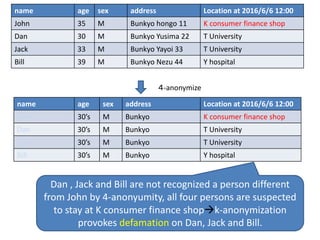
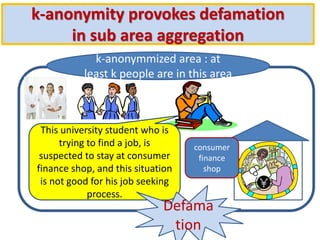
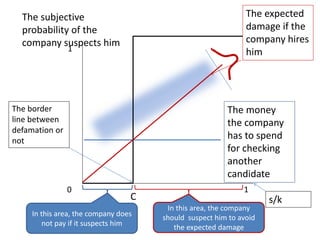
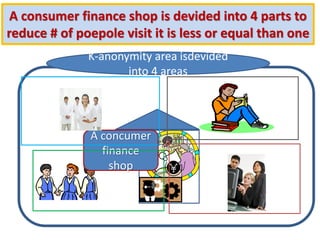
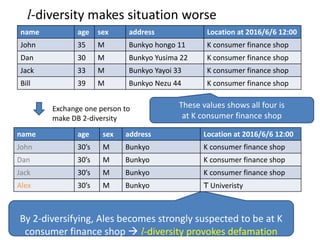
The document discusses the implications of k-anonymization in relation to defamation, particularly how it can harm individuals, such as job candidates, by linking them to negative reputations based on their group associations. It outlines a case study illustrating how a candidate's chances of employment can be affected if he is anonymized in a group containing individuals with undesirable backgrounds. The proposed solution is to improve k-anonymization algorithms to minimize the presence of undesirable individuals in groups while balancing the accuracy of the anonymized data.