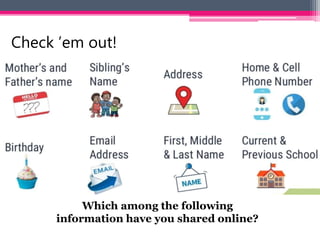
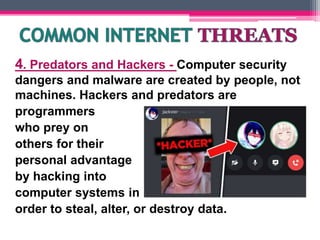
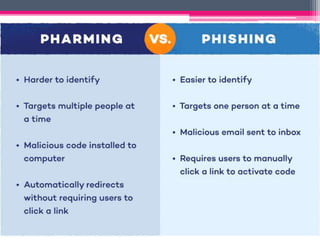
Use antivirus software and firewalls, be wary of phishing attempts, only provide personal information on secure sites, and use strong and unique passwords for each account. Be careful about what information you share publicly and avoid communicating with strangers.