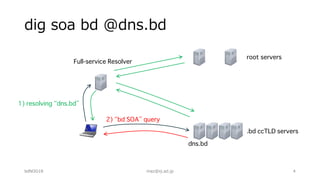
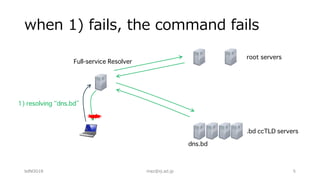
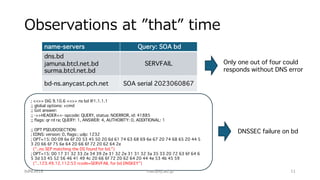
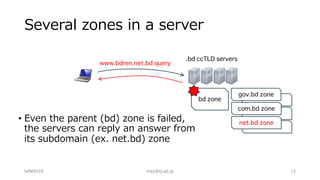
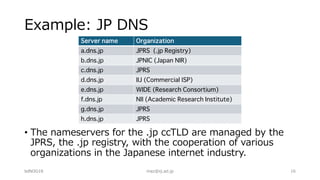
The document outlines troubleshooting techniques for DNS issues, emphasizing tools like ping, traceroute, and dig. It details the process for resolving domain names and identifying potential failure causes on various server sides, including authoritative and client configurations. Recommendations for diagnosing problems include using alternative resolvers and confirming internet connectivity, with examples of specific queries provided to illustrate effective troubleshooting.