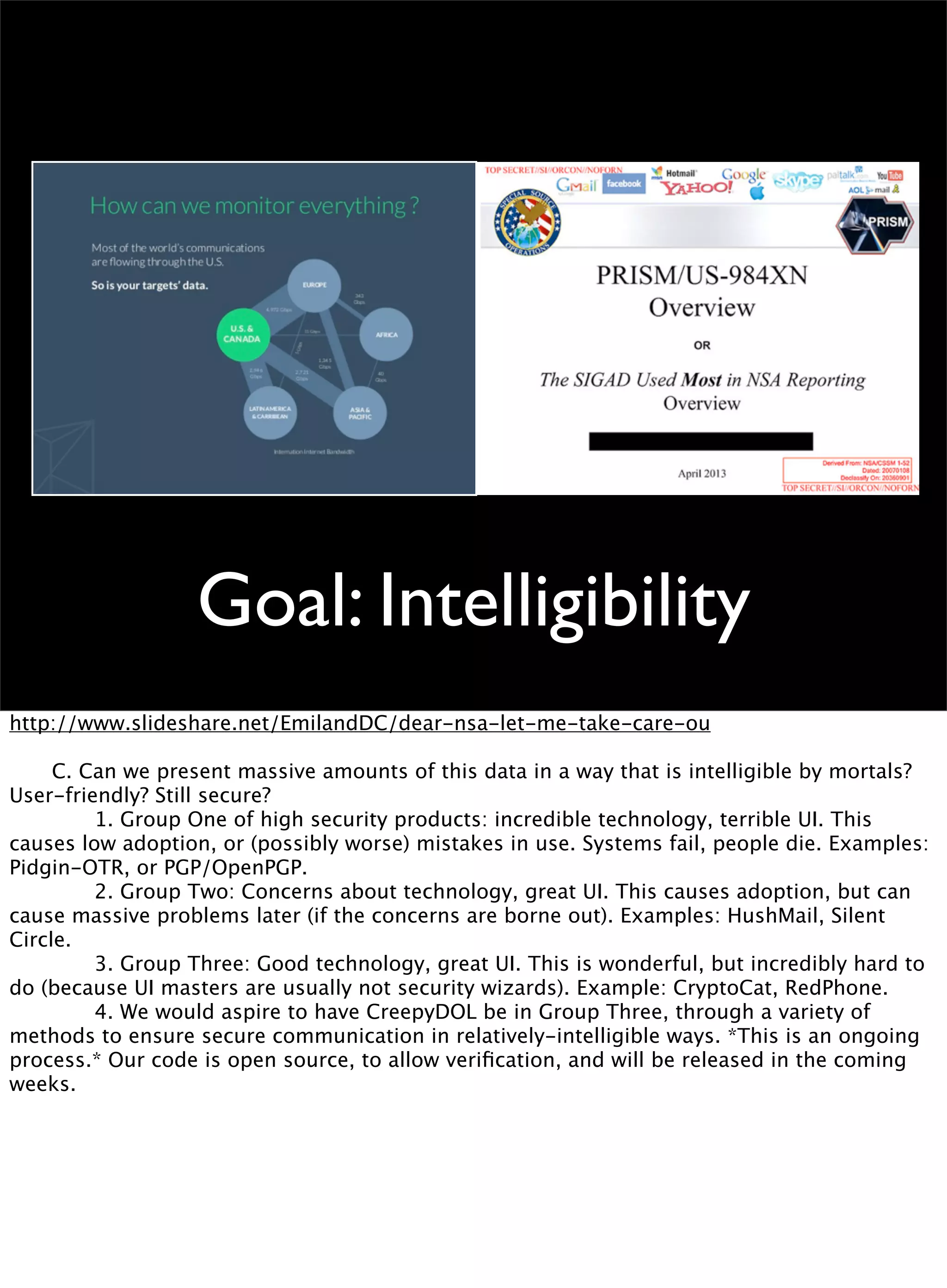
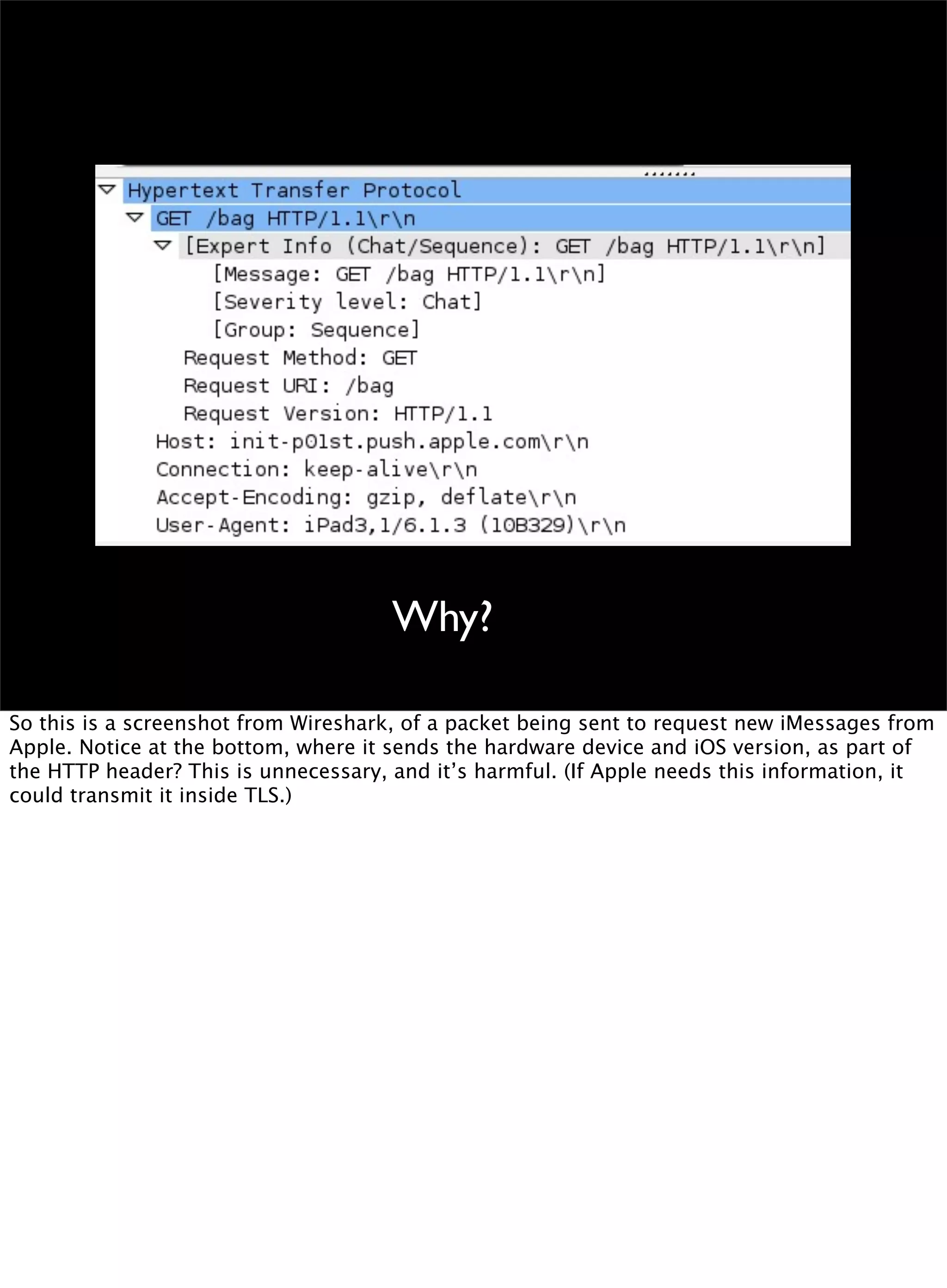
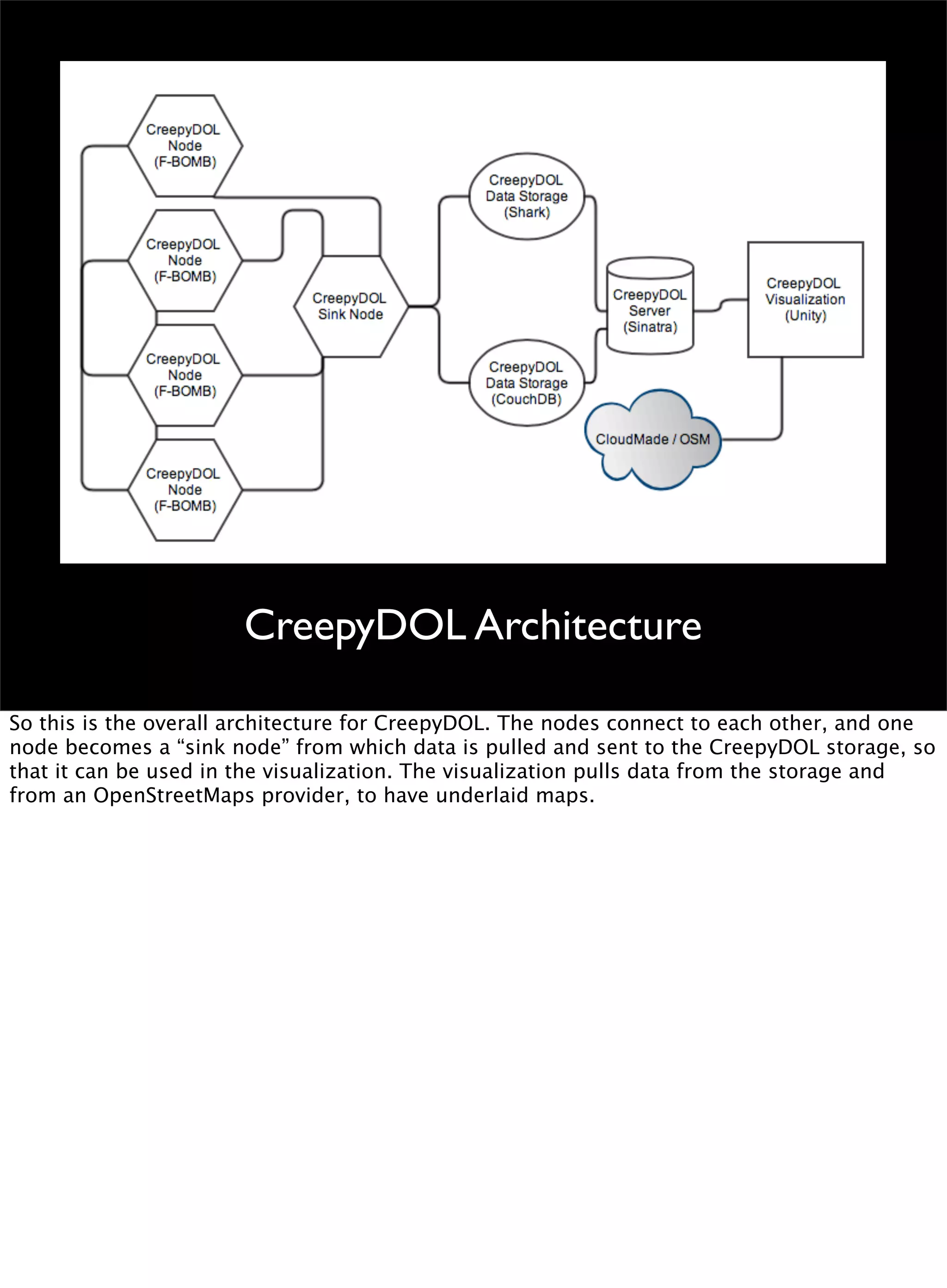
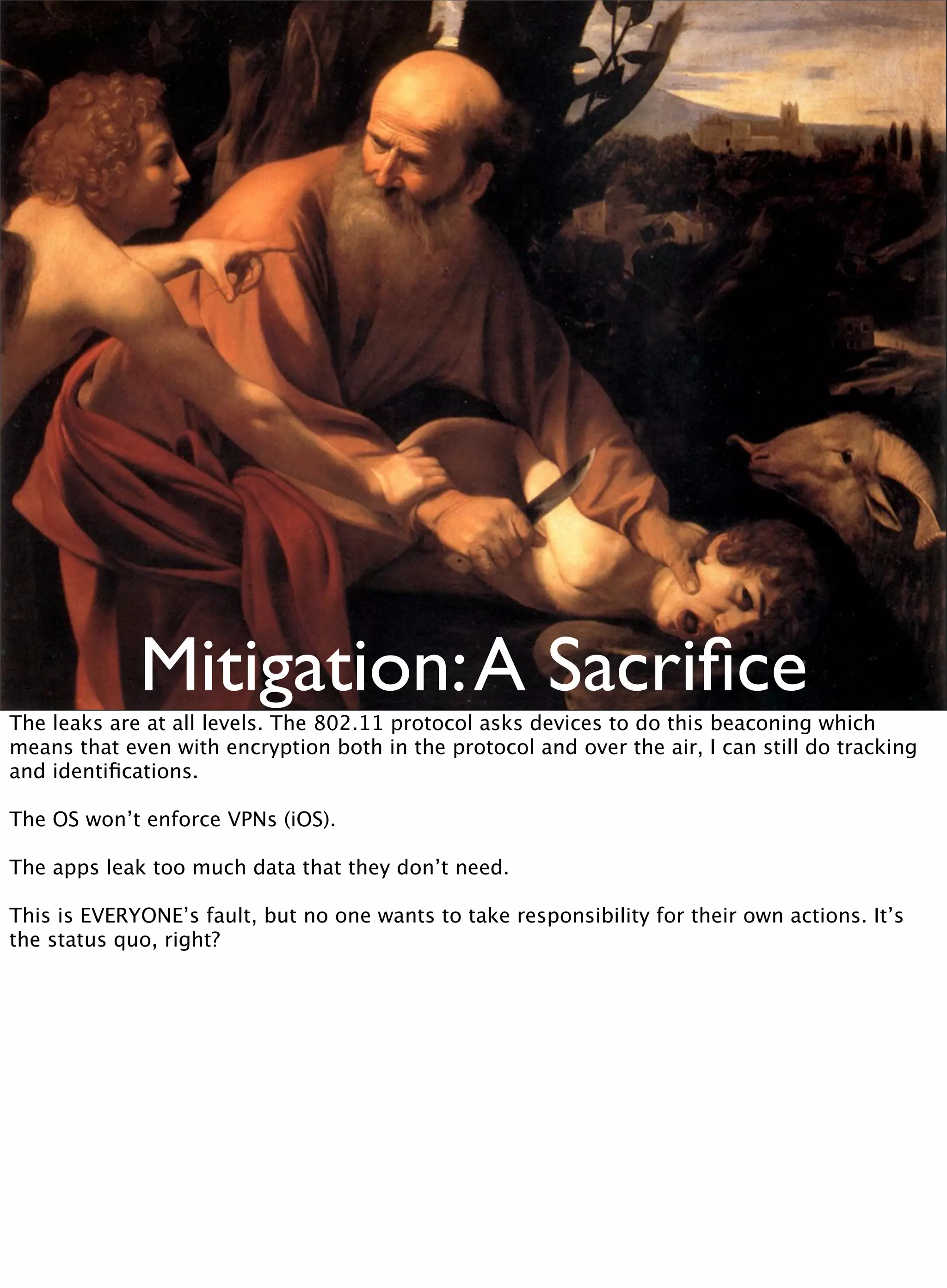
This document discusses the development of a distributed sensor network called CreepyDOL that could track people in an urban area through passive wireless monitoring and analysis of leaked data from devices. The goal is to demonstrate how much information can be extracted without consent and to shape technology development to better protect privacy. CreepyDOL would use inexpensive hardware like Raspberry Pi boards placed in common objects to passively monitor WiFi traffic and device behaviors. While not actually deploying a full surveillance system, the author aims to educate about privacy risks and push for technical and cultural changes to limit unwarranted data collection and transmission. Concerns are also raised about government overreach in surveillance and prosecution of security researchers.