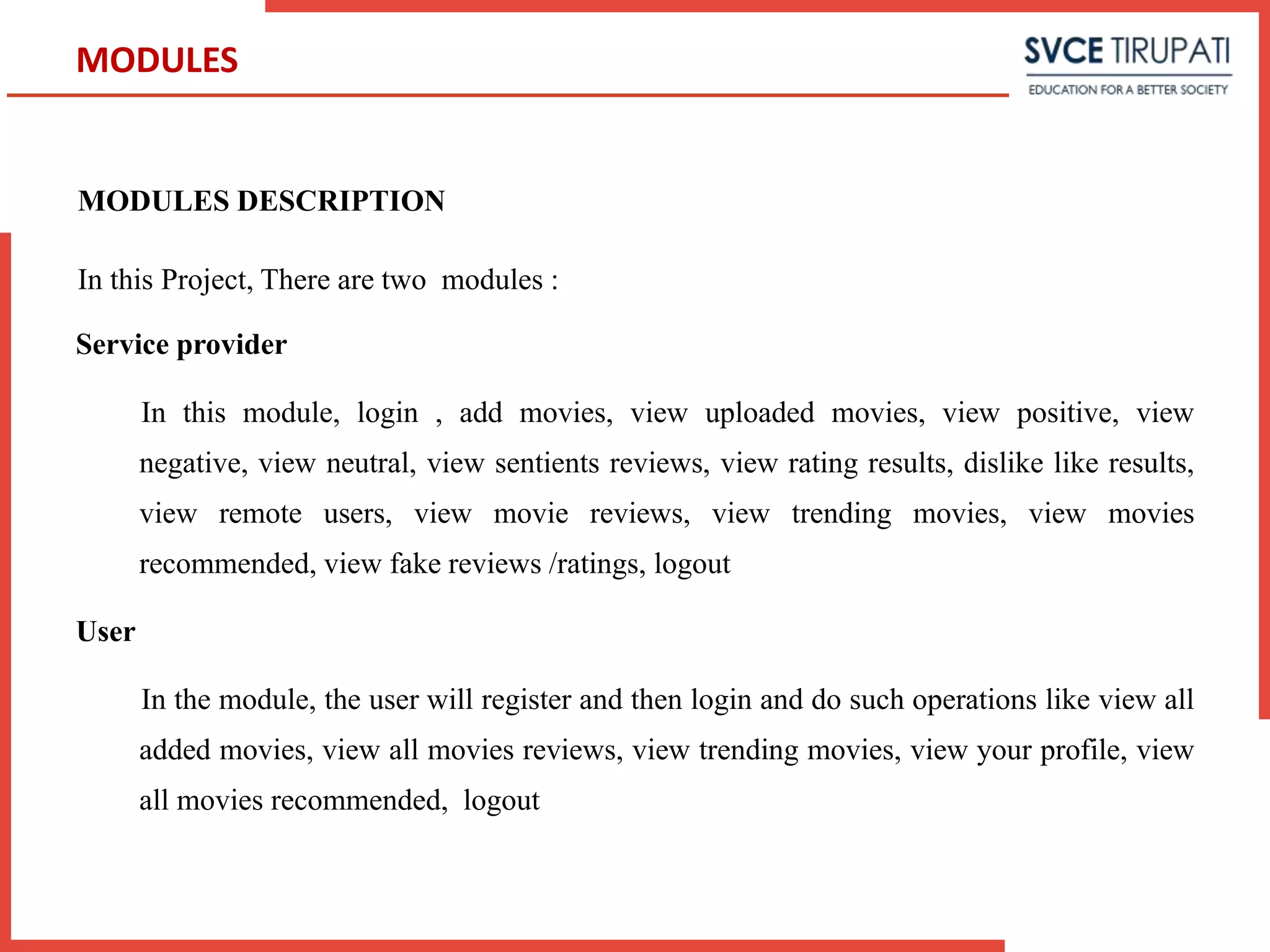
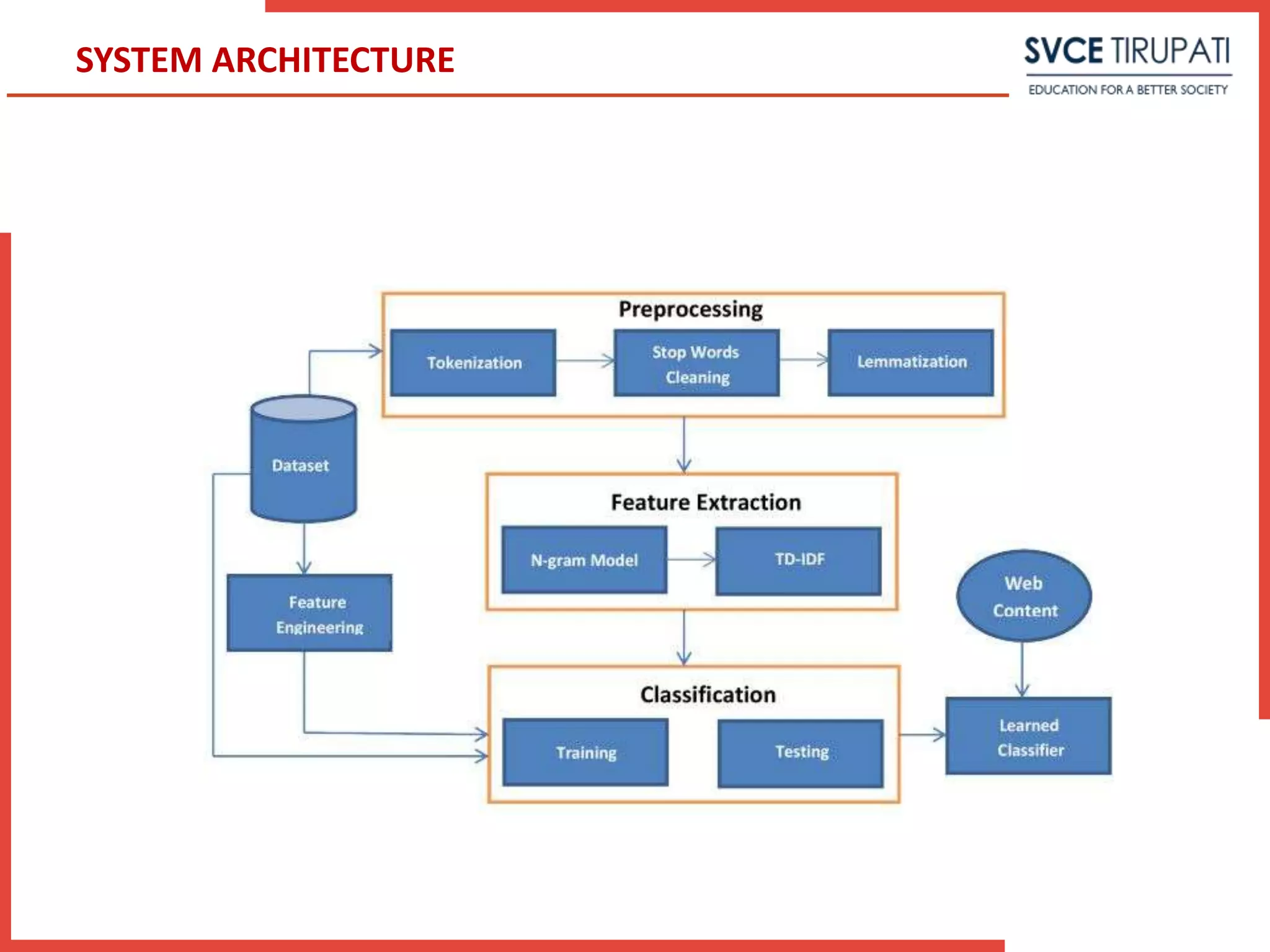
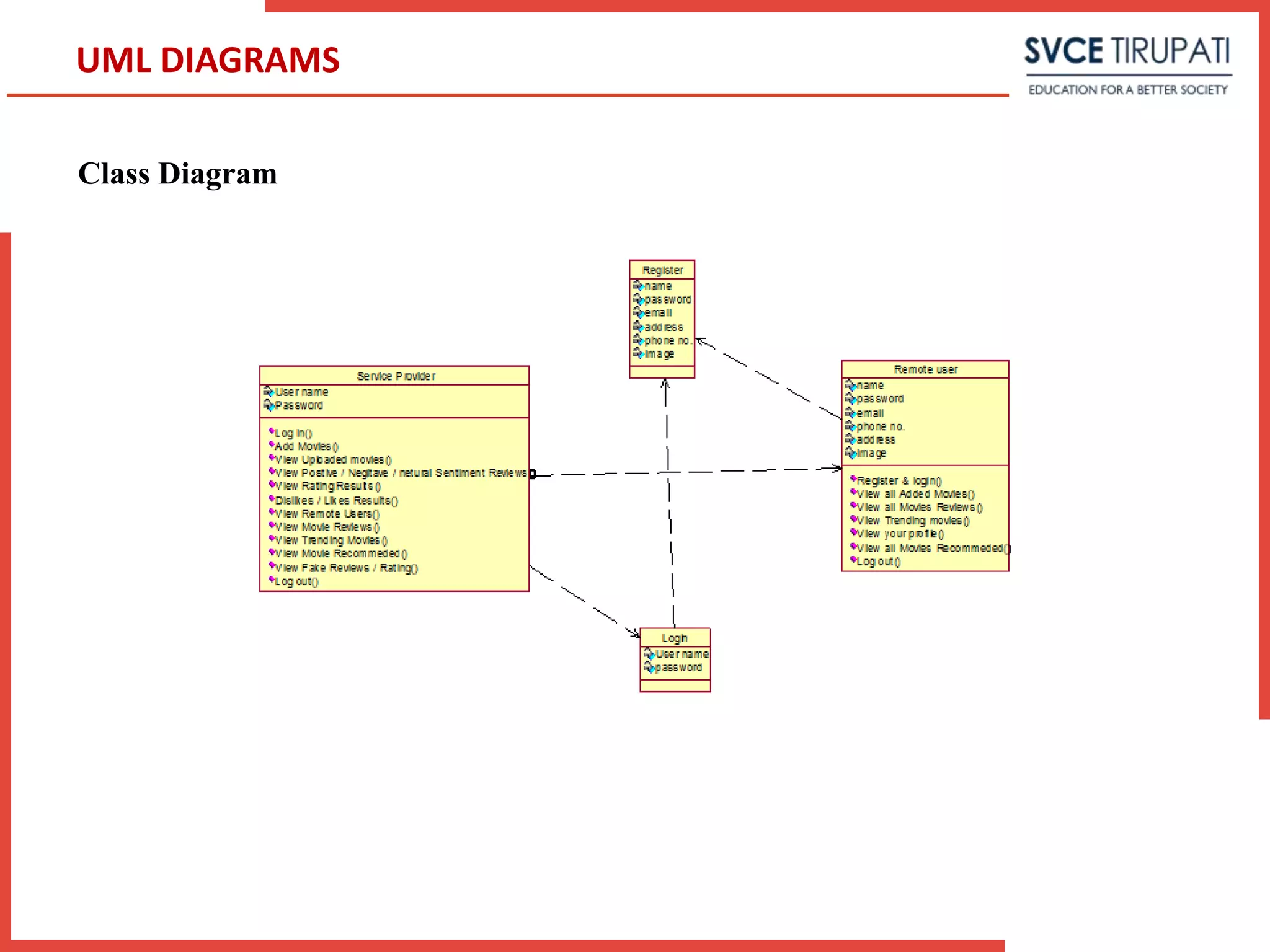
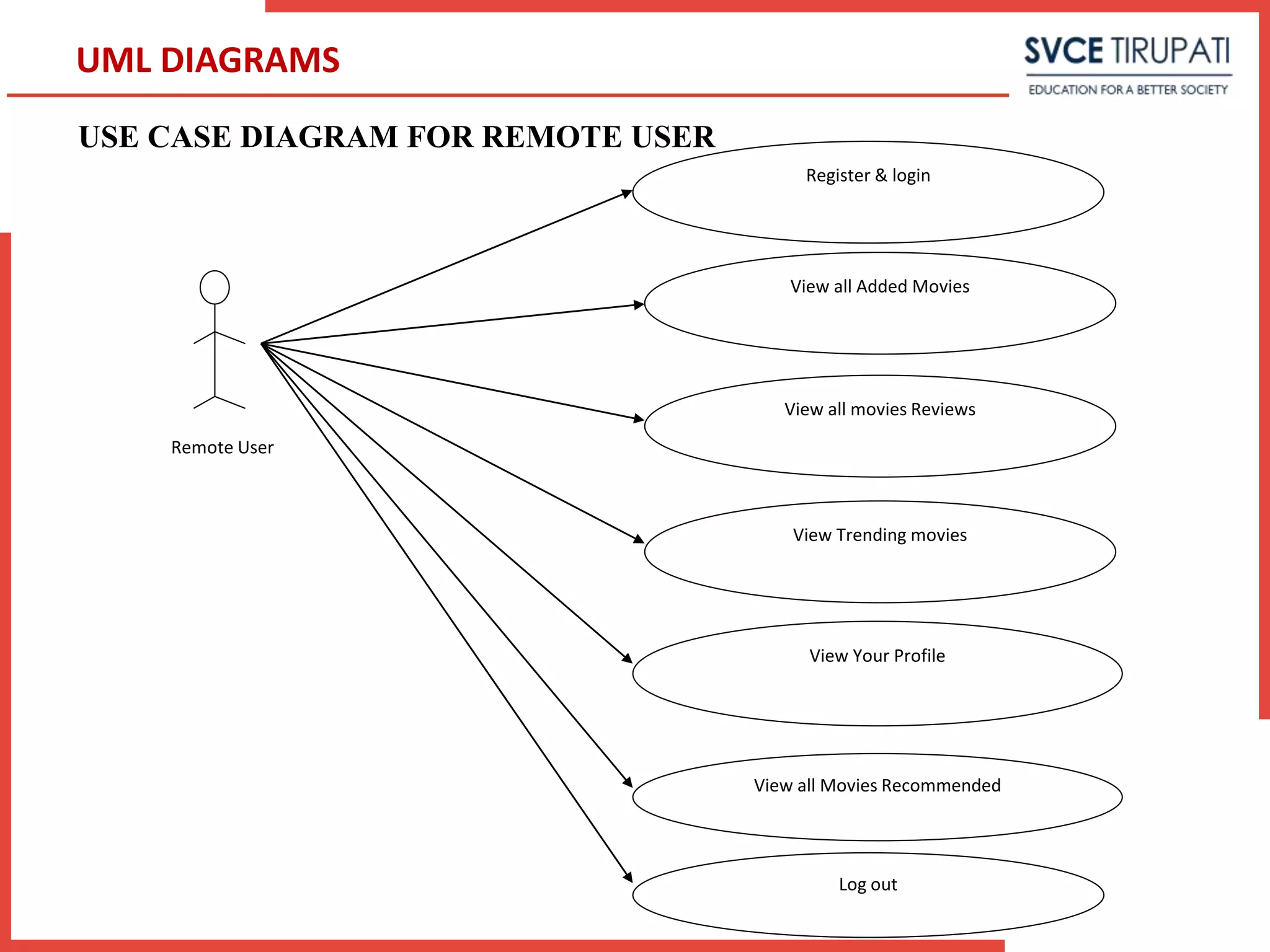
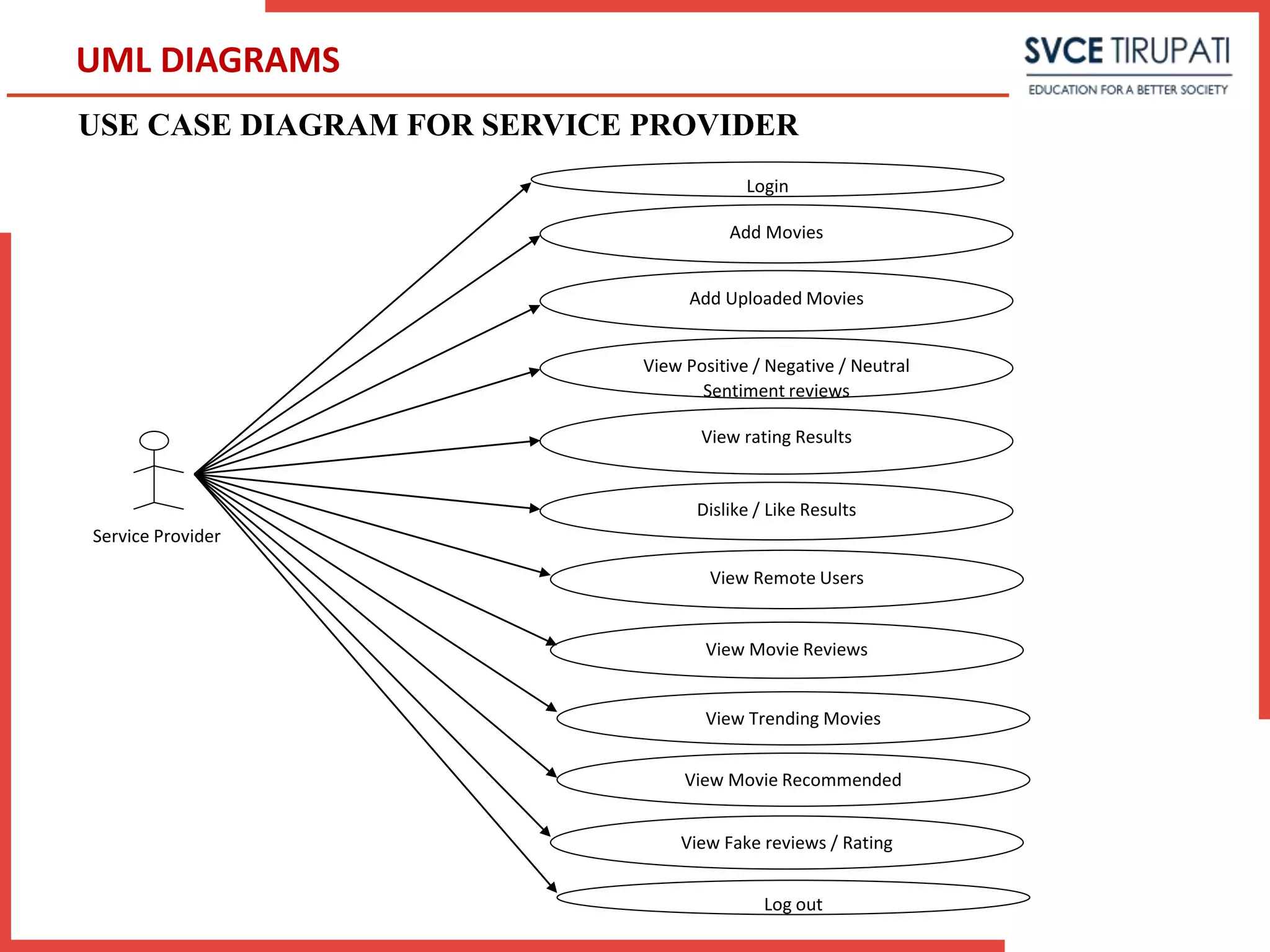
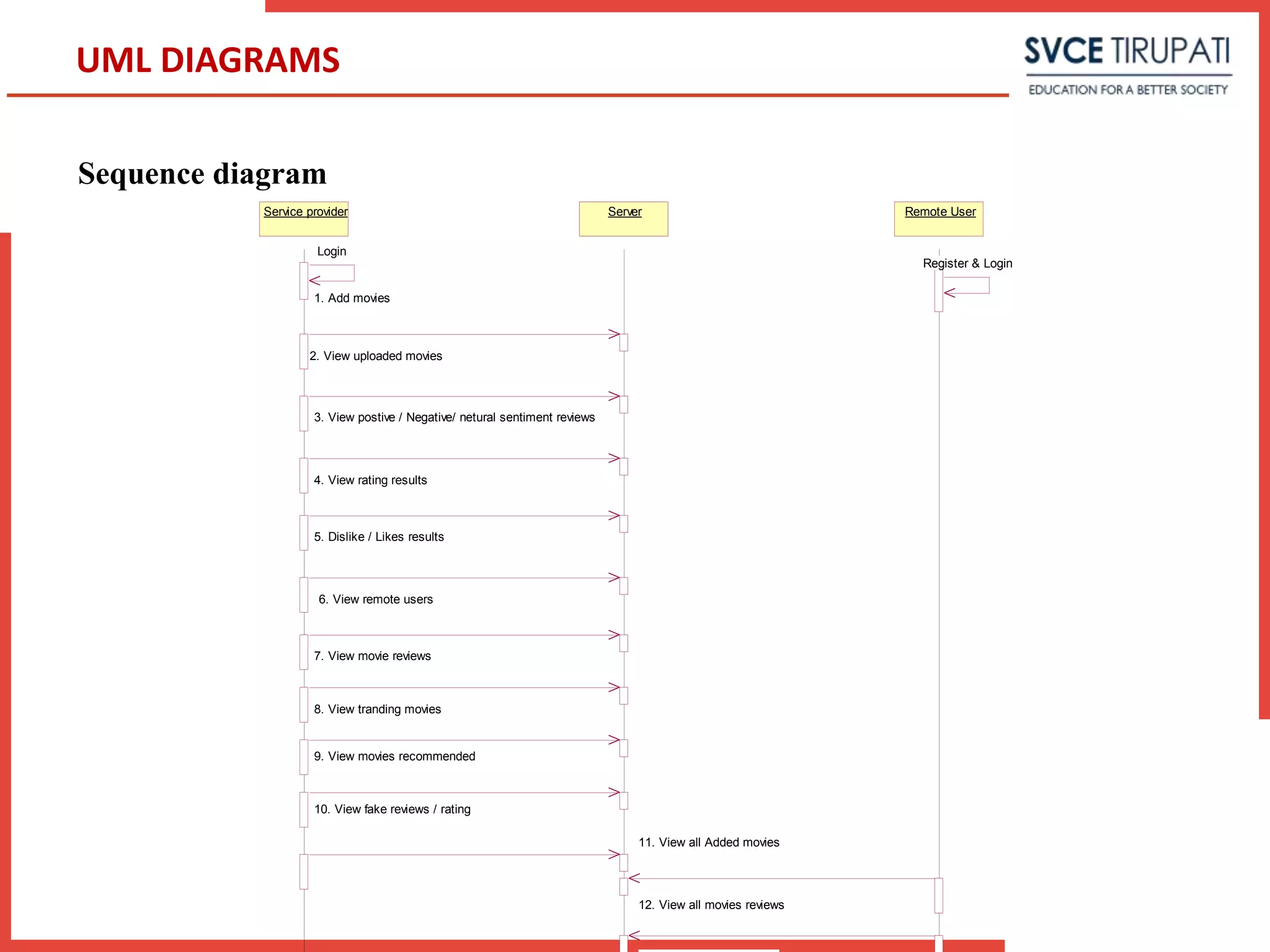
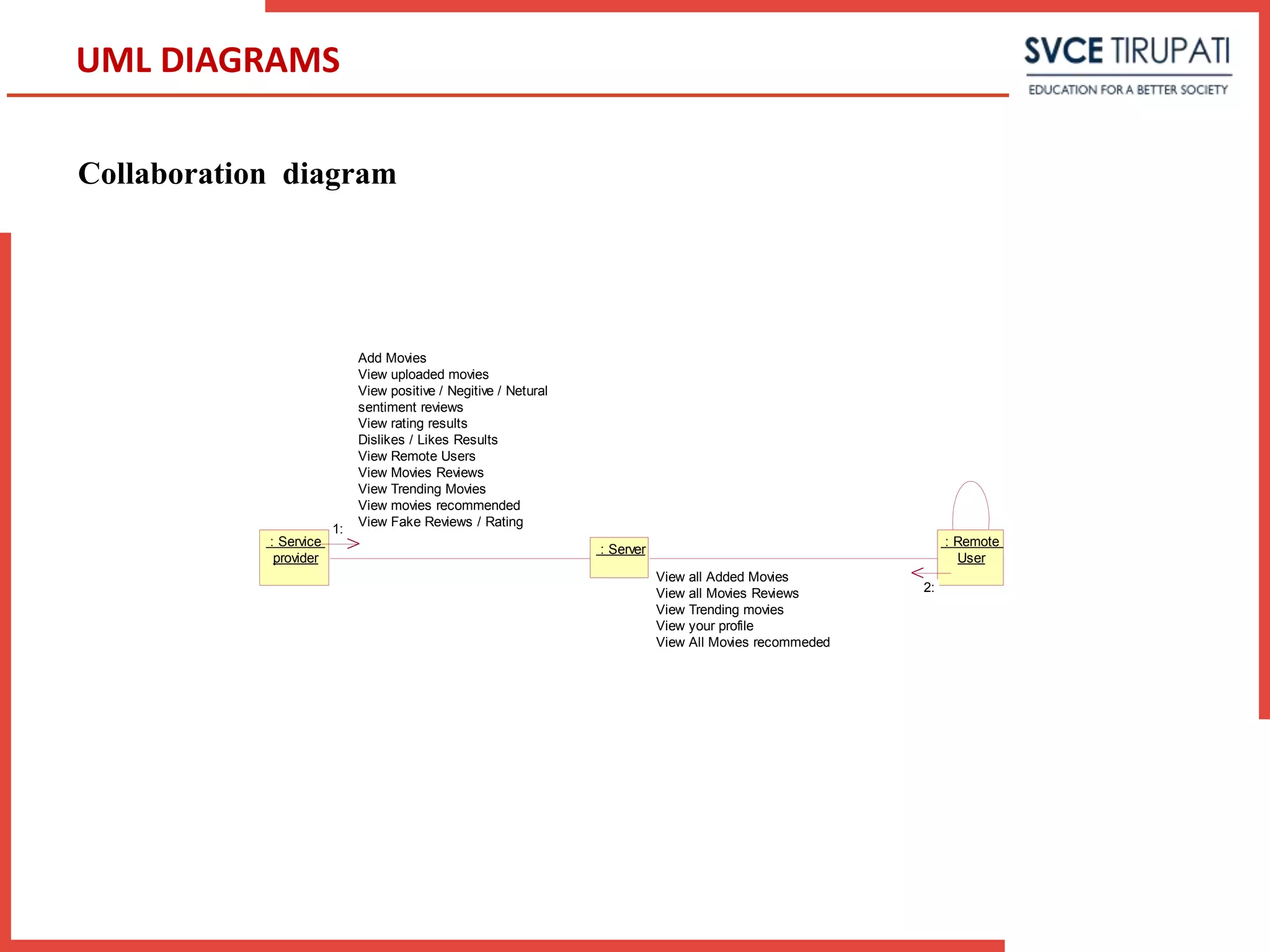
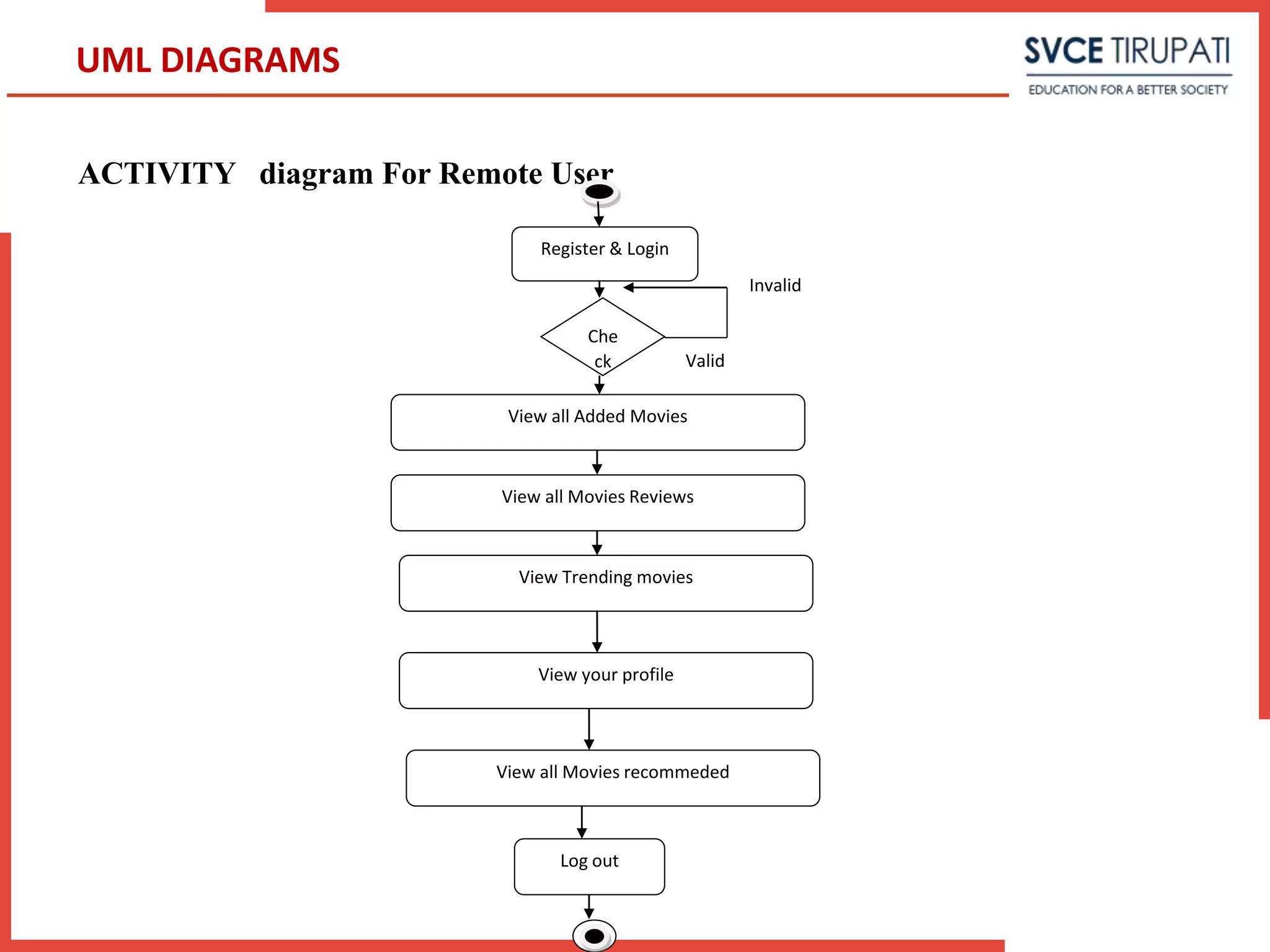
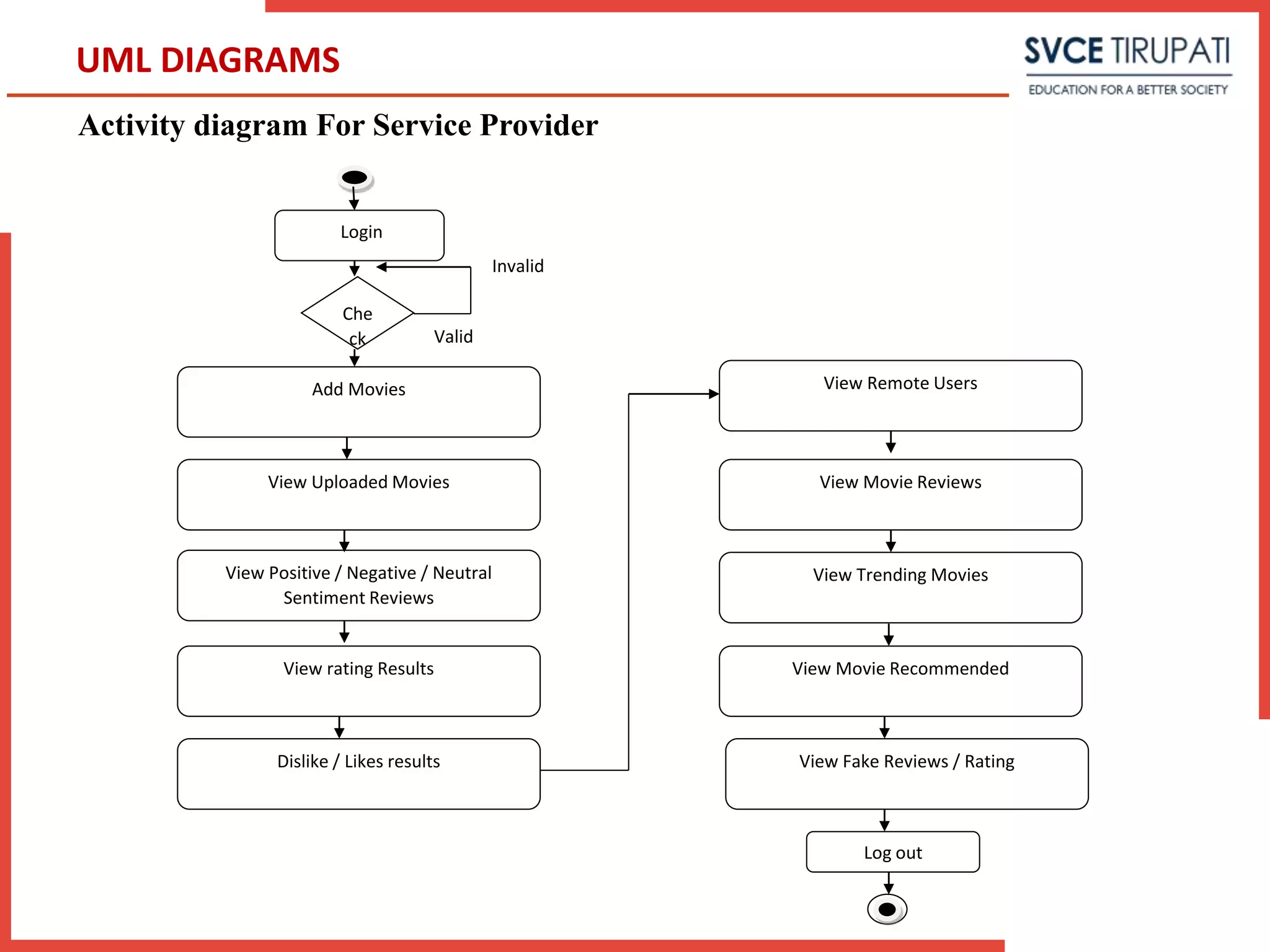
This document presents a project that aims to detect fake online reviews using semi-supervised and supervised learning techniques. It discusses detecting fake reviews as the problem definition. The proposed system generates feature vectors from reviews for classification using algorithms like Naive Bayes. The system has modules for service providers and remote users. UML diagrams like use case diagrams, sequence diagrams and activity diagrams are presented to model the system. Testing strategies like unit testing, integration testing are discussed.