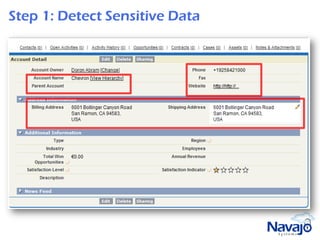
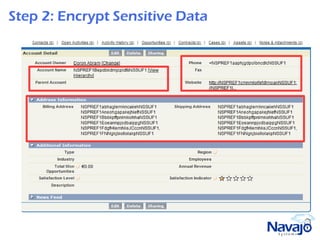
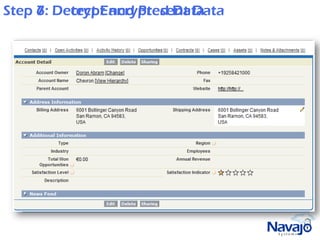
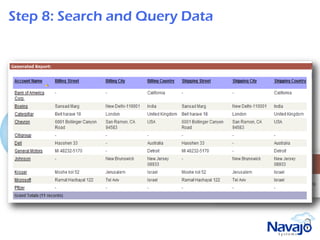
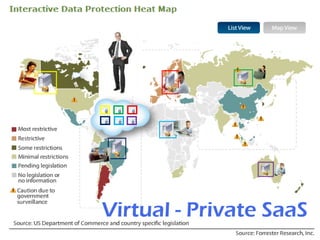
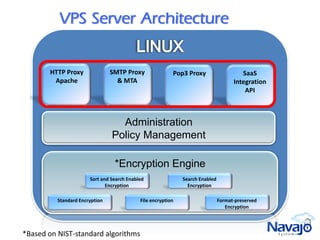
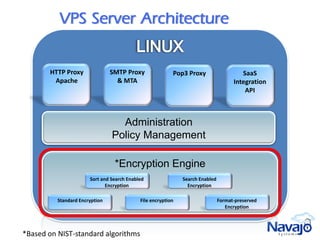
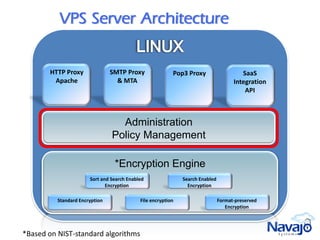
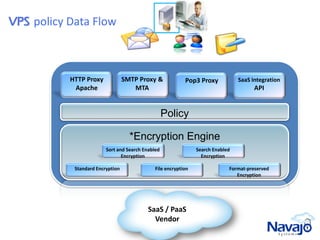
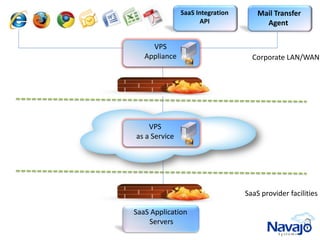
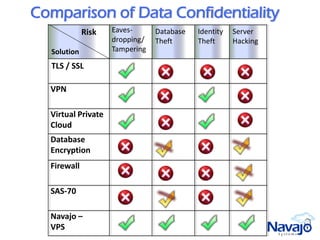
Navajo Systems aims to expand cloud computing adoption by addressing data privacy and regulatory compliance barriers. It was founded in 2009 by information security experts and is backed by venture capital. Navajo's Virtual Private SaaS solution allows customers to encrypt sensitive data within SaaS applications in real-time, maintaining functionality while keeping data encrypted at rest. This addresses privacy and compliance concerns while keeping customers in control of their sensitive data.