Embed presentation
Download as PDF, PPTX
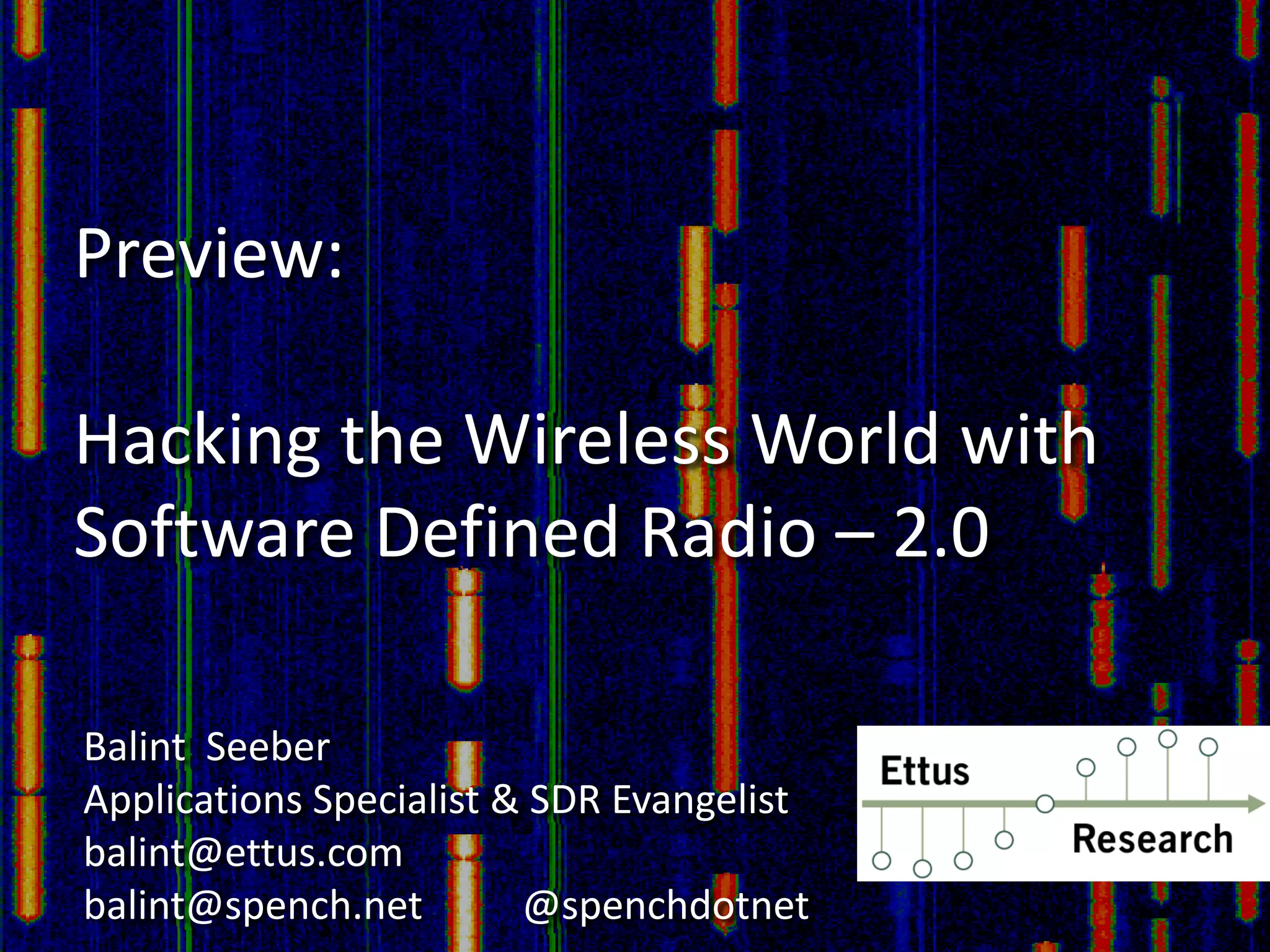



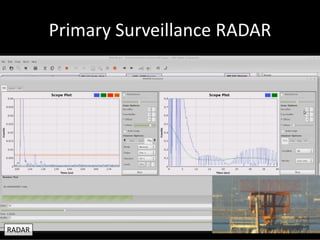



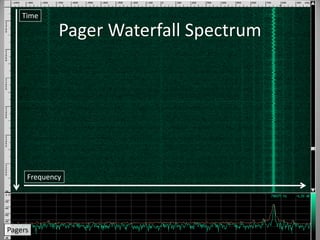
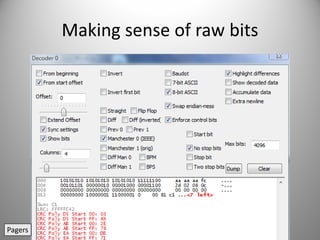
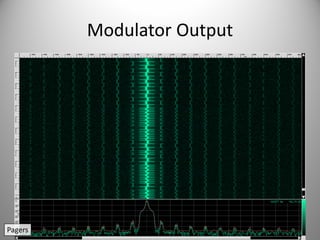
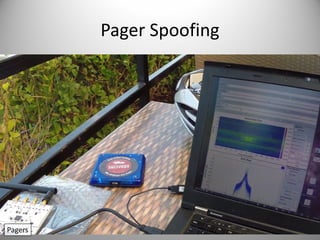
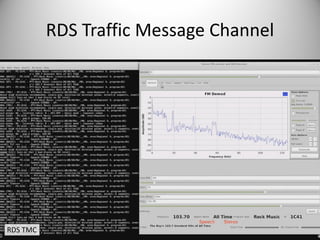
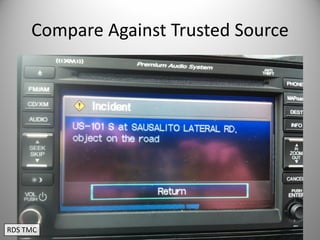
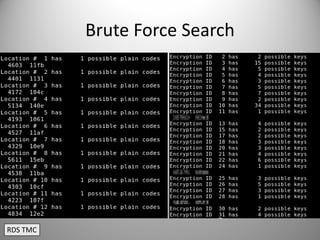

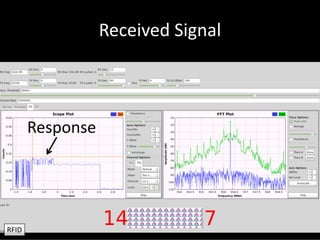


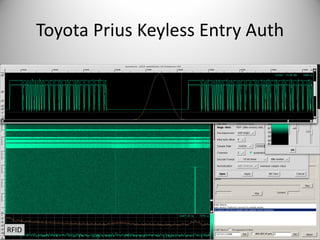
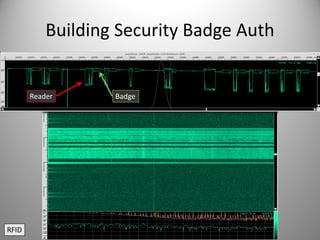



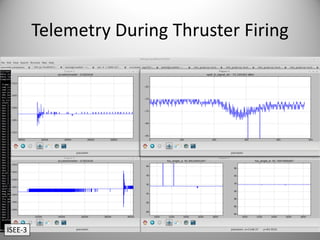


The document discusses the capabilities of software-defined radio (SDR) in various applications, including aviation radar and RFID systems. It highlights the use of SDR hardware, like the USRP B210, for intercepting and analyzing signals, as well as specific projects like the ISEE-3 spacecraft. The content also touches on topics like pager communication, RDS traffic message channel, and the reboot of the ISEE-3 project.

























