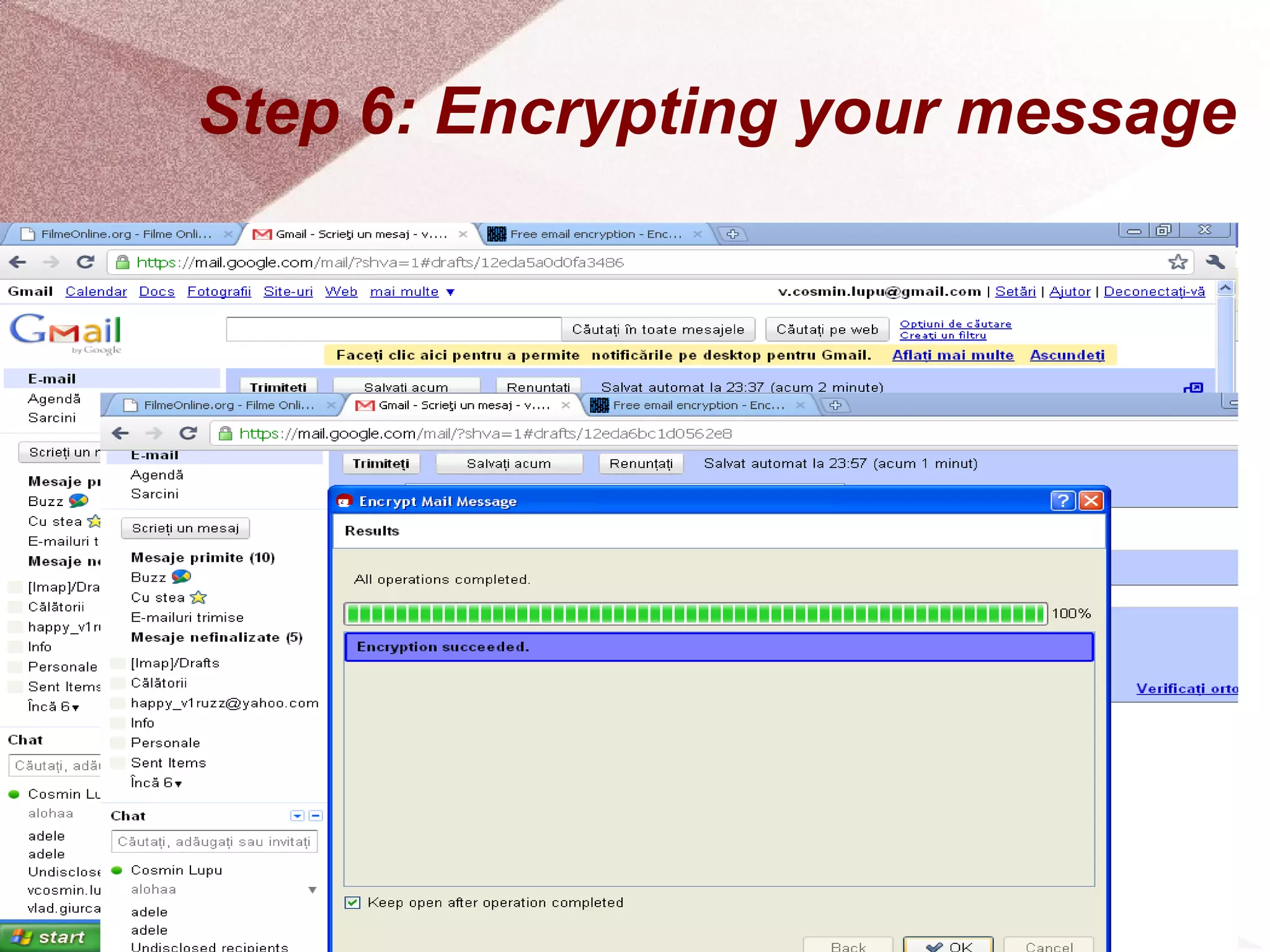
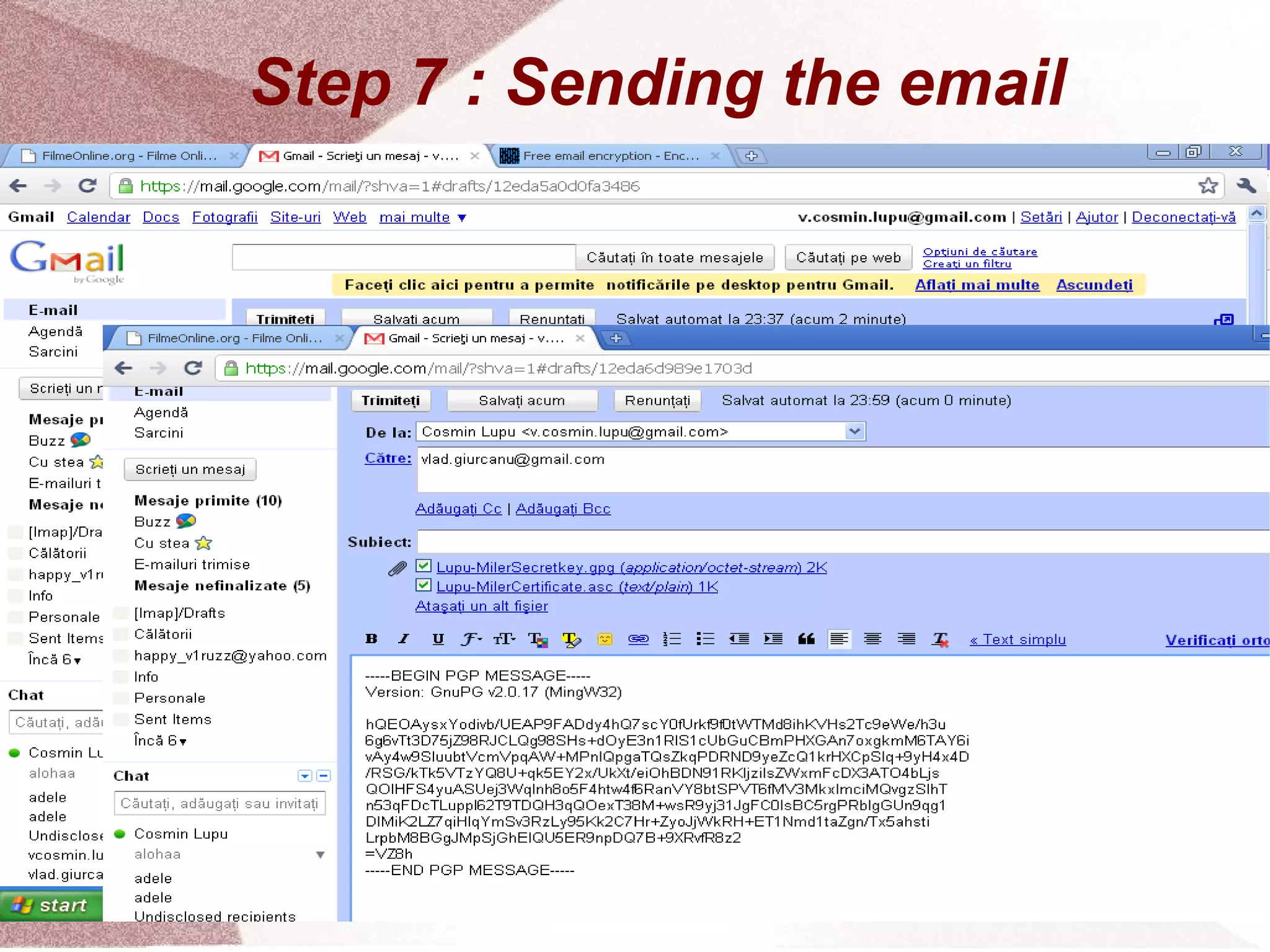
The document outlines a step-by-step guide for encrypting emails using Kleopatra PGP. It includes instructions on installing Kleopatra, creating a certificate, exporting and importing keys, and attaching them to emails for secure communication. The guide is prepared by students at Colegiul Național 'G.H. Roșca Codreanu' under the coordination of their professor.