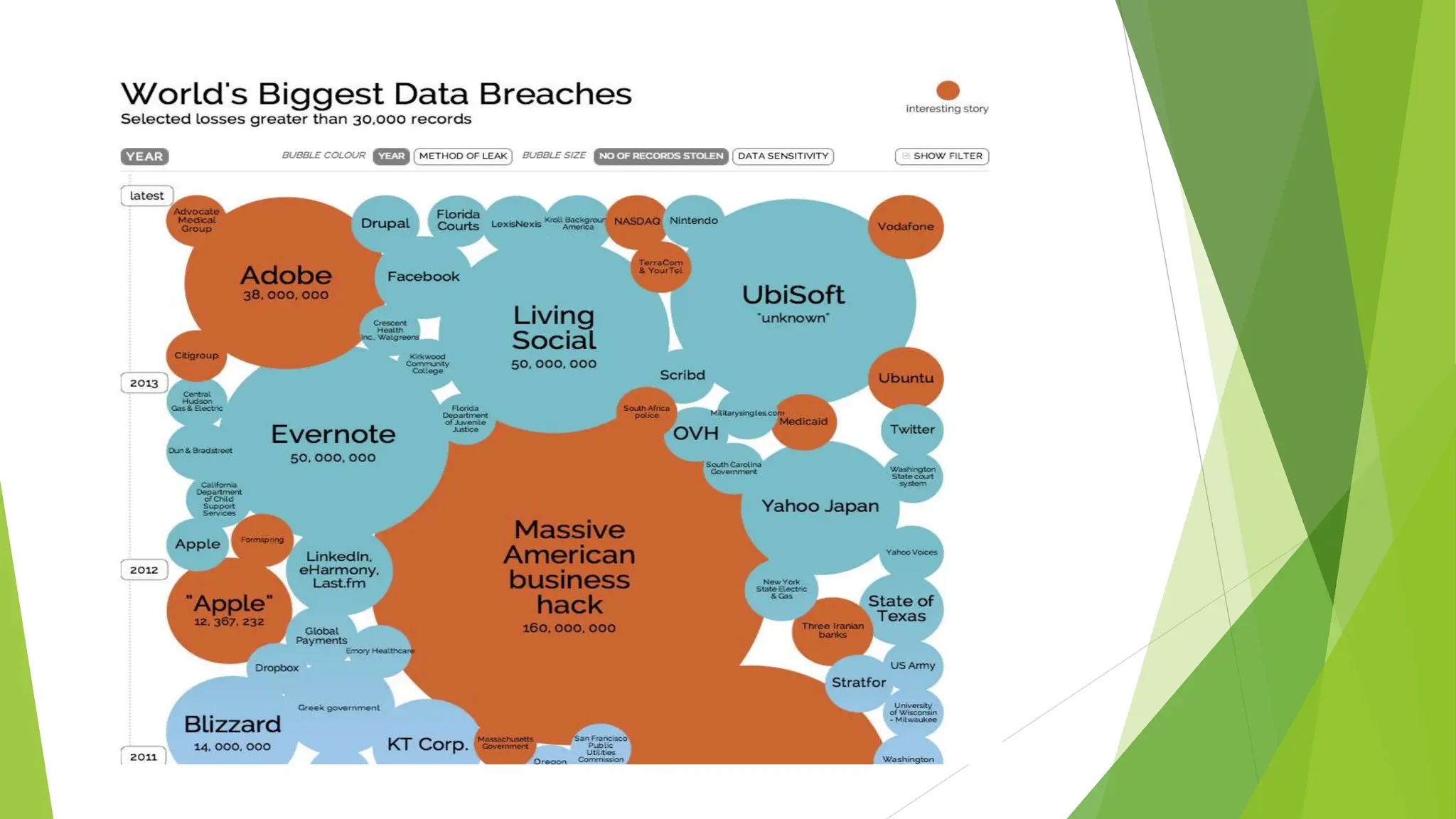
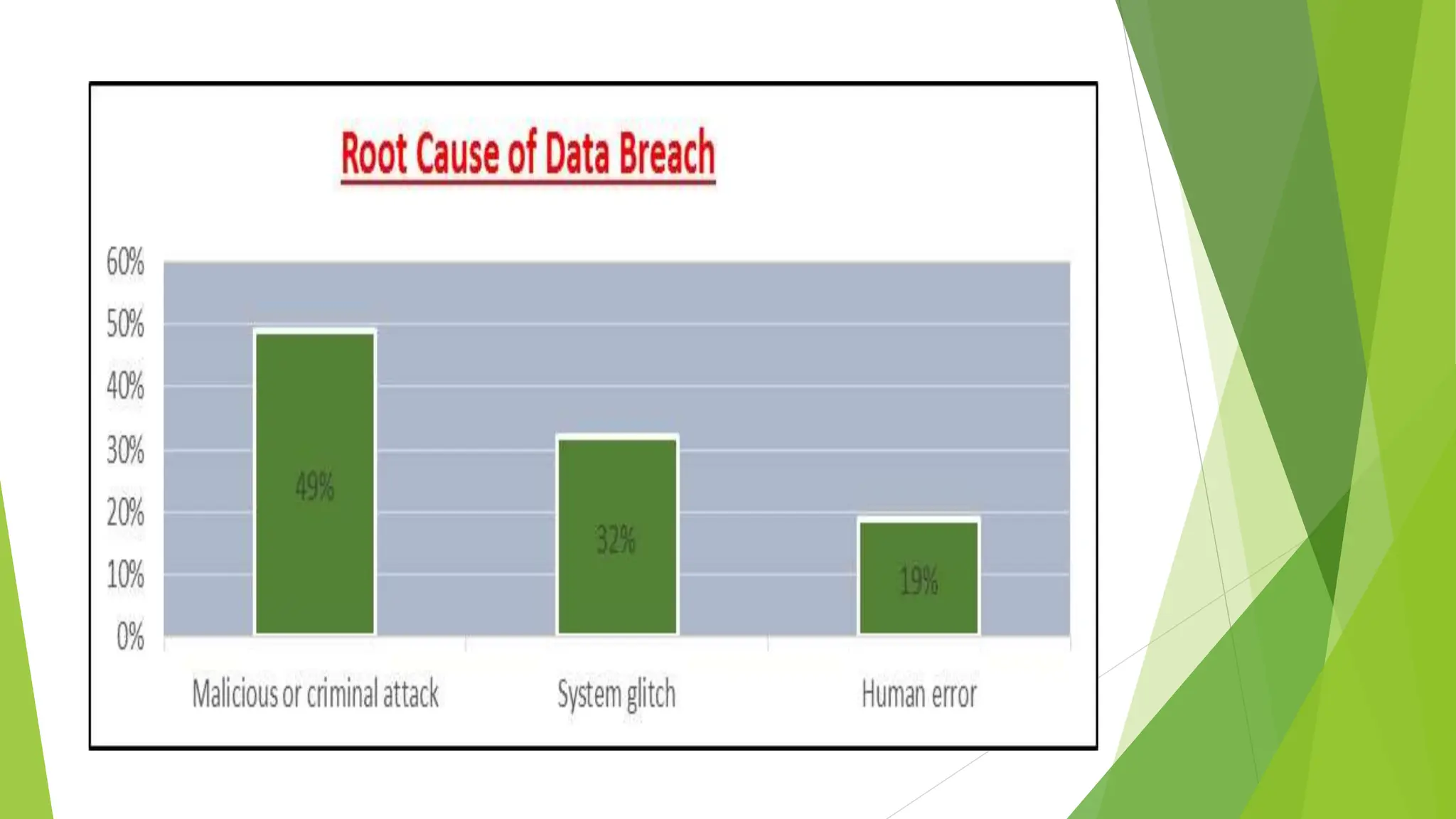
This document discusses data leakage detection techniques. It begins with an introduction to data leakage and examples of how it occurs when data is shared with third parties. It then summarizes some of the largest data breaches of the 21st century involving Yahoo, eBay, Uber and Election Systems & Software. Existing detection techniques like watermarking and steganography are explained along with their drawbacks. Applications of detection include identifying who leaked the data to reduce cybercrime. Future work aims to model agent guilt and handle online data allocation to agents.

















![dx1=dct2(x1); dx11=dx1; //discrete cosine transform
dx2=dct2(x2); dx22=dx2;
dx3=dct2(x3); dx33=dx3;
load m.dat
g=10; // to decide water-marking limit
[rm,cm]=size(m);
dx1(1:rm,1:cm)=dx1(1:rm,1:cm)g*m;
dx1(1:rm,1:cm)=dx1(1:rm,1:cm)g*m;
dx1(1:rm,1:cm)=dx1(1:rm,1:cm)g*m;
figure,imshow(dx1);
figure,imshow(dx2);
figure,imshow(dx3);](https://image.slidesharecdn.com/dataleakagedetection-181121040001-240313041144-60606ee5/75/dataleakagedetection-1811210400vgjcd01-pptx-20-2048.jpg)








