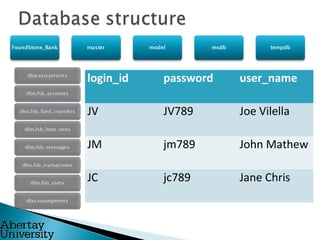
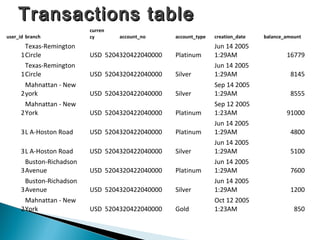
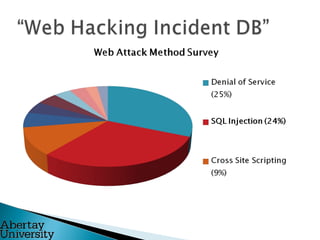
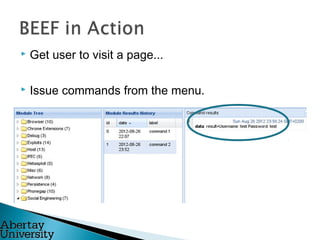
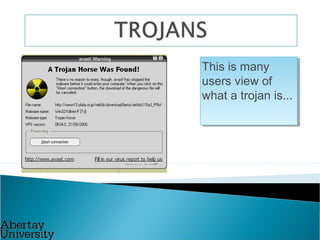
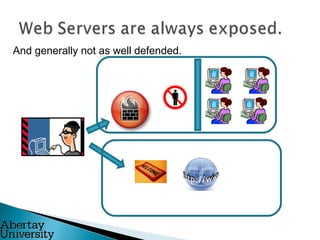
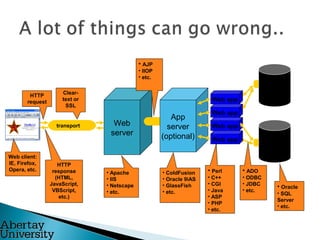
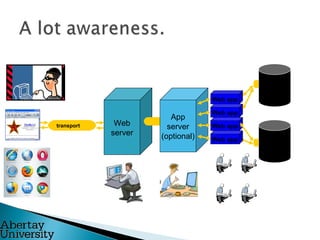
Colin McLean gave a presentation on SQL injection vulnerabilities and hacking. He demonstrated how easily a hacker could exploit an SQL injection flaw to extract sensitive data like usernames, passwords and bank account information from a vulnerable web application. He emphasized that awareness is key to mitigating hacking threats, as most modern attacks require user interaction, such as clicking a malicious link. Abertay University offers various cybersecurity training courses to help improve awareness.


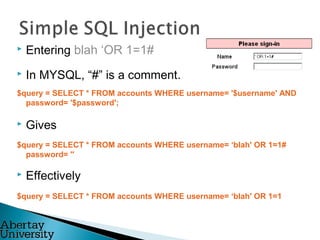
![ Entering Colin and test gives a SQL query similar to the
following: -
$query = "SELECT * FROM accounts WHERE username=‘Colin' AND
password=‘test’;
PROBLEM: - Often there is no filtering of input meaning that a
hacker can inject CODE.
Typical Code
$username = $_REQUEST["username"];
$password = $_REQUEST["password"];
$query = "SELECT * FROM accounts WHERE username='$username' AND
password='$password';](https://image.slidesharecdn.com/edinburgh-130528112448-phpapp01/85/Edinburgh-7-320.jpg)