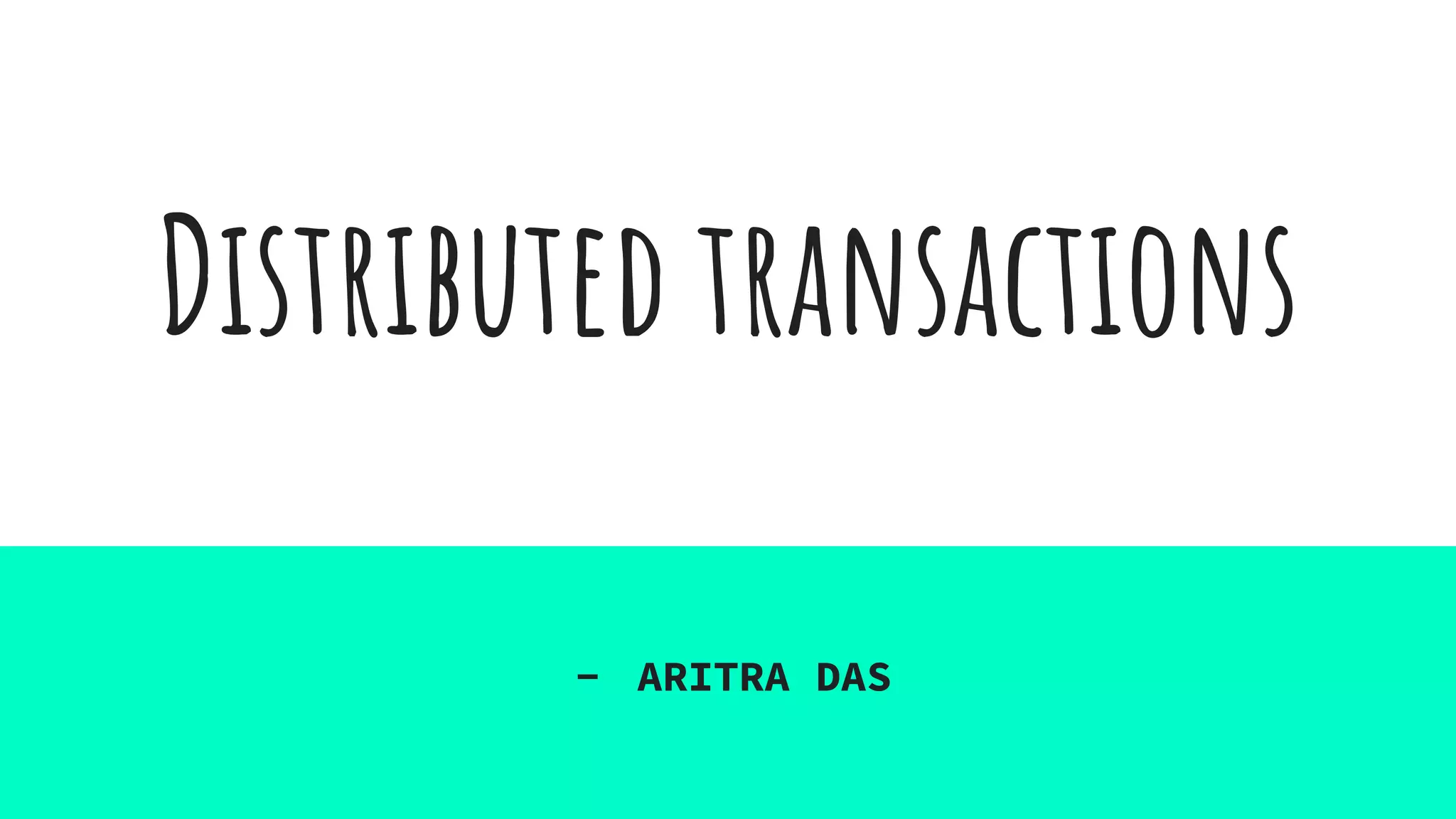
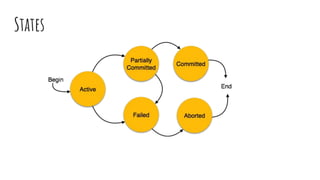
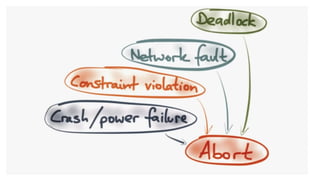
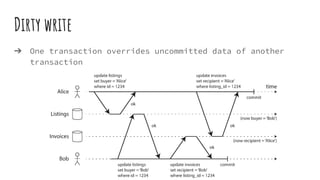
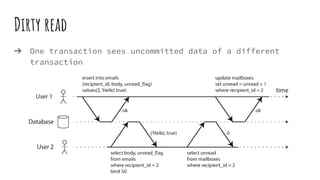
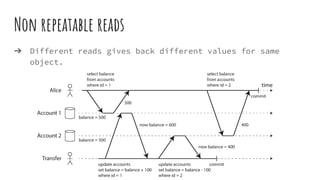
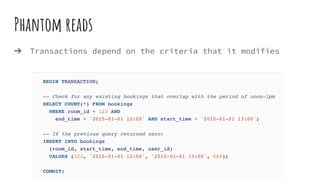
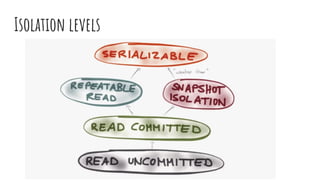
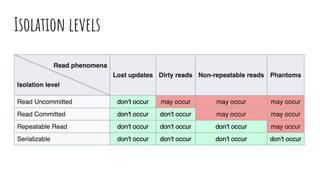
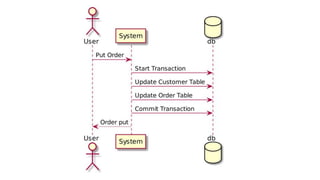
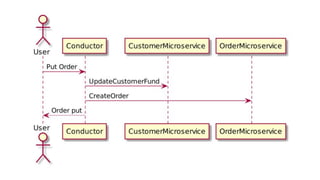
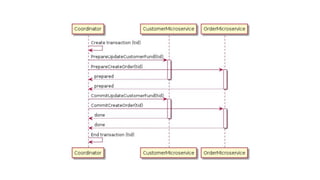
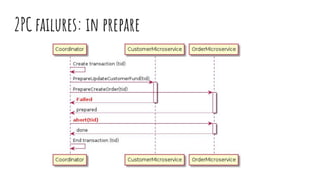
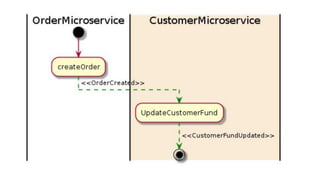
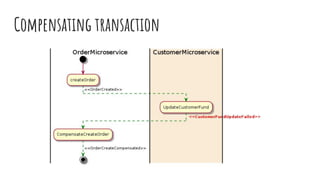
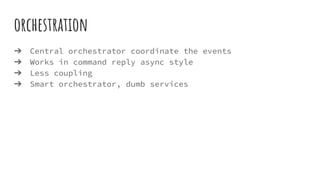
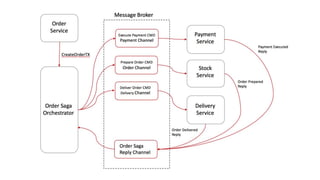
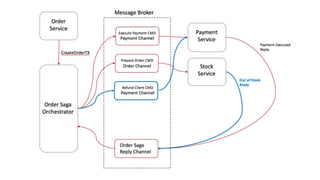
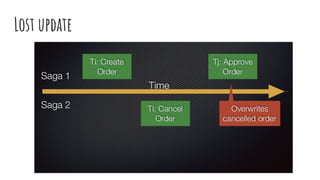
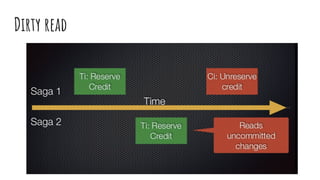
This document discusses distributed transactions and database isolation levels. It covers ACID properties including atomicity, consistency, isolation, and durability. Isolation levels like read uncommitted, read committed, and serializable are explained. Distributed transaction protocols like two phase commit are described along with their failures and disadvantages. Finally, sagas and compensation transactions are introduced as asynchronous alternatives to two phase commit, along with potential isolation anomalies and countermeasures.