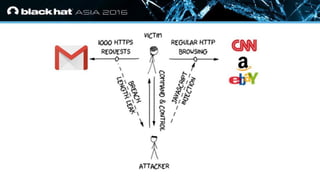
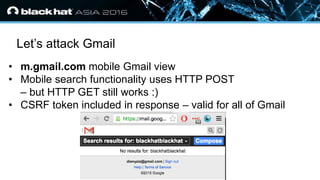
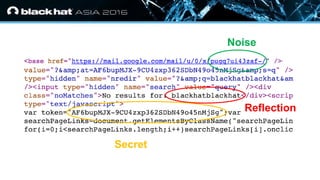
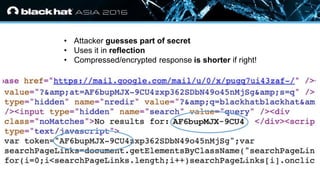
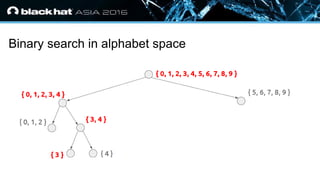
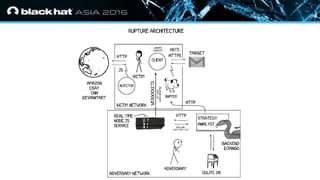
The document discusses the vulnerabilities associated with HTTPS and GZIP compression, exemplified through a modern breach attack that exposes these weaknesses despite upgrades to AES encryption. It introduces an open-source tool called 'Rupture' that aids in executing such attacks, offering improved methodologies for targeting noisy endpoints and block ciphers. Key recommendations include enabling first-party cookies to mitigate these vulnerabilities, highlighting the need for awareness in web security.