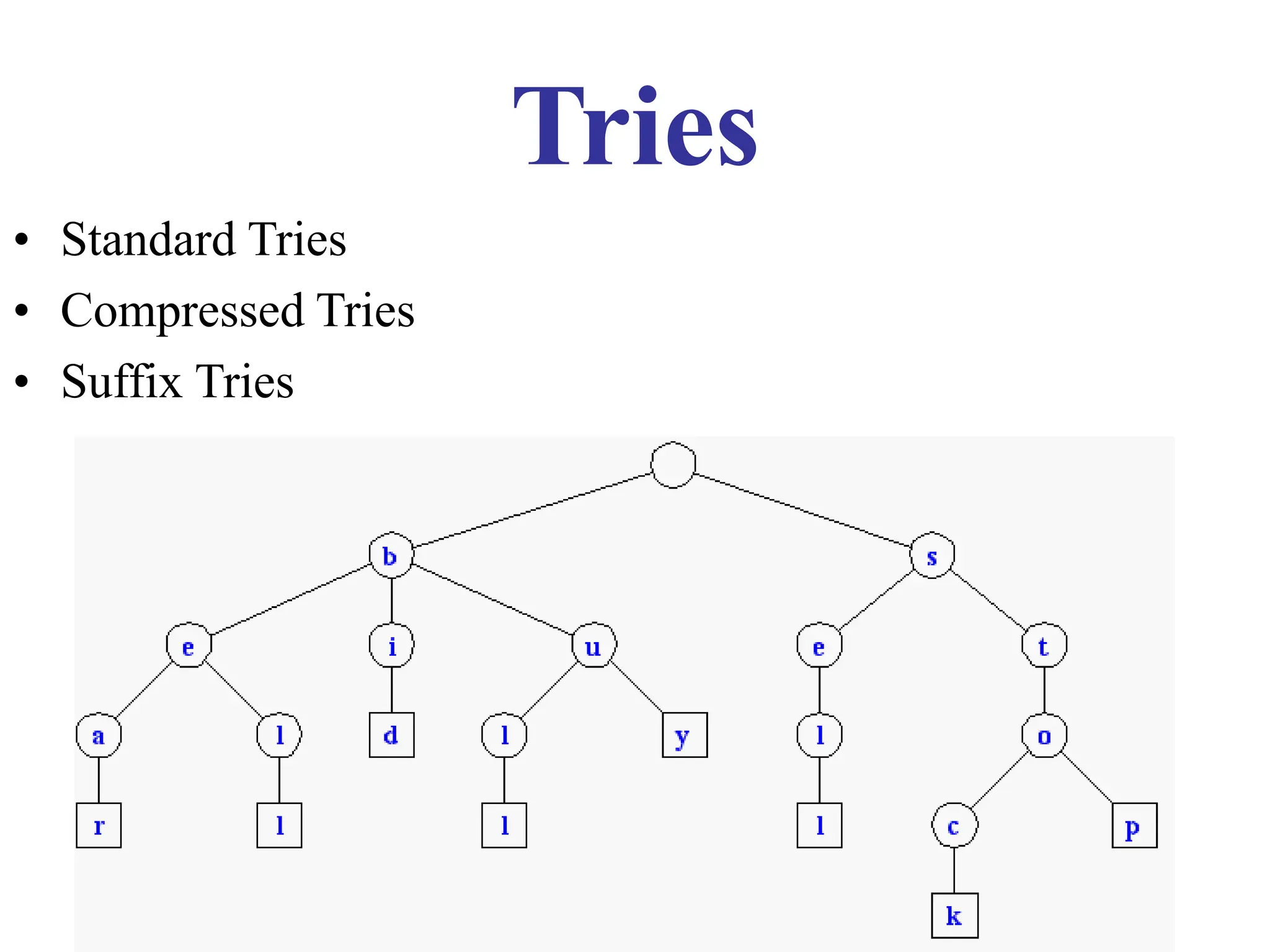
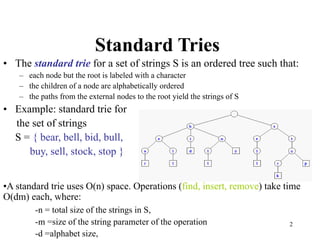
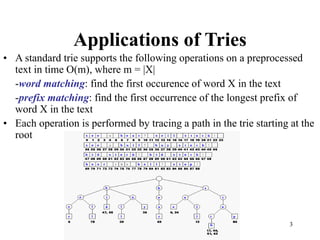
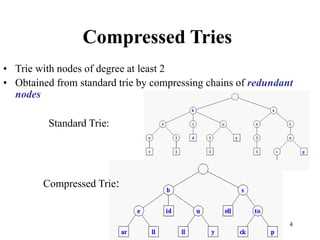
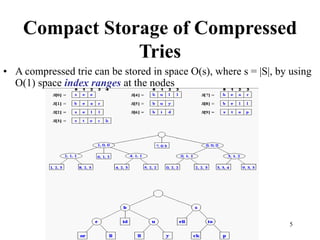
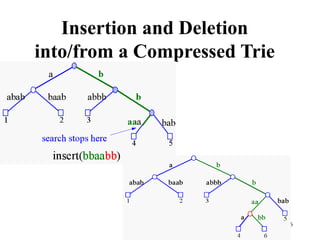
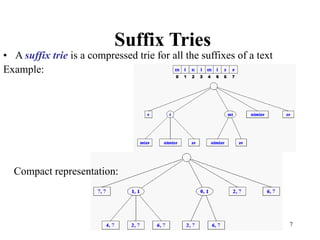
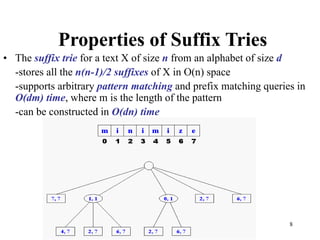
The document discusses different types of tries, including standard, compressed, and suffix tries, detailing their structure, space complexity, and operational efficiency for string management tasks such as word and prefix matching. It highlights the applications of tries in search engines and internet routers, where tries facilitate efficient data storage and retrieval through unique indexing methods. Additionally, it mentions optimization techniques like stopword elimination and link analysis that enhance search performance.