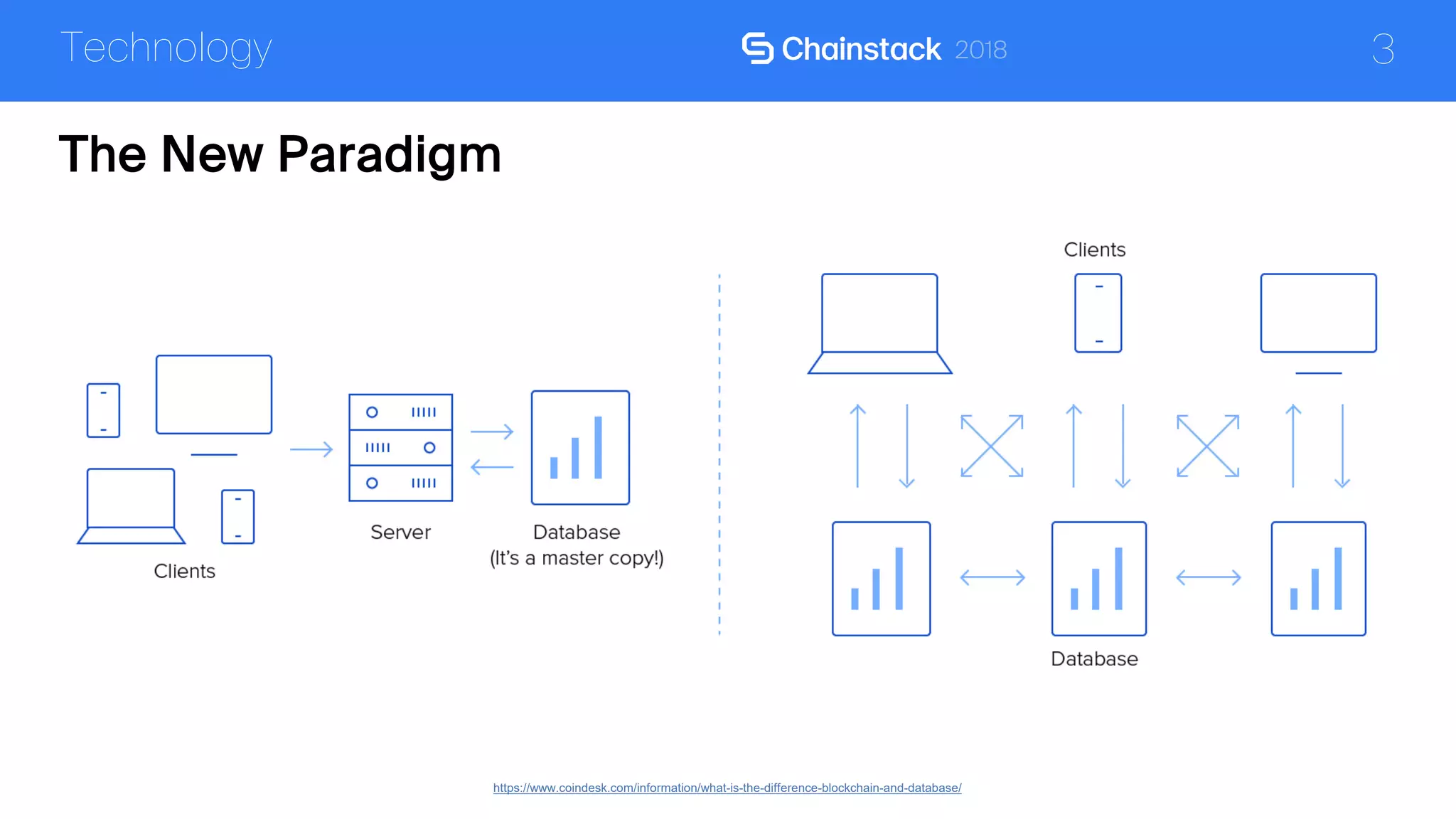
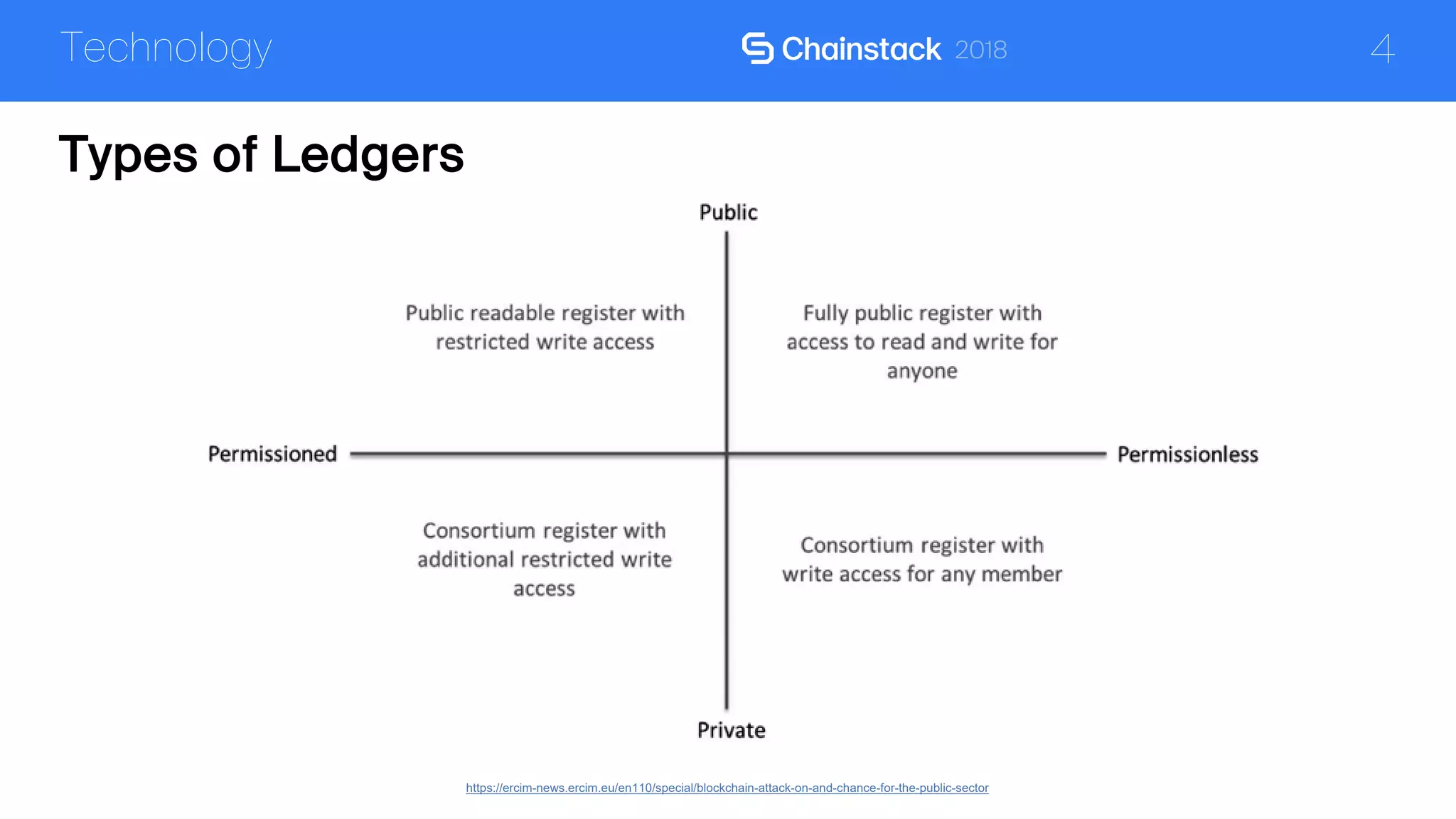
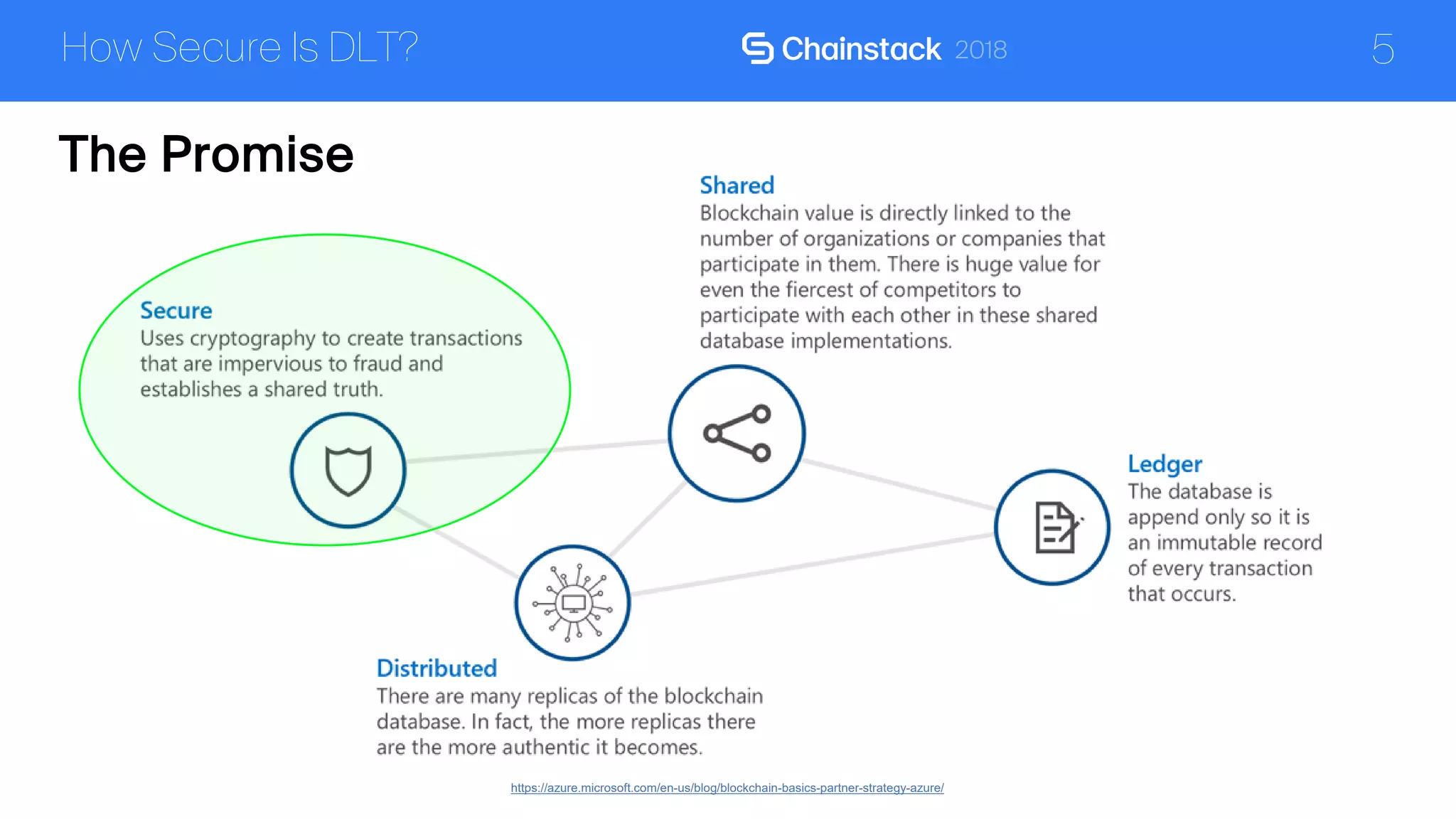
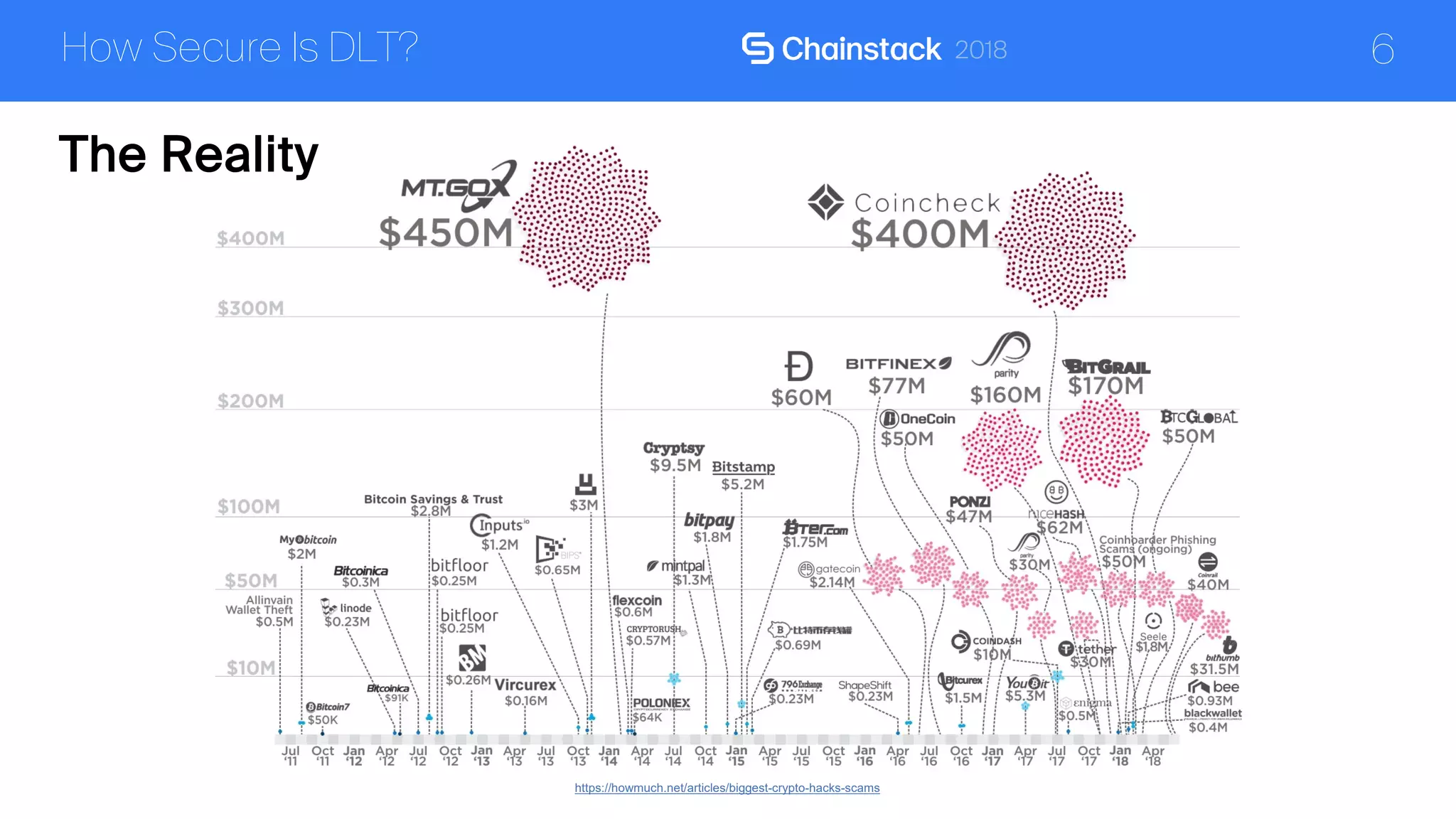
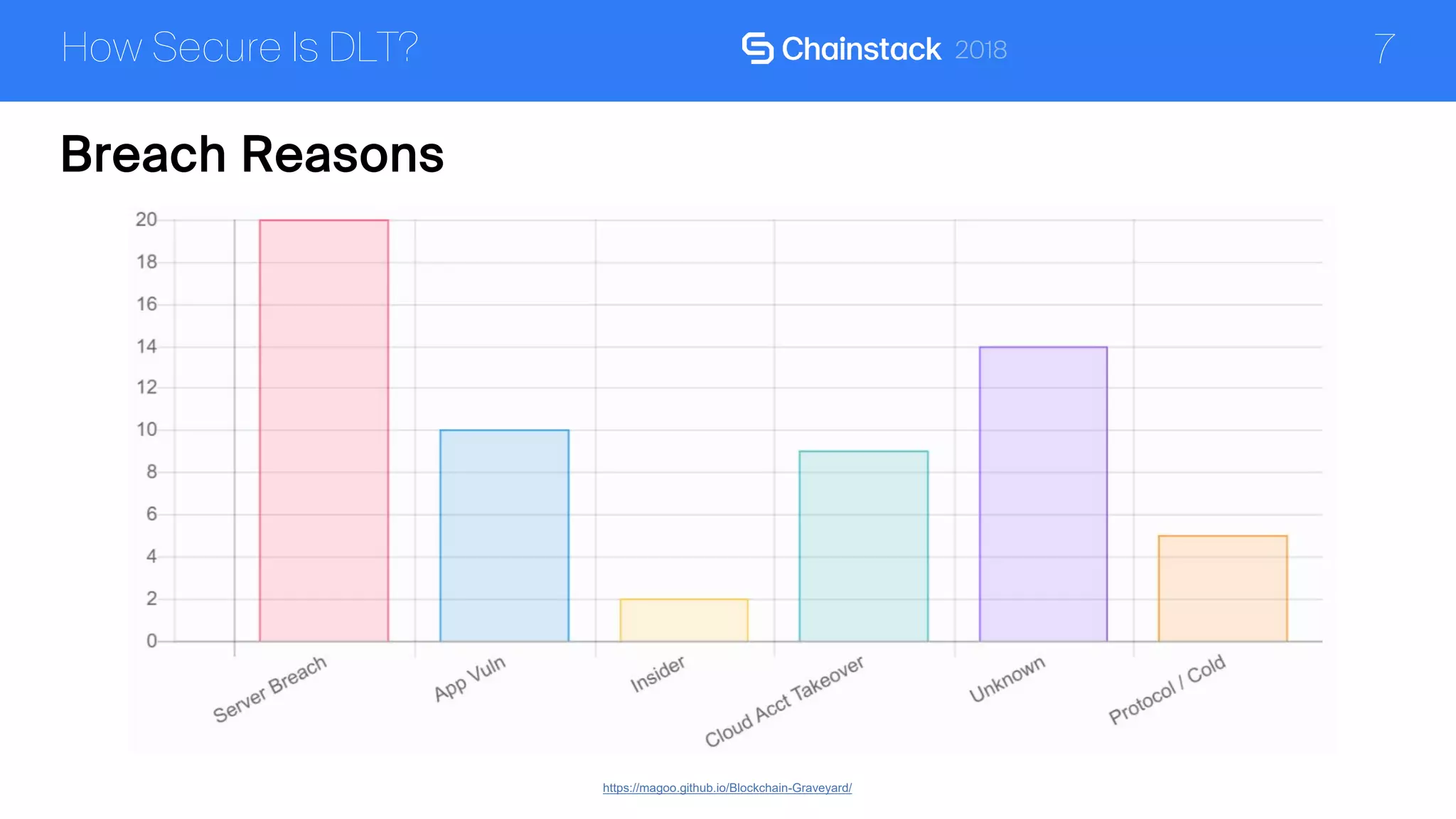
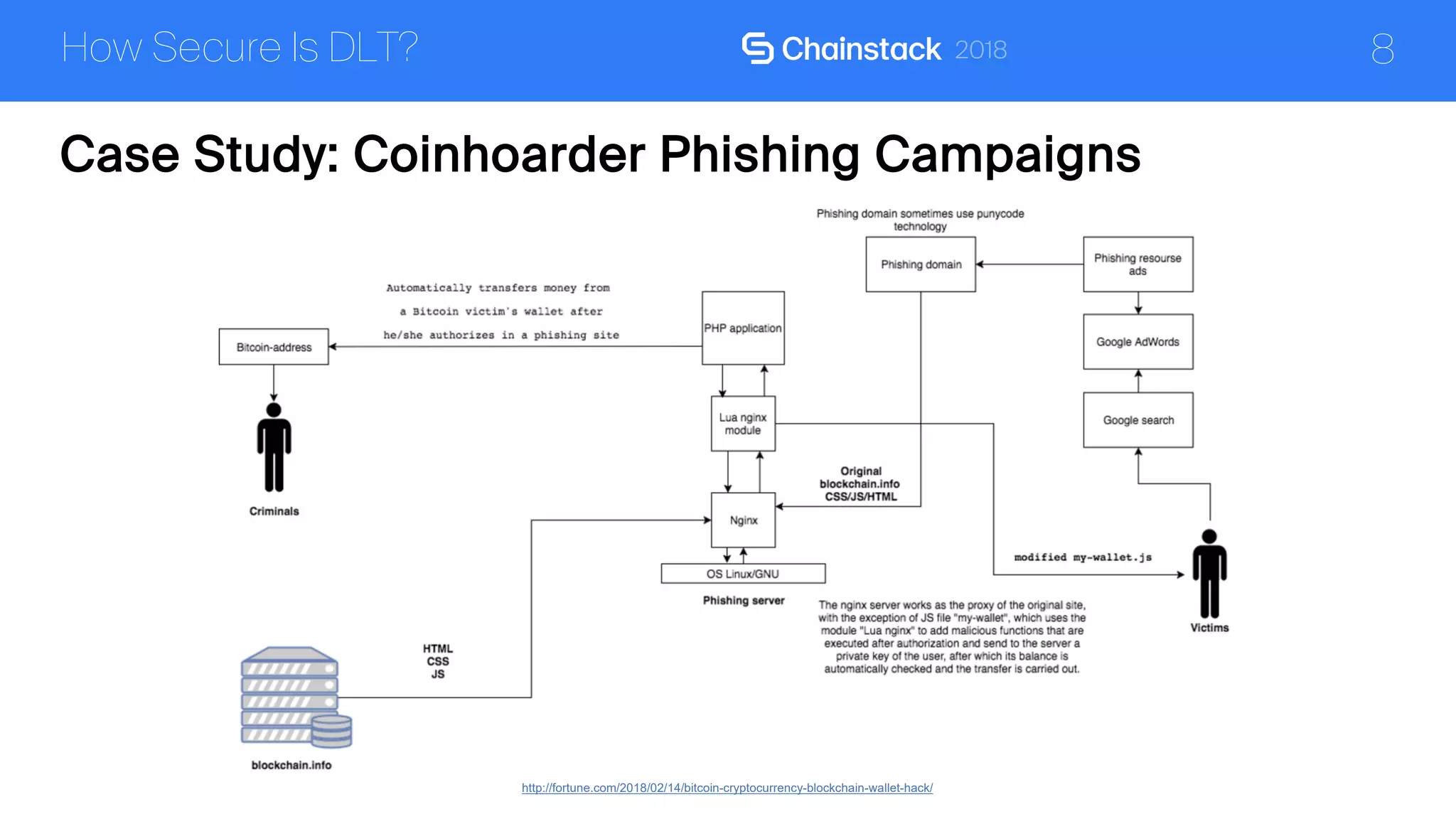
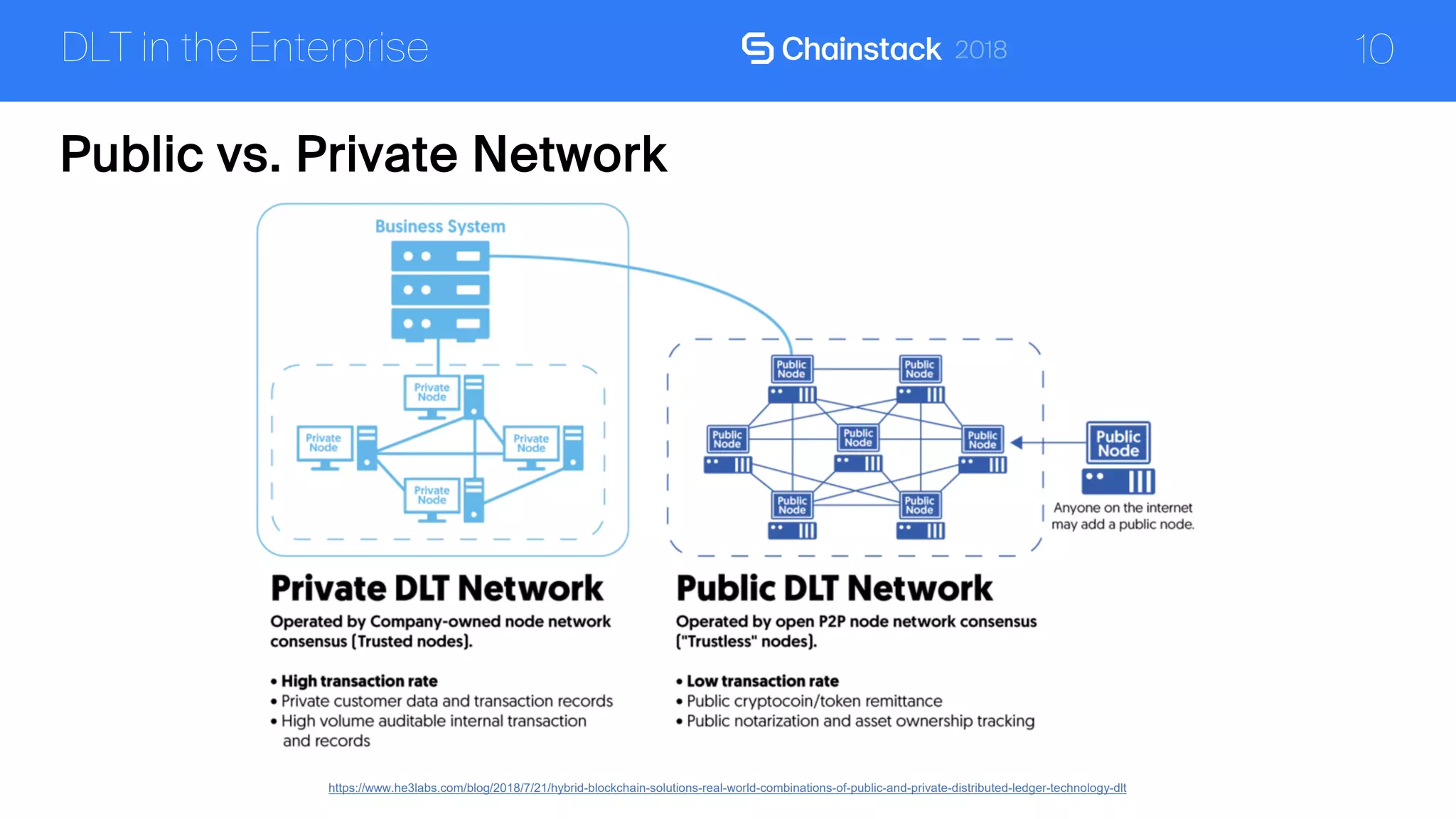
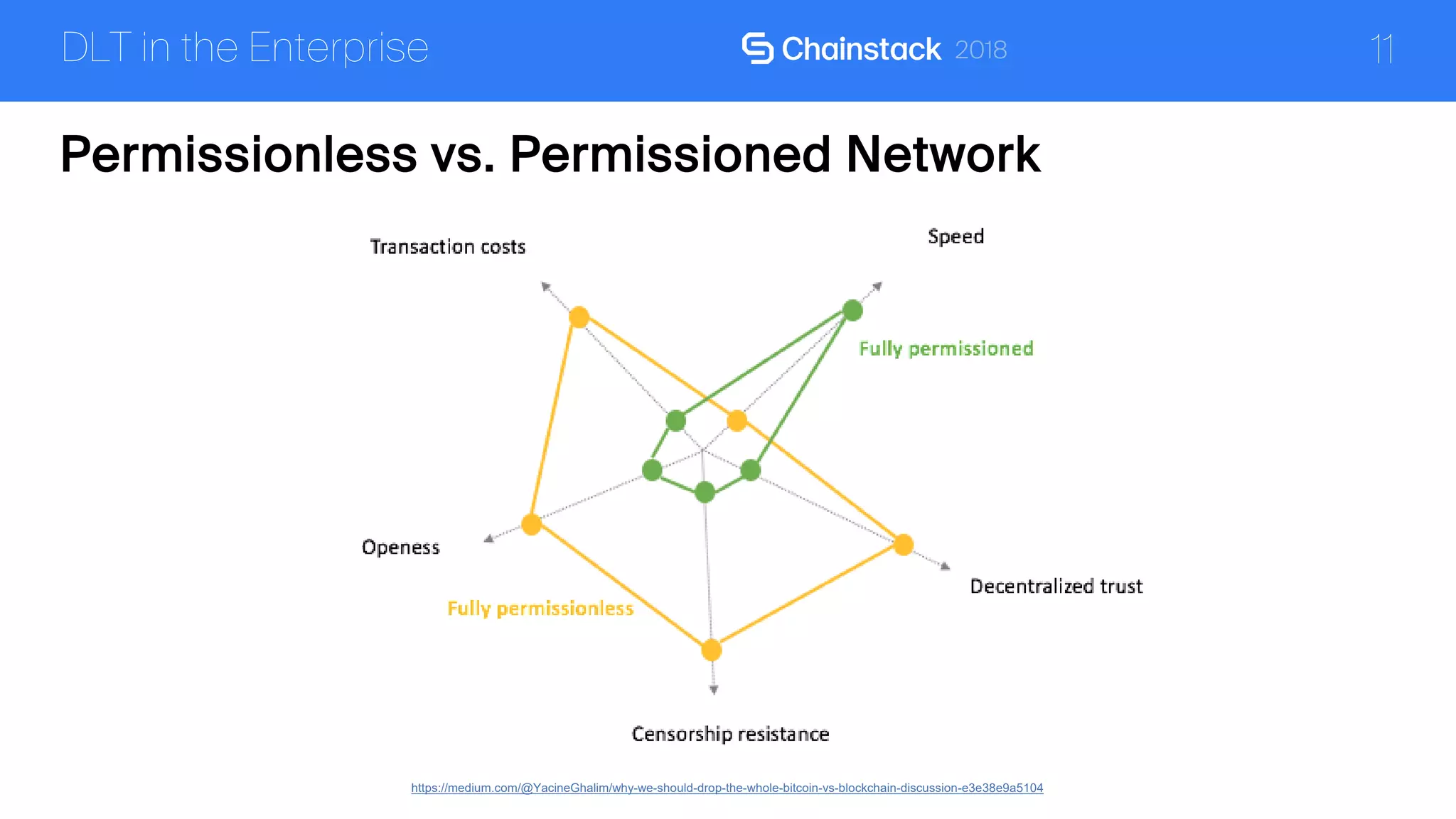
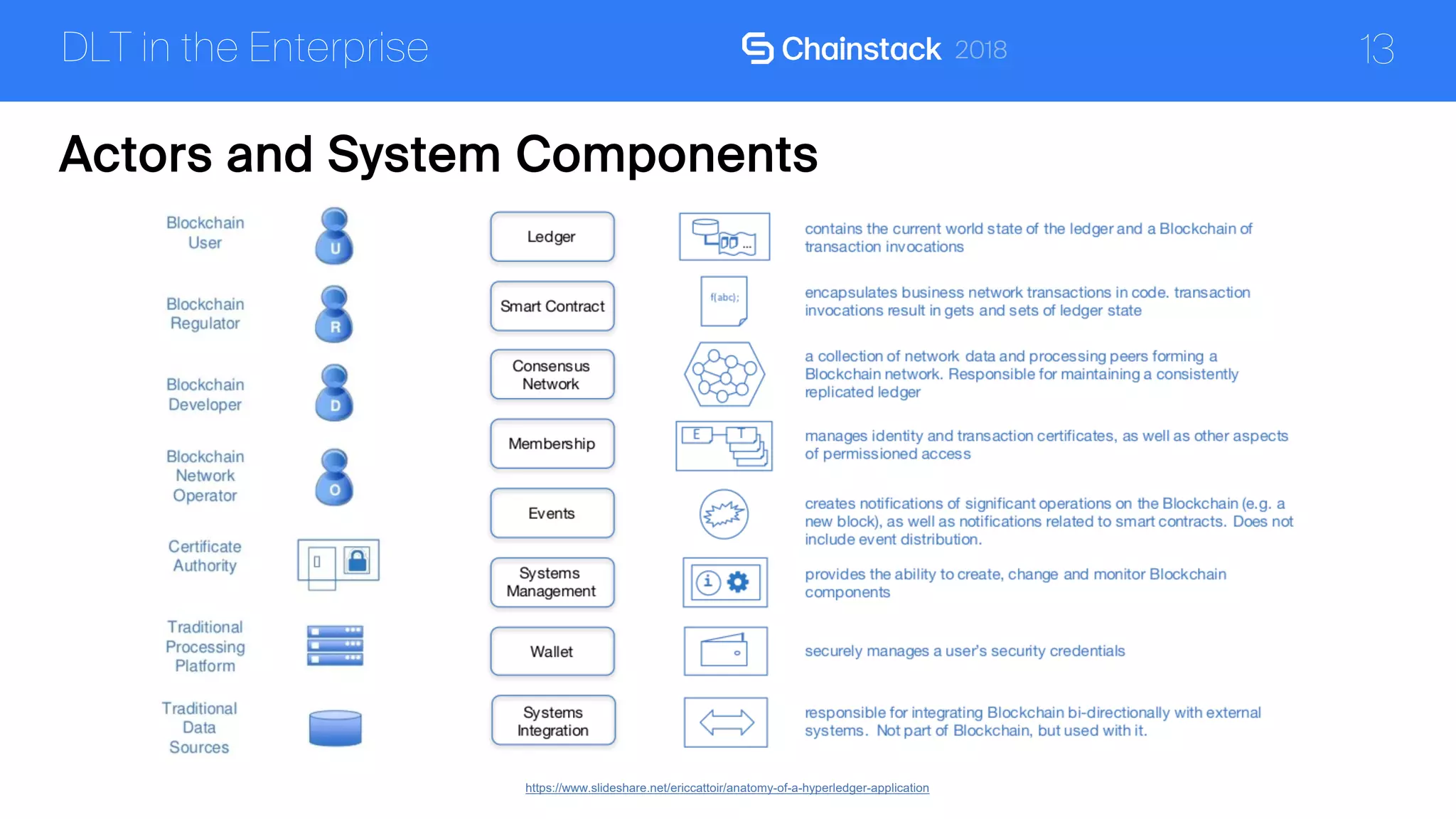
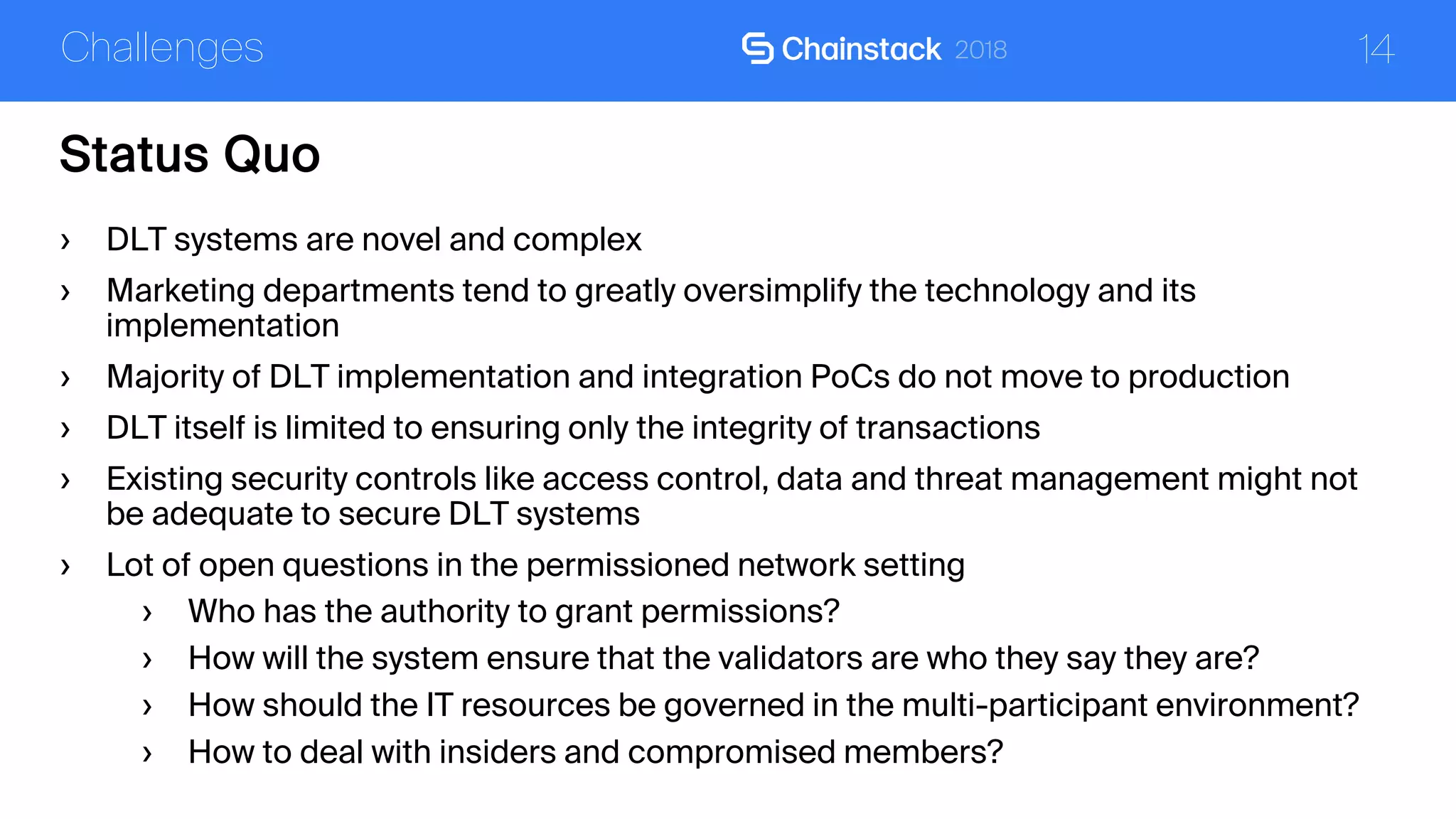
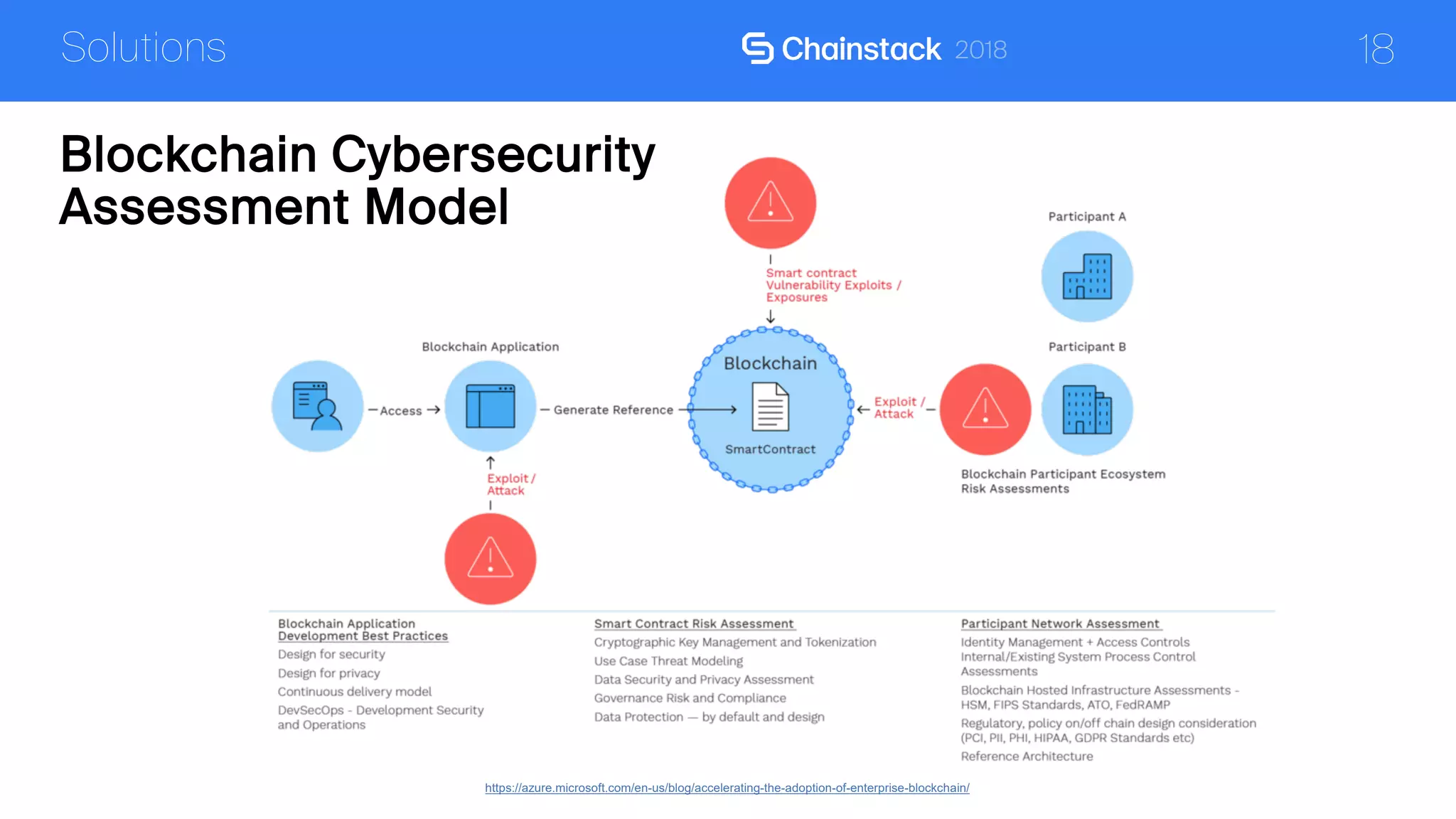
The document discusses the security challenges and solutions associated with Distributed Ledger Technology (DLT) in enterprise environments. It highlights issues such as protocol vulnerabilities, weak authentication, insider threats, and the complexities of implementing security measures. It also outlines best practices and advanced measures for securing DLT systems, emphasizing the use of third-party blockchain-as-a-service solutions.