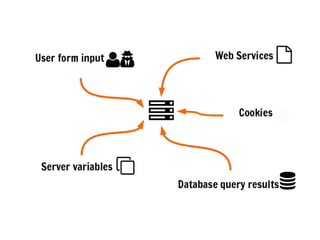
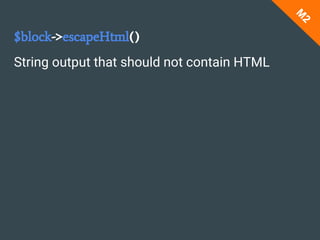
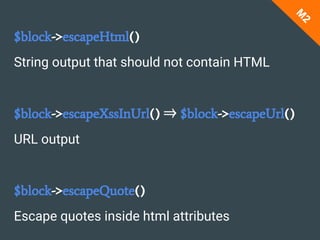
This document is a presentation by Anna about Magento security, focusing on cross-site scripting (XSS) vulnerabilities and best practices for frontend and backend input validation. It emphasizes the importance of not trusting user input and implementing multiple layers of security, including client-side validation and output escaping. The presentation also discusses Magento’s built-in validation rules and methods to enhance security against XSS attacks.


















![Add your own validator
define([
'jquery',
'jquery/ui',
'jquery/validate',
'mage/translate'
], function ($) {
$.validator.addMethod('validate-custom-name',
function (value) {
return (value !== 'anna');
}, $.mage.__('Enter valid name'));
});
M
2](https://image.slidesharecdn.com/magetitans-secureinputandoutputhandling-161114060836/85/Secure-input-and-output-handling-Mage-Titans-Manchester-2016-28-320.jpg)