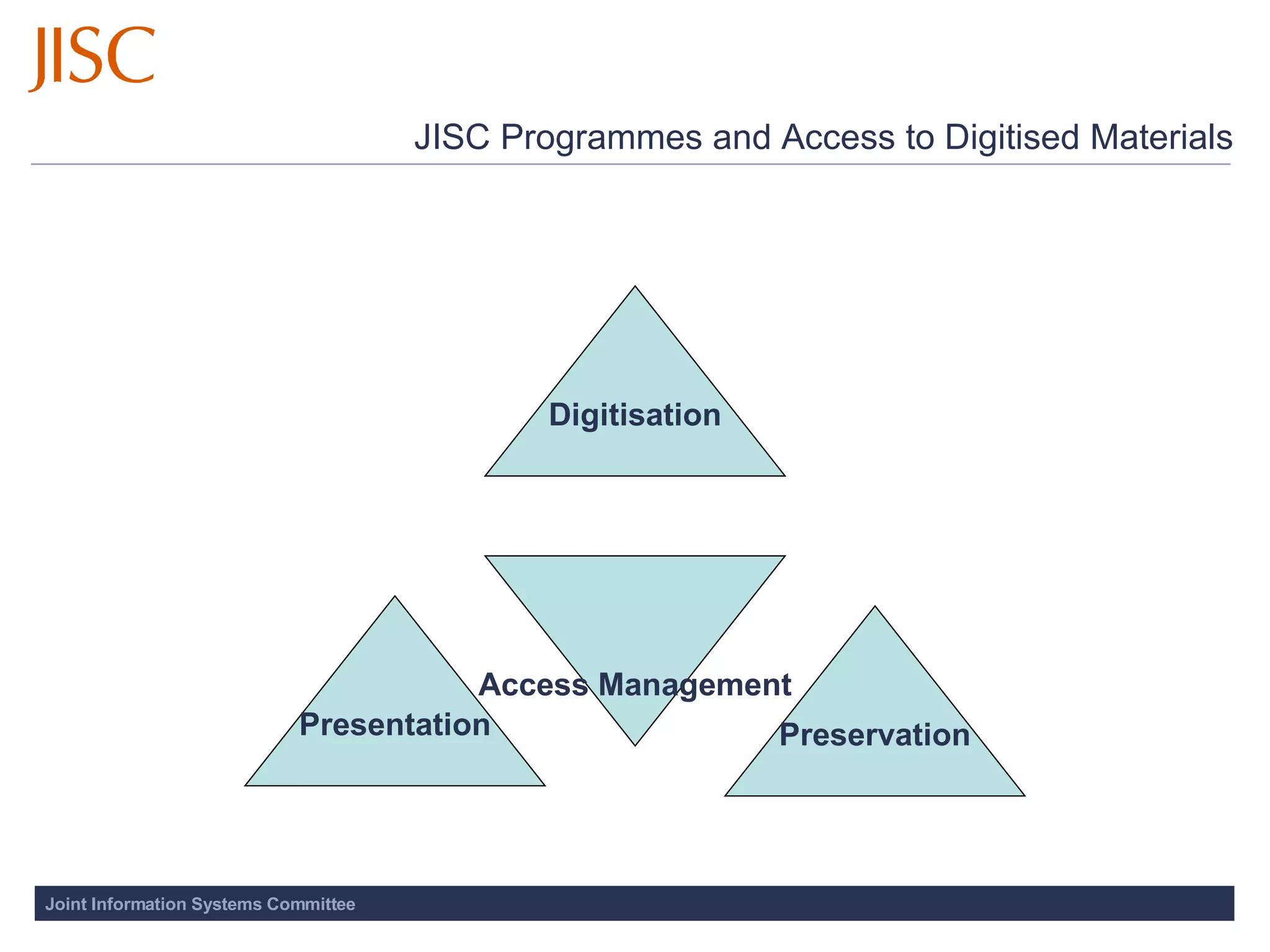
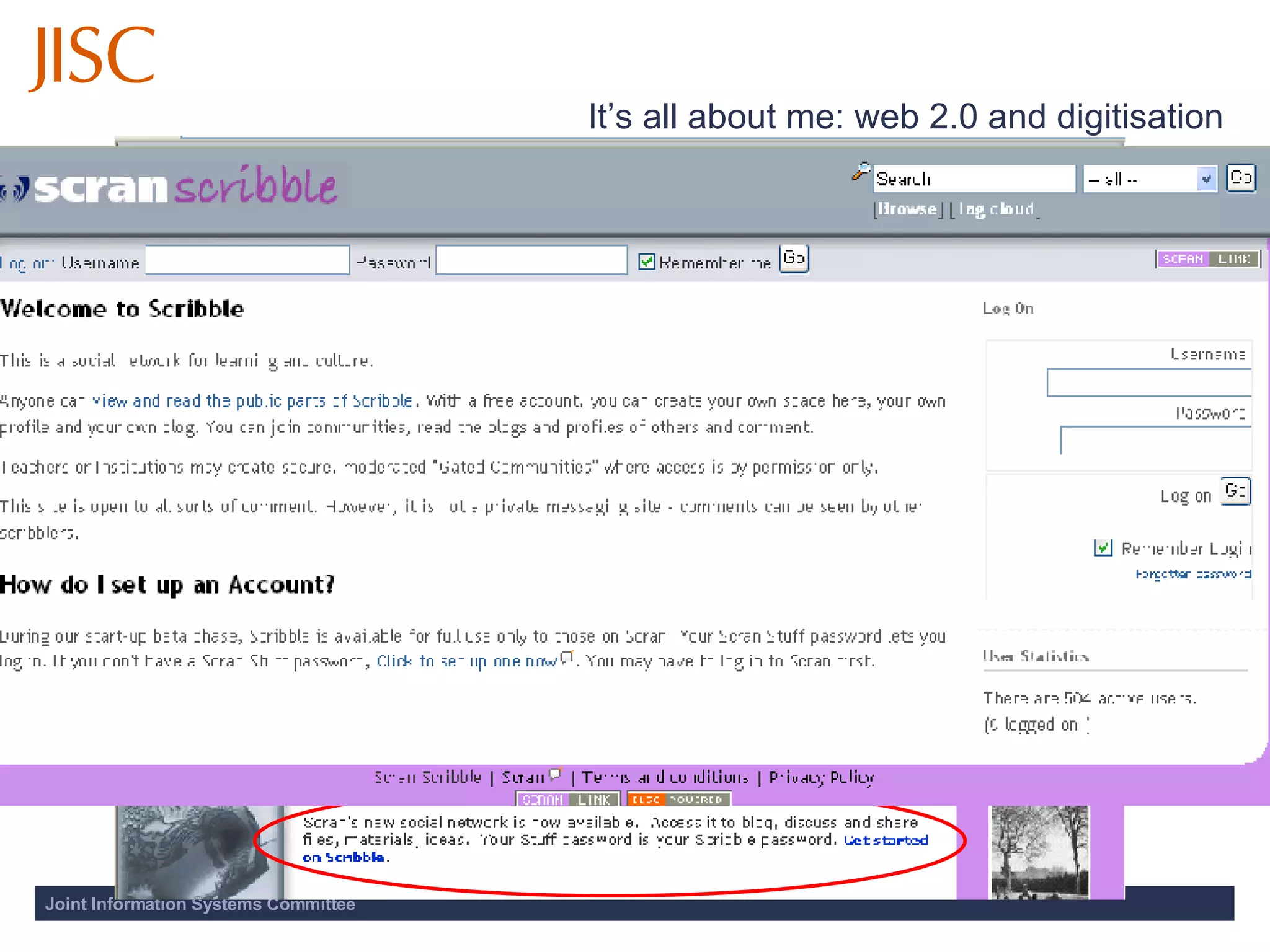
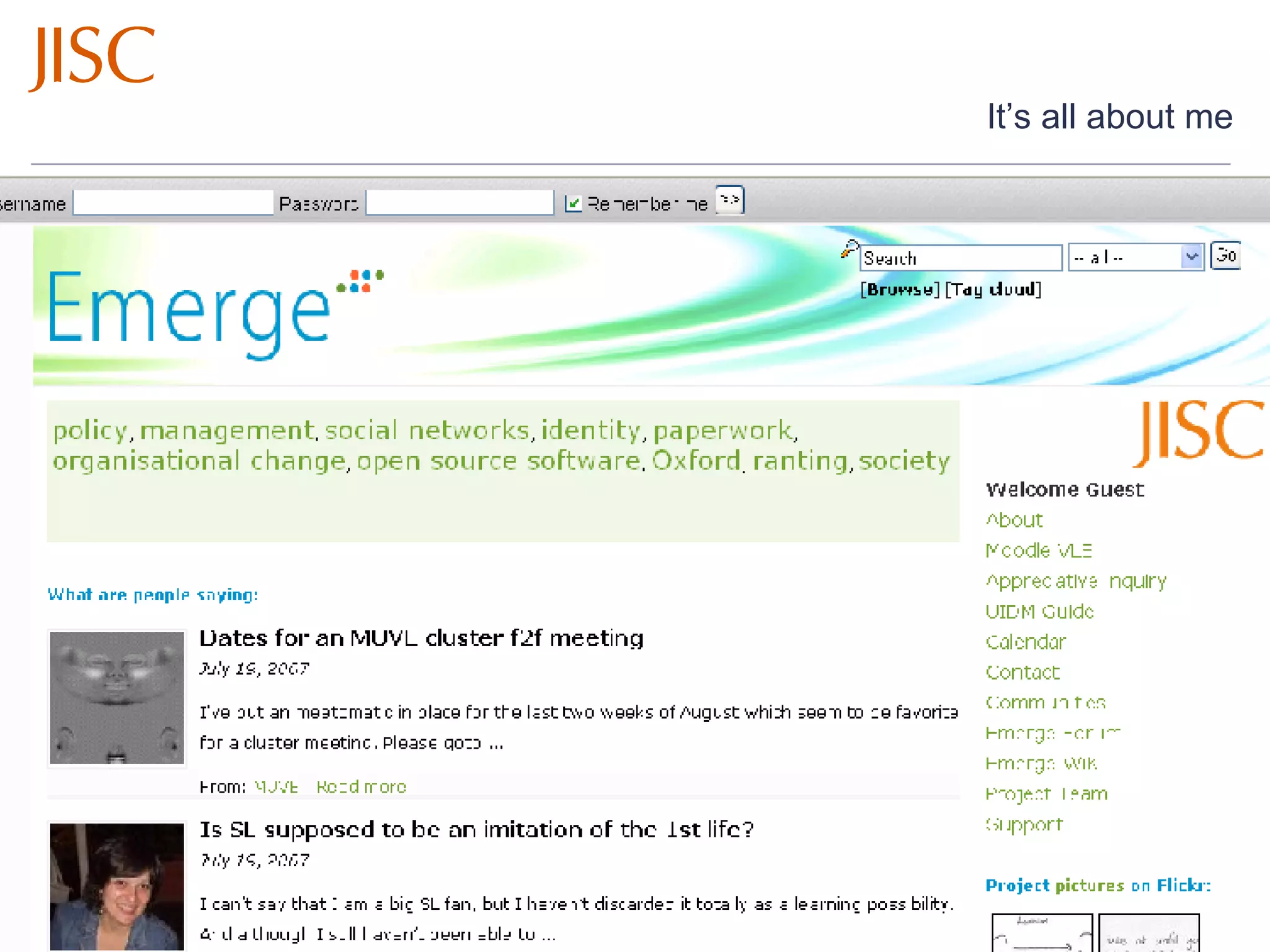
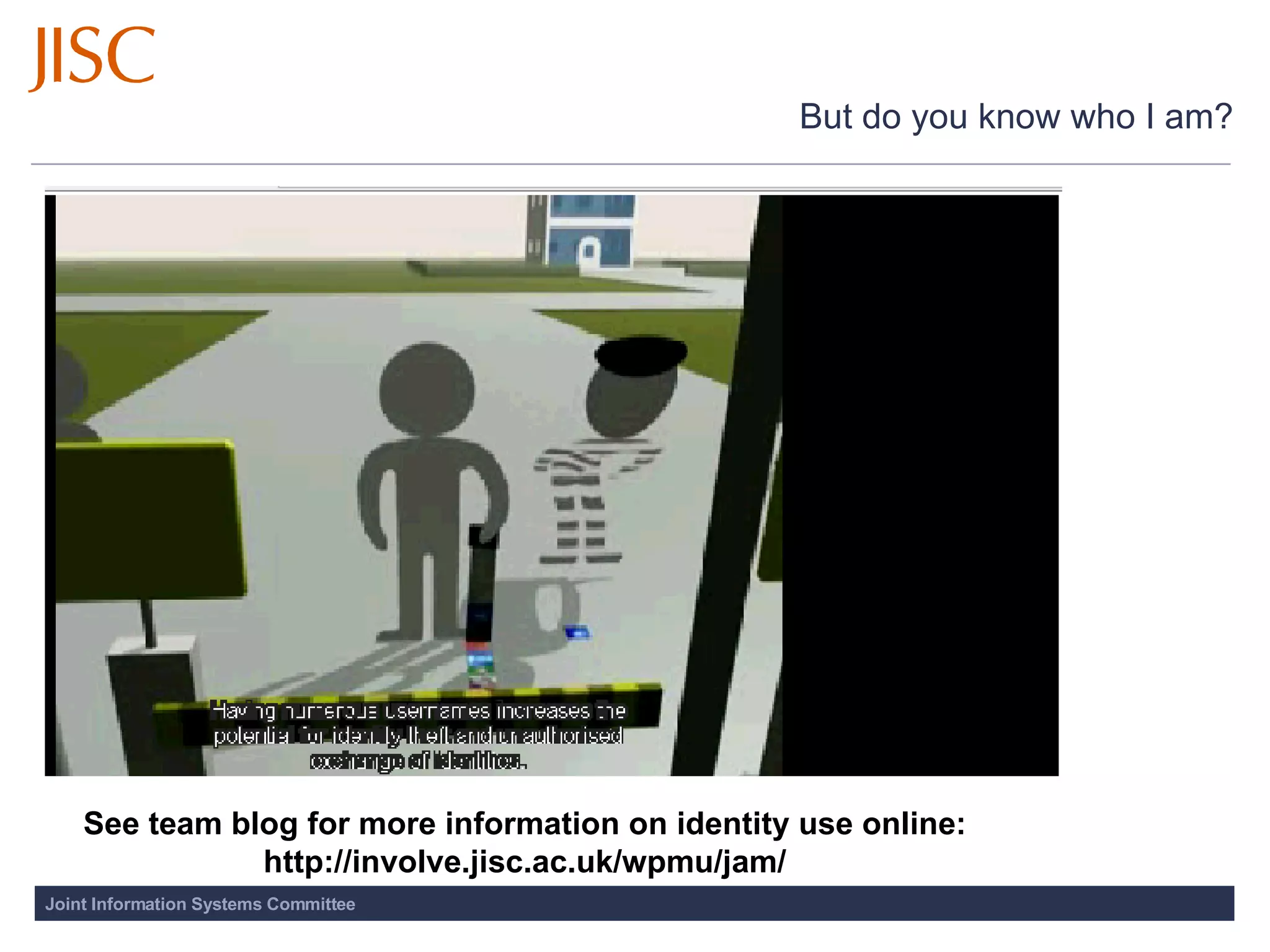
The document discusses the importance of access and identity management for digitization projects. It notes that digitization can democratize access to cultural works, safeguard artifacts from destruction, and nurture cultural identity. Effective access and identity management is needed to safely deliver digitized content to users while respecting copyright and managing metadata and user experience. Trusted systems are also important to provide users access to authentic resources through a transparent process.






![JISC Access Management Team: [email_address] www.jisc.ac.uk/federation [email_address]](https://image.slidesharecdn.com/digitisation-access-and-identity-management1500/75/Digitisation-Access-and-Identity-Management-20-2048.jpg)