The document discusses DNS monitoring from various perspectives, highlighting the significance of understanding DNS as a distributed database and the challenges posed by geographical and technical variations. It examines different monitoring tools and methods, such as open resolvers, public resolvers, DNS looking glasses, and atlas probes, assessing their pros and cons. Additionally, it emphasizes the importance of setting up tools like looking glasses and atlas probes to improve DNS measurement and stability.































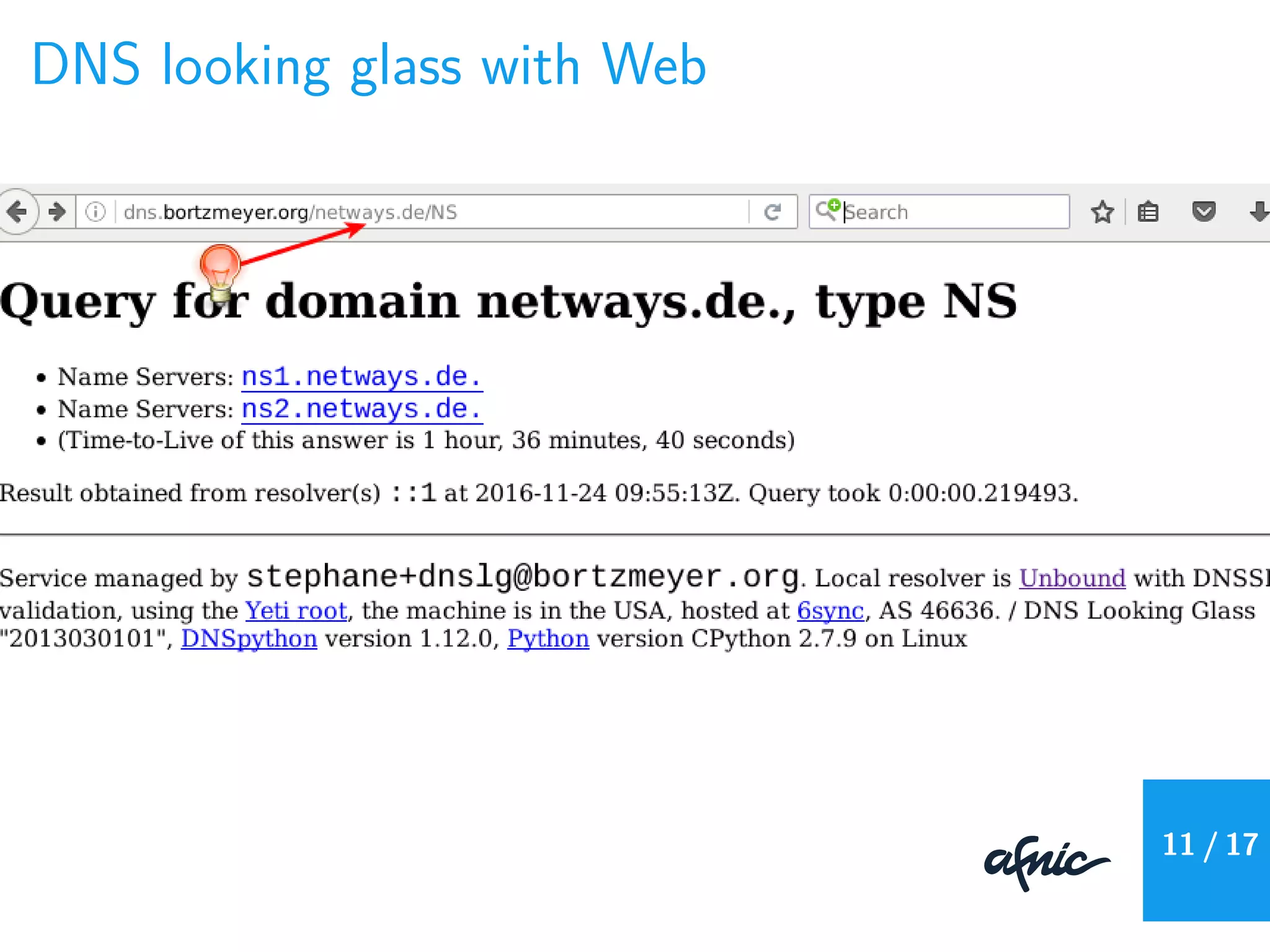
![DNS looking glass with REST + JSON
% curl -q http://dns.bortzmeyer.org/netways.de/NS?format=json
{
...
"AnswerSection": [
{
"Name": "netways.de.",
"Type": "NS",
"Target": "ns1.netways.de.",
"TTL": 4270
},
...
],
"ReturnCode": "NOERROR",
"QuestionSection": {
"Qclass": "IN",
"Qtype": "NS",
"Qname": "netways.de."
}
} 12 / 17](https://image.slidesharecdn.com/stphanebortzmeyer-dnsmonitoringfromseveralvantagepoints-161205163351/75/OSMC-2016-DNS-Monitoring-from-Several-Vantage-Points-by-Stephane-Bortzmeyer-45-2048.jpg)










![Atlas tests
% atlas-resolve --requested 10 --type AAAA www.afnic.fr
[2001:67c:2218:30::24] : 10 occurrences
Test #6939593 done at 2016-11-24T10:53:01Z
% atlas-resolve --requested 20 --country FR www.thepiratebay.se
[ERROR: SERVFAIL] : 4 occurrences
[104.31.18.30 104.31.19.30] : 10 occurrences
[ERROR: NXDOMAIN] : 2 occurrences
[127.0.0.1] : 3 occurrences
Test #6939617 done at 2016-11-24T11:22:49Z
15 / 17](https://image.slidesharecdn.com/stphanebortzmeyer-dnsmonitoringfromseveralvantagepoints-161205163351/75/OSMC-2016-DNS-Monitoring-from-Several-Vantage-Points-by-Stephane-Bortzmeyer-57-2048.jpg)