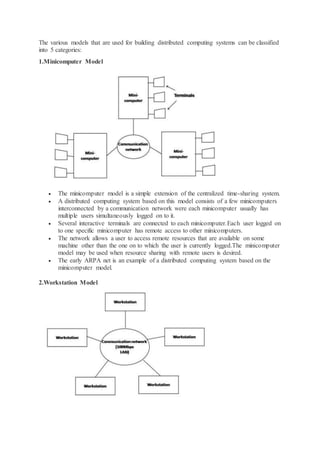
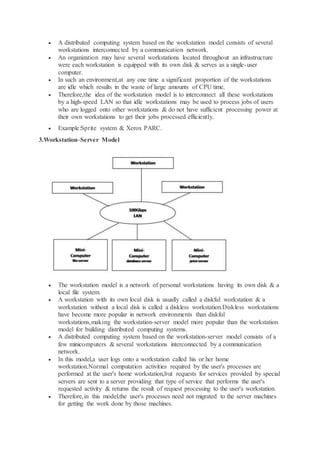
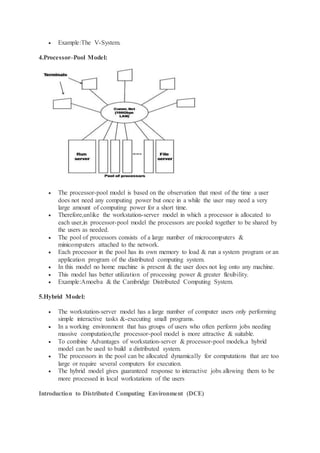
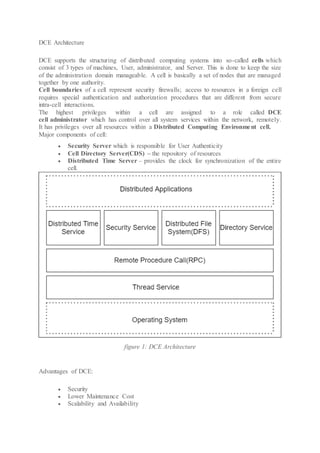
The document discusses the history and goals of distributed systems. It begins by describing how computers evolved from large centralized mainframes in the 1940s-1980s, to networked systems in the mid-1980s enabled by microprocessors and computer networks. The key goals of distributed systems are to make resources accessible across a network, hide the distributed nature of resources to provide transparency, remain open to new services, and scale effectively with increased users and resources. Examples of distributed systems include the internet, intranets, and worldwide web.