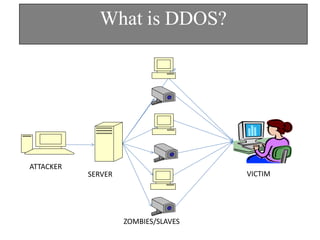
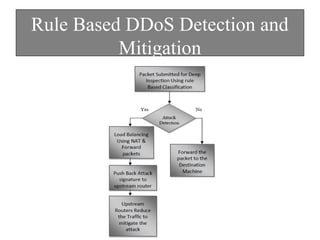
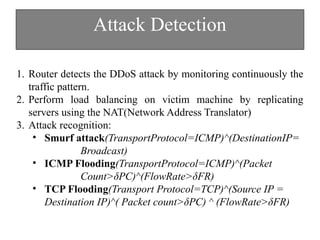
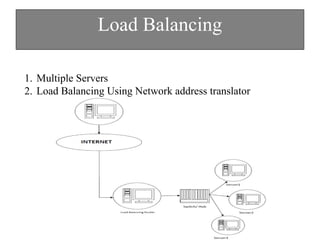
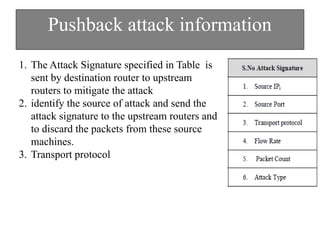
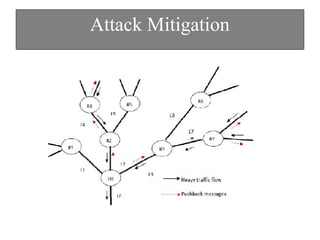
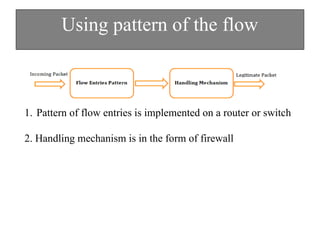
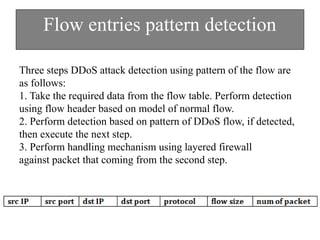
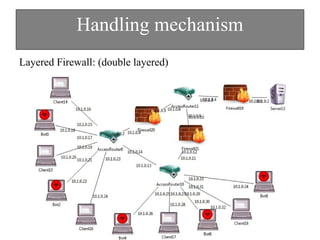
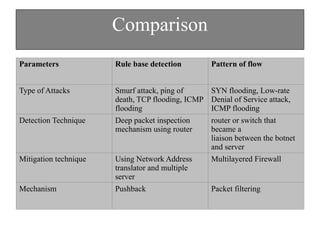
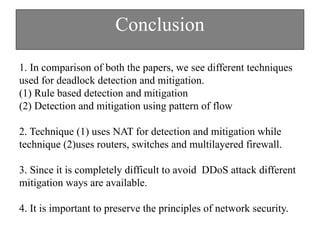
The document discusses DDoS attacks and categorizes various types, including SYN flooding, ICMP flooding, and others, alongside mitigation techniques. It describes rule-based detection methods, load balancing using NAT, and techniques for pushback attack information to reduce traffic to the victim. Additionally, it emphasizes the importance of network security and offers multiple approaches to handle DDoS attacks.





![References
[1] Khamruddin, Md, and Ch Rupa. "
A rule based DDoS detection and mitigation technique." In 2012 Nirma University
International Conference on Engineering (NUiCONE), pp. 1-5. IEEE, 2012.
[2] Sanmorino, Ahmad, and Setiadi Yazid. "Ddos
attack detection method and mitigation using pattern of the flow." In Information and
Communication Technology (ICoICT), 2013 International Conference of, pp. 12-16.
IEEE, 2013
[3] 2016. [Online]. Available: Anon. Confidentiality, Integrity, Availability: The three
components of the CIA Triad. Retrieved November 4, 2016 from
http://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-the-
three-components-of-the-cia-triad/. [Accessed: 04- Nov- 2016].
[4] Cisco Systems. (2014, January). Defeating DDos attack. [Online]. Available:
http://www.cisco.com/c/en/us/products/collateral/security/traffic-anomaly-detector-xt-5
600a/prod_white_paper0900aecd8011e927.html](https://image.slidesharecdn.com/ddosattackandmitigationtechniques-250205160700-2df01f60/85/DDOS_Attack_and_Mitigation_Techniques-pptx-18-320.jpg)
