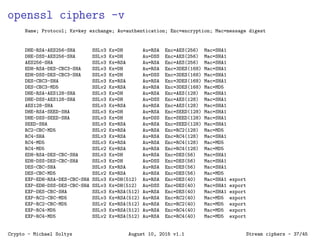
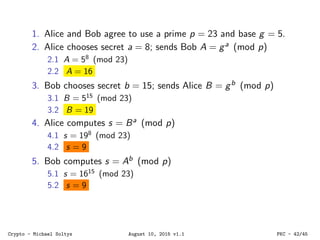
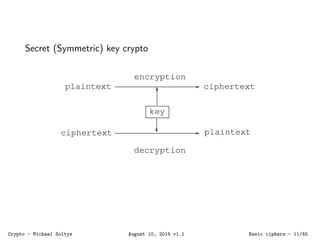
The document provides an introduction to cryptography, covering various methods like symmetric and asymmetric encryption, digital signatures, and hash functions. It highlights the challenges of building secure systems using potentially insecure components and the importance of key management in cryptographic algorithms. Additionally, it addresses practical applications such as the use of cryptography in network security protocols like WEP, WPA, and WPA2.































![(Keep in mind that 28 = 256)
let S[i] be an array of octets (i.e., bytes)
Initialize S:
for i=0 . . . 255
S[i]=i
end for
j=0
for i=0 . . . 255
j=(j+S[i]+key[i mod keylength]) mod 256
swap S[i] and S[j]
end for
Crypto - Michael Soltys August 10, 2015 v1.1 Stream ciphers - 33/45](https://image.slidesharecdn.com/ok24e3sdsgnykufa096a-signature-29cf0c7818fe71939a03d6a0287ad15dcab0e4b533d7b7d40693b4dceb095882-poli-150822201930-lva1-app6892/85/Intro-to-Cryptography-33-320.jpg)
![Generate pseudo-random bit stream (byte at a time)
i=0
j=0
while "next byte needed"
i=(i+1) mod 256
j=(j+S[i]) mod 256
swap S[i] and S[j]
k=S[(S[i]+S[j]) mod 256]
output k
end while
Crypto - Michael Soltys August 10, 2015 v1.1 Stream ciphers - 34/45](https://image.slidesharecdn.com/ok24e3sdsgnykufa096a-signature-29cf0c7818fe71939a03d6a0287ad15dcab0e4b533d7b7d40693b4dceb095882-poli-150822201930-lva1-app6892/85/Intro-to-Cryptography-34-320.jpg)