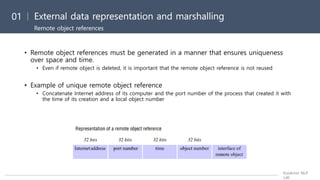
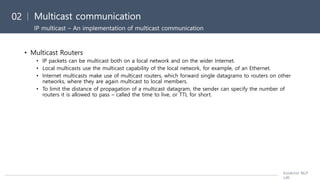
The document discusses several key issues related to data communication between computers including different data formats, marshalling or converting data to a common format for transmission, and representation standards like CORBA CDR, Java serialization, and XML. It also covers remote object references, multicast communication, and the failure characteristics of unreliable multicast.

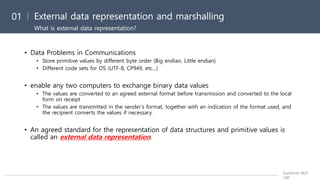

![• CORBA CDR is the external data representation defined
with CORBA 2.0 [OMG 2004a].
• It consists of primitive type and constructed type.
Type Representation
sequence length(unsignedlong) followedby elements in order
string length(unsignedlong) followedby characters in order (can also
can have widecharacters)
array arrayelements in order (no length specified becauseit is fixed)
struct in theorder of declaration of thecomponents
enumerated unsignedlong(thevalues are specifiedby theorder declared)
union type tag followed by the selected member](https://image.slidesharecdn.com/171030interprocesscommunication-190321055145/85/Distributed-System-ch4-interprocess-communication-4-320.jpg)
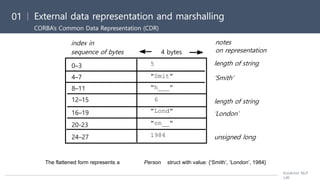



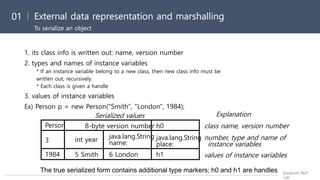

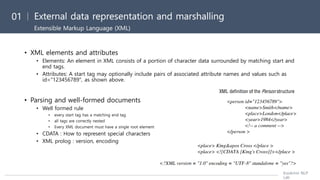









![[Distributed System] ch4. interprocess communication](https://image.slidesharecdn.com/171030interprocesscommunication-190321055145/85/Distributed-System-ch4-interprocess-communication-23-320.jpg)