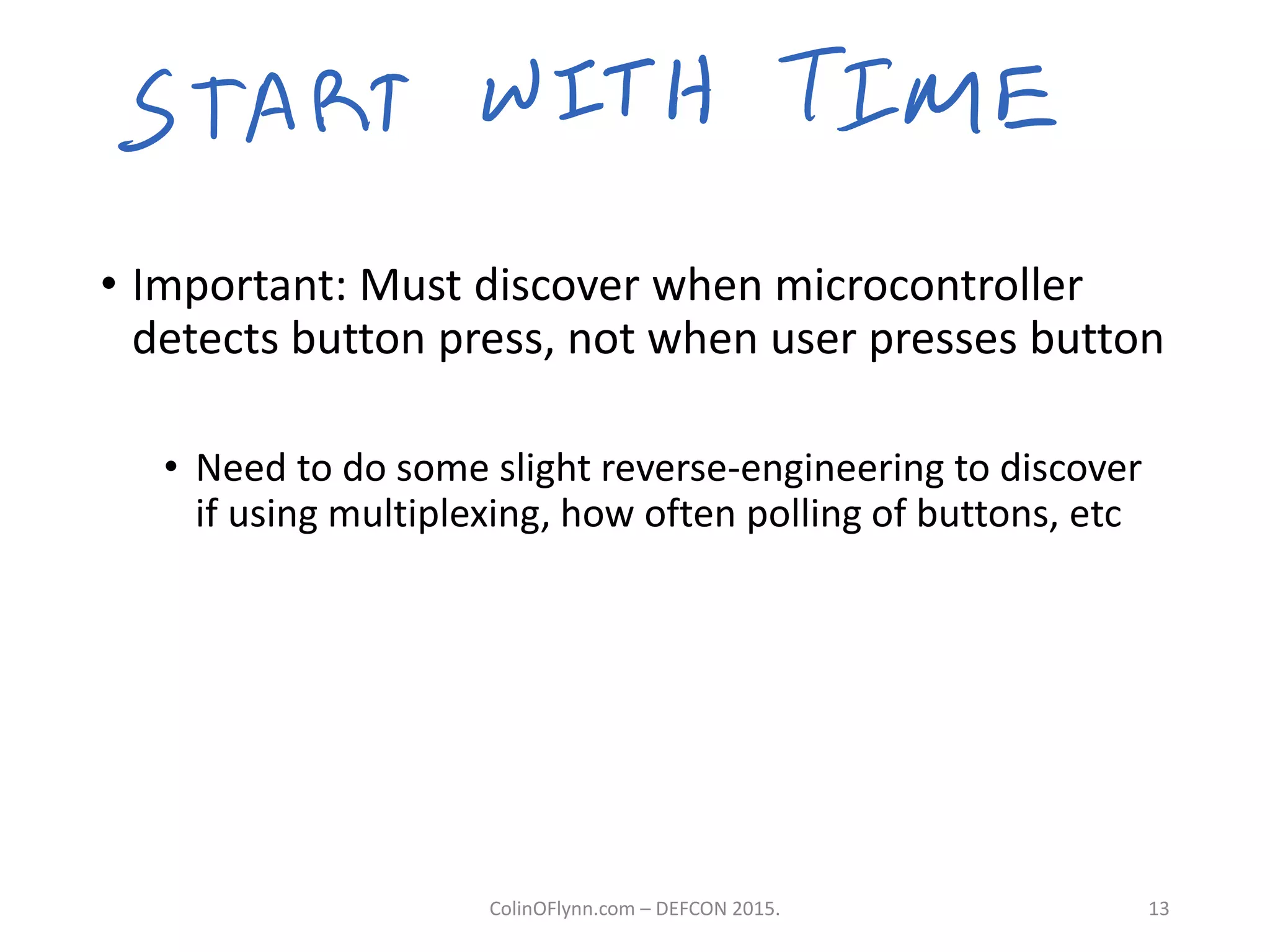
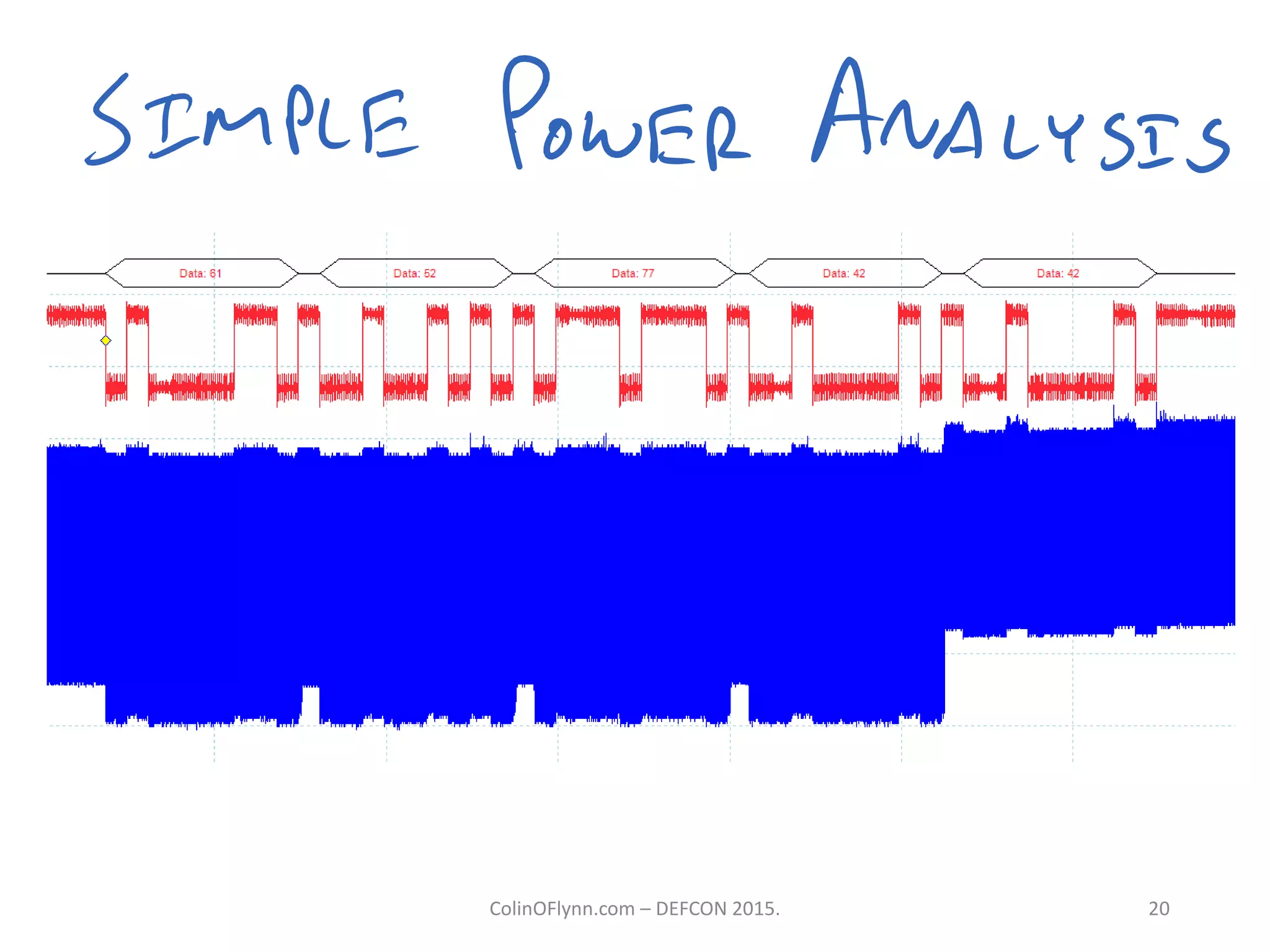
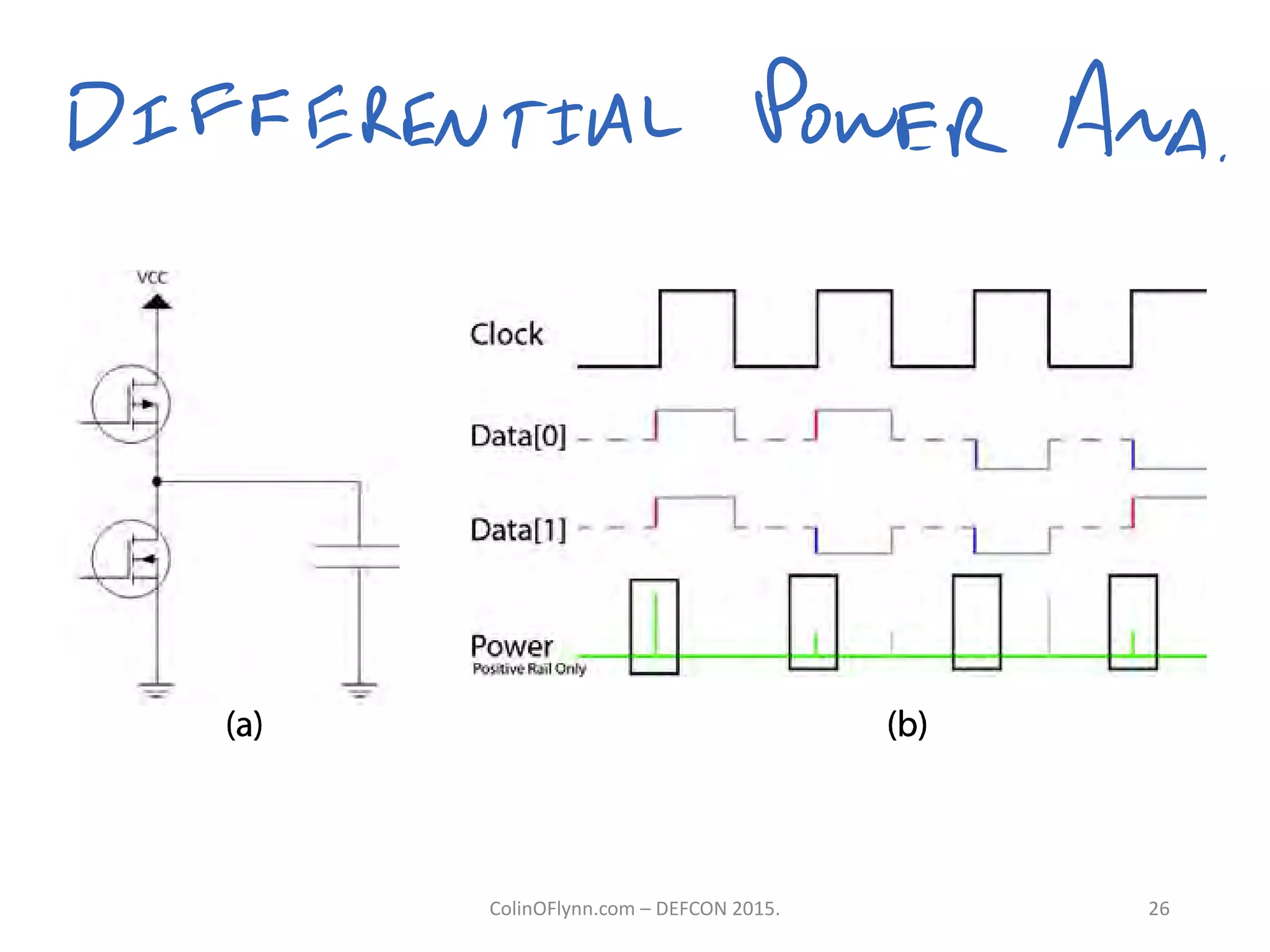
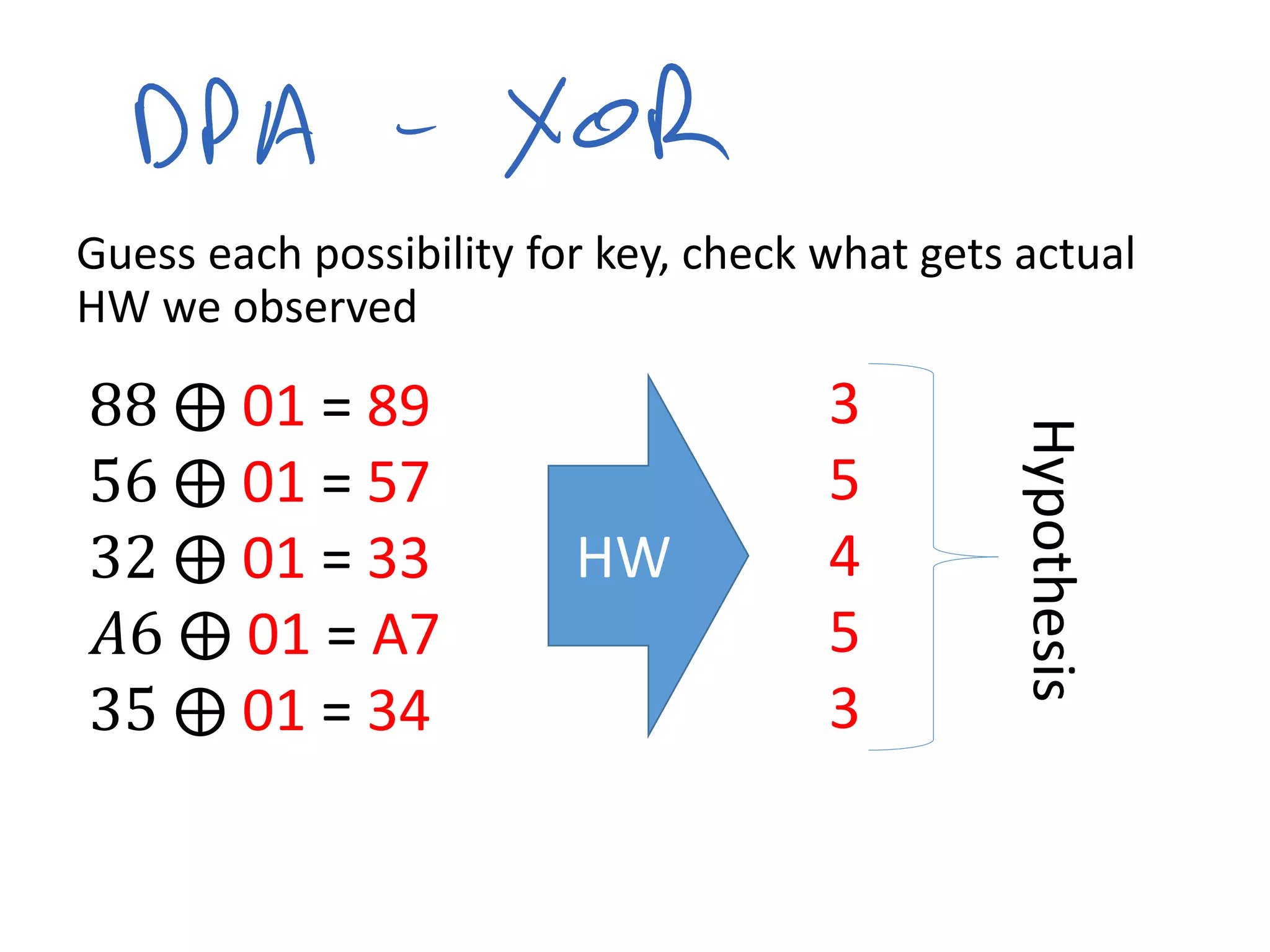
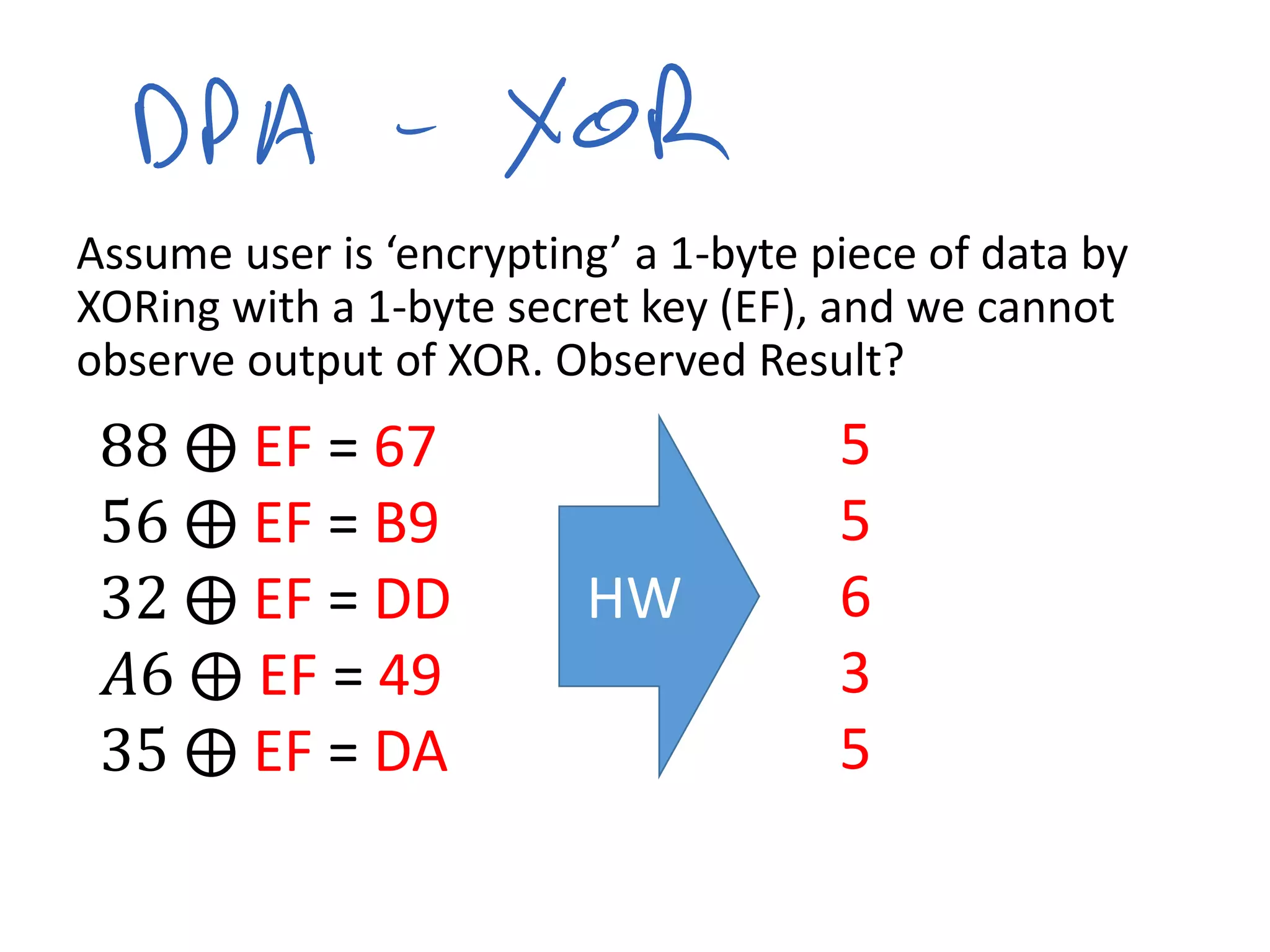
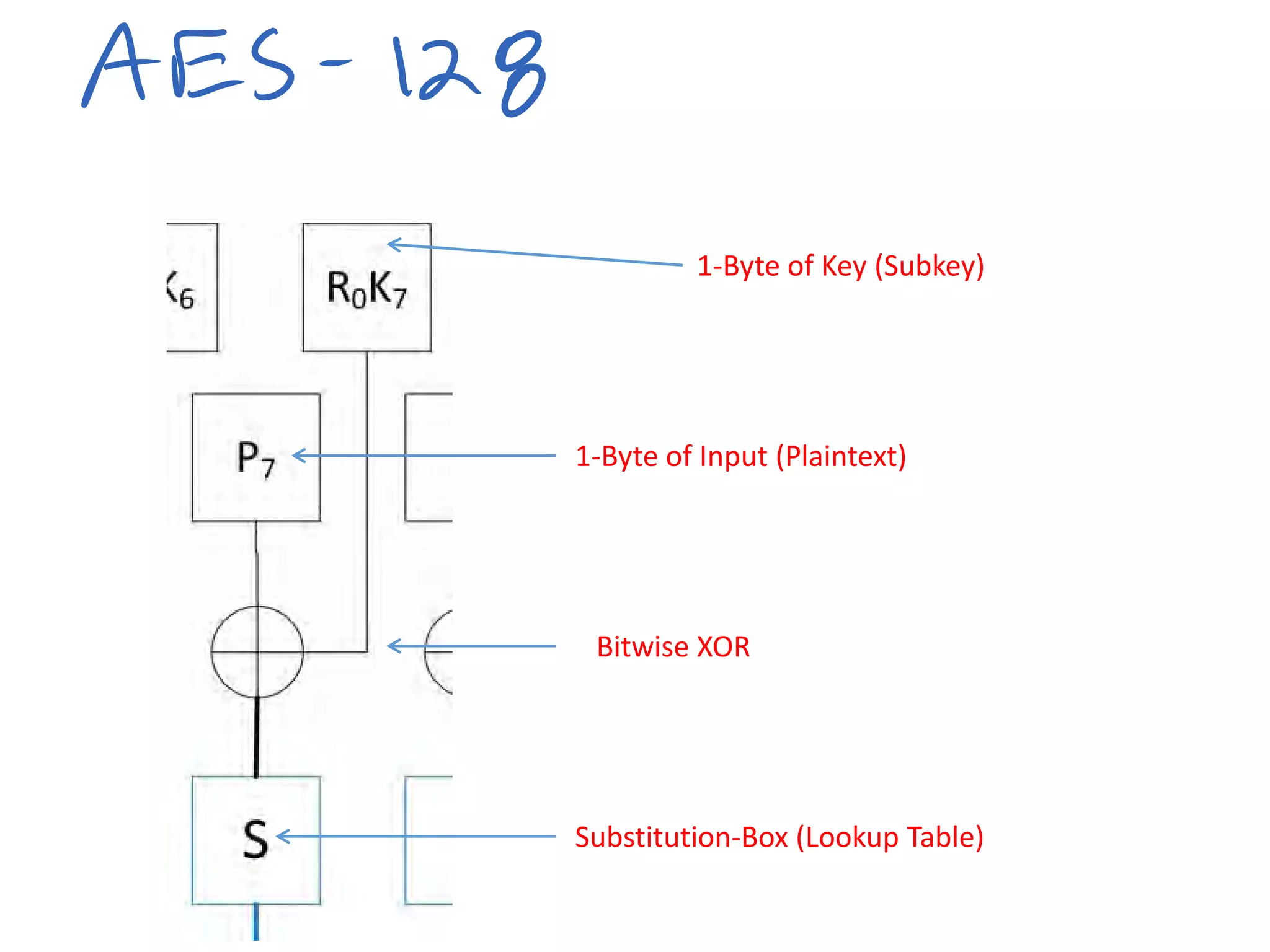
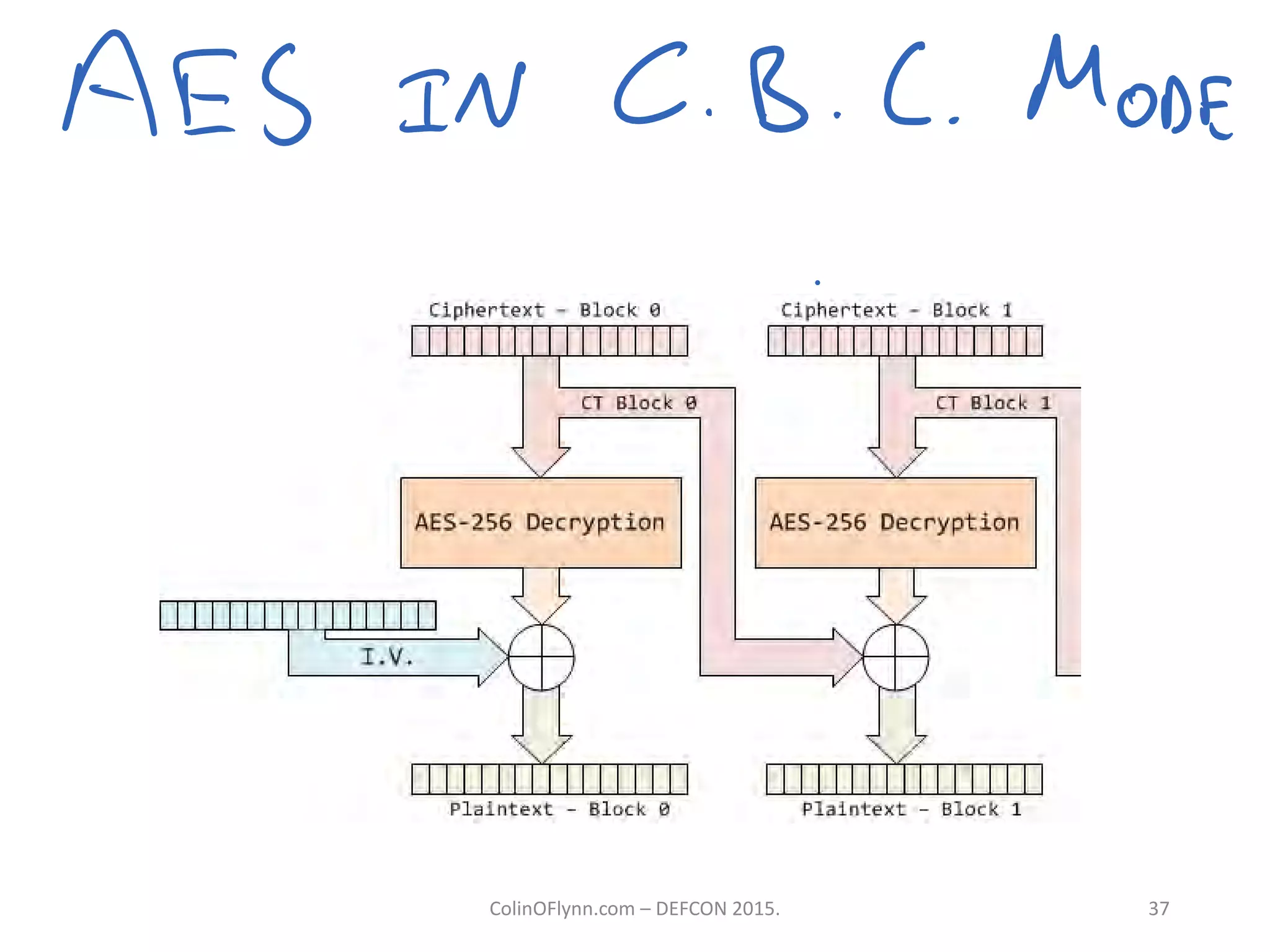
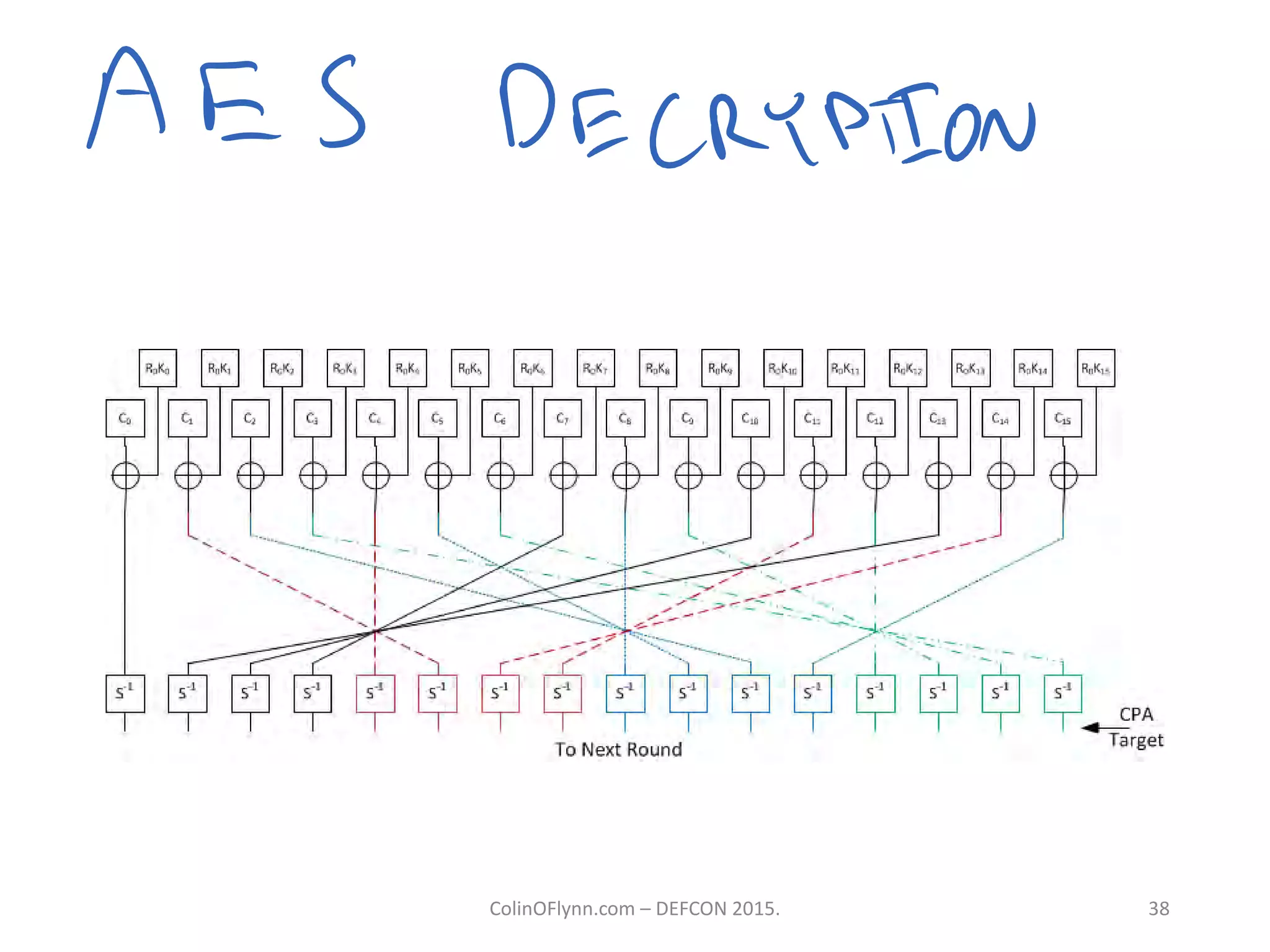
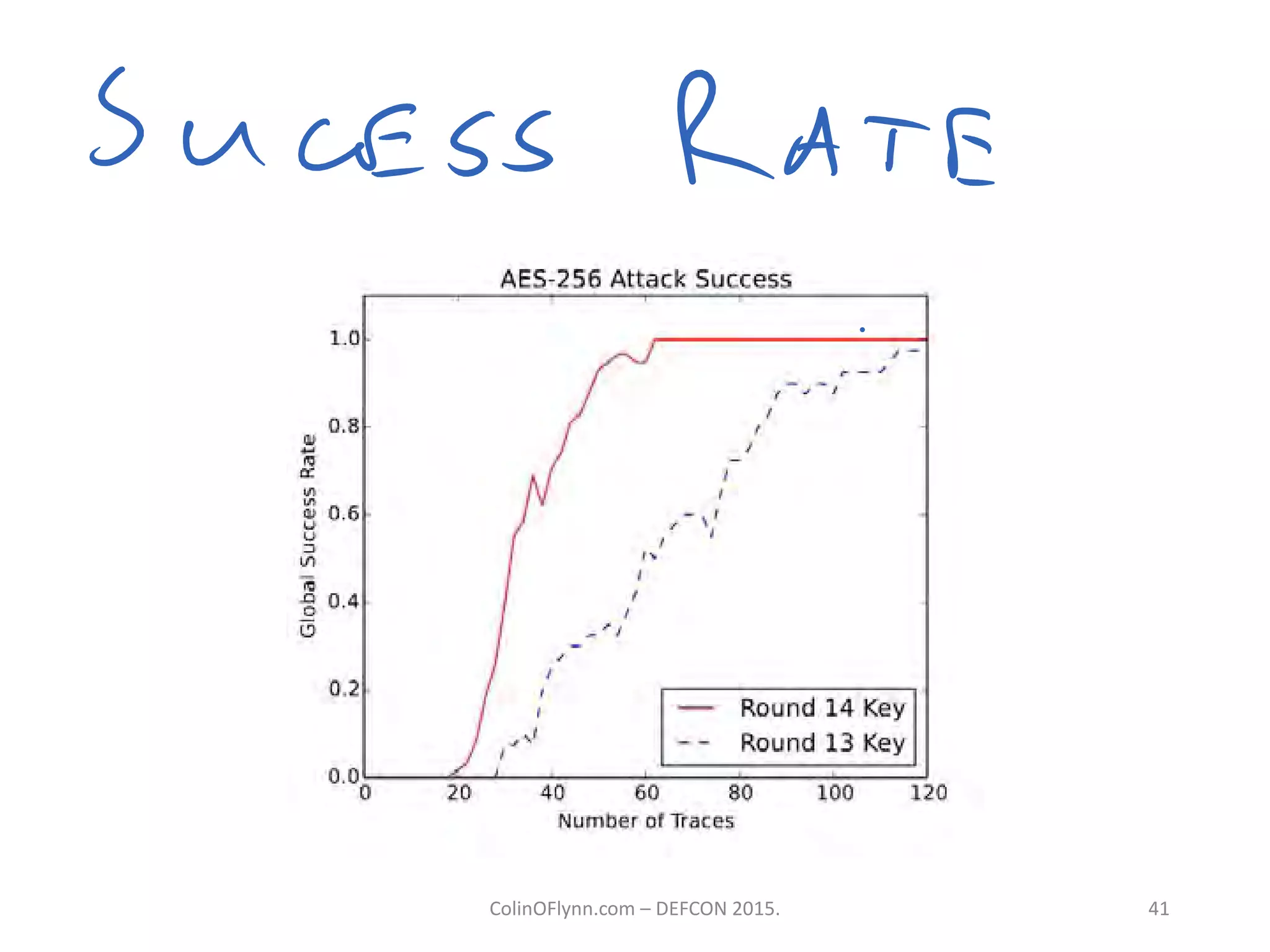
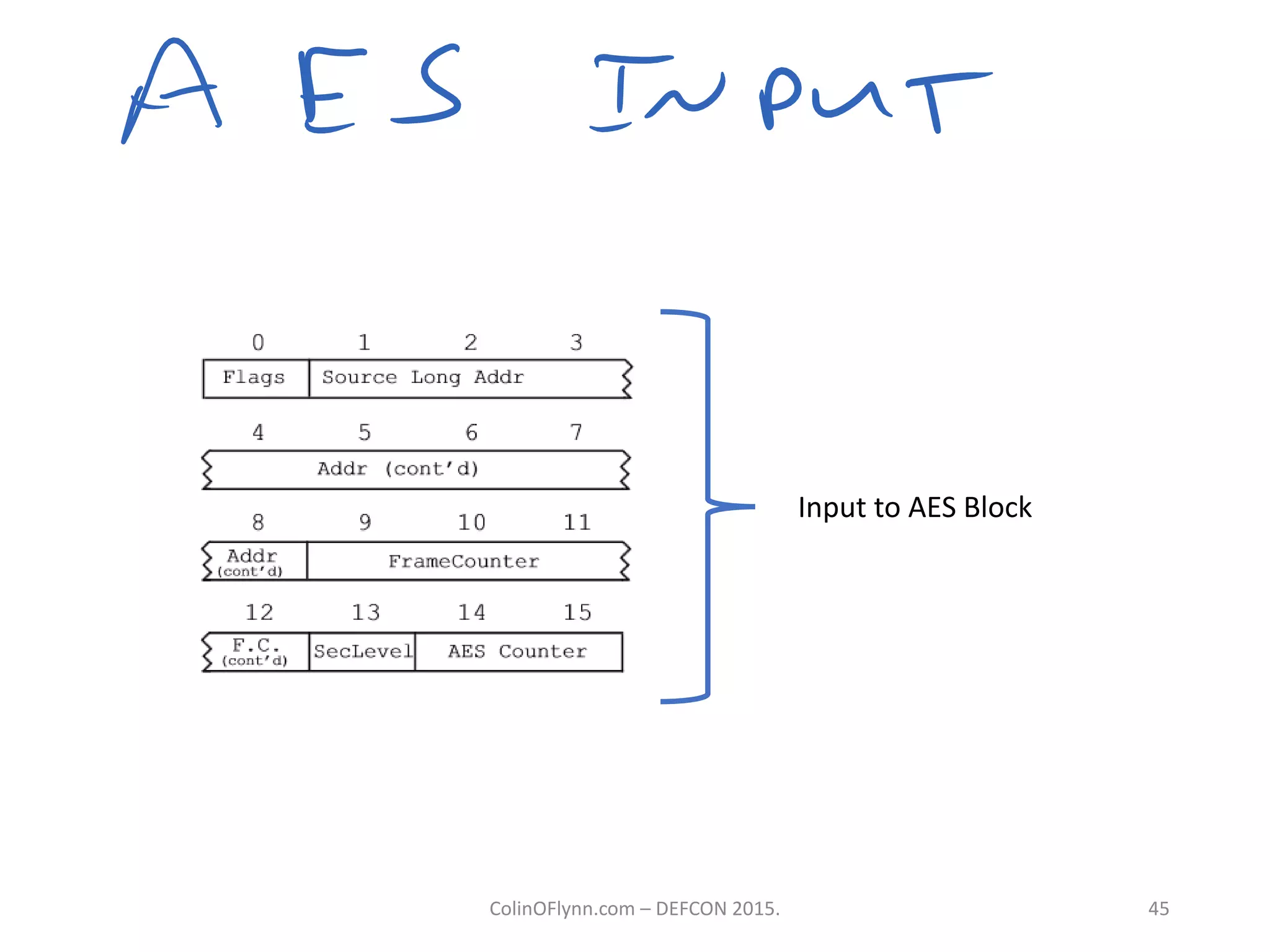
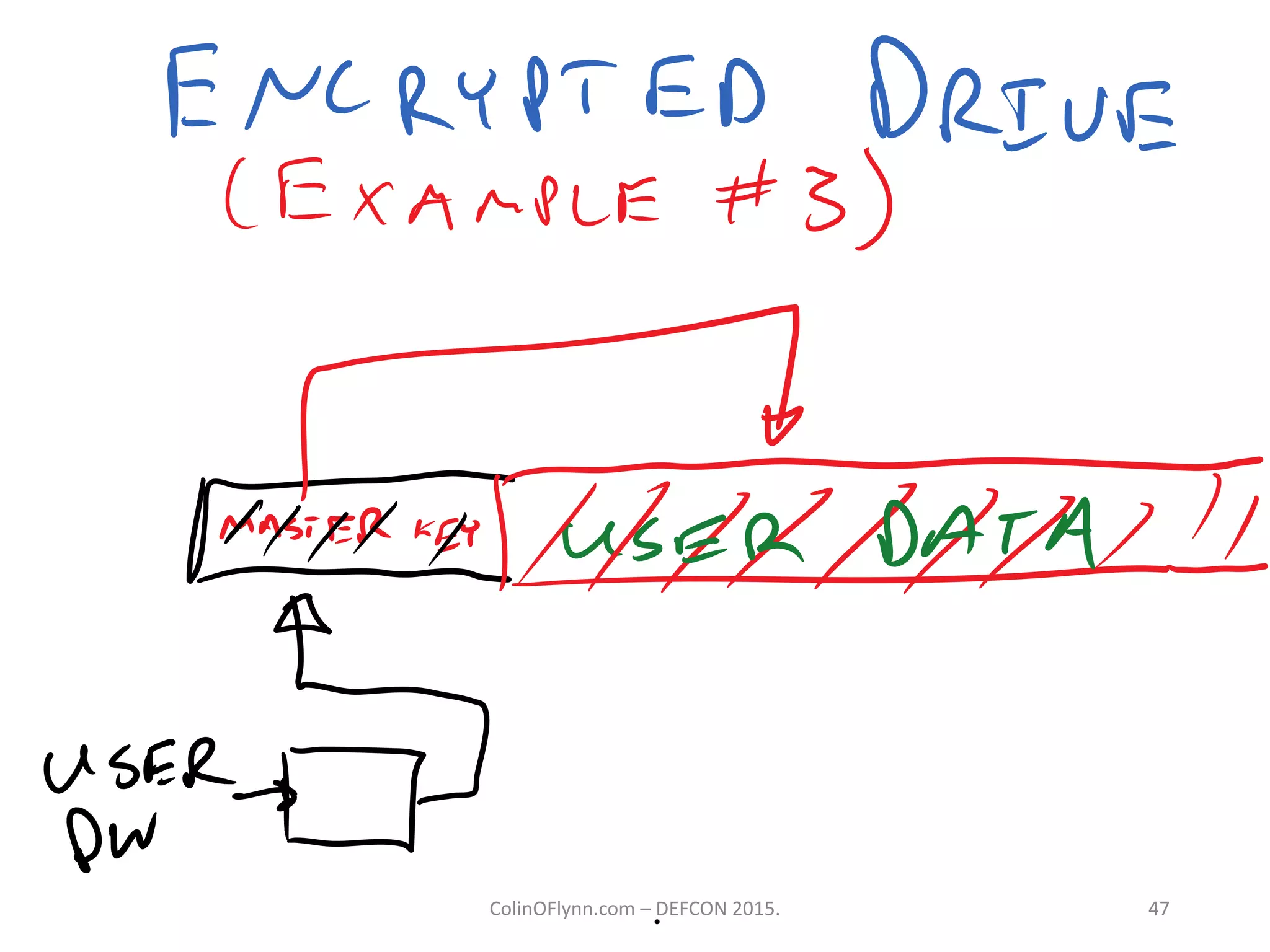
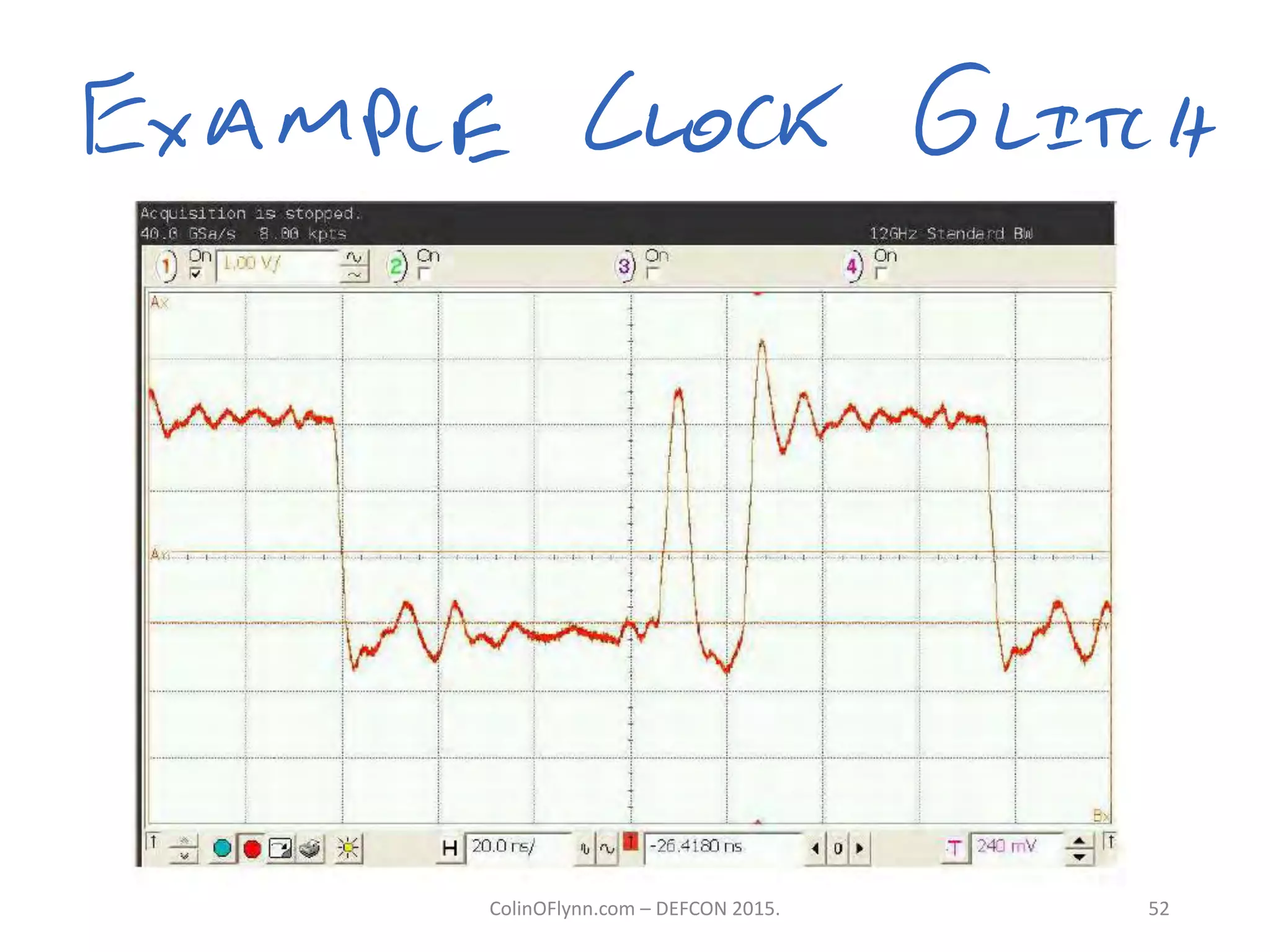
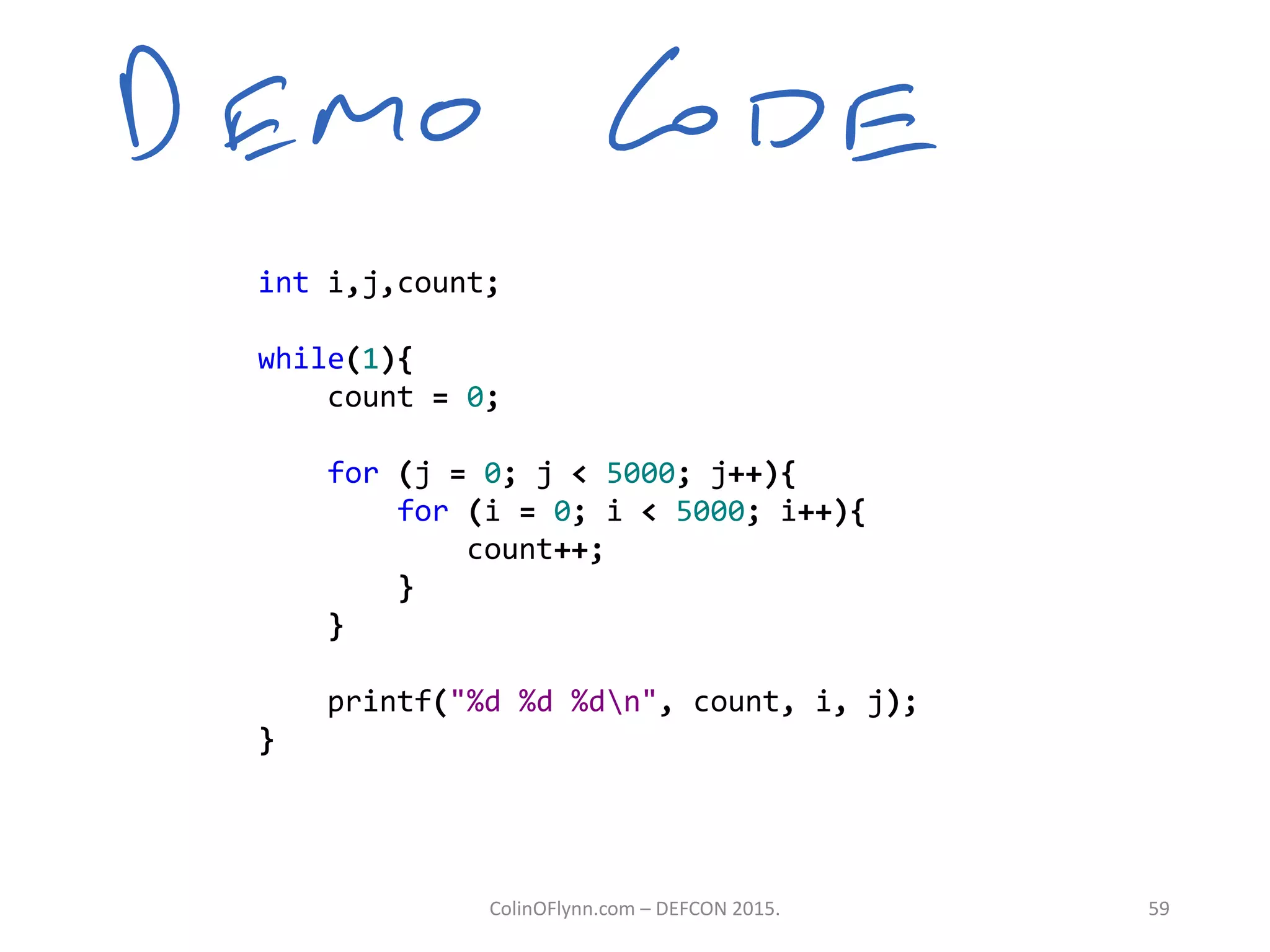
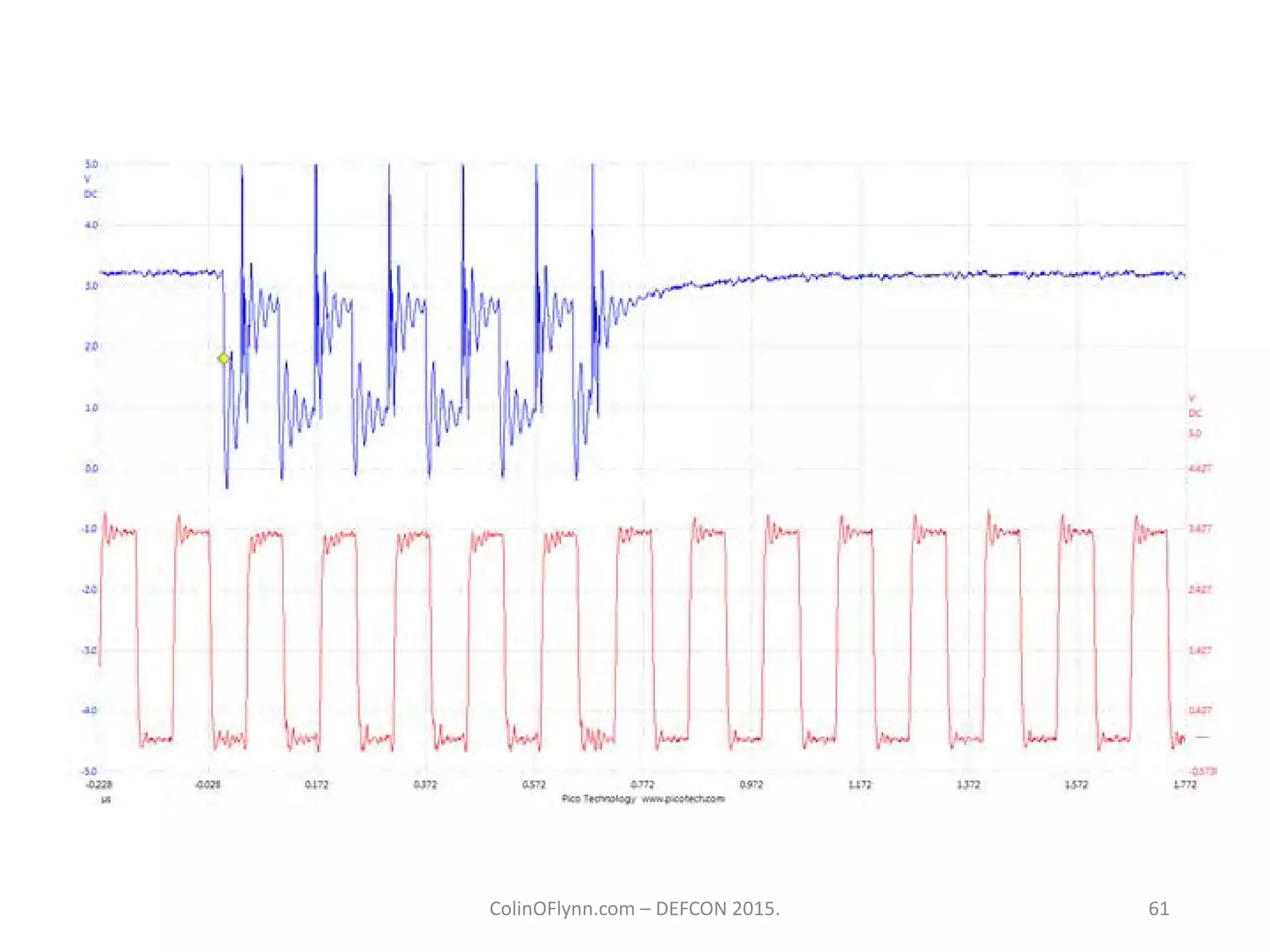
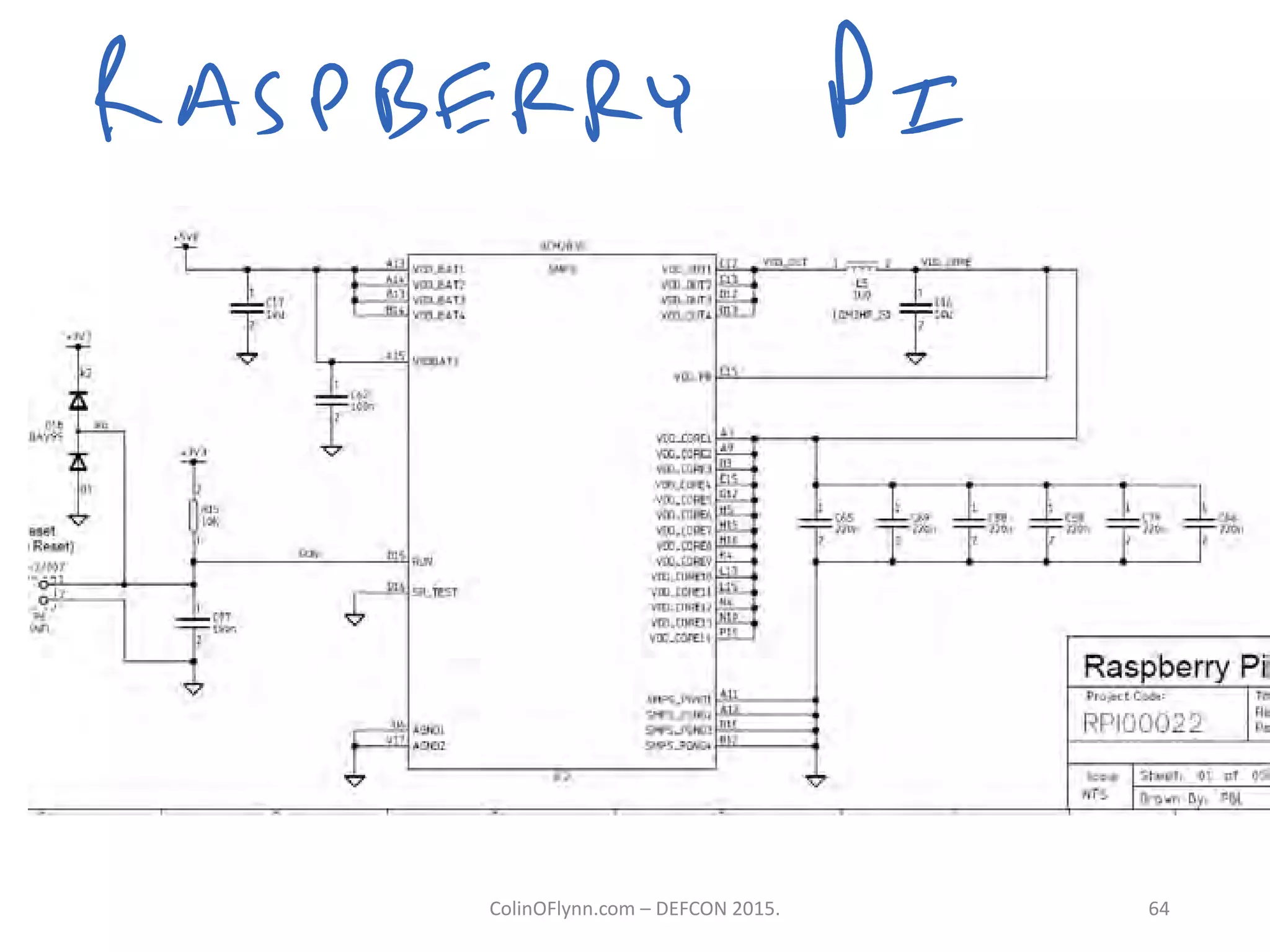
This document summarizes a presentation given by Colin O'Flynn at DEFCON 2015 about physical layer attacks. The objective of the presentation was to teach about various physical layer attacks and show that the tools used are open source and freely available. Many of the hardware tools are commercially available but can also be homemade. The presentation covered topics like side-channel analysis, fault injection, and cryptography attacks on embedded devices and discussed tools like the ChipWhisperer for performing analyses. Code and documentation for the tools are available on the listed websites.








![unsigned char correctpin[6] = {1,2,3,4,5,6};
unsigned char enteredpin[6];
read_pin_from_buttons(enteredpin);
for (i = 0; i < 6; i++){
if (correctpin[i] != enteredpin[i]){
return;
}
}
ColinOFlynn.com – DEFCON 2015. 10](https://image.slidesharecdn.com/defcon-23-colin-oflynn-dont-whisper-my-chips-200502123847/75/DEF-CON-23-COLIN-O-FLYNN-dont-whisper-my-chips-10-2048.jpg)